VMware 5v0-91-20 practice test
VMware Carbon Black Portfolio Skills Exam
Question 1
An alert for a device running a proprietary application is tied to a vital business operation.
Which action is appropriate to take?
- A. Add the application to the Approved List.
- B. Terminate the process.
- C. Deny the operation.
- D. Quarantine the device.
Answer:
A
Question 2
Which wildcard configuration applies a policy to all files and subfolders in a specific folder in
Endpoint
Standard?
- A. C:\Program Files\example\$$
- B. C:\Program Files\example\**
- C. C:\Program Files\example\$
- D. C:\Program Files\example\*
Answer:
B
Reference:
https://community.carbonblack.com/t5/Knowledge-Base/Endpoint-Standard-How-to-
Create-Policy-Blocking-Isolation-and/ta-p/65941
Question 3
Which statement should be used when constructing queries in Carbon Black Audit and Remediation,
Live
Query?
- A. ALTER
- B. UPDATE
- C. REMOVE
- D. SELECT
Answer:
D
Question 4
How often do watchlists run?
- A. Every 10 minutes
- B. Every 5 minutes
- C. Watchlists can be configured to run at scheduled intervals
- D. Every 30 minutes
Answer:
C
Question 5
An organization leverages a commonly used software distribution tool to manage deployment of
enterprise software and updates. Custom rules are a suitable option to ensure the approval of files
delivered by this tool.
Which other trust mechanism could the organization configure for large-scale approval of these files?
- A. Windows Update
- B. Trusted Distributor
- C. Local Approval Mode
- D. Rapid Config
Answer:
C
Reference:
https://uit.stanford.edu/service/cbprotect/approval-mechanisms
Question 6
Refer to the exhibit: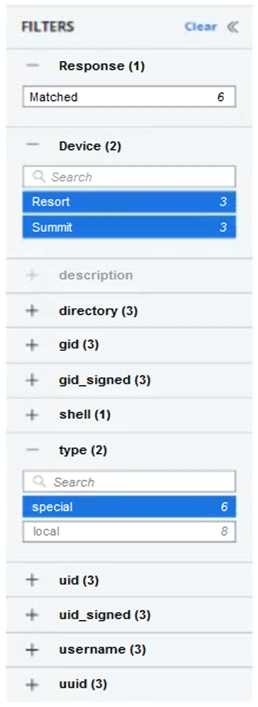
Which two logic statements correctly explain filtering within the UI? (Choose two.)
- A. Filtering between fields is a logical OR
- B. Filtering within the same field is a logical AND
- C. Filtering between fields is a logical AND
- D. Filtering between fields is a logical XOR
- E. Filtering within the same field is a logical OR
Answer:
AD
Question 7
An administrator wants to query the status of the firewall for all endpoints. The administrator will
query the
registry key found here
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPoli
cy
\StandardProfile.
To make the results easier to understand, the administrator wants to return either enabled or
disabled for the results, rather than the value from the registry key.
Which SQL statement will rewrite the output based on a specific result set returned from the system?
- A. CASE
- B. AS
- C. ALTER
- D. SELECT
Answer:
A
Reference:
https://www.carbonblack.com/blog/8-live-queries-that-will-speed-up-your-next-pci-
audit/l
Question 8
An analyst wants to block an application's specific behavior but does not want to kill the process
entirely as it is heavily used on workstations. The analyst needs to use a Blocking and Isolation Action
to ensure that the process is kept alive while blocking further unwanted activity.
Which Blocking and Isolation Action should the analyst use to accomplish this goal?
- A. Log Operation
- B. Deny Operation
- C. Terminate Process
- D. Block Process
Answer:
B
Question 9
App Control System Health email alerts for excessive agent backlog are occurring hourly. This is
overwhelming the analysts, and they would like to reduce the notifications.
How can the analyst reduce the unneeded alerts?
- A. Set the email address for subscribers to an invalid email.
- B. Change reminder email to daily or disabled.
- C. Disable the alert.
- D. Delete the alert.
Answer:
B
Question 10
An administrator needs to query all endpoints in the HR group for instances of an obfuscated copy of
cmd.exe.
Given this Enterprise EDR query:
process_name:cmd.exe AND device_group:HR AND NOT enriched:true
Which example could be added to the query to provide the desired results?
- A. NOT process_name:cmd.exe
- B. NOT process_original_filename:cmd.exe
- C. NOT process_company_name:cmd.exe
- D. NOT process_internal_name:cmd.exe
Answer:
A
Question 11
A company uses Audit and Remediation to check configurations and adhere to compliance
regulations. The regulations require monthly reporting and twelve months of data retained.
How can an administrator accomplish this requirement with Audit and Remediation?
- A. Schedule the query to run monthly, and set the data retention to 12 months for the query.
- B. Schedule the query to run monthly, and configure the audit log retention to 12 months.
- C. Schedule the query to run monthly, and no further action is required.
- D. Schedule the query to run monthly, and export the results for each run to an external location.
Answer:
D
Question 12
Which list below captures all Enforcement Levels for App Control policies?
- A. Critical, Lockdown, Monitored, Tracking, Banning
- B. High Enforcement, Medium Enforcement, Low Enforcement
- C. High Enforcement, Medium Enforcement, Low Enforcement, None (Visibility), None (Disabled)
- D. Control, Local Approval, Disabled
Answer:
C
Reference:
https://www.google.com/url
?
sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwiFsPPz04XvAhWRsnEKHV4lBukQFjABegQIA
hAD&
url=https%3A%2F%2Fcommunity.carbonblack.com%2Fgbouw27325%2Fattachments%2Fgbouw2732
5%
2Fproduct-docs-
news%2F2961%2F1%2FVMware%2520Carbon%2520Black%2520App%2520Control%
25208.5.0%2520User%2520Guide.pdf&usg=AOvVaw3es_0JTc8-_BifNR4iFiGl (6)
Question 13
An incorrectly constructed watchlist generates 10,000 incorrect alerts.
How should an administrator resolve this issue?
- A. Delete the watchlist to automatically clear the alerts, and then create a new watchlist with the correct criteria.
- B. From the Triage Alerts Page, use the facets to select the watchlist, click the Wrench button to Mark all as Resolved False Positive, and then update the watchlist with the correct criteria.
- C. Update the Triage Alerts Page to show 200 alerts, click the Select All Checkbox, click the “Dismiss Alert(s)” button for each page, and then update the watchlist with the correct criteria.
- D. From the Watchlists Page, select the offending watchlist, click Clear Alerts from the Action menu, and then update the watchlist with the correct criteria.
Answer:
B
Question 14
An Enterprise EDR administrator wants to use Watchlists curated by VMware Carbon Black and other
threat intelligence specialists.
How should the administrator add these curated Watchlists from the Watchlists page?
- A. Click Add Watchlists, and input the URL(s) for the desired Watchlists.
- B. Click Take Action, select Edit, and select the desired Watchlists.
- C. Click Take Action, and select Subscribe for the desired Watchlists.
- D. Click Add Watchlists, on the Subscribe tab select the desired Watchlists, and click Subscribe.
Answer:
A
Reference:
https://www.google.com/url
?
sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwjl1tW404XvAhWZRhUIHSygB74QFjADegQI
ExAD&
url=https%3A%2F%2Fcommunity.carbonblack.com%2Fgbouw27325%2Fattachments%2Fgbouw2732
5%
2Fproduct-docs-news%2F1913%2F18%2FEnterprise%2520EDR%2520Getting%
2520Started.pdf&usg=AOvVaw2_M7opfEgUaIIfutBZChvk (5)
Question 15
Which identifier is shared by all events when an alert is investigated?
- A. Process ID
- B. Event ID
- C. Priority Score
- D. Alert ID
Answer:
B