snia s10-210 practice test
Storage Networking Management and Administration
Question 1
You have replaced an HBA and are trying to add it to an existing zone using the FC switch GUI
interface. You are unable to do so.
Why is this happening?
- A. The OS login has not occurred.
- B. The Web login has not occurred.
- C. The fabric login has not occurred.
- D. The port login has occurred.
Answer:
C
Question 2
A number of servers are experiencing slower than expected performance. Analyzing the server,
switch, and storage logs do not indicate any issues. You have been asked by the customer to address
this issue.
What will improve performance?
- A. Increase the current queue depth setting from 1.
- B. Change the frame size from 2148 bytes,
- C. Decrease the buffer-to-buffer credits setting.
- D. Enable write caching functionality for the device driver.
Answer:
A
Question 3
A company wants to implement a database which requires a storage subsystem with no more than 2
ms write latency and 1 ms read latency.
Which type of drive would you use?
- A. SATA
- B. FC
- C. SSD
- D. ATA
Answer:
C
Question 4
A colleague asks you if the added cost of using encrypting tape drives and sending the tapes off-site
is warranted, since your IT organization already has large security investments such as firewalls and
database table encryption.
What is your response?
- A. The correct firewall rule set would make encrypted tape drives obsolete, but there has not always been strong confidence in the firewall administrators.
- B. Encrypted database tables only protect data against inappropriate access by super users such as database or server administrators abusing root privileges.
- C. Encrypt tape drives as part of a defense in depth strategy to ensure that one security mechanism being compromised does not expose all information to a malicious user.
- D. The existing firewalls and database table encryption do not replace encrypted tape drives, but implementing an intrusion protection system (IPS) will make tape encryption obsolete.
Answer:
C
Question 5
The latest storage utilization report shows that 80% of the current 500 TB of enterprise storage is
allocated. The storage administrator must specify the amount of additional storage needed for local
copies for approximately half of the active storage.
How much additional storage should the administrator request?
- A. 400 TB
- B. 300 TB
- C. 200 TB
- D. 100 TB
Answer:
C
Question 6
What is a common protocol used in cloud communications?
- A. WebDAV
- B. SCP
- C. HTTP
- D. CDMI
Answer:
C
Question 7
Click the Exhibit button.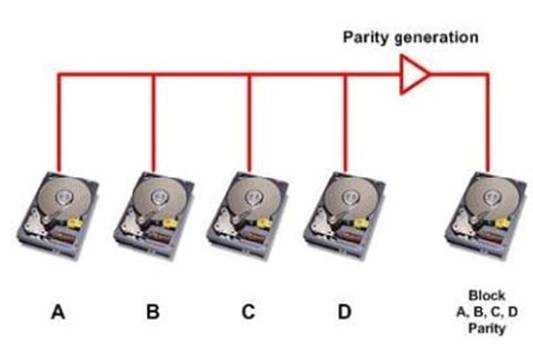
Referring to the exhibit, which RAID level is shown?
- A. RAID 4
- B. RAID 5
- C. RAID 0
- D. RAID 6
Answer:
A
Question 8
A customer has upgraded all switches in their redundant fabrics during a single maintenance
window. Shortly after the upgrades are completed on the core switches, all servers lose access to all
SAN attached storage.
What would have prevented this scenario?
- A. High availability
- B. Fault tolerance
- C. Change or risk management
- D. Clustered servers
Answer:
C
Question 9
Click the Exhibit button.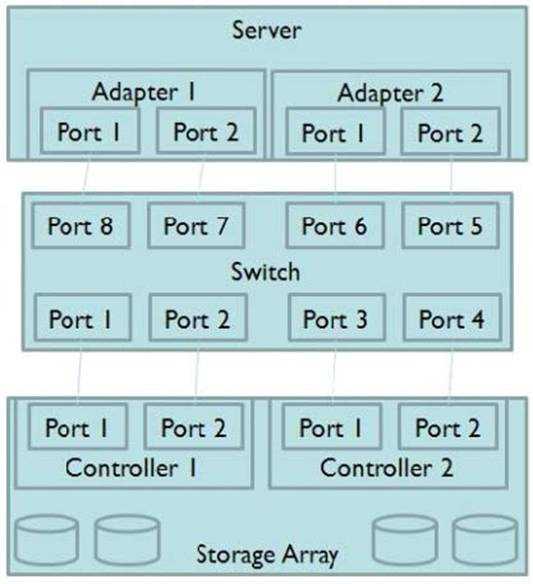
Referring to the exhibit, what are the two largest risks to a highly available solution? (Choose two.)
- A. Only two adapters per controller
- B. Only two adapters on the server
- C. Only one server
- D. Only one switch
Answer:
C,D
Question 10
The storage administrator is required to create five zones within the FC SAN.
Which Fibre Channel server would be used to do this?
- A. Fabric Login server
- B. Name server
- C. Management server
- D. Fabric Controller
Answer:
C
Question 11
You want to visibly verify FC port initialization by reading an analyzer trace. Your objective is to find
the frames associated with the initialization protocol to ensure that the FC device is operating
correctly during the login process, to be recognized as part of the switched fabric, and appear in a
directory of attached FC devices.
What must all Fibre Channel devices do to accomplish this?
- A. Log in using the Name server.
- B. Log in using the Fabric Controller.
- C. Log in using the Management server.
- D. Log in using the Fabric Login server.
Answer:
D
Question 12
You have been hired to consult with storage administrators that are working with zoning and naming
convention consistency issues. There are numerous types of zoning methods available using
standards that also include aliasing. You want to use a method that guarantees unique global port
identification.
What accomplishes this goal?
- A. WWPN
- B. domain_id:port_#
- C. Alias
- D. Zone set
Answer:
A
Question 13
Click the Exhibit button.
What is the protocol stack shown in the exhibit?
- A. FCoE
- B. SCSI
- C. InfiniBand
- D. Fibre Channel
Answer:
B
Question 14
You have a file system which allows data and metadata segregation.
How should you accelerate read I/O on the file system while keeping costs low?
- A. Assign the fastest storage to the data portion of the file system.
- B. Assign the fastest storage to the metadata portion of the file system.
- C. Assign fast storage to the data and the metadata portions of the file system.
- D. Keep the file system very small.
Answer:
B
Question 15
A company has a storage subsystem that supports a variety of replication options. They have
purchased an identical array and placed it at a secondary site 50 km away and will provide the
shortest RPO.
Which statement is correct?
- A. Asynchronous replication is the only replication option for distances over 50 km.
- B. Synchronous replication is the only replication option for distances over 50 km.
- C. Snapshots allow for data to be quickly captured, copied, and mounted from one storage array to another and is the ideal solution for all distances.
- D. Synchronous replication will keep the arrays closely synchronized and is ideal for short distances.
Answer:
D