palo alto networks xdr-engineer practice test
Palo Alto Networks Certified XDR Engineer
Question 1
[Data Ingestion and Integration]
An administrator wants to employ reusable rules within custom parsing rules to apply consistent log
field extraction across multiple data sources. Which section of the parsing rule should the
administrator use to define those reusable rules in Cortex XDR?
- A. RULE
- B. INGEST
- C. FILTER
- D. CONST
Answer:
D
Question 2
[Data Ingestion and Integration]
What will be the output of the function below?
L_TRIM("a* aapple", "a")
- A. ' aapple'
- B. " aapple"
- C. "pple"
- D. " aapple-"
Answer:
A
Question 3
[Data Ingestion and Integration]
How can a customer ingest additional events from a Windows DHCP server into Cortex XDR with
minimal configuration?
- A. Activate Windows Event Collector (WEC)
- B. Install the XDR Collector
- C. Enable HTTP collector integration
- D. Install the Cortex XDR agent
Answer:
B
Question 4
[Cortex XDR Agent Configuration]
How are dynamic endpoint groups created and managed in Cortex XDR?
- A. Endpoint groups require intervention to update the group with new endpoints when a new device is added to the network
- B. Each endpoint can belong to multiple groups simultaneously, allowing different security policies to be applied to the same device at the same time
- C. After an endpoint group is created, its assigned security policy cannot be changed without deleting and recreating the group
- D. Endpoint groups are defined based on fields such as OS type, OS version, and network segment
Answer:
D
Question 5
[Dashboards and Reporting]
An engineer is building a dashboard to visualize the number of alerts from various sources. One of
the widgets from the dashboard is shown in the image below:
The engineer wants to configure a drilldown on this widget to allow dashboard users to select any of
the alert names and view those alerts with additional relevant details. The engineer has configured
the following XQL query to meet the requirement:
dataset = alerts
| fields alert_name, description, alert_source, severity, original_tags, alert_id, incident_id
| filter alert_name =
| sort desc _time
How will the engineer complete the third line of the query (filter alert_name =) to allow dynamic
filtering on a selected alert name?
- A. $y_axis.value
- B. $x_axis.value
- C. $x_axis.name
- D. $y_axis.name
Answer:
B
Question 6
[Detection Engineering]
An XDR engineer is creating a correlation rule to monitor login activity on specific systems. When the
activity is identified, an alert is created. The alerts are being generated properly but are missing the
username when viewed. How can the username information be included in the alerts?
- A. Select “Initial Access” in the MITRE ATT&CK mapping to include the username
- B. Update the query in the correlation rule to include the username field
- C. Add a mapping for the username field in the alert fields mapping
- D. Add a drill-down query to the alert which pulls the username field
Answer:
C
Question 7
[Detection Engineering]
A correlation rule is created to detect potential insider threats by correlating user login events from
one dataset with file access events from another dataset. The rule must retain all user login events,
even if there are no matching file access events, to ensure no login activity is missed.
text
Copy
dataset = x
| join (dataset = y)
Which type of join is required to maintain all records from dataset x, even if there are no matching
events from dataset y?
- A. Inner
- B. Left
- C. Right
- D. Outer
Answer:
B
Question 8
[Post-Deployment Management and Configuration]
A cloud administrator reports high network bandwidth costs attributed to Cortex XDR operations and
asks for bandwidth usage to be optimized without compromising agent functionality. Which two
techniques should the engineer implement? (Choose two.)
- A. Configure P2P download sources for agent upgrades and content updates
- B. Enable minor content version updates
- C. Enable agent content management bandwidth control
- D. Deploy a Broker VM and activate the local agent settings applet
Answer:
A,C
Question 9
[Cortex XDR Agent Configuration]
How can a Malware profile be configured to prevent a specific executable from being uploaded to the
cloud?
- A. Disable on-demand file examination for the executable
- B. Set PE and DLL examination for the executable to report action mode
- C. Add the executable to the allow list for executions
- D. Create an exclusion rule for the executable
Answer:
D
Question 10
[Planning and Installation]
During the deployment of a Broker VM in a high availability (HA) environment, after configuring the
Broker VM FQDN, an XDR engineer must ensure agent installer availability and efficient content
caching to maintain performance consistency across failovers. Which additionalconfiguration steps
should the engineer take?
- A. Use shared SSL certificates and keys for all Broker VMs and configure a single IP address for failover
- B. Upload the-signed SSL server certificate and key and deploy a load balancer
- C. Deploy a load balancer and configure SSL termination at the load balancer
- D. Enable synchronized session persistence across Broker VMs and use a self-signed certificate and key
Answer:
B
Question 11
[Cortex XDR Agent Configuration]
Based on the Malware profile image below, what happens when a new custom-developed
application attempts to execute on an endpoint?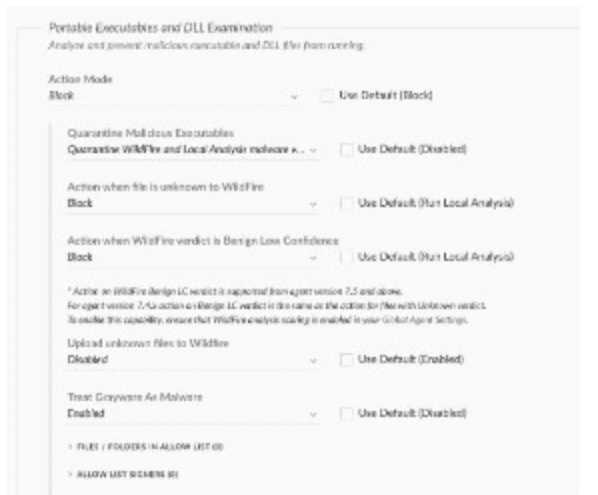
- A. It will immediately execute
- B. It will not execute
- C. It will execute after one hour
- D. It will execute after the second attempt
Answer:
B
Question 12
[Data Ingestion and Integration]
Which configuration profile option with an available built-in template can be applied to both
Windows and Linux systems by using XDR Collector?
- A. Filebeat
- B. HTTP Collector template
- C. XDR Collector settings
- D. Winlogbeat
Answer:
A
Question 13
[Detection Engineering]
What is the earliest time frame an alert could be automatically generated once the conditions of a
new correlation rule are met?
- A. Between 30 and 45 minutes
- B. Immediately
- C. 5 minutes or less
- D. Between 10 and 20 minutes
Answer:
C
Question 14
[Detection Engineering]
A Custom Prevention rule that was determined to be a false positive alert needs to be tuned. The
behavior was determined to be authorized and expected on the affected endpoint. Based on the
image below, which two steps could be taken? (Choose two.)
[Image description: A Custom Prevention rule configuration, assumed to trigger a Behavioral
Indicator of Compromise (BIOC) alert for authorized behavior]
- A. Apply an alert exception
- B. Apply an alert exclusion to the XDR behavioral indicator of compromise (BIOC) alert
- C. Apply an alert exclusion to the XDR agent alert
- D. Modify the behavioral indicator of compromise (BIOC) logic
Answer:
A,B
Question 15
[Data Ingestion and Integration]
In addition to using valid authentication credentials, what is required to enable the setup of the
Database Collector applet on the Broker VM to ingest database activity?
- A. Valid SQL query targeting the desired data
- B. Access to the database audit log
- C. Database schema exported in the correct format
- D. Access to the database transaction log
Answer:
A