palo alto networks pcnse practice test
Palo Alto Networks Certified Network Security Engineer
Question 1
Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.)
- A. log forwarding auto-tagging
- B. XML API
- C. GlobalProtect agent
- D. User-ID Windows-based agent
Answer:
bd
Reference:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-new-features/user-id-features/dynamic-user-groups.html
Question 2
What is the function of a service route?
- A. The service packets exit the firewall on the port assigned for the external service. The server sends its response to the configured source interface and source IP address.
- B. The service packets enter the firewall on the port assigned from the external service. The server sends its response to the configured destination interface and destination IP address.
- C. The service route is the method required to use the firewall's management plane to provide services to applications.
- D. Service routes provide access to external services, such as DNS servers, external authentication servers or Palo Alto Networks services like the Customer Support Portal.
Answer:
a
Reference:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/networking/service-routes.html
Question 3
An administrator is considering upgrading the Palo Alto Networks NGFW and central management Panorama version.
What is considered best practice for this scenario?
- A. Perform the Panorama and firewall upgrades simultaneously.
- B. Upgrade the firewall first, wait at least 24 hours, and then upgrade the Panorama version.
- C. Upgrade Panorama to a version at or above the target firewall version.
- D. Export the device state, perform the update, and then import the device state.
Answer:
c
Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClRrCAK
Question 4
VPN traffic intended for an administrators Palo Alto Networks NGFW is being maliciously intercepted and retransmitted by the interceptor. When creating a VPN tunnel, which protection profile can be enabled to prevent this malicious behavior?
- A. Zone Protection
- B. DoS Protection
- C. Web Application
- D. Replay
Answer:
a
Question 5
A Security policy rule is configured with a Vulnerability Protection Profile and an action of Deny.
Which action will this configuration cause on the matched traffic?
- A. It will cause the firewall to deny the matched sessions. Any configured Security Profiles have no effect if the Security policy rule action is set to Deny.
- B. The configuration will allow the matched session unless a vulnerability signature is detected. The Deny action will supersede the per-severity defined actions defined in the associated Vulnerability Protection Profile.
- C. It will cause the firewall to skip this Security policy rule. A warning will be displayed during a commit.
- D. The Profile Settings section will be grayed out when the Action is set to Deny.
Answer:
a
Question 6
Which two features require another license on the NGFW? (Choose two.)
- A. SSL Inbound Inspection
- B. SSL Forward Proxy
- C. Decryption Mirror
- D. Decryption Broker
Answer:
cd
Reference:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/decryption/configure-decryption-port-mirroring.html https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/decryption/decryption-licenses.html
Question 7
An engineer is creating a template and wants to use variables to standardize the configuration across a large number of devices.
Which two variable types can be defined? (Choose two.)
- A. IP netmask
- B. Zone
- C. Path group
- D. FQDN
Answer:
ad
Question 8
Which Zone Pair and Rule Type will allow a successful connection for a user on the Internet zone to a web server hosted on the DMZ zone? The web server is reachable using a Destination NAT policy in the Palo Alto Networks firewall.
A.
B.
C.
D.
Answer:
b
Question 9
An administrator cannot see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall.
Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the firewall to Panorama?
A.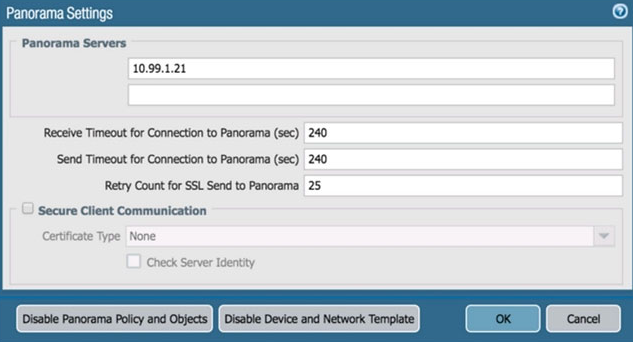
B.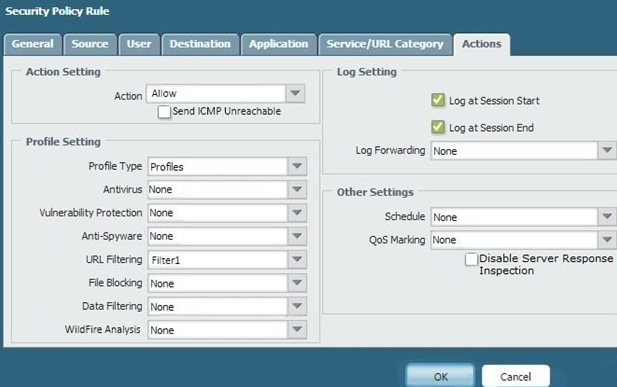
C.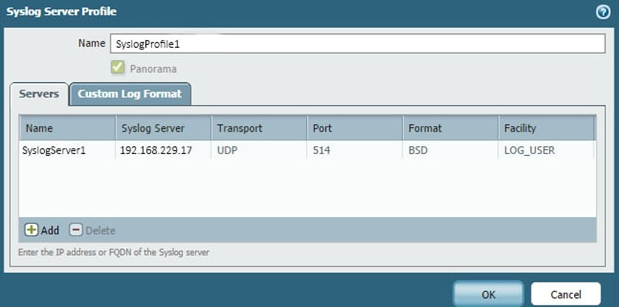
D.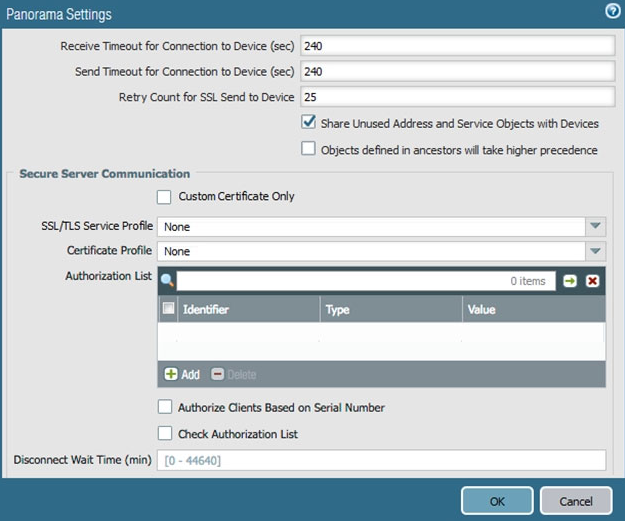
Answer:
b
Question 10
An engineer is configuring Packet Buffer Protection on ingress zones to protect from single-session DoS attacks. Which sessions does Packet Buffer Protection apply to?
- A. It applies to existing sessions and is not global
- B. It applies to existing sessions and is global
- C. It applies to new sessions and is global
- D. It applies to new sessions and is not global
Answer:
b
Answer is B and D