palo alto networks pccse practice test
Prisma Certified Cloud Security Engineer
Question 1
What improves product operationalization by adding visibility into feature utilization and missed opportunities?
- A. Alert Center
- B. Alarm Center
- C. Alarm Advisor
- D. Adoption Advisor
Answer:
d
Question 2
Which two options may be used to upgrade the Defenders with a Console v20.04 and Kubernetes deployment? (Choose two.)
- A. Run the provided curl | bash script from Console to remove Defenders, and then use Cloud Discovery to automatically redeploy Defenders.
- B. Remove Defenders DaemonSet, and then use Cloud Discovery to automatically redeploy the Defenders.
- C. Remove Defenders, and then deploy the new DaemonSet so Defenders do not have to automatically update on each deployment.
- D. Let Defenders automatically upgrade.
Answer:
ab
Question 3
Where can a user submit an external new feature request?
- A. Aha
- B. Help Center
- C. Support Portal
- D. Feature Request
Answer:
c
Question 4
A security team has a requirement to ensure the environment is scanned for vulnerabilities.
What are three options for configuring vulnerability policies? (Choose three.)
- A. individual actions based on package type
- B. output verbosity for blocked requests
- C. apply policy only when vendor fix is available
- D. individual grace periods for each severity level
- E. customize message on blocked requests
Answer:
bcd
Reference:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/19-11/prisma-cloud-compute-edition-admin/vulnerability_management/ vuln_management_rules.html
Question 5
What is the frequency to create a compliance report? (Choose two.)
- A. Weekly
- B. One time
- C. Monthly
- D. Recurring
Answer:
cd
Question 6
An administrator for Prisma Cloud needs to obtain a graphical view to monitor all connections, including connections across hosts and connections to any configured network objects.
Which setting does the administrator enable or configure to accomplish this task?
- A. ADEM
- B. WAAS Analytics
- C. Telemetry
- D. Cloud Native Network Firewall
- E. Host Insight
Answer:
d
Question 7
The security team wants to enable the block option under compliance checks on the host.
What effect will this option have if it violates the compliance check?
- A. The host will be taken offline.
- B. Additional hosts will be prevented form starting.
- C. Containers on a host will be stopped.
- D. No containers will be allowed to start on that host.
Answer:
b
Question 8
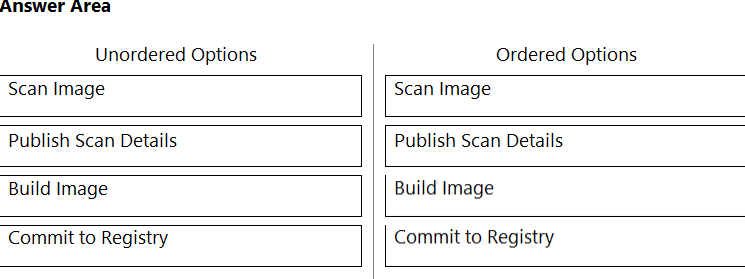
DRAG DROP What is the order of steps in a Jenkins pipeline scan?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
Select and Place:
Answer:
Question 9
Which three options are selectable in a CI policy for image scanning with Jenkins or twistcli? (Choose three.)
- A. Scope - Scans run on a particular host
- B. Credential
- C. Apply rule only when vendor fixes are available
- D. Failure threshold
- E. Grace Period
Answer:
bde
Question 10
Which three types of classifications are available in the Data Security module? (Choose three.)
- A. Personally identifiable information
- B. Malicious IP
- C. Compliance standard
- D. Financial information
- E. Malware
Answer:
cde