palo alto networks pccsa practice test
Palo Alto Networks Certified Cybersecurity Associate
Question 1
DRAG DROP
Match the attack definition to the type of security method used to protect against the attack.
Select and Place: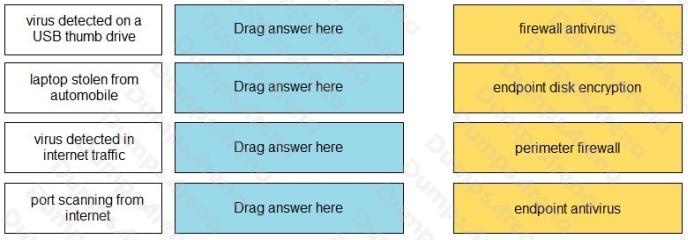
Answer:
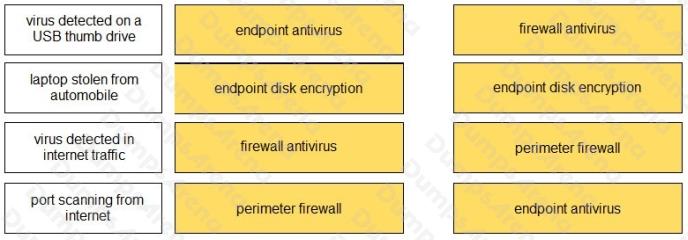
Question 2
When accessing an intranet website, a certificate error is received. What can be done to move past the certificate error and
ensure that the error is not received the next time the website is accessed?
- A. install the website certificate into the web browser
- B. request trusted access from the web developer
- C. enable TLS 2.0 in the advanced options of the web browser
- D. trust the web developer for the application
Answer:
A
Question 3
Which security component should be used to prevent a malware attack delivered by USB drive?
- A. endpoint security
- B. password security
- C. physical security
- D. firewall security
Answer:
C
Question 4
How does machine learning enhance WildFire operation?
- A. analyzes file sample characteristics during static analysis
- B. determines which file samples should be forwarded to WildFire
- C. determines the optimum OS WildFire uses to analyze file samples
- D. analyzes file sample characteristics during dynamic analysis
Answer:
D
Question 5
Which two components are part of a next-generation firewall security policy? (Choose two.)
- A. role-based access controls
- B. user identification
- C. content identification
- D. file permissions
Answer:
B C
Question 6
Which device would an Evil Twin attack use to lure the victim to connect to the attack surface network?
- A. switch
- B. firewall
- C. router
- D. access point
Answer:
D
Question 7
Which type of cloud computing service provides access to email and word processing applications running in a cloud
infrastructure?
- A. software as a service
- B. computing as a service
- C. platform as a service
- D. infrastructure as a service
Answer:
A
Question 8
Which type of malware is self-replicating but must first infect a host program and be executed by a user or process?
- A. vulnerability
- B. worm
- C. exploit
- D. virus
Answer:
B
Question 9
Which network method securely connects two sites across a public network?
- A. VPN
- B. VLAN
- C. switch
- D. router
Answer:
A
Question 10
Which component of a digital certificate provides authentication of the certificate’s issuer?
- A. digital signature
- B. certificate revocation list
- C. issuer’s private key
- D. certificate’s expiration date
Answer:
A
Question 11
What does a hypervisor enable?
- A. high-speed searching of already aggregated security log files
- B. high-speed aggregation and viewing of security log files
- C. multiple physical machines to be configured into a high-performance cluster
- D. multiple guest operating systems to run on a single physical machine
Answer:
D
Question 12
DRAG DROP
Match the OSI network model Layer 3 function to the correct description.
Select and Place: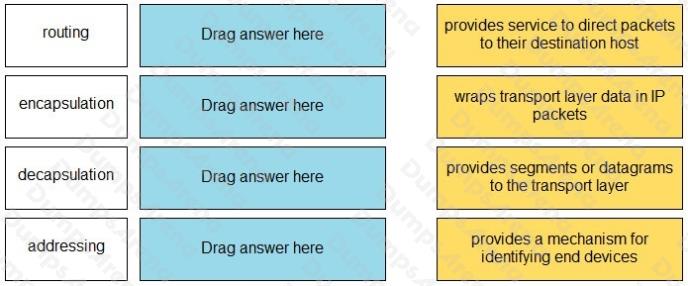
Answer:
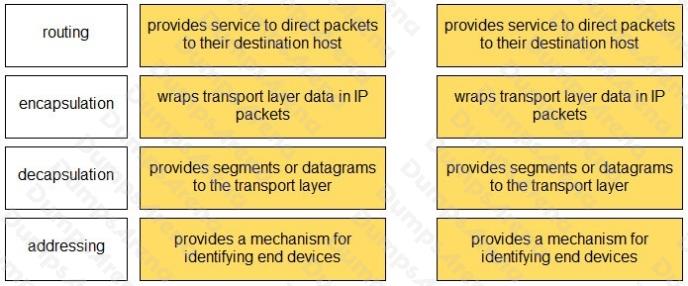
Question 13
Which two remote access methods are secure because they encrypt traffic? (Choose two.)
- A. IPsec-AH
- B. SSH
- C. VPN
- D. Telnet
- E. rlogin
Answer:
B C
Question 14
Which type of adversary would commit cybercrimes with the authorization of their country’s government?
- A. state-sponsored
- B. hacktivist
- C. gray hat
- D. white hat
Answer:
A
Question 15
Which protocol converts voice into a digital signal?
- A. IVO
- B. VoIP
- C. SNMP
- D. IGMP
Answer:
B