oracle 1z0-1104-25 practice test
Oracle Cloud Infrastructure 2025 Security Professional
Question 1
SIMULATION
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a
security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to
create or update a resource in the security zone if the action violates the attached Maximum Security
Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You
therefore, need to configure Custom Security Zones that allow the creation of compute instances in
the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the
requirement: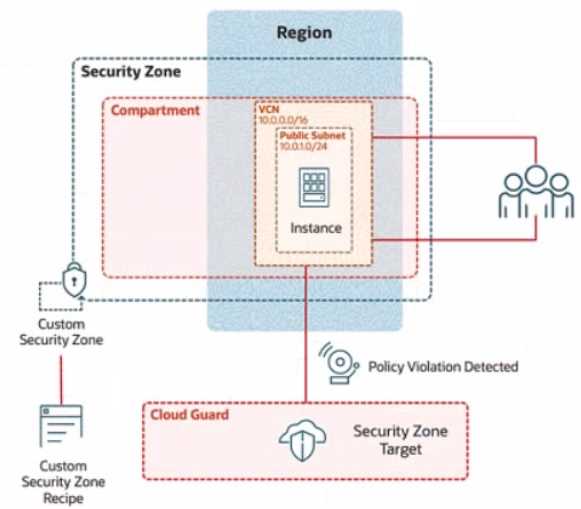
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 1: Create a Custom Security Zone Recipe
Create a Custom Security Zone Recipe named IAD-SP-PBT-CSP-01 that allows the provisioning of
compute instances in the public subnet.
Enter the OCID of the created custom security zone recipe in the text box below.
Answer:
See the
solution below in
Explanation.
Explanation:
To create a Custom Security Zone Recipe named IAD-SP-PBT-CSP-01 that allows the provisioning of
compute instances in a public subnet, we will follow the steps outlined in the Oracle Cloud
Infrastructure (OCI) Security Zones documentation. These steps are based on verified procedures
from the OCI Security Zone Guide and related resources.
Step-by-Step Solution for Task 1: Create a Custom Security Zone Recipe
Log in to the OCI Console:
Use your OCI credentials to log in to the OCI Console (
https://console.us-ashburn-
1.oraclecloud.com
).
Ensure you have access to the assigned compartment provided in the tenancy.
Navigate to Security Zones:
From the OCI Console, go to the navigation menu (hamburger icon) on the top left.
Under Governance and Administration, select Security Zones.
Create a New Security Zone Recipe:
In the Security Zones dashboard, click on the Recipes tab.
Click the Create Recipe button.
Configure the Recipe Details:
Name: Enter IAD-SP-PBT-CSP-01.
Description: (Optional) Add a description, e.g., "Custom recipe to allow compute instances in public
subnet."
Leave the Compartment as the assigned compartment provided.
Define the Security Zone Policy:
In the policy editor, start with a base policy. Since the Maximum Security Zone recipe restricts public
subnet usage, you need to customize it.
Add the following policy statement to allow compute instances in a public subnet:
Allow service compute to use virtual-network-family in compartment <compartment-name> where
ALL {
target.resource.type = 'Instance',
target.vcn.cidr_block = '10.0.0.0/16',
target.subnet.cidr_block = '10.0.10.0/24'
}
Replace <compartment-name> with the name of your assigned compartment.
This policy allows the Compute service to provision instances in the public subnet (10.0.10.0/24)
within the VCN (10.0.0.0/16).
Adjust Restrictions:
Ensure the recipe does not inherit the Maximum Security Zone recipe's default restrictions that block
public subnet usage. Explicitly allow the public subnet by including the subnet CIDR block
(10.0.10.0/24) in the policy.
Remove or modify any conflicting default rules that prohibit public subnet usage (e.g., rules blocking
internet access or public IP assignment).
Save the Recipe:
Click Create to save the custom security zone recipe.
Once created, note the OCID of the recipe from the recipe details page. The OCID will be a unique
identifier starting with ocid1.securityzonerecipe.
Verify the Recipe:
Go to the Recipes tab and locate IAD-SP-PBT-CSP-01.
Ensure the policy reflects the allowance for compute instances in the public subnet by reviewing the
policy statement.
OCID of the Created Custom Security Zone Recipe
The exact OCID will be generated upon creation (e.g., ocid1.securityzonerecipe.oc1..unique_string).
Please enter the OCID displayed in the OCI Console after completing Step 7.
Notes
Ensure IAM policies are correctly configured to grant you permissions to create and manage security
zone recipes in the compartment.
The policy assumes the public subnet CIDR (10.0.10.0/24) matches the diagram. Adjust if the actual
subnet CIDR differs.
Test the recipe by associating it with a security zone and attempting to launch a compute instance to
confirm compliance.
Question 2
SIMULATION
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a
security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to
create or update a resource in the security zone if the action violates the attached Maximum Security
Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You
therefore, need to configure Custom Security Zones that allow the creation of compute instances in
the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the
requirement:
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 2: Create a Security Zone
Create a security Zone named IAD_SAP-PBT-CSZ-01 in your assigned compartement and associate it
with the Custom Security Zone Recipe (IAD-SAP-PBT-CSP-01) created in the previous task.
Enter the OCID of the created Security zone in the box below.
Answer:
See the
solution below in
Explanation.
Explanation:
To create a Security Zone named IAD_SAP-PBT-CSZ-01 in your assigned compartment and associate it
with the Custom Security Zone Recipe IAD-SP-PBT-CSP-01 created in the previous task, follow these
steps based on the Oracle Cloud Infrastructure (OCI) Security Zones documentation.
Step-by-Step Solution for Task 2: Create a Security Zone
Log in to the OCI Console:
Use your OCI credentials to log in to the OCI Console (
https://console.us-ashburn-
1.oraclecloud.com
).
Ensure you have access to the assigned compartment.
Navigate to Security Zones:
From the OCI Console, click the navigation menu (hamburger icon) on the top left.
Under Governance and Administration, select Security Zones.
Create a New Security Zone:
In the Security Zones dashboard, click the Create Security Zone button.
Configure the Security Zone Details:
Name: Enter IAD_SAP-PBT-CSZ-01.
Compartment: Select the assigned compartment provided.
Description: (Optional) Add a description, e.g., "Security Zone for public subnet compute instances."
Associate the Custom Security Zone Recipe:
In the Recipe section, select the custom recipe IAD-SP-PBT-CSP-01 created in Task 1 from the
dropdown list.
Ensure the recipe is correctly associated to enforce the policy allowing compute instances in the
public subnet.
Define the Security Zone Scope:
Under Resources to Protect, select the compartment or specific resources (e.g., the VCN with CIDR
10.0.0.0/16 and public subnet 10.0.10.0/24) to apply the security zone.
Check the box to include all resources in the selected compartment if applicable.
Create the Security Zone:
Click Create to finalize the security zone creation.
Once created, note the OCID of the security zone from the security zone details page. The OCID will
be a unique identifier starting with ocid1.securityzone.
Verify the Security Zone:
Go to the Security Zones tab and locate IAD_SAP-PBT-CSZ-01.
Confirm the associated recipe (IAD-SP-PBT-CSP-01) and the applied policies.
OCID of the Created Security Zone
The exact OCID will be generated upon creation (e.g., ocid1.securityzone.oc1..<unique_string>).
Please enter the OCID displayed in the OCI Console after completing Step 7.
Question 3
SIMULATION
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a
security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to
create or update a resource in the security zone if the action violates the attached Maximum Security
Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You
therefore, need to configure Custom Security Zones that allow the creation of compute instances in
the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the
requirement: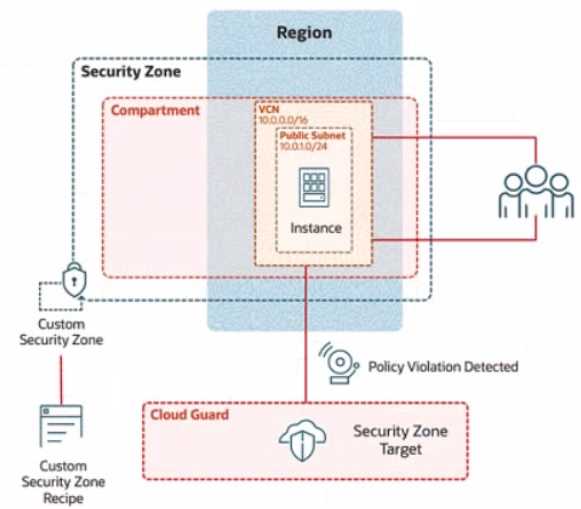
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task3: Create and configure a Virtual Cloud Network and Private Subnet
Create and configure virtual cloud Network (VCN) named IAD SP-PBT-VCN-01, with an internet
Gateway and configure appropriate route rules to allow external connectivity.
Enter the OCID of the created VCN in the text box below.
Answer:
See the
solution below in
Explanation.
Explanation:
To create and configure a Virtual Cloud Network (VCN) named IAD-SP-PBT-VCN-01 with an Internet
Gateway and appropriate route rules for external connectivity, follow these steps based on the
Oracle Cloud Infrastructure (OCI) Networking documentation.
Step-by-Step Solution for Task 3: Create and Configure a VCN and Private Subnet
Log in to the OCI Console:
Use your OCI credentials to log in to the OCI Console (
https://console.us-ashburn-
1.oraclecloud.com
).
Ensure you have access to the assigned compartment.
Navigate to Virtual Cloud Networks:
From the OCI Console, click the navigation menu (hamburger icon) on the top left.
Under Networking, select Virtual Cloud Networks.
Create a New VCN:
Click Start VCN Wizard and select Create VCN with Internet Connectivity.
VCN Name: Enter IAD-SP-PBT-VCN-01.
Compartment: Select the assigned compartment.
VCN CIDR Block: Enter 10.0.0.0/16 (matches the diagram's VCN CIDR).
Public Subnet CIDR Block: Enter 10.0.10.0/24 (matches the diagram's public subnet).
Accept the default settings for the public subnet and Internet Gateway creation.
Click Create to provision the VCN, Internet Gateway, and public subnet.
Verify the Internet Gateway:
After creation, go to the VCN details page for IAD-SP-PBT-VCN-01.
Under Resources, select Internet Gateways.
Ensure the Internet Gateway is attached and enabled.
Configure Route Rules:
In the VCN details page, under Resources, select Route Tables.
Select the default route table associated with the public subnet (10.0.10.0/24).
Click Add Route Rules.
Target Type: Select Internet Gateway.
Destination CIDR Block: Enter 0.0.0.0/0.
Target Internet Gateway: Select the Internet Gateway created with the VCN.
Click Add Route Rule to save.
Update Security List (if needed):
Under Resources, select Security Lists.
Edit the default security list for the public subnet.
Add an ingress rule:
Source CIDR: 0.0.0.0/0
IP Protocol: TCP
Source Port Range: All
Destination Port Range: 22 (for SSH) or as required by your application.
Add an egress rule:
Destination CIDR: 0.0.0.0/0
IP Protocol: All
Save the changes.
Note the VCN OCID:
Return to the VCN details page for IAD-SP-PBT-VCN-01.
Copy the OCID displayed (e.g., ocid1.vcn.oc1..<unique_string>).
OCID of the Created VCN
Enter the OCID of the created VCN (IAD-SP-PBT-VCN-01) into the text box. The exact OCID will be
available after Step 3 (e.g., ocid1.vcn.oc1..<unique_string>).
Question 4
SIMULATION
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a
security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to
create or update a resource in the security zone if the action violates the attached Maximum Security
Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You
therefore, need to configure Custom Security Zones that allow the creation of compute instances in
the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the
requirement: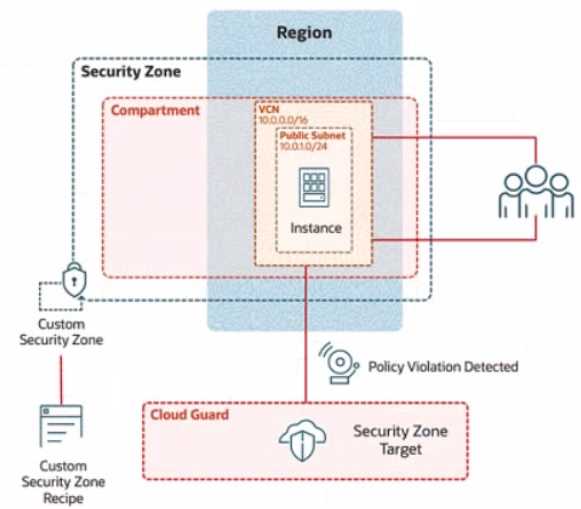
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 4: Create a Public Subnet
Create a public subnet named IAD-SP-PBT-PUBSNET-01, within the VCN IAD-SP-PBT-VCN-01
use a CIDR block of 10.0.1.0/24 and configure the subnet to use the internet Gateway
Answer:
See the
solution below in
Explanation.
Explanation:
To create a public subnet named IAD-SP-PBT-PUBSNET-01 within the VCN IAD-SP-PBT-VCN-01 using a
CIDR block of 10.0.1.0/24 and configure it to use the Internet Gateway, follow these steps based on
the Oracle Cloud Infrastructure (OCI) Networking documentation.
Step-by-Step Solution for Task 4: Create a Public Subnet
Log in to the OCI Console:
Use your OCI credentials to log in to the OCI Console (
https://console.us-ashburn-
1.oraclecloud.com
).
Ensure you have access to the assigned compartment.
Navigate to Virtual Cloud Networks:
From the OCI Console, click the navigation menu (hamburger icon) on the top left.
Under Networking, select Virtual Cloud Networks.
Select the VCN:
Locate and click on the VCN named IAD-SP-PBT-VCN-01 created in Task 3.
Under Resources, select Subnets.
Create a New Subnet:
Click the Create Subnet button.
Configure the Subnet Details:
Name: Enter IAD-SP-PBT-PUBSNET-01.
Compartment: Ensure it is set to the assigned compartment.
Subnet Type: Select Public Subnet.
CIDR Block: Enter 10.0.1.0/24.
Route Table: Select the default route table associated with the VCN (ensure it includes a route to the
Internet Gateway with destination 0.0.0.0/0).
Subnet Access: Select Public Subnet and ensure the Internet Gateway is associated.
DHCP Options: Leave as default or customize if required.
Security List: Use the default security list or create a new one with appropriate ingress/egress rules
(e.g., allow TCP port 22 for SSH and all egress traffic).
Associate the Internet Gateway:
Verify that the subnet is configured to route traffic through the Internet Gateway. This is
automatically handled if you selected the public subnet option and the VCN’s route table is correctly
set (as configured in Task 3).
If needed, edit the route table for the subnet to ensure a rule exists:
Destination CIDR Block: 0.0.0.0/0
Target Type: Internet Gateway
Target: Select the Internet Gateway associated with IAD-SP-PBT-VCN-01.
Create the Subnet:
Click Create to provision the subnet.
Once created, the subnet will be listed under the VCN’s subnets.
Verify the Configuration:
Go to the subnet details page for IAD-SP-PBT-PUBSNET-01.
Confirm the CIDR block is 10.0.1.0/24 and that it is a public subnet with Internet Gateway access.
Notes
Ensure the CIDR block 10.0.1.0/24 does not overlap with existing subnets in the VCN (10.0.0.0/16,
including 10.0.10.0/24 from Task 3).
The Internet Gateway association relies on the route table configuration from Task 3. If it’s missing,
update the route table as described in Step 6.
Question 5
SIMULATION
Challenge 2
In deploying a new application, a cloud customer needs to reflect different security postures. If a
security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to
create or update a resource in the security zone if the action violates the attached Maximum Security
Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You
therefore, need to configure Custom Security Zones that allow the creation of compute instances in
the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the
requirement: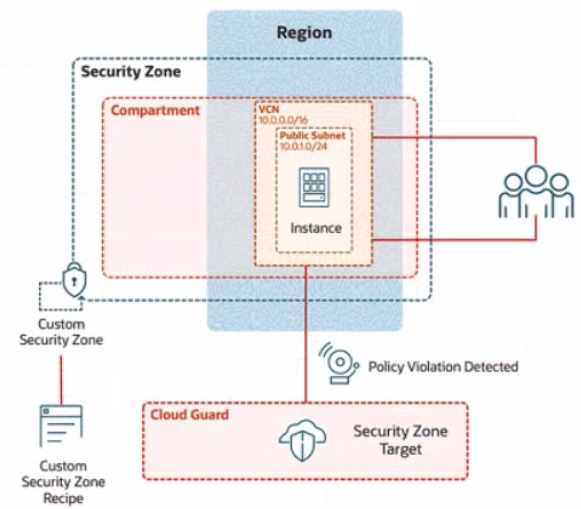
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 5: Provision a Compute Instance
Provision a compute instance in the IAD-SP-PBT-PUBSNET-01 public subnet, where:
Name IAD-SP-PBT-1-VM-01
image: Oracle Linux 8
Shape VM: Standard, A1, Flex
Enter the OCID of the created compute instance in the text box below.
Answer:
See the
solution below in
Explanation.
Explanation:
To provision a compute instance named IAD-SP-PBT-1-VM-01 in the IAD-SP-PBT-PUBSNET-01 public
subnet with the specified configuration (Oracle Linux 8 image, VM Standard A1 Flex shape), follow
these steps based on the Oracle Cloud Infrastructure (OCI) Compute documentation.
Step-by-Step Solution for Task 5: Provision a Compute Instance
Log in to the OCI Console:
Use your OCI credentials to log in to the OCI Console (
https://console.us-ashburn-
1.oraclecloud.com
).
Ensure you have access to the assigned compartment.
Navigate to Compute Instances:
From the OCI Console, click the navigation menu (hamburger icon) on the top left.
Under Compute, select Instances.
Create a New Compute Instance:
Click the Create Instance button.
Configure the Instance Details:
Name: Enter IAD-SP-PBT-1-VM-01.
Compartment: Select the assigned compartment.
Placement: Choose the availability domain (e.g., AD-1) based on your region’s availability.
Select the Image:
Under Image and Shape, click Change Image.
Select Oracle Linux 8 from the platform images list.
Click Select Image.
Choose the Shape:
Click Change Shape.
Select VM Standard category.
Choose A1 Flex from the shape options.
Configure the OCPUs (e.g., 1 OCPU) and memory (e.g., 6 GB) as needed for A1 Flex, then click Select
Shape.
Configure Networking:
Under Networking, ensure the Virtual Cloud Network is set to IAD-SP-PBT-VCN-01.
Set the Subnet to IAD-SP-PBT-PUBSNET-01 (public subnet with CIDR 10.0.1.0/24).
Enable Assign a public IPv4 address to allow external connectivity.
Leave the default security list or assign a custom one if configured previously.
Set Up SSH Access:
Under Add SSH Keys, either:
Upload your public SSH key file, or
Paste your public SSH key manually.
This ensures you can access the instance via SSH.
Launch the Instance:
Click Create to provision the compute instance.
Wait for the instance to reach the Running state (this may take a few minutes).
Note the Instance OCID:
Once the instance is running, go to the instance details page for IAD-SP-PBT-1-VM-01.
Copy the OCID displayed (e.g., ocid1.instance.oc1..<unique_string>).
OCID of the Created Compute Instance
Enter the OCID of the created compute instance (IAD-SP-PBT-1-VM-01) into the text box. The exact
OCID will be available after Step 9 (e.g., ocid1.instance.oc1..<unique_string>).
Notes
Ensure the security zone IAD_SAP-PBT-CSZ-01 and its associated recipe IAD-SP-PBT-CSP-01 allow
compute instance creation in the public subnet (10.0.1.0/24).
Verify network connectivity by testing SSH access using the public IP assigned to the instance.
Question 6
SIMULATION
Challenge 1 - Task 1
Integrate TLS Certificate Issued by the OCI Certificates Service with Load Balancer
You are a cloud engineer at a tech company that is migrating its services to Oracle Cloud
Infrastructure (OCI). You are required to set up secure communication for your web application using
OCI's Certificate service. You need to create a Certificate Authority (CA), issue a TLS/SSL server
certificate, and configure a load balancer to use this certificate to ensure encrypted traffic between
clients and the backend servers.
Review the architecture diagram, which outlines the resources you'll need to address the
requirement.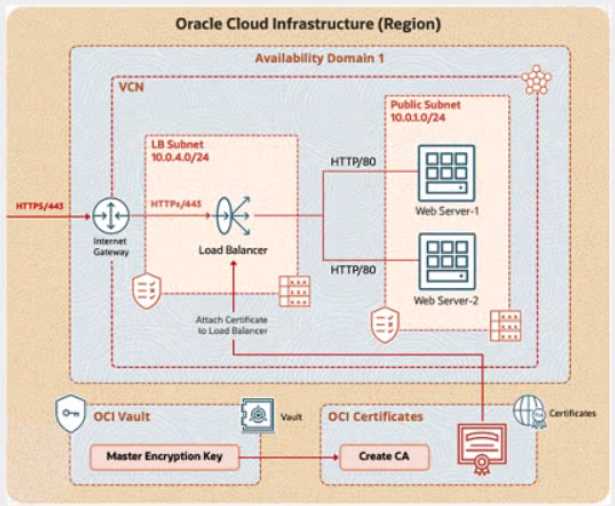
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
OCI Vault to store the secret required by the program, which is created in the root compartment as
PBI_Vault_SP
Task 1: Create and Configure a Virtual Cloud Network (VCN)
Create a Virtual Cloud Network (VCN) named PBT-CERT-VCN-01 with the following specifications:
VCN with a CIDR block of 10.0.0.0/16
Subnet 1 (Compute Instance):
Name: Compute-Subnet-PBT-CERT
CIDR Block: 10.0.1.0/24
Subnet 2 (Load Balancer):
Name: LB-Subnet-PBT-CERT-SNET-02
CIDR Block: 10.0.2.0/24
Internet Gateway for external connectivity
Route table and security lists:
Security List named PBT-CERT-CS-SL-01 for Subnet 1 (Compute-Subnet-PBT-CERT) to allow SSH (port
22) traffic
Security List named PBT-CERT-LB-SL-01 for Subnet 2 (LB-Subnet-PBT-CERT) to allow HTTPS (port 443)
traffic
"Enter the OCID of the created VCN in the text box below.
Answer:
See the
solution below in
Explanation.
Explanation:
Challenge 1: Integrate TLS Certificate Issued by the OCI Certificates Service with Load Balancer
Task 1: Create and Configure a Virtual Cloud Network (VCN)
Step 1: Create the Virtual Cloud Network (VCN)
Log in to the OCI Console.
Navigate to Networking > Virtual Cloud Networks.
Click Create Virtual Cloud Network.
Select VCN with Internet Connectivity (to include an Internet Gateway by default).
Enter the following details:
Name: PBT-CERT-VCN-01
Compartment: Select your assigned compartment.
VCN CIDR Block: 10.0.0.0/16
Leave other settings as default (e.g., create a new public subnet and route table).
Click Create Virtual Cloud Network. Wait for the VCN to be created.
Step 2: Create Subnet 1 (Compute-Subnet-PBT-CERT)
In the VCN details page for PBT-CERT-VCN-01, click Subnets under Resources.
Click Create Subnet.
Enter the following details:
Name: Compute-Subnet-PBT-CERT
Subnet Type: Regional
CIDR Block: 10.0.1.0/24
Route Table: Select the default route table created with the VCN.
Subnet Access: Public Subnet (to allow internet access).
DNS Resolution: Enabled.
Click Create.
Step 3: Create Subnet 2 (LB-Subnet-PBT-CERT-SNET-02)
In the VCN details page, click Subnets under Resources.
Click Create Subnet.
Enter the following details:
Name: LB-Subnet-PBT-CERT-SNET-02
Subnet Type: Regional
CIDR Block: 10.0.2.0/24
Route Table: Select the default route table created with the VCN.
Subnet Access: Public Subnet (to allow internet access for the load balancer).
DNS Resolution: Enabled.
Click Create.
Step 4: Verify Internet Gateway
In the VCN details page, under Resources, click Internet Gateways.
Ensure an Internet Gateway is listed and attached to PBT-CERT-VCN-01. If not created, click Create
Internet Gateway, name it (e.g., PBT-CERT-IGW), and attach it.
Step 5: Configure Route Table
In the VCN details page, under Resources, click Route Tables.
Select the default route table or create a new one named PBT-CERT-RT-01.
Click Add Route Rule. 4 - Destination CIDR Block: 0.0.0.0/0
Target Type: Internet Gateway
Target: Select the Internet Gateway created (e.g., PBT-CERT-IGW).
Click Add Route Rule and save.
Step 6: Create Security List for Subnet 1 (Compute-Subnet-PBT-CERT)
In the VCN details page, under Resources, click Security Lists.
Click Create Security List.
Enter the following:
Name: PBT-CERT-CS-SL-01
Compartment: Your assigned compartment.
Add the following ingress rule:
Source CIDR: 0.0.0.0/0 (allow from any source, adjust as per security needs)
IP Protocol: TCP
Source Port Range: All
Destination Port Range: 22 (for SSH)
Allows: Traffic
Click Create.
Step 7: Create Security List for Subnet 2 (LB-Subnet-PBT-CERT-SNET-02)
In the VCN details page, under Resources, click Security Lists.
Click Create Security List.
Enter the following:
Name: PBT-CERT-LB-SL-01
Compartment: Your assigned compartment.
Add the following ingress rule:
Source CIDR: 0.0.0.0/0 (allow from any source, adjust as per security needs)
IP Protocol: TCP
Source Port Range: All
Destination Port Range: 443 (for HTTPS)
Allows: Traffic
Click Create.
Step 8: Retrieve and Enter VCN OCID
Go to the VCN details page for PBT-CERT-VCN-01.
Copy the OCID from the VCN information section.
Enter the OCID in the provided text box.
Question 7
SIMULATION
Task 2: Create a Compute Instance and Install the Web Server
Create a compute instance, where:
Name: PBT-CERT-VM-01
Image: Oracle Linux 8
Shape: VM.Standard.A1.Flex
Subnet: Compute-Subnet-PBT-CERT
Install and configure Apache web server:
a.
Install Apache
sudo yum -y install httpd
b.
Enable and start Apache
sudo systemctl enable httpd
sudo systemctl restart httpd
2. Install and configure Apache web server:
a. Install Apache
sudo yum -y install httpd
b. Enable and start Apache
sudo systemctl enable httpd
sudo systemctl restart httpd
c. Configure firewall to allow HTTP traffic (port 80)
sudo firewall-cmd --permanent --add-port=80/tcp
sudo firewall-cmd --reload
d. Create an index.html file
sudo bash -c 'echo You are visiting Web Server 1 >> /var/www/html/index.html'
Enter the OCID of the created compute instance PBT-CERT-VM-01 in the text box below.
Answer:
See the
solution below in
Explanation.
Explanation:
Task 2: Create a Compute Instance and Install the Web Server
Step 1: Create the Compute Instance
Log in to the OCI Console.
Navigate to Compute > Instances.
Click Create Instance.
Enter the following details:
Name: PBT-CERT-VM-01
Compartment: Select your assigned compartment.
Placement: Leave as default or select an availability domain (e.g., Availability Domain 1).
Image: Click Change Image, select Oracle Linux 8, and confirm.
Shape: Click Change Shape, select VM.Standard.A1.Flex, and configure:
OCPUs: 1 (or adjust as needed)
Memory: 6 GB (or adjust as needed)
Networking:
Virtual Cloud Network: Select PBT-CERT-VCN-01.
Subnet: Select Compute-Subnet-PBT-CERT.
Leave public IP assignment enabled for internet access.
SSH Key: Provide your public SSH key (upload or paste) for secure access.
Click Create and wait for the instance to be provisioned.
Step 2: Connect to the Compute Instance
Once the instance is created, note the Public IP Address from the instance details page.
Use an SSH client to connect:
Command: ssh -i <private-key-file> opc@<public-ip-address>
Replace <private-key-file> with your private key path and <public-ip-address> with the instance’s
public IP.
Step 3: Install and Configure Apache Web Server
Install Apache:
Run: sudo yum -y install httpd
Enable and Start Apache:
Run: sudo systemctl enable httpd
Run: sudo systemctl restart httpd
Configure Firewall to Allow HTTP Traffic (Port 80):
Run: sudo firewall-cmd --permanent --add-port=80/tcpRun:sudofirewall-cmd--reloadCreateanindex.htmlFile:
Run: sudo bash -c 'echo "You are visiting Web Server 1" >> /var/www/html/index.html'
Step 4: Verify the Configuration
Open a web browser and enter http://<public-ip-address> to ensure the page displays "You are
visiting Web Server 1".
If needed, troubleshoot by checking Apache status: sudo systemctl status httpd.
Step 5: Retrieve and Enter the OCID
Go to the instance details page for PBT-CERT-VM-01 under Compute > Instances.
Copy the OCID (a long string starting with ocid1.instance., unique to your tenancy).
Enter the copied OCID exactly as it appears into the text box provided.
Notes
These steps are based on OCI Compute documentation and Oracle Linux 8 setup guides.
Ensure the security list PBT-CERT-CS-SL-01 allows inbound traffic on port 22 (SSH) and port 80 (HTTP)
if not already configured.
The OCID will be unique to your instance; obtain it from the OCI Console after creation
Question 8
SIMULATION
Task 3: Create a Master Encryption Key
Note: OCI Vault to store the key required by this task is created in the root compartment as
PBI_Vault_SP
Create an RSA Master Encryption Key (MEK), where:
Key name: PBT-CERT-MEK-01-<username>
For example, if your username is 99008677-lab.user01, then the MEK name should be PBT-CERT-
MEK-01990086771abuser01
Ensure you eliminate special characters from the user name.
Key shape: 4096 bits
Enter the OCID of the Master Encryption Key created in the provided text box:
Answer:
See the
solution below in
Explanation.
Explanation:
Task 3: Create a Master Encryption Key
Step 1: Access the OCI Vault
Log in to the OCI Console.
Navigate to Identity & Security > Vault.
Select the root compartment.
Locate and click on the vault named PBI_Vault_SP.
Step 2: Create the Master Encryption Key
In the PBI_Vault_SP vault details page, under Resources, click Keys.
Click Create Key.
Enter the following details:
Name: Replace <username> with your username (e.g., if your username is 99008677-lab.user01,
remove special characters like - and . to get 99008677labuser01, then use PBT-CERT-MEK-
0199008677labuser01).
Key Shape: Select RSA with 4096 bits.
Protection Mode: Select HSM (Hardware Security Module) if available, or Software if HSM is not
required (based on vault capabilities).
Compartment: Ensure it’s set to the root compartment (where PBI_Vault_SP resides).
Leave other settings (e.g., key usage) as default unless specified.
Click Create Key and wait for the key to be generated.
Step 3: Retrieve and Enter the OCID
After the key is created, go to the Keys section under PBI_Vault_SP.
Click on the key named PBT-CERT-MEK-01<username> (e.g., PBT-CERT-MEK-0199008677labuser01).
Copy the OCID (a long string starting with ocid1.key., unique to your tenancy) from the key details
page.
Enter the copied OCID exactly as it appears into the provided text box.
Task 4: Create a Certificate Authority (CA)
Create a certificate authority, where:
CA name: PBT-CERT-CA-01-<username>
For example, if your username is 99008677-lab.user01, then the certificate authority name should be
PBT-CERT-CA-01990086771abuser01
Ensure you eliminate special characters from the user name.
Common name: PBT-CERT-OCICA-01
Master Encryption Key: PBT-CERT-MEK-01 (created in the previous task)
Answer: See the solution below in Explanation.
Explanation:
Task 4: Create a Certificate Authority (CA)
Step 1: Access the OCI Vault
Log in to the OCI Console.
Navigate to Identity & Security > Vault.
Select the root compartment.
Locate and click on the vault named PBI_Vault_SP.
Step 2: Create the Certificate Authority
In the PBI_Vault_SP vault details page, under Resources, click Certificate Authorities.
Click Create Certificate Authority.
Enter the following details:
Name: Replace <username> with your username (e.g., if your username is 99008677-lab.user01,
remove special characters like - and . to get 99008677labuser01, then use PBT-CERT-CA-
0199008677labuser01).
Common Name: Enter PBT-CERT-OCICA-01.
Master Encryption Key: Select the PBT-CERT-MEK-01<username> key created in Task 3 (e.g., PBT-
CERT-MEK-0199008677labuser01).
Subject: Leave as default or adjust (e.g., Organization, Country) if required by your setup.
Validity Period: Set as needed (e.g., 10 years), or use the default.
Compartment: Ensure it’s set to the root compartment.
Click Create Certificate Authority and wait for the CA to be provisioned.
Step 3: Verify the Certificate Authority
After creation, go to the Certificate Authorities section under PBI_Vault_SP.
Confirm the CA PBT-CERT-CA-01<username> (e.g., PBT-CERT-CA-0199008677labuser01) is listed and
its status is active.
Question 9
SIMULATION
Task 5: Create a Certificate
Create a certificate, where:
Certificate name: PBT-CERT-01-<username>
For example, if your username is 99008677-lab.user01, then the certificate name should be PBT-
CERT-01990086771abuser01
Ensure you eliminate special characters from the user name.
Common name: PBT-CERT-OCICERT-01
Certificate Authority: PBT-CERT-CA-01 (created in the previous task)
Answer:
See the
solution below in
Explanation.
Explanation:
Since I can’t create resources or retrieve OCIDs directly in your OCI environment, I’ll provide a step-
by-step solution based on verified OCI documentation and best practices as of 02:30 PM BST on
Thursday, June 12, 2025. Follow these instructions precisely in the OCI Console or CLI, using the
preconfigured PBI_Vault_SP vault and the PBT-CERT-CA-01<username> Certificate Authority created
in the previous task. Replace <username> with your actual username (e.g., 99008677-lab.user01),
ensuring special characters are removed.
Task 5: Create a Certificate
Step 1: Access the OCI Vault
Log in to the OCI Console.
Navigate to Identity & Security > Vault.
Select the root compartment.
Locate and click on the vault named PBI_Vault_SP.
Step 2: Create the Certificate
In the PBI_Vault_SP vault details page, under Resources, click Certificates.
Click Create Certificate.
Enter the following details:
Name: Replace <username> with your username (e.g., if your username is 99008677-lab.user01,
remove special characters like - and . to get 99008677labuser01, then use PBT-CERT-
0199008677labuser01).
Common Name: Enter PBT-CERT-OCICERT-01.
Certificate Authority: Select the PBT-CERT-CA-01<username> CA created in Task 4 (e.g., PBT-CERT-
CA-0199008677labuser01).
Subject: Leave as default or adjust (e.g., Organization, Country) if required.
Validity Period: Set as needed (e.g., 1 year), or use the default.
Compartment: Ensure it’s set to the root compartment.
Click Create Certificate and wait for the certificate to be issued.
Step 3: Verify the Certificate
After creation, go to the Certificates section under PBI_Vault_SP.
Confirm the certificate PBT-CERT-01<username> (e.g., PBT-CERT-0199008677labuser01) is listed and
its status is active.
Question 10
SIMULATION
Task 6: Create Load Balancer and Attach Certificate
Create a Load Balancer with the name PBT-CERT-LB-01 in subnet LB-Subnet-PBT-CERT-SNET-02
Create a Listener for the load balancer, where:
Name: PBT-CERT-LB_LTSN_01
Protocol: HTTPS
Port: 443
Attach the certificate PBT-CERT-01-<username> to the load balancer
Attach the security list PBT-CERT-LB-SL-01 to subnet LB-Subnet-PBT-CERT-SNET-02
Answer:
See the
solution below in
Explanation.
Explanation:
Task 6: Create Load Balancer and Attach Certificate
Step 1: Create the Load Balancer
Log in to the OCI Console.
Navigate to Networking > Load Balancers.
Click Create Load Balancer.
Enter the following details:
Name: PBT-CERT-LB-01
Compartment: Select your assigned compartment.
Load Balancer Type: Select Public.
Virtual Cloud Network: Select PBT-CERT-VCN-01.
Subnet: Select LB-Subnet-PBT-CERT-SNET-02.
Shape: Choose a shape (e.g., 10 Mbps, adjust based on needs).
Click Next.
Leave backend sets and listeners as default for now (we’ll configure the listener next).
Click Create Load Balancer and wait for it to be provisioned.
Step 2: Create a Listener
Once the load balancer is created, go to the Load Balancers page and click on PBT-CERT-LB-01.
Under Resources, click Listeners.
Click Create Listener.
Enter the following details:
Name: PBT-CERT-LB_LTSN_01
Protocol: Select HTTPS.
Port: Enter 443.
Certificate: Click Add Certificate, then select the PBT-CERT-01<username> certificate (e.g., PBT-CERT-
0199008677labuser01) created in Task 5.
Leave other settings (e.g., SSL handling) as default unless specified.
Click Create.
Step 3: Configure the Backend Set
In the PBT-CERT-LB-01 details page, under Resources, click Backend Sets.
Click Create Backend Set (if not already created).
Enter basic details (e.g., name like PBT-CERT-BS-01).
Add a backend server:
IP Address: Use the private IP of PBT-CERT-VM-01 (find this in the instance details under Compute >
Instances).
Port: 80 (HTTP, as configured on the web server).
Protocol: HTTP.
Click Create.
Step 4: Attach the Security List to the Subnet
Navigate to Networking > Virtual Cloud Networks.
Select PBT-CERT-VCN-01 and click Subnets.
Click on LB-Subnet-PBT-CERT-SNET-02.
Under Security Lists, ensure PBT-CERT-LB-SL-01 is attached. If not:
Click Edit.
Remove the default security list and add PBT-CERT-LB-SL-01.
Click Save Changes.
Step 5: Verify the Configuration
Ensure the load balancer health status is OK (check under Backend Sets > Health).
Test by accessing https://<load-balancer-public-ip> in a browser (replace with the public IP from the
load balancer details).
Question 11
SIMULATION
Task 7: Verify the OCI Certificate with Load Balancer
Verify HTTPS connection to the load balancer by running the following command in Cloud Shell
curl -k https://<Public IP of PBT-CERT-LB-01>
Enter the following URL in the web browser:
https://<Public IP of PBT-CERT-LB-01>
If prompted with a certificate error, accept the risk and continue.
Verify web page content by ensuring the text, "You are visiting Web Server 1" from the index.html
file is displayed in the browser
Answer:
See the
solution below in
Explanation.
Explanation:
Task 7: Verify the OCI Certificate with Load Balancer
Step 1: Obtain the Public IP of the Load Balancer
Log in to the OCI Console.
Navigate to Networking > Load Balancers.
Click on PBT-CERT-LB-01.
Note the Public IP Address from the load balancer details page.
Step 2: Verify HTTPS Connection Using Cloud Shell
Open the OCI Cloud Shell from the top-right corner of the OCI Console.
Run the following command, replacing <Public IP of PBT-CERT-LB-01> with the public IP you noted:
curl -k https://<Public IP of PBT-CERT-LB-01>
Expected output: You should see the text "You are visiting Web Server 1" if the connection is
successful. The -k flag ignores certificate validation errors (common during initial testing with self-
signed or newly issued certificates).
If you encounter an error, ensure the load balancer is active, the listener is configured correctly, and
the backend server (PBT-CERT-VM-01) is reachable.
Step 3: Verify in a Web Browser
Open a web browser.
Enter the following URL, replacing <Public IP of PBT-CERT-LB-01> with the public IP you noted:
https://<Public IP of PBT-CERT-LB-01>
If prompted with a certificate warning (e.g., due to a self-signed certificate or untrusted CA), accepttheriskandproceed(click"Advanced"and"Proceed"orsimilar,dependingonyourbrowser).Verifythatthewebpagedisplaysthetext"YouarevisitingWebServer1"fromtheindex.htmlfile
created on PBT-CERT-VM-01.
Step 4: Troubleshoot (if needed)
If the text is not displayed:
Check the load balancer health status under Backend Sets > Health in the OCI Console.
Ensure the security list PBT-CERT-LB-SL-01 allows port 443 and the compute instance security list
allows port 80.
Verify the Apache service is running on PBT-CERT-VM-01 by SSHing in and running sudo systemctl
status httpd.
Topic 2, Misc. Questions
Question 12
An E-commerce company running on Oracle Cloud Infrastructure (OCI) wants to prevent accidental
misconfigurations that could expose sensitive data. They need an OCI service that can enforce
predefined security rules when creating or modifying cloud resources.
Which OCI service should they use?
- A. OCI Web Application Firewall (WAF)
- B. OCI Identity and Access Management (IAM)
- C. OCI Security Zone
- D. OCI Certificates
Answer:
C
Question 13
According to the Oracle Cloud Infrastructure (OCI) Shared Responsibility Model, which statement
accurately reflects OCI's responsibility for security?
- A. OCI is responsible for securing the underlying infrastructure but not customer data.
- B. Customers are responsible for securing both infrastructure and data.
- C. OCI has no security responsibilities; customers need to secure their resources.
- D. OCI provides security only for free-tier services; customers secure everything else.
Answer:
A
Question 14
In Oracle Cloud Infrastructure (OCI), bare metal instances provide customers with direct access to the
underlying hardware. To mitigate security risks when a customer terminates a bare metal instance,
OCI utilizes Root-of-Trust hardware.
What is the primary function of the Root-of-Trust hardware in this context?
- A. It automatically encrypts data at rest on the bare metal instance.
- B. It ensures all non-volatile memory on the terminated instance is securely wiped before reuse.
- C. It guarantees complete isolation between customer workloads on different instances.
- D. It eliminates the need for hypervisors, reducing the potential attack surface.
Answer:
B
Question 15
You have created a compartment TEST in your subscribed tenancy. Then, you created two groups,
test1 and test2, and want the users in these groups to be able to manage all the resources in the
TEST compartment.
Which policy would you use to achieve this?
- A. Allow group /test*/ to manage all resources in compartment test.
- B. Allow group test1, test2 to manage all resources in compartment test.
- C. Allow any-user to manage all resources in compartment test where any {request.groups.test1, test2}
- D. Allow any-user to manage all resources in compartment test where request.group='test*'
Answer:
B