oracle 1z0-1085-21 practice test
Oracle Cloud Infrastructure Foundations 2021 Associate Exam
Question 1
Which feature allows you to group and logically isolate your Oracle Cloud Infrastructure(OCI)
resources?
- A. Tenancy
- B. Identity and Access Management Groups
- C. Availability Domains
- D. Compartments
Answer:
D
Explanation:
It is collection ofrelatedresources.Compartmentsare a fundamental component of Oracle Cloud
Infrastructure for organizing and isolating your cloud resources. You use them to clearly separate
resources for the purposes of measuring usage and billing, access (through the use of IAM Service
policies), and isolation (separating the resources for one project or business unit from another). A
common approach is to create a compartment for each major part of your organization. For more
information, see
Overview of the IAM Service
and also
Setting Up Your Tenancy
.
To place a resource in a compartment, simply specify the compartment ID in the "Create" request
object when initially creating the resource. For example, to launch an instance into a particular
compartment, specify that compartment's OCID in the LaunchInstance request. You can't move an
existing resource from one compartment to another.
To use any of the API operations, you must be authorized in an IAM policy. If you're not authorized,
talk to an administrator. If you're an administrator who needs to write policies to give users access,
see
Getting Started with Policies
.
Reference:
https://docs.cloud.oracle.com/en-us/iaas/tools/oci-cli/2.9.9/oci_cli_docs/cmdref/iam/compartment.html
Question 2
What is Oracle's responsibility according to the Oracle Cloud Infrastructure (OCI)shared-security
model?
- A. Functions
- A. Configuring OCI services securely
- B. Block Volume
- B. Data classification and compliance
- C. Object Storage
- C. Securing application workloads
- D. Auto Scaling
- D. Security of data center facilities
- E. Identity and Access Management
- F. File Storage
Answer:
D
Explanation:
Oracles mission is to build cloud infrastructure and platform services for your business to have
effective and manageable security to run your mission-critical workloads and store your data with
confidence.
Oracle Cloud Infrastructure offers best-in-class security technology and operational processes to
secure its enterprise cloud services. However, for you to securely run your workloads in Oracle Cloud
Infrastructure, you must be aware of your security and compliance responsibilities. By design, Oracle
provides security of cloud infrastructure and operations (cloud operator access controls,
infrastructure security patching, and so on), and you are responsible for securely configuring your
cloud resources. Security in the cloud is a shared responsibility between you and Oracle.
In ashared, multi-tenant compute environment, Oracle is responsible for the security of the
underlying cloud infrastructure (such as data-center facilities, and hardware and software systems)
and you are responsible for securing your workloads and configuring your services (such as compute,
network, storage, and database) securely.
In a fully isolated, single-tenant, bare metal server with no Oracle software on it, your responsibility
increases as you bring the entire software stack (operating systems and above) on which you deploy
your applications. In this environment, you are responsible for securing your workloads, and
configuring your services (compute, network, storage, database) securely, and ensuring that the
software components that you run on the bare metal servers are configured, deployed, and managed
securely.
More specifically, your and Oracle's responsibilities can be divided into the following areas: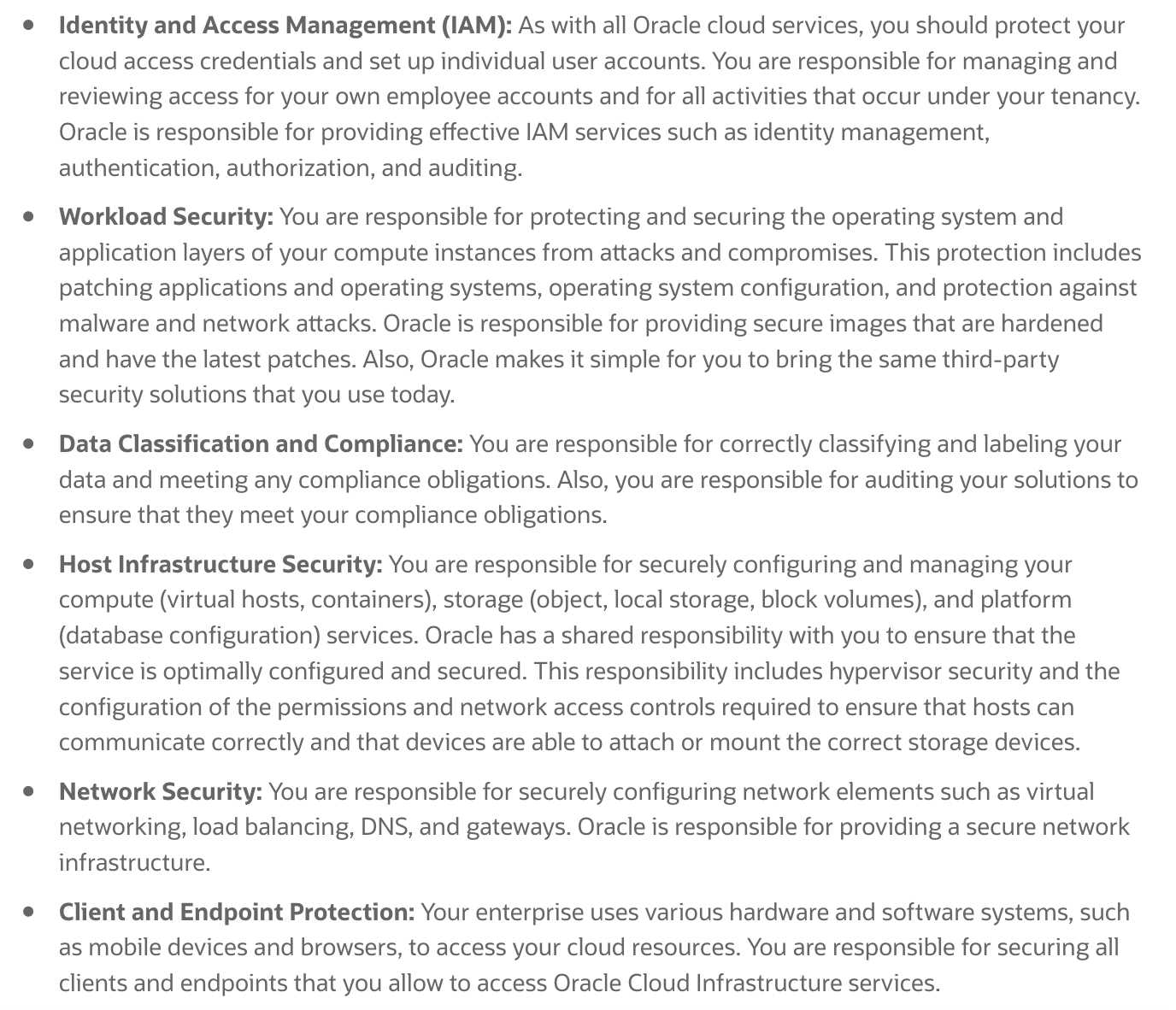

Reference:
https://docs.cloud.oracle.com/en-
us/iaas/Content/Security/Concepts/security_overview.htm
Question 3
Which two situations incur costs in Oracle Cloud Infrastructure (OCI)?
- A. ensuring your solution components are distributed across OCI Fault Domains
- A. Data ingress from the internet
- B. performing data integrity check when using OCI File StorageService
- B. Transferring data across regions
- C. writing custom scripts that will monitor your solution
- C. Transferring data from one instance to another in the same Availibility Domain
- D. using multiple OCI Availability Domains (AD), where available, to deploy your solution
- D. Data egress to the internet
- E. creating a manual cluster of compute instances
- E. Transferring data from one instance to another across different Availibility Domains in a Region
Answer:
BD
Question 4
You have an application that requires a shared file system. Which of the following services would you
use?
- A. File Storage
- B. Local NVMe
- B. Archive Storage
- C. Object Storage
- D. Block Volume
Answer:
A
Explanation:
Oracle Cloud InfrastructureFile Storage serviceprovides a durable, scalable, secure, enterprise-grade
network file system. You can connect to a File Storage service file system from any bare metal, virtual
machine, or container instance in your Virtual Cloud Network (VCN). You can also access a file system
from outside the VCN using Oracle Cloud Infrastructure FastConnect and Internet Protocol security
(IPSec) virtual private network (VPN).
Large Compute clusters ofthousandsof instances can use the File Storage service for high-
performance shared storage. Storage provisioning is fully managed and automatic as your use scales
from a single byte to exabytes without upfront provisioning.
The File Storage service supports the Network File System version 3.0(NFSv3)protocol. The service
supports the Network Lock Manager (NLM) protocol for file locking functionality.
Oracle Cloud Infrastructure File Storage employs5-wayreplicated storage, located in different fault
domains, to provide redundancy for resilient data protection. Data is protected with erasure
encoding.
The File Storage service uses the"eventual overwrite"method of data eradication. Files are created
in the file system with a unique encryption key. When you delete a single file, its associated
encryption key is eradicated, making the file inaccessible. When you delete an entire file system, the
file system is marked as inaccessible. The service systematically traverses deleted files and file
systems, frees all the used space, and eradicates all residual files.
Use the File Storage service when your application or workload includes big data and analytics,
media processing, or content management, and you require Portable Operating System Interface
(POSIX)-compliant file system access semantics and concurrently accessible storage. The File Storage
service is designed to meet the needs of applications and users that need an enterprise file system
across a wide range of use cases, including the following:
Reference:
https://docs.cloud.oracle.com/en-
us/iaas/Content/File/Concepts/filestorageoverview.htm
Question 5
Which Oracle Cloud Infrastructure compute shapes does not incur instance billing in a
STOPPEDstate?
- A. Support for RAC DB systems
- A. Dense I/O
- B. No need to create database Indices
- B. Standard
- C. Automated backups to OCI Block Volume
- C. GPU
- D. Automated disaster recovery
- D. HPC
Answer:
B
Explanation:
Explanation
A shape is a template that determines the number of CPUs, amount of memory, and other resources
that are allocated to an instance.
Standard shapes don't incur costs in a STOPPEDstate.
Reference:
https://docs.cloud.oracle.com/en-
us/iaas/Content/Compute/References/computeshapes.htm#baremetalshapes__bm-standard
Question 6
Which of the following services can you control access to via IAM?
- A. OCI virtual or Bare Metal DB Systems
- A. Networking components
- B. OCI Streaming Service
- B. Compute Instances
- C. Object Storage Service
- C. All services including IAM
- D. Virtual Machine (VM) or Bare Metal (BM) compute Instances
- D. DB systems
- E. File Storage Service
- F. Oracle Container Engine for Kubernetes
Answer:
C
Explanation:
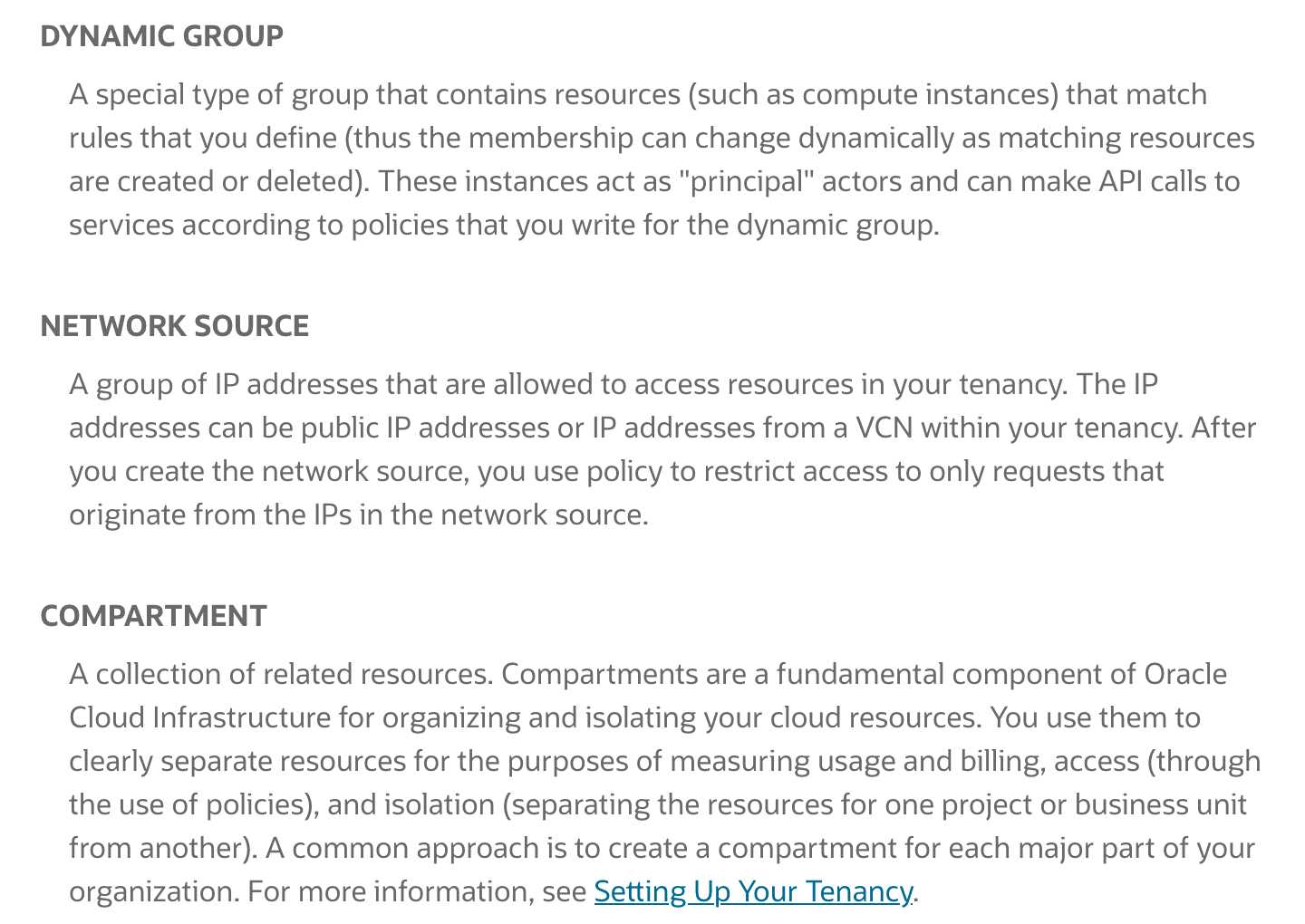
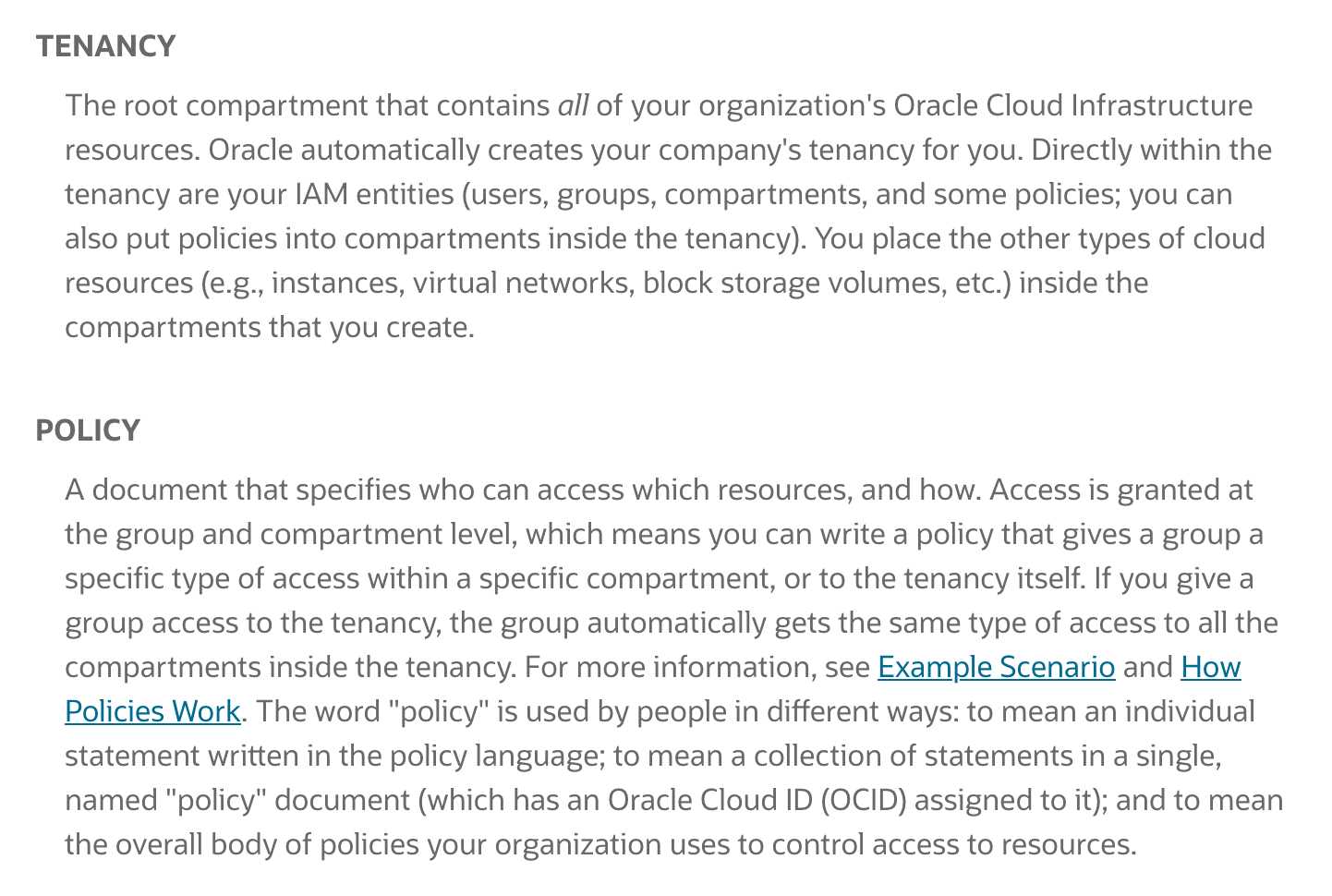
Oracle Cloud Infrastructure Identity and Access Management (IAM) lets you control who has access
to your cloud resources. You can control what type of access a group of users have and to which
specific resources. This section gives you an overview of IAM components and an example scenario
to help you understand how they work together.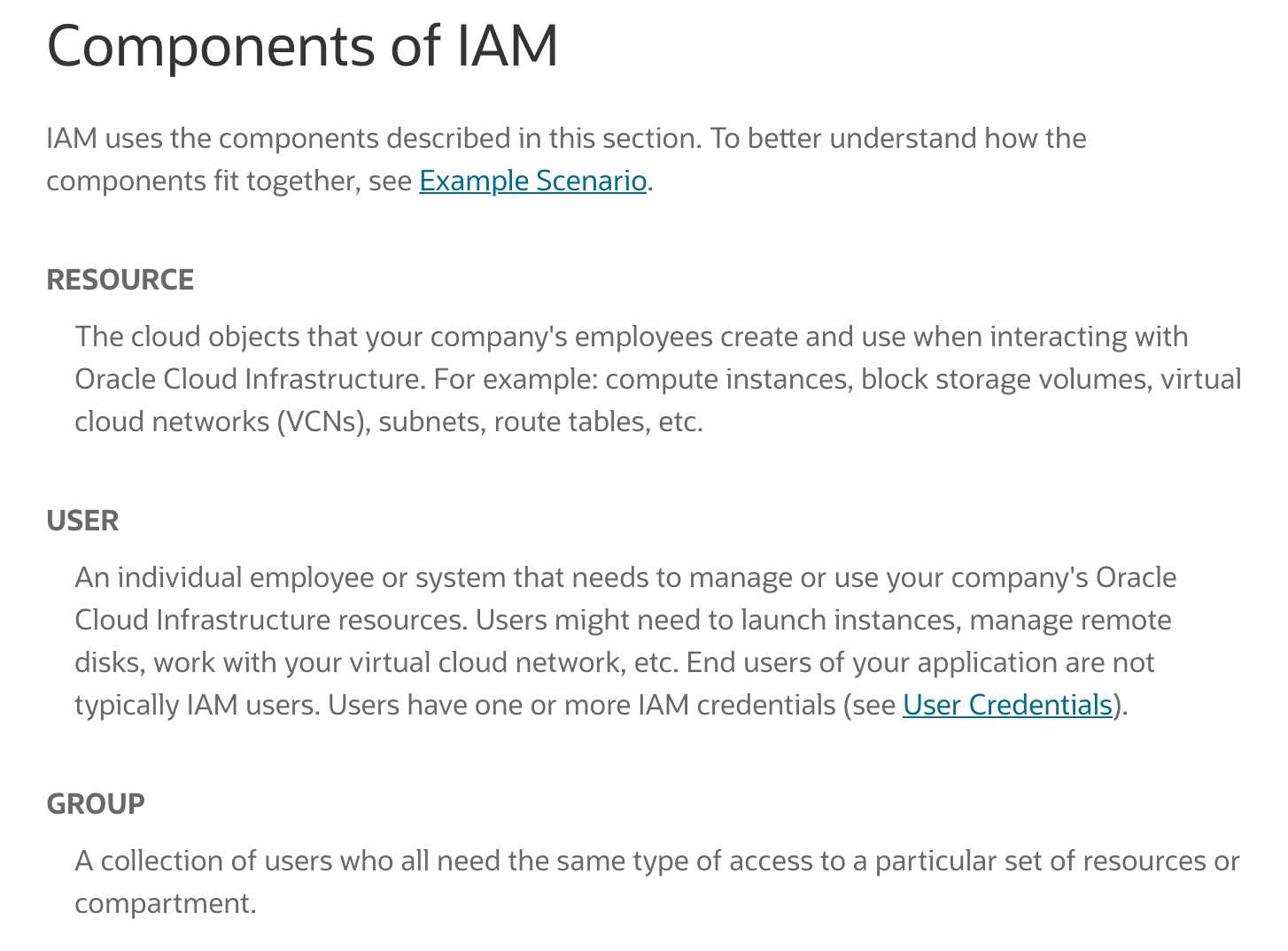
Reference:
https://docs.cloud.oracle.com/en-us/iaas/Content/Identity/Concepts/overview.htm
Question 7
Which option provides the best performance for running OLTPworkloads in Oracle Cloud
Infrastructure?
- A. Use API endpoints to create resources in the desired region.
- A. OCI Exadata DB Systems
- B. Navigate to the desired region and begin creating resources.
- B. OCI Autonomous Data Warehouse
- C. Subscribe to the desired region.
- C. OCI Virtual Machine Instance
- D. File a service request for access to each additional region.
- D. OCI Dedicated Virtual Host
Answer:
A
Explanation:
Explanation
On an Exadata DB system, all databases share dedicated storage servers which include flash storage.
By default, the databases are given equal priority with respect to these resources. The Exadata
storage management software uses a first come, first served approach for query processing. If a
database executes a major query that overloads I/O resources, overall system performance can be
slowed down.
The I/O Resource Management (IORM) allows you to assign priorities to your databases to ensure
critical queries are processed first when workloads exceed their resource allocations. You assign
priorities by creating directives that specify the number of shares for each database. The number of
shares corresponds to a percentage of resources given to that database when I/O resources are
stressed.
Directives work together with an overall optimization objective you set for managing the resources.
The following objectives are available:
1) Auto- Recommended. IORM determines the optimization objective and continuously and
dynamically determines the optimal settings, based on the workloads observed, and resource plans
enabled.
2) Balanced- For critical OLTP and DSS workloads. This setting balances low disk latency and high
throughput. This setting limits disk utilization of large I/Os to a lesser extent than low latency to
achieve a balance between good latency and good throughput.
3) High throughput- For critical DSS workloads that require high throughput.
4)Low latency- For critical OLTP workloads. This setting provides the lowest possible latency by
significantly limiting disk utilization.
Reference:
https://docs.cloud.oracle.com/en-
us/iaas/Content/Database/Tasks/examanagingiorm.htm
Question 8
Which OCI storage service does not provide encryption for data at rest?
- A. OCI Bare Metal DB Systems
- A. File Storage
- B. OCI Virtual Machine DB Systems
- B. Block Volume
- C. OCI Exadata DB Systems.
- C. Local NVMe
- D. OCI Autonomous Database
- D. Object Storage
Answer:
C
Explanation:
NVMe stands for non-volatile memory express. It is a storage protocol created to fasten the transfer
of data between enterprise and client systems and solid-state drives (SSDs) over a computers high-
speed Peripheral Component Interconnect Express bus. The characteristics are:
1) Local NVMe is NVMe SSD-based temporary storage.
2) It is the locally-attached NVMe devices to the OCI compute instance
3) It is used very high storage performance requirements, lots of throughput, lots of IOPS, local
storage and when you dont want to go out on network
4) Oracle does not protect in any way through RAID, or snapshots, or backup out of the box and data
is not encrypted at rest.
Reference:
https://techgoeasy.com/local-nvme-storage-oci/
Question 9
Which statement about the Oracle Cloud Infrastructure (OCI) shared-security model is true?
- A. Resource Manager
- A. You are responsible for securing all data that you place in OCI
- B. Events
- B. You are not responsible for any aspect of security in OCI
- C. Compartment Explorer
- C. You are responsible for securing the hypervisor within OCI compute service
- D. Oracle Functions
- D. You are responsible for managing security controls within the physical OCI network
Answer:
A
Explanation:
Explanation
Oracle Cloud Infrastructure offers best-in-class security technology and operational processes to
secure its enterprise cloud services. However, for you to securely run your workloads in Oracle Cloud
Infrastructure, you must be aware of your security and compliance responsibilities. By design, Oracle
provides security of cloud infrastructure and operations (cloud operator access controls,
infrastructure security patching, and so on), and you are responsible for securely configuring your
cloud resources. Security in the cloud is a shared responsibility between you and Oracle.
In a shared, multi-tenant compute environment, Oracle is responsible for the security of the
underlying cloud infrastructure (such as data-center facilities, and hardware and software systems)
and you are responsible for securing your workloads and configuring your services (such as compute,
network, storage, and database) securely.
In a fully isolated, single-tenant, bare metal server with no Oracle software on it, your responsibility
increases as you bring the entire software stack (operating systems and above) on which you deploy
your applications. In this environment, you are responsible for securing your workloads, and
configuring your services (compute, network, storage, database) securely, and ensuring that the
software components that you run on the bare metal servers are configured, deployed, and managed
securely.
The responsibilities can be divided as: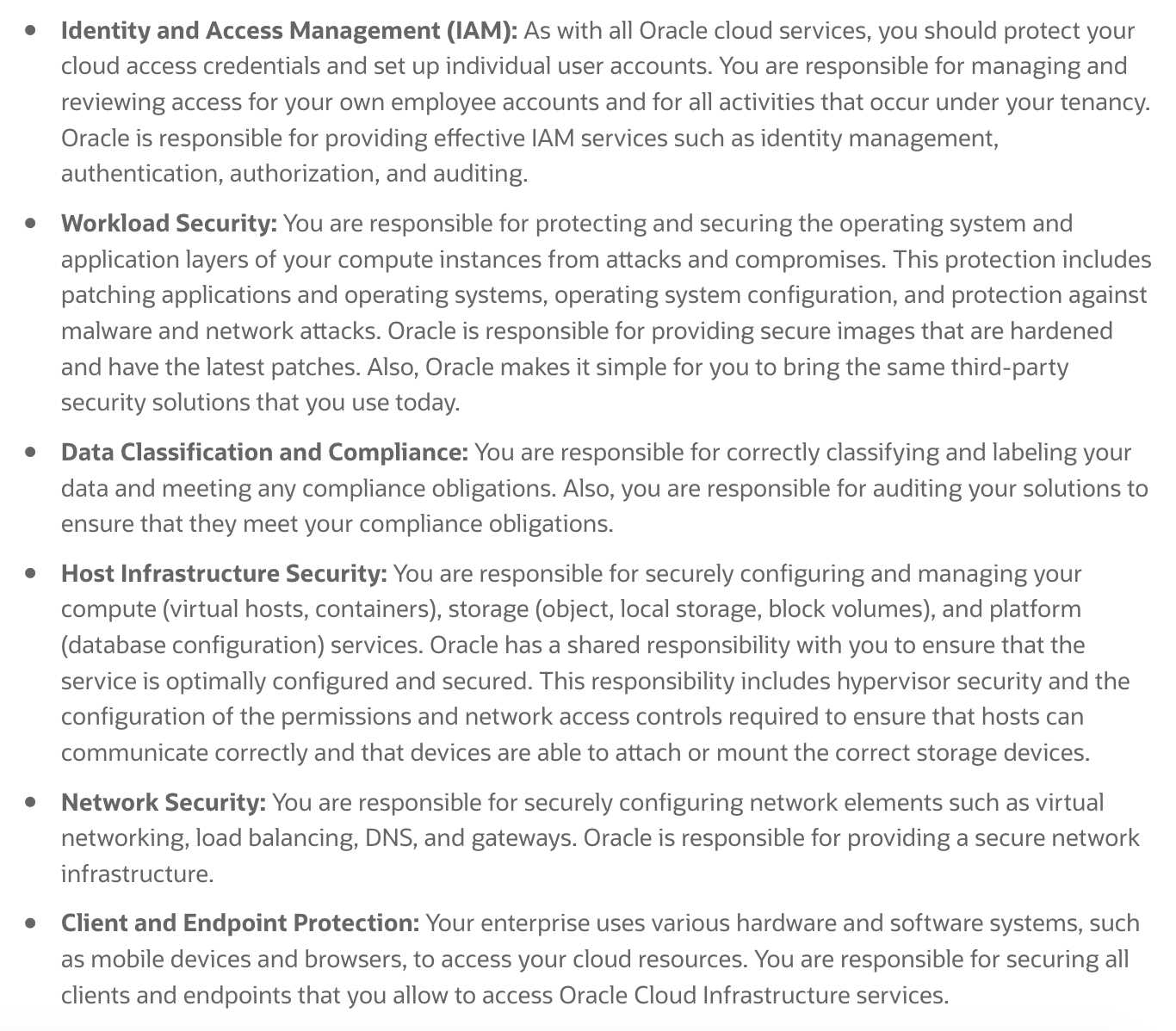
Reference:
https://docs.cloud.oracle.com/en-
us/iaas/Content/Security/Concepts/security_overview.htm
Question 10
You run 5 Oracle Cloud Infrastructure (OCI)Virtual Machine instances on an OCIdedicated virtual
host. How will this deployment be billed?
- A. Public internet
- A. Only the dedicated virtual machine host will be billed
- B. Virtual Cloud Network Remote Peering
- B. The dedicated virtual machine host and the boot volumes of each instance will be billed
- C. OCI FastConnact
- C. The dedicated virtual machine host all 5 instances, and the boot volume of each instance will be billed
- D. IPSec Virtual Private Network (VPN)
- D. All 5 instances will be billed on the basis of the number of OCPUs
Answer:
B
Explanation:
You must create a dedicated virtual machinehostbefore you can place any instances on it. When
creating the dedicated virtual machine host, you select an availability domain and fault domain to
launch it in. All the VM instances that you place on the host will subsequently be created in this
availability domain and fault domain. You also select a compartment when you create the dedicated
virtual machine host, but you can move the host to a new compartment later without impacting any
of the instances placed on it. You can also create the instances in a different compartment than the
dedicated virtual machine host, or move them to difference compartments after they have been
launched.
You are billed for the dedicated virtual machine host as soon as you create it, but you are not billed
for any of the individual VM instances you place on it. You will still be billed for image licensing costs
if they apply to the image you are using for the VM instances.
Read
more:
https://docs.cloud.oracle.com/en-
us/iaas/Content/Compute/Concepts/dedicatedvmhosts.htm
Question 11
Which SLA type is not offered by Oracle Cloud Infrastructure compute service?
- A. Always on data encryption for data-at-rest.
- A. Data Plane
- B. Certificate Management service
- B. Performance Plane
- C. Captcha
- C. Service Plane
- D. Key Management service
- D. Control Plane
- E. Managed Active Directory service
Answer:
C
Explanation:
Service Plane isNOTan SLA provided by OCI. See the table below: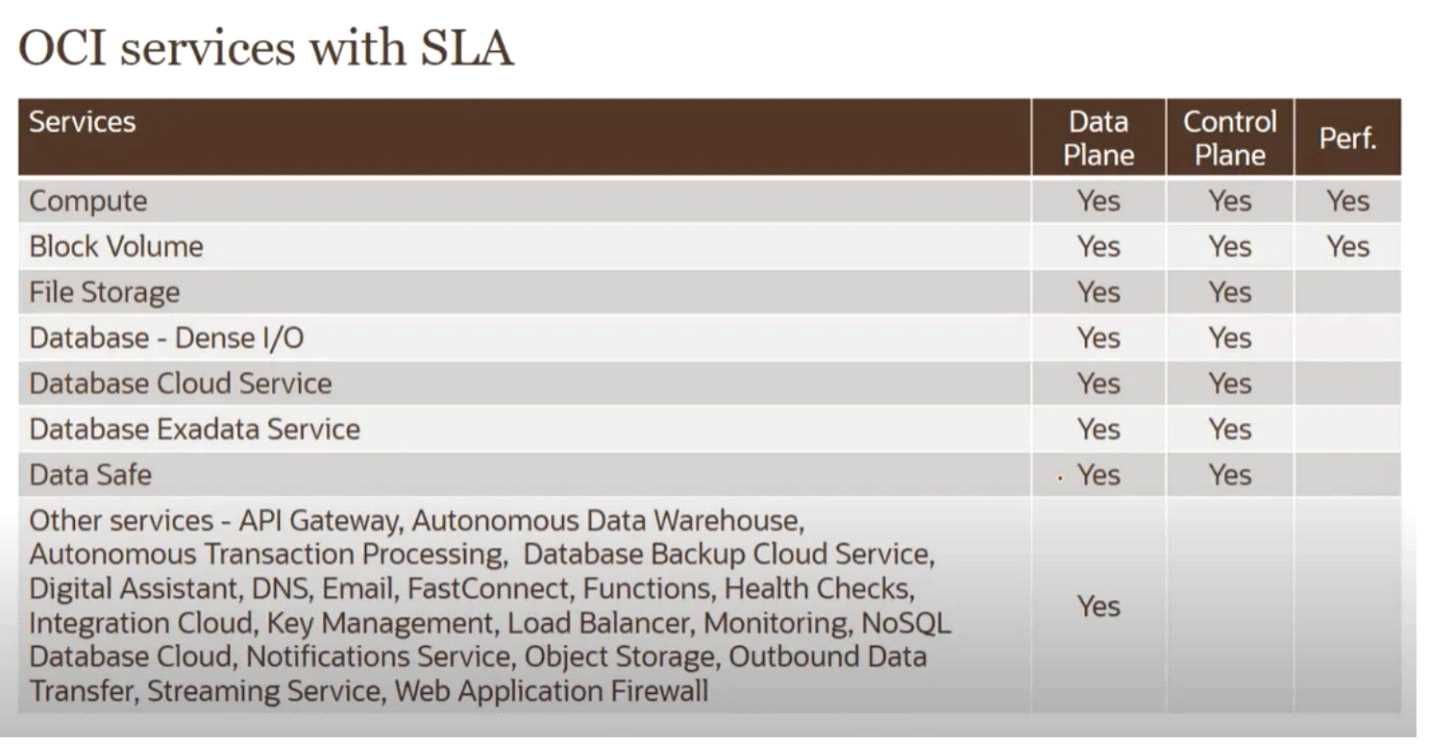
Reference:
https://k21academy.com/1z0-1085/service-level-agreement-sla-in-oracle-cloud-oci/
Question 12
Which of the following is an example of an edge service in OCI?
- A. stopping/starting the instance
- A. DNS Zone Management
- B. backing up data to object storage
- B. Virtual Machines
- C. adding additional compute instances
- C. OCI compute instances
- D. changing compute instance size
- D. Oracle Data Guard
Answer:
A
Explanation:
The Oracle Cloud Infrastructure Domain Name System (DNS) service lets you
create and manage your
DNS zones
. You can create zones, add records to zones, and allow Oracle Cloud Infrastructure's edge
network to handle your domain's DNS queries.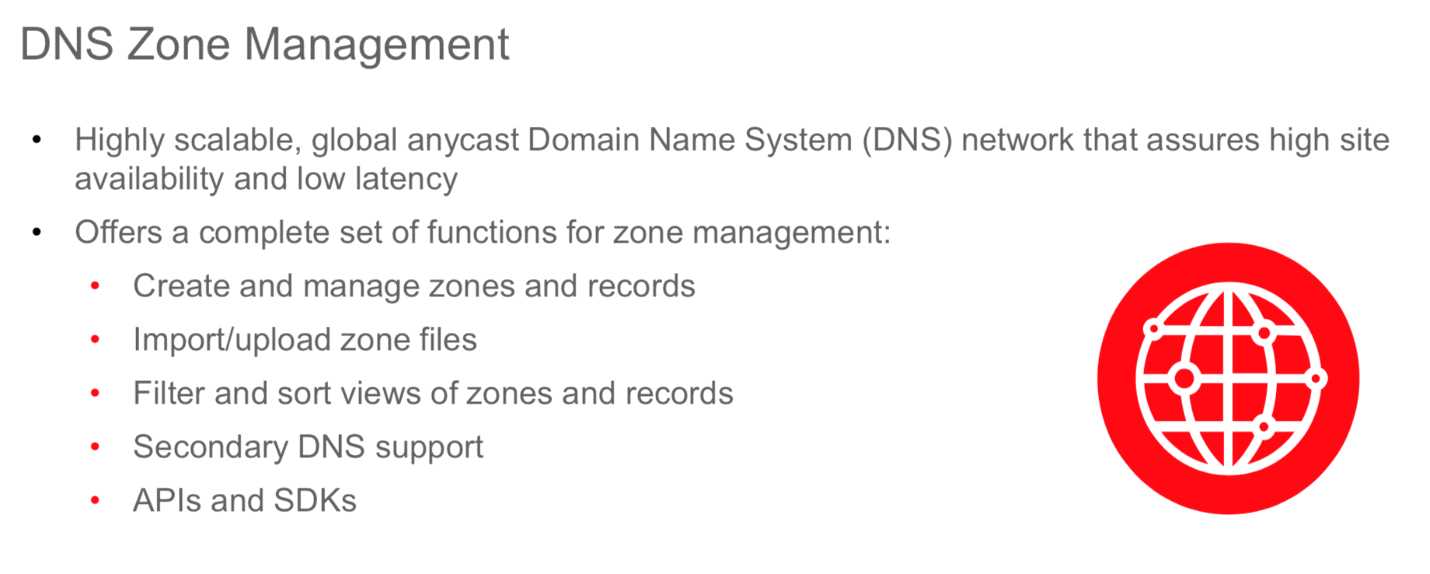
Reference:
https://www.oracle.com/a/ocom/docs/cloud/edge-services-100.pdf
Question 13
You are analyzing your Oracle Cloud Infrastructure (OCI) usage with Cost Analysis tool in the OCI
console.
Which of the following is NOT a default feature of the tool?
- A. Fault Domains
- A. Filter costs by applications
- B. Compartments
- B. Filter costs by tags
- C. Top of Rack Switches
- C. Filter costs by compartments
- D. Power Distribution Units
- D. Filter costs by date
Answer:
A
Explanation:
Cost Analysisis an easy-to-use visualization tool to help you track and optimize your Oracle Cloud
Infrastructure spending, allows you to generate charts, and download accurate, reliable tabular
reports of aggregated cost data on your Oracle Cloud Infrastructure consumption. Use the tool for
spot checks of spending trends and for generating reports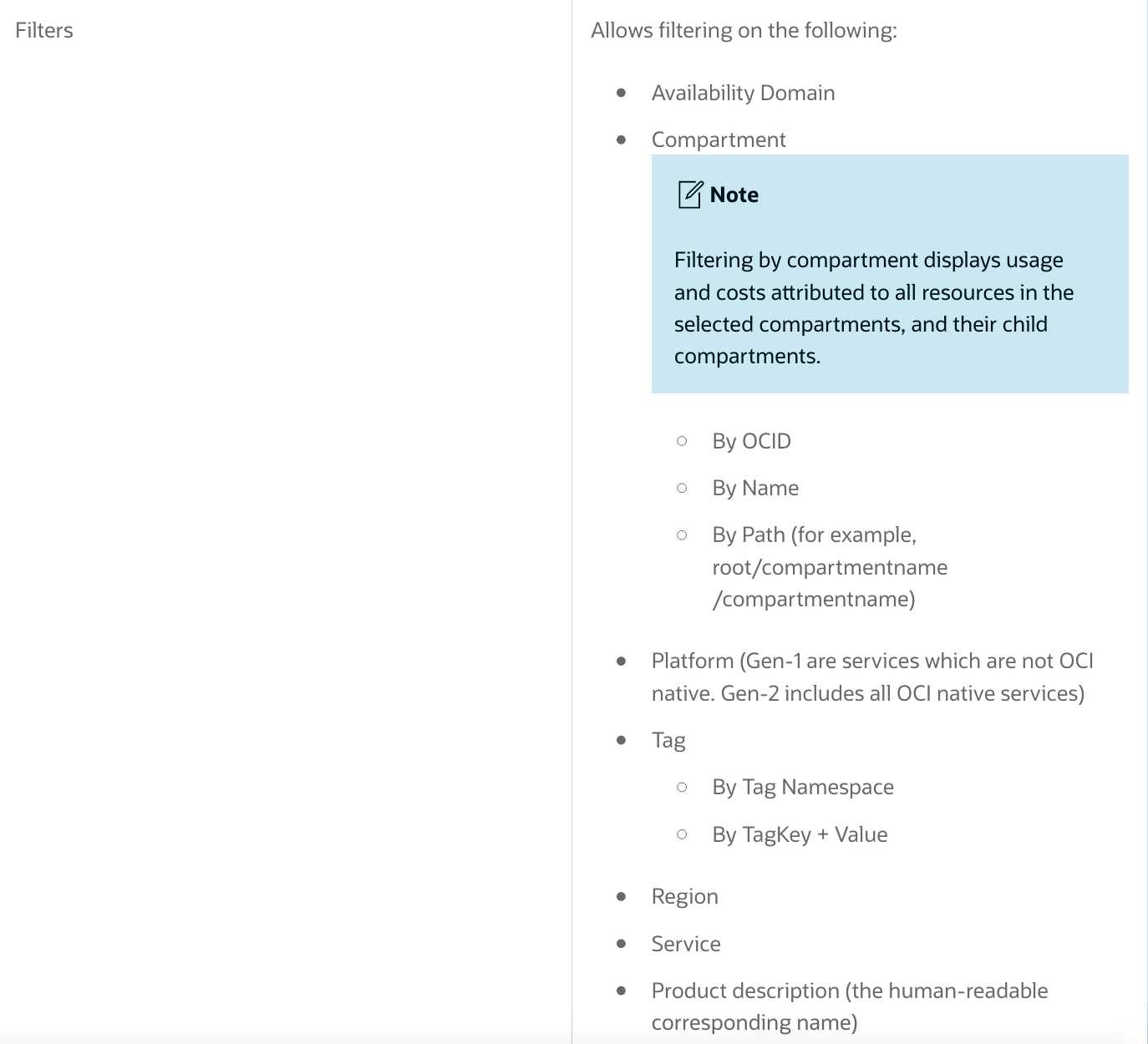
Reference:
https://docs.cloud.oracle.com/en-
us/iaas/Content/Billing/Concepts/costanalysisoverview.htm
Question 14
Which security service is offered by Oracle Cloud Infrastructure?
- A. REST APIs
- A. Certificate Management System
- B. OCI desktop client
- B. Key Management
- C. Secure Shell (SSH)
- C. Managed Active Directory
- D. OCI Console
- D. Managed Intrusion Detection
- E. Command-line Interface
- F. Remote Desktop Protocol (RDP)
- G. Serial console connection
Answer:
B
Explanation:
Oracle Cloud InfrastructureKey Managementis a managed service that enables you to encrypt your
data using keys that you control.
Reference:
https://www.oracle.com/in/cloud/security/cloud-services/key-management.html
Question 15
___________________ is a fully-managed, scalable, and highly available service that you can use to
deploy your containerized applications to the cloud.
- A. VCN Peering
- A. Oracle Cloud Infrastructure Container Engine for Kubernetes
- B. FastConnect
- B. Oracle Cloud Infrastructure Container Engine for Containerization
- C. Internet Gateway
- C. Oracle Cloud Infrastructure Container Engine for Deployment
- D. IPSec VPN
- D. Oracle Cloud Infrastructure Container Engine for Docker
Answer:
A
Explanation:
Oracle Cloud InfrastructureContainer Engine for Kubernetesis a fully-managed, scalable, and highly
available service that you can use to deploy your containerized applications to the cloud. Use
Container Engine for Kubernetes (sometimes abbreviated to just OKE) when your development team
wants to reliably build, deploy, and manage cloud-native applications. You specify the compute
resources that your applications require, and Container Engine for Kubernetes provisions them on
Oracle Cloud Infrastructure in an existing OCI tenancy.
You can access Container Engine for Kubernetes to define and create Kubernetes clusters using the
Console and the REST API. You can access the clusters you create using the Kubernetes command line
(kubectl), the Kubernetes Dashboard, and the Kubernetes API.
Container Engine for Kubernetes is integrated with Oracle Cloud Infrastructure Identity and Access
Management (IAM), which provides easy authentication with native Oracle Cloud Infrastructure
identity functionality.
Reference:
https://docs.cloud.oracle.com/en-
us/iaas/Content/ContEng/Concepts/contengoverview.htm