oracle 1z0-1072-21 practice test
Oracle Cloud Infrastructure 2021 Architect Associate Exam
Question 1
In Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE), what does a Replica Set do?
- A. It provides declarative updates for Pods.
- B. It maintains a stable set of replica Pods running at any given time.
- C. It ensures that all Nodes run a copy of a Pod.
- D. It exposes an application running on a set of Pods.
Answer:
D
Explanation:
Question 2
Which two resources reside exclusively in a single Oracle Cloud Infrastructure Availability Domain?
- A. Identity and Access Management Groups
- B. Web Application Firewall policy
- C. Block volume
- D. Compute Instance
- E. Object Storage
Answer:
C, D
Explanation:
https://docs.cloud.oracle.com/iaas/Content/General/Concepts/regions.htm#one
Question 3
Which three load-balancing policies can be used with a backend set?
- A. throughput
- B. least connections
- C. IP hash
- D. CPU utilization
- E. weighted round robin
Answer:
B, C, E
Question 4
You created a public subnet and an internet gateway in your virtual cloud network (VCN) of Oracle
Cloud Infrastructure. The public subnet has an associated route table and security list. However, after
creating several compute instances In the public subnet, none can reach the Internet.
Which two are possible reasons for the connectivity Issue?
- A. A NAT gateway is needed to enable the communication flow to internet.
- B. There Is no stateful egress rule In the security list associated with the public subnet.
- C. There Is no dynamic routing gateway (DRG) associated with the VCN.
- D. The route table has no default route for routing traffic to the internet gateway.
- E. There is no stateful ingress rule in the security list associated with the public subnet.
Answer:
B, D
Question 5
Which two statements are true about Autonomous Data Warehouse (ADW) backup?
- A. You can perform manual backups to OCI object storage in addition to automated backups available on ADW
- B. You can backup ADW database only to a standard bucket type in OCI object storage
- C. Oracle Cloud Infrastructure (OCI) recommends backing up ADW databases manually to on- premises storage devices
- D. You must backup ADW database to object storage bucket named ADW_backup
Answer:
AB
Explanation:
Autonomous Database automatically backs up your database for you.In addition to automatic
backups Autonomous Database also allows you take manual backups to your Oracle Cloud
Infrastructure Object Storage. for example if you want to take a backup before a major change to
make restore and recovery faster.
Also, Manual backups are only supported with buckets created in the standard storage tier
if you provision an Autonomous Data Warehouse instance named ADWC1, the bucket name should
be backup_adwc1 (the bucket name is lowercase)
Question 6
Which of the following two tasks can be performed in the Oracle Cloud Infrastructure Console for
Autonomous Data Warehouse?
- A. Adjust Network Bandwidth
- B. Scale up/down Memory
- C. Increase Storage allocated for Database
- D. Scale up/down CPU
Answer:
CD
Explanation:
You can scale up/down your Autonomous Database to scale both in terms of compute (CPU) and
storage only when needed, allows people to pay per use.
Oracle allows you to scale compute and storage independently, no need to do it together. these
scaling activities fully online (no downtime required)
in Details page Autonomous Database in OCI console, click Scale Up/Down. Click on arrow to select a
value for CPU Core Count or Storage (TB).
Or Select auto scaling to allow the system to automatically use up to three times more CPU and IO
resources to meet workload demand, compared to the database operating with auto scaling
disabled.
Question 7
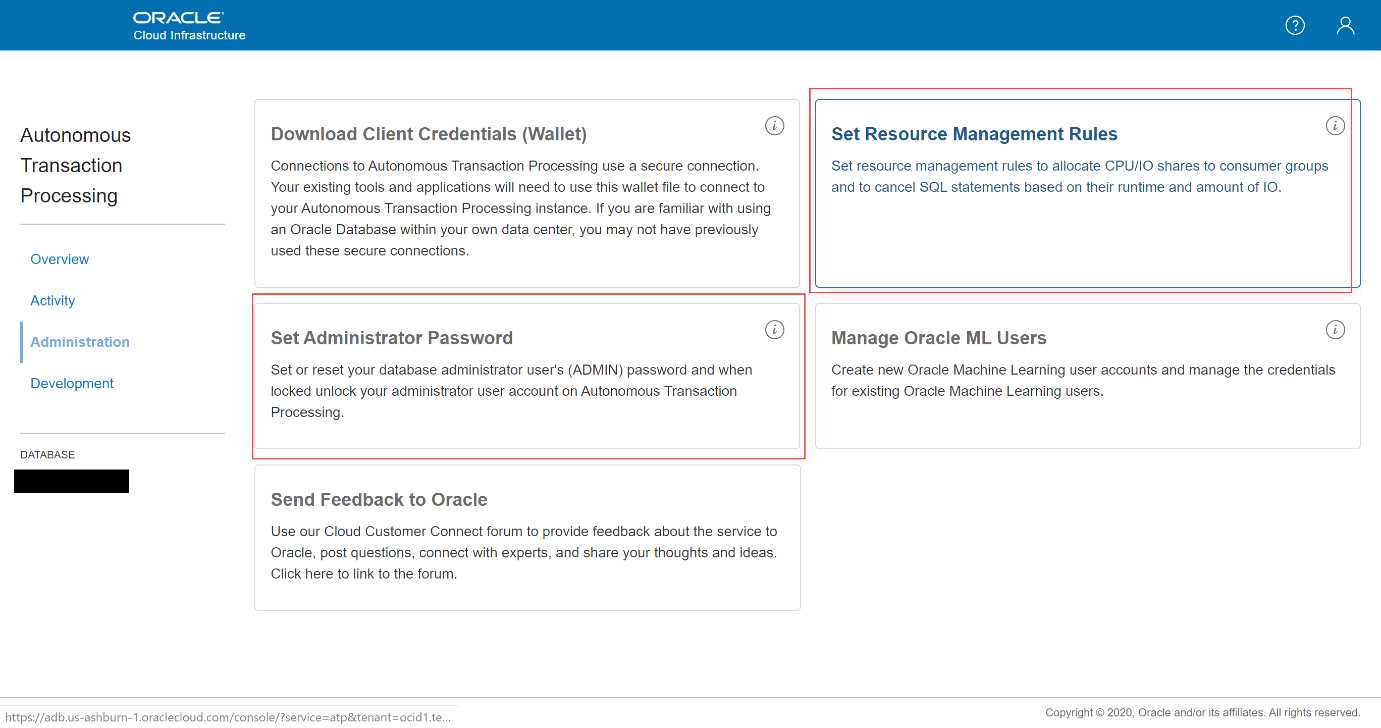
Which two options are available within the service console of Autonomous Transaction Processing?
- A. Monitor the health of the database server including CPU, memory and query performance
- B. Configure resource management rules and reset the admin password
- C. Perform a manual backup of the ATP database
- D. Fine tune a long running query using optimizer hints
Answer:
AB
Explanation:
Question 8
Which two statements are true about Oracle Cloud Infrastructure (OCI) DB Systems Data Guard
service?
- A. Both DB systems must use the same VCN, and port 1521 must be open
- B. Data guard configuration on the OCI is limited to a virtual machine only
- C. Data guard implementation for Bare Metal shapes requires two DB Systems, one containing the primary database and one containing the standby database.
- D. Data guard implementation requires two DB Systems, one running the primary database on a virtual machine and the standby database running on bare metal.
Answer:
AC
Explanation:
An Oracle Data Guard implementation requires two DB systems, one containing the primary
database and one containing the standby database. When you enable Oracle Data Guard for a virtual
machine DB system database, a new DB system with the standby database is created and associated
with the primary database. For a bare metal DB system, the DB system with the database that you
want to use as the standby must already exist before you enable Oracle Data Guard.
Requirement details are as follows:
- Both DB systems must be in the same compartment.
- The DB systems must be the same shape type (for example, if the shape of the primary database is
a virtual machine, then the shape of the standby database can be any other virtual machine shape).
- If your primary and standby databases are in different regions, then you must peer the virtual cloud
networks (VCNs) for each database.
- Configure the security list ingress and egress rules for the subnets of both DB systems in the Oracle
Data Guard association to enable TCP traffic to move between the applicable ports. Ensure that the
rules you create are stateful (the default).
Question 9
Which statement is true about the Oracle Cloud Infrastructure File Storage Service Snapshots?
- A. Snapshots are created under the root folder of file system, in a hidden directory named .snapshot
- B. Snapshots are not incremental
- C. You can restore the whole snapshot, but not the individual files
- D. It Is not possible to create snapshots from OCI console, but just the CLI
Answer:
A
Explanation:
The File Storage service supports snapshots for data protection of your file system. Snapshots are a
consistent, point-in-time view of your file systems. Snapshots are copy-on-write, and scoped to the
entire file system. The File Storage service encrypts all file system and snapshot data at rest. You can
take as many snapshots as you need.
Data usage is metered against differentiated snapshot data. If nothing has changed within the file
system since the last snapshot was taken, the new snapshot does not consume more storage
Snapshots are accessible under the root directory of the file system at.snapshot/name. For data
protection, you can use a tool that supports NFSv3 to copy your data to a different
availability
domain, region,
file system,
object storage
, or remote location.
Question 10
Which statement is true about the Oracle Cloud Infrastructure File Storage Service Mount Target?
- A. You can access multiple file systems through a single mount target
- B. Mount target has a public IP address and DNS name
- C. Mount target lives in a single subnet of your choice, but is not highly available
- D. Each mount target requires six internal IP addresses in the subnet to function
Answer:
A
Explanation:
A mount target is an NFS endpoint that lives in a VCN subnet of your choice and provides network
access for file systems. The mount target provides the IP address or DNS name that is used together
with a unique export path to mount the file system. A single mount target can export many file
systems. Typically, you
create your first mount target and export when you create your first file
system
. The mount target maintains an export set which contains all of the exports for its associated
file systems.
Limitations and Considerations
Each availability domain is limited to two mount targets by default. However, you can export up to
100 file systems through each mount target.
See
Service Limits
for a list of applicable limits and instructions for requesting a limit increase.
Each mount target requires three internal IP addresses in the subnet to function. Two of the IP
addresses are used during mount target creation. The third IP address must remain available for the
mount target to use for high availability failover.
The File Storage service doesn't "reserve" the third IP address required for high availability failover.
Use care when designing your subnets and file systems to ensure that sufficient IP addresses remain
available for your mount targets.
Question 11
You have two NFS clients running in two different subnets within the same Oracle Cloud
Infrastructure (OCI) Virtual Cloud Network (VCN). You have created a shared file system for the two
NFS clients who want to connect to the same file system, but you want to restrict one of the clients to
have READ access while the other has READ/Write access. Which OCr feature would you leverage to
meet this requirement?
- A. Use VCN security rules to control access for the NFS clients
- B. Use OCI Identity Access Management to control access for the NFS clients
- C. Use File Storage NFS Export Options to control access for the NFS clients
- D. Use NFS security to control access for the NES clients
Answer:
C
Explanation:
Oracle Cloud Infrastructure File Storage service provides a durable, scalable, secure, enterprise-grade
network file system. You can connect to a File Storage service file system from any bare metal, virtual
machine, or container instance in your Virtual Cloud Network (VCN). You can also access a file system
from outside the VCN using Oracle Cloud Infrastructure FastConnect and Internet Protocol security
(IPSec) virtual private network (VPN).
EXPORT
Exports control how NFS clients access file systems when they connect to a mount target. File
systems are exported (made available) through mount targets. Each mount target maintains an
export set which contains one or many exports. A file system must have at least one export in one
mount target in order for instances to mount the file system. The information used by an export
includes the file system OCID, mount target OCID, export set OCID,
export path
, and client
export
options
. For more information, see
Managing Mount Targets
.
EXPORT SET
Collection of one or more exports that control what file systems the mount target exports using
NFSv3 protocol and how those file systems are found using the NFS mount protocol. Each mount
target has an export set. Each file system associated with the mount target has at least one export in
the export set.
EXPORT PATH
A path that is specified when an export is created. It uniquely identifies the file system within the
mount target, letting you associate up to 100 file systems to a single mount target. This path is
unrelated to any path within the file system itself, or the client mount point path.
EXPORT OPTIONS
NFS export options are a set of parameters within the export that specify the level of access granted
to NFS clients when they connect to a mount target. An NFS export options entry within an export
defines access for a single IP address or CIDR block range. For more information, see
Working with
NFS Export Options
.
Question 12
Which of the following statement is true regarding Oracle Cloud Infrastructure Object Storage Pre-
Authenticated Requests?
- A. It Is not possible to create pre-authenticated requests for "archive" storage tier
- B. Changing the bucket visibility does not change existing pre-authenticated requests
- C. It is not possible to create pre-authenticated requests for the buckets, but only for the objects
- D. Pre-authenticated requests don't have an expiration
Answer:
B
Explanation:
Pre-authenticated requests provide a way to let users access a bucket or an object without having
their own credentials, as long as the request creator has permissions to access those objects. For
example, you can create a request that lets an operations support user upload backups to a bucket
without owning API keys. Or, you can create a request that lets a business partner update shared
data in a bucket without owning API keys.
When you create a pre-authenticated request, a unique URL is generated. Anyone you provide this
URL to can access the Object Storage resources identified in the pre-authenticated request, using
standard HTTP tools like curl and wget.
Understand the following scope and constraints regarding pre-authenticated requests:
Users can't list bucket contents.
You can create an unlimited number of pre-authenticated requests.
There is no time limit to the expiration date that you can set.
You can't edit a pre-authenticated request. If you want to change user access options in response to
changing requirements, you must create a new pre-authenticated request.
The target and actions for a pre-authenticated request are based on the creator's permissions. The
request is not, however, bound to the creator's account login credentials. If the creator's login
credentials change, a pre-authenticated request is not affected.
You cannot delete a bucket that has a pre-authenticated request associated with that bucket or with
an object in that bucket.
Understand the following scope and constraints regarding public access:
Changing the type of access is bi-directional. You can change a bucket's access from public to private
or from private to public.
Changing the type of access doesn't affect existing pre-authenticated requests. Existing pre-
authenticated requests still work.
Question 13
You have a working application in the US East region. The app is a 3-tier app with a database backend
- you take regular backups of the database into OCI Object Storage in the US East region. For Business
continuity; you are leveraging OCI Object Storage cross-region copy feature to copy database backups
to the US West region. Which of the following three steps do you need to execute to meet your
requirement?
- A. Write an IAM policy and authorize the Object Storage service to manage objects on your behalf
- B. Specify an existing destination bucket
- C. Specify the bucket visibility for both the source and destination buckets
- D. Provide a destination object name
- E. Provide an option to choose bulk copying of objects
- F. Choose an overwrite rule
Answer:
ABF
Explanation:
You can copy objects to other buckets in the same region and to buckets in other regions.
You must have the required access to both the source and destination buckets when performing an
object copy. You must also have permissions to manage objects in the source and destination
buckets.
Because Object Storage is a regional service, you must authorize the Object Storage service for each
region carrying out copy operations on your behalf. For example, you might authorize the Object
Storage service in region US East (Ashburn) to manage objects on your behalf. Once you authorize
the Object Storage service, you can copy an object stored in a US East (Ashburn) bucket to a bucket in
another region.
You can use overwrite rules to control the copying of objects based on their entity tag (ETag) values.
Specify an existing target bucket for the copy request. The copy operation does not automatically
create buckets.
Question 14
Your IT department wants to cut down storage costs, but also meet compliance requirements as set
up by the central audit group. You have a legacy bucket with both Word does (*.docx) and Excel files
(*.xlsx). Your auditors want to retain only Excel files for compliance purposes. Your IT departments
wants to keep all other files for 365 days only. What two steps can you take to meet this
requirement?
- A. Create Object Storage Lifecycle rules to archive objects from the legacy bucket after 365 days without any pattern matching
- B. Create Object Storage Lifecycle rules to delete objects from the legacy bucket after 365 days with a filter type - include by pattern: ''.docx
- C. It is not possible to meet this requirement
- D. Create Object Storage Lifecycle rules to delete objects from the legacy bucket after 365 days with a filter type - exclude by pattern: ''.xlsx"
- E. Create Object Storage Lifecycle rules to delete objects from the legacy bucket after 365 days without any pattern matching
Answer:
BD
Explanation:
Object Lifecycle Management lets you automatically manage the archiving and deletion of objects.
By using Object Lifecycle Management to manage your
Object Storage
and
Archive Storage
data, you
can reduce your storage costs and the amount of time you spend managing data.
Use object name filters to specify which objects the lifecycle rule applies to.
You can add object filters in any order. Object Lifecycle Management evaluates the precedence of the
rules as follows:
Pattern exclusions
Pattern inclusions
Prefix inclusions
Question 15
Your application consists of three Oracle Cloud Infrastructure compute instances running behind a
public load balancer. You have configured the load balancer to perform health checks on these
instances, but one of the three instances fails to pass the configured health check. Which of the
following action will the load balancer perform?
- A. Stop sending traffic to the instance that failed health check
- B. Terminate the instance that failed health check
- C. Stop the instances that failed health check
- D. Remove the instance that failed the health check from the backend set
Answer:
A
Explanation:
health check A test to confirm the availability of backend servers. A health check can be a request or
a connection attempt. Based on a time interval you specify, the load balancer applies the health
check policy to continuously monitor backend servers. If a server fails the health check, the load
balancer takes the server temporarily out of rotation. If the server subsequently passes the health
check, the load balancer returns it to the rotation.
You configure your health check policy when you create a backend set. You can configure TCP-level or
HTTP-level health checks for your backend servers.
- TCP-level health checks attempt to make a TCP connection with the backend servers and validate
the response based on the connection status.
- HTTP-level health checks send requests to the backend servers at a specific URI and validate the
response based on the status code or entity data (body) returned.
The service provides application-specific health check capabilities to help you increase availability
and reduce your application maintenance window.
https://tinvcc.com/product/buy-exoclick-ads-accounts/