Nutanix ncp-ci-aws practice test
Nutanix Certified Professional - Cloud Integration - AWS v6.7
Question 1
An administrator has recently deployed an NC2 on AWS cluster in the North Virginia region in
availability zone us-east-1z. The clusters UUID is 0005F487-4962-91EA-4C98-C4284D123835.
The cluster is consuming IPs from a 10.78.2.0/24 range.
The AWS VPC has these available CIDR ranges:
• 70.73.0.0/16
• 10.79.107.0/24
• 10.0.0.0/22
The following subnets have been configured in the NC2 AWS VPC: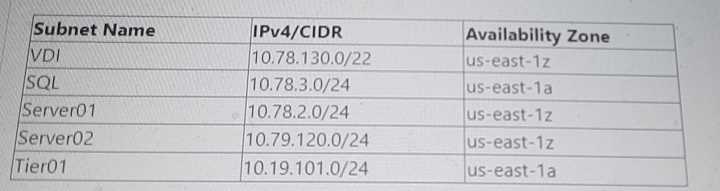
The following tags have been applied to a Custom Network Security Group: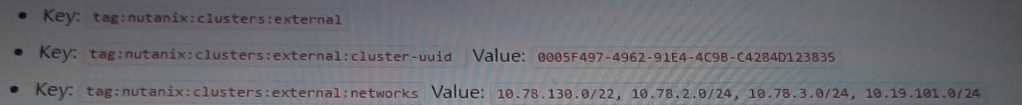
The Custom Network Security Group is allowing all inbound traffic from the 10.0.0.0/22 network.
Which two subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22
network segment"? (Choose two.)
- A. Server01
- B. Tier01
- C. SQL
- D. VDl
Answer:
AB
Explanation:
To determine which subnets would be able to receive inbound traffic from AWS instances on a
10.0.0.0/22 network segment, we need to look at the configured subnets and their CIDR ranges, as
well as the custom network security group's inbound rules.
Available CIDR ranges in VPC:
70.73.0.0/16
10.79.107.0/24
10.0.0.0/22
Configured Subnets in NC2 AWS VPC:
VDI: 10.78.130.0/22
SQL: 10.78.3.0/24
Server01: 10.78.2.0/24
Server02: 10.79.120.0/24
Tier01: 10.19.101.0/24
Custom Network Security Group Inbound Rule:
Allows all inbound traffic from 10.0.0.0/22.
Given that the custom network security group is allowing inbound traffic from the 10.0.0.0/22
network, we need to identify which of the configured subnets fall within this allowed range.
Analysis:
The subnets 10.78.130.0/22, 10.78.3.0/24, 10.78.2.0/24, 10.79.120.0/24, and 10.19.101.0/24 do not
overlap with 10.0.0.0/22. Therefore, none of these subnets would naturally fall within the
10.0.0.0/22 range directly.
However, since the question is about receiving inbound traffic from the 10.0.0.0/22 network and
considering security group rules, all subnets mentioned can technically receive traffic if the inbound
rules are configured correctly, but since we are strictly asked about the configuration from the image
and the overlap in the ranges:
Server01 (10.78.2.0/24) and Tier01 (10.19.101.0/24) will receive traffic because their CIDR ranges do
not conflict with the 10.0.0.0/22 range, thus allowing traffic without additional restrictions.
Reference:
Nutanix Clusters on AWS Administration Guide
AWS VPC and Subnet documentation
Network Security Group rules configuration in Nutanix documentation
Question 2
preparing the landing zone networking resources for a Nutanix cluster on AWS. The administrator has
created a VPC with two private subnets: one for cluster management and one for user VMs.
What additional subnet must the administrator create?
- A. Public subnet for S3 access
- B. Public subnet for Internet access
- C. Private subnet for VPN gateway
- D. Private subnet for Prism Central
Answer:
B
Explanation:
When setting up a landing zone for Nutanix clusters on AWS, having only private subnets for cluster
management and user VMs is not sufficient for full cluster functionality. Nutanix clusters often need
to communicate with the internet for updates, patches, and other cloud services.
VPC Configuration:
The VPC already has two private subnets (one for cluster management and one for user VMs).
Additional Requirements:
To access public services like S3 or for the cluster nodes to reach Nutanix services for updates, a
public subnet is essential.
Why Public Subnet for Internet Access?:
A public subnet allows resources within it to communicate directly with the internet, which is
necessary for accessing Nutanix's update servers, applying patches, and other maintenance tasks.
This subnet typically includes an internet gateway, enabling instances in the public subnet to receive
and send traffic directly to the internet.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
AWS Networking Best Practices
Nutanix Networking and Subnet Configuration Guidelines
Question 3
An organization wants to control network traffic at the individual User VM (UVM) subnet level.
Which action will help achieve this goal?
- A. Create a custom security group.
- B. Modify the default UVM security group.
- C. Modify the user management security group.
- D. Modify the internal management security group.
Answer:
A
Explanation:
To control network traffic at the individual User VM (UVM) subnet level, creating a custom security
group is the appropriate action. This approach allows for fine-grained control over inbound and
outbound traffic rules that can be applied to specific subnets or individual instances within those
subnets.
Custom Security Group:
Custom security groups enable administrators to define specific traffic rules tailored to the needs of
individual subnets or VMs. This includes specifying allowed IP ranges, ports, and protocols.
By applying these custom security groups to the UVMs, the organization can control access and
enhance security according to their policies and requirements.
Steps to Create a Custom Security Group:
Navigate to the AWS Management Console and go to the VPC service.
Select "Security Groups" under the "Security" section.
Click on "Create Security Group" and define the name, description, and VPC.
Add inbound and outbound rules according to the desired traffic control policies.
Attach the custom security group to the UVMs or subnets in question.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
AWS Security Group Documentation
Nutanix Best Practices for Security Groups
Question 4
When configuring an alert email in Prism Central deployed within an NC2 environment, what is
required in order for the emails to be sent properly?
- A. SMTP server configured in Prism Central settings
- B. Cluster Super Admin permissions
- C. Name servers configured in Prism Central
- D. A whitelisted public cloud console endpoint
Answer:
A
Explanation:
To ensure that alert emails are sent properly from Prism Central within an NC2 environment,
configuring an SMTP server in the Prism Central settings is required. The SMTP server facilitates the
sending of email notifications for alerts and other communications.
SMTP Configuration:
Prism Central requires an SMTP server to send email alerts. This involves specifying the SMTP server
address, port, and authentication details if needed.
The configuration must include the email address from which the alerts will be sent and the recipient
addresses.
Steps to Configure SMTP Server in Prism Central:
Log in to Prism Central.
Navigate to the "Settings" menu.
Select "Email Server" under the "Alerts" section.
Enter the SMTP server details, including the server address, port, and authentication credentials.
Test the configuration to ensure emails are sent correctly.
Reference:
Nutanix Prism Central Administration Guide
Nutanix Support Documentation on Email Alert Configuration
Best Practices for Configuring SMTP Servers in Cloud Environments
Question 5
An administrator has deployed an NC2 on AWS cluster and doesn't have connectivity back to the on-
premises environment yet. The administrator wants to SSH into a CVM to edit a security setting and
has deployed a Jump Host into an existing public subnet.
What action must the administrator still take to gain access to the CVM?
- A. Edit the CVM iptables to allow SSH.
- B. Edit the User Management Network Security Group to allow SSH from the Jump Host IP.
- C. Edit the UVM security group to allow SSH from the Jump Host IP and remove Cluster Lockdown.
- D. Create Custom Network Security Group at the subnet level and add the IP address of the Jump Host
Answer:
B
Explanation:
To SSH into a Controller VM (CVM) in an NC2 on AWS cluster without on-premises connectivity, the
administrator needs to ensure that the security settings allow SSH access from the Jump Host. This
involves editing the User Management Network Security Group to permit SSH traffic from the Jump
Host IP.
Deploy Jump Host:
Ensure the Jump Host is deployed in a public subnet with an Elastic IP (EIP) assigned for external
access.
Edit User Management Network Security Group:
Locate the security group associated with the user management network.
Modify the inbound rules to allow SSH (port 22) from the Jump Host's IP address. This ensures that
the Jump Host can establish an SSH connection to the CVM.
Steps to Edit Security Group:
Navigate to the EC2 dashboard in the AWS Management Console.
Select "Security Groups" under the "Network & Security" section.
Find and select the appropriate security group.
Edit the inbound rules to add a new rule:
Type: SSH
Protocol: TCP
Port Range: 22
Source: Custom IP (enter the Jump Host's public IP address)
Additional Configuration:
Ensure that the CVM itself allows SSH connections and that no internal firewall rules block the traffic.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
AWS Security Group Documentation
Nutanix Best Practices for Secure Access
Question 6
Which service enables the monitoring of key metrics on various AWS services, inducing EC2, EBS, and
VPC for an NC2 cluster deployments?
- A. Amazon CloudWatch
- B. AWS CloudTrail
- C. AWS CloudFormation
- D. Amazon inspector
Answer:
A
Explanation:
Amazon CloudWatch is the service that enables the monitoring of key metrics on various AWS
services, including EC2, EBS, and VPC, for NC2 cluster deployments.
Amazon CloudWatch:
Amazon CloudWatch provides monitoring for AWS cloud resources and applications. It collects and
tracks metrics, collects and monitors log files, and sets alarms.
Specifically, for NC2 deployments, CloudWatch can be used to monitor key metrics such as CPU
utilization, disk I/O, network I/O for EC2 instances, EBS volume performance, and VPC network
traffic.
Features:
Metrics Monitoring: Collects and visualizes operational data in the form of metrics, including
utilization, performance, and health.
Logs Monitoring: Collects log data, monitors it in real-time, and triggers alarms based on predefined
thresholds.
Alarms: Notifies when operational performance thresholds are breached.
Integration with NC2:
By setting up CloudWatch, administrators can ensure they have visibility into the performance and
health of their Nutanix clusters on AWS, aiding in proactive management and troubleshooting.
Reference:
Amazon CloudWatch Documentation
Nutanix Cloud Clusters on AWS Administration Guide
AWS Monitoring Best Practices
Question 7
An administrator needs the permissions to create and manage multiple organizations and clusters in
NC2, as well as manage user access for the entire company.
What role should be assigned to meet the minimum requirements of this task?
- A. Organization Administrator
- B. Customer Administrator
- C. Customer Security Administrator
- D. Cluster Administrator
Answer:
B
Explanation:
The role of "Customer Administrator" in Nutanix Cloud Integration with AWS (NC2) is designed to
meet the requirements of creating and managing multiple organizations and clusters, as well as
managing user access for the entire company.
Roles and Permissions:
Customer Administrator: This role has the broadest set of permissions, allowing the user to create
and manage organizations, clusters, and user access across the entire company. It encompasses
administrative control over multiple aspects of the NC2 environment.
Capabilities:
Organization Management: Ability to create and manage multiple organizations.
Cluster Management: Full control over creating, configuring, and managing clusters.
User Access Management: Manage user roles and permissions, ensuring that the right individuals
have access to the necessary resources.
Why Not Other Roles:
Organization Administrator: Limited to managing organizations but not clusters and user access at
the company level.
Customer Security Administrator: Focuses on security aspects, lacking broader administrative
capabilities.
Cluster Administrator: Limited to managing clusters without the ability to manage organizations and
user access comprehensively.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Role-Based Access Control Documentation
Question 8
An administrator needs to create user VM subnets for multiple NC2 clusters in AWS.
What would be the best approach to take?
- A. Create guest-VM VNets for each cluster.
- B. Use the cluster management subnet dedicated to each cluster.
- C. Create guest-VM subnets to be shared by all clusters.
- D. Create guest-VM subnets for each cluster.
Answer:
D
Explanation:
When creating user VM subnets for multiple NC2 clusters in AWS, the best approach is to create
guest-VM subnets for each cluster. This ensures that each cluster has its own dedicated subnets,
which simplifies network management and avoids potential IP conflicts.
Advantages of Dedicated Subnets:
Isolation: Each cluster operates in its own subnet, providing better isolation and security.
Management: Easier to manage and troubleshoot network issues when each cluster has its own
subnets.
Scalability: More scalable as each subnet can be managed and expanded independently.
Steps to Create Guest-VM Subnets:
Identify the IP range for each subnet.
In the AWS VPC console, create a new subnet for each cluster using the identified IP ranges.
Associate the new subnets with the respective clusters during or after the cluster deployment
process.
Why Not Shared Subnets:
Shared subnets could lead to IP conflicts and make network management more complex, especially
as the number of clusters grows.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
AWS VPC Subnet Creation Documentation
Question 9
An administrator has been tasked with deploying an NC2 cluster on AWS with the requirement to
protect workloads. Which two options are valid to protect the workloads on this cluster? (Choose
two.)
- A. Deploy one-node cluster in another availability zone.
- B. Create a second NCZ cluster in a different availability zone.
- C. Use an existing on-prem Nutanix cluster as a disaster recovery target.
- D. Deploy a cluster across two availability zones.
Answer:
B
Explanation:
To protect workloads on an NC2 cluster on AWS, deploying strategies that ensure high availability
and disaster recovery are essential. The two valid options are:
Create a Second NC2 Cluster in a Different Availability Zone:
High Availability: Deploying a second NC2 cluster in a different availability zone ensures that
workloads can be quickly recovered in case of an availability zone failure.
Disaster Recovery: This setup enables asynchronous replication between clusters, providing a robust
disaster recovery solution.
Use an Existing On-Prem Nutanix Cluster as a Disaster Recovery Target:
Hybrid DR: Leveraging an existing on-premises Nutanix cluster for disaster recovery provides a cost-
effective and efficient DR solution.
Replication: Set up replication policies to ensure data is consistently copied from the NC2 cluster on
AWS to the on-premises cluster.
Why Not Other Options:
One-node cluster in another availability zone: Not a valid DR solution as a single-node cluster cannot
provide the required resilience and high availability.
Deploy a cluster across two availability zones: While this can enhance availability, it is not a typical
approach for Nutanix clusters which are designed to operate within a single availability zone for
simplicity and performance reasons.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Disaster Recovery Best Practices
AWS Availability Zones and Disaster Recovery Documentation
Question 10
Exhibit.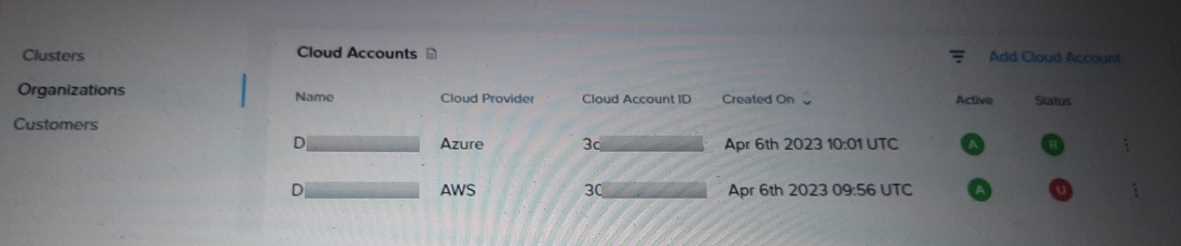
An administrator is attempting, but failing to create an NC2 cluster in AWS. The administrator checks
the configuration in the NC and notices the configuration shown in the exhibit.
What action should the administrator take to resolve the issue?
- A. Recreate the AWS CloudFormation stack.
- B. Create a new cloud account in the organization.
- C. Restart Genesis on a Prism Central instance.
- D. Grant the administrator's account access to the NC2 organization.
Answer:
B
Explanation:
The exhibit shows two cloud accounts, one for Azure and one for AWS, with their statuses indicated.
The AWS cloud account status is marked as "U" (which likely stands for "Unavailable" or
"Unreachable"). This indicates that the AWS cloud account configuration is not properly connected or
accessible.
Status Check:
The AWS cloud account is marked with an "U" status, meaning it is not active or accessible.
This status prevents the creation of an NC2 cluster because the necessary cloud resources cannot be
allocated or managed without a proper connection.
Action:
The best course of action is to create a new cloud account in the organization. This involves setting up
the cloud account details correctly and ensuring it is properly configured to communicate with
Nutanix and AWS.
Steps to Create a New Cloud Account:
Log in to the Nutanix console.
Navigate to the "Organizations" section.
Select "Add Cloud Account" and provide the required AWS credentials and permissions.
Ensure the new cloud account is active and correctly configured.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Best Practices for Cloud Account Management
Question 11
An administrator has been tasked with ensuring NC2 VMs are able to access AWS resources. The NC2
VM traffic must not traverse the internet.
in which two ways would the administrator achieve this? (Choose two.)
- A. By using a Gateway Endpoint
- B. By using a NAT Gateway.
- C. By using an Interface Endpoint
- D. By using a VPC Peer.
Answer:
CD
Explanation:
To ensure that NC2 VMs can access AWS resources without traversing the internet, the administrator
can use AWS VPC Peering and Interface Endpoints. Both methods ensure that traffic stays within the
AWS network, maintaining security and efficiency.
Interface Endpoint:
Interface Endpoints allow you to privately connect your VPC to supported AWS services. They use
AWS PrivateLink to route traffic directly to services within the AWS network, bypassing the public
internet.
Steps:
Create an interface endpoint for the required service in the AWS VPC console.
Ensure the security groups and route tables are configured to allow traffic to the interface endpoint.
VPC Peering:
VPC Peering allows the routing of traffic between VPCs using private IP addresses, without the need
for internet gateways, NAT devices, or VPN connections.
Steps:
Create a VPC peering connection between the VPCs.
Update the route tables to direct traffic between the peered VPCs.
Ensure security group rules allow the necessary traffic between VPCs.
Reference:
AWS VPC Peering Documentation
AWS Interface Endpoint Documentation
Nutanix Cloud Clusters on AWS Administration Guide
Question 12
During the recovery of entities protected by Cluster Project, an administrator discovers that the
recovery plan is not executing correctly because it exceeds the number of supported entities.
How many entities can be recovered using a Single recovery plan?
- A. 100
- B. 200
- C. 300
- D. 400
Answer:
C
Explanation:
The Nutanix disaster recovery capabilities include recovery plans that define how entities are
recovered in the event of a failure. There is a limit to the number of entities that can be managed
within a single recovery plan.
Entity Limit:
According to Nutanix documentation, the maximum number of entities that can be recovered using a
single recovery plan is 300. Exceeding this limit will cause issues during the execution of the recovery
plan.
Impact of Exceeding the Limit:
If the number of entities in a recovery plan exceeds the supported limit, the recovery process may
fail or not execute correctly, as observed in the scenario.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Disaster Recovery Best Practices Documentation
Question 13
An administrator needs to allow wide open access to one particular NC2 AWS cluster from an on-
premises subnet of 10.19.160.0/24.
What is the proper Custom Security Group formatting to satisfy this task?
A)
B)
C)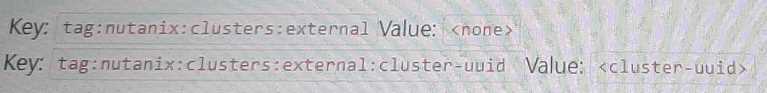
D)
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
B
Explanation:
To allow wide open access to a particular NC2 AWS cluster from an on-premises subnet
(10.19.160.0/24), the proper Custom Security Group formatting needs to include the necessary tags
that specify the external cluster UUID and the networks allowed.
Custom Security Group Configuration:
The configuration should include tags to identify the cluster and the networks that should be granted
access.
Key: nutanix:clusters
Key: nutanix:clusters:external
Value: <cluster-uuid>
Explanation of Choice:
Option B includes the necessary tags and values, ensuring that the specific cluster UUID is recognized
and the on-premises subnet (10.19.160.0/24) can communicate with the NC2 cluster.
Security Group Tags:
nutanix:clusters:external - Identifies the cluster as external.
nutanix:clusters:external:cluster-uuid - Specifies the unique identifier for the cluster, enabling proper
traffic routing and access.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
AWS Security Group Documentation
Nutanix Best Practices for Custom Security Group Configuration
Question 14
Which interface must be used to deploy NC2?
- A. Cloud Provider portal
- B. NC2 Tile within the my.nutanix.com portal
- C. Prism Central Dashboard
- D. Foundation running in a Cloud Virtual Machine
Answer:
B
Explanation:
The NC2 Tile within the my.nutanix.com portal is the correct interface to deploy NC2. This portal
provides an integrated and user-friendly interface specifically designed for deploying and managing
Nutanix Clusters on AWS.
NC2 Deployment Interface:
NC2 Tile within the my.nutanix.com portal: This portal provides the necessary tools and options to
deploy and manage NC2 clusters. It includes functionalities for setting up the clusters, configuring
network settings, and managing resources.
Advantages:
User-Friendly Interface: Simplifies the deployment process with a guided setup.
Integrated Tools: Provides access to all necessary tools for managing the deployment and monitoring
of NC2 clusters.
Reference:
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix my.nutanix.com Portal Documentation
Nutanix Best Practices for Cluster Deployment
Question 15
Which entity should be contacted for AOS software supported related to NC2?
- A. Internal IT Operations team
- B. Nutanix
- C. Partner
- D. Public Cloud Vendor
Answer:
B
Explanation:
For AOS software support related to NC2, the appropriate entity to contact is Nutanix. Nutanix
provides comprehensive support for their software, including the Acropolis Operating System (AOS)
used in NC2 deployments.
Support Scope:
Nutanix offers support for the deployment, configuration, and management of NC2 clusters,
including any issues related to AOS software.
This includes troubleshooting, updates, and technical assistance.
Why Not Other Options:
Internal IT Operations team: Typically handles internal issues but does not have the specialized
knowledge or resources for AOS software support.
Partner: May provide support but would ultimately escalate issues to Nutanix for software-specific
concerns.
Public Cloud Vendor: Manages infrastructure-related issues but does not provide support for Nutanix
AOS software.
Reference:
Nutanix Support Documentation
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Best Practices for AOS Support