nokia 4a0-100 practice test
Nokia IP Networks and Services Fundamentals
Question 1
Which of the following is NOT a goal of a layered protocol stack?
- A. To exchange information and divide it into simpler functions.
- B. To provide flexibility so that new protocols can be easily added.
- C. To reduce protocol overhead.
- D. To relieve some devices of some unnecessary tasks.
Answer:
C
Explanation:
A layered protocol stack is designed to simplify network communication by separating functionalities
into distinct layers. Each layer has a defined role and communicates with the layers directly above
and below it. The main benefits of this model include:
Simplified design and implementation: Developers can focus on one layer without needing to
understand the entire system.
Flexibility: New protocols can be developed and inserted at specific layers without redesigning the
whole stack.
Interoperability: Standard interfaces allow different systems and vendors to work together.
Isolation of functions: Errors and updates can be managed within one layer without impacting
others.
However, reducing protocol overhead is not a primary goal of this model. In fact, the encapsulation
and interaction between layers can sometimes introduce extra overhead. This overhead is a trade-off
accepted to gain the other benefits listed above.
Reference: Nokia IP Networking Fundamentals Study Guide – Chapter 2: "Layered Protocol
Architectures", Section: "Benefits and Goals of Layered Models"
Question 2
Which of the following is a function of the Link layer?
- A. It is responsible for encapsulating packets into frames for transmission on physical media.
- B. It is responsible for encapsulating packets into IP datagrams and routing them.
- C. It is responsible for encapsulating application data into TCP/UDP messages.
- D. It is responsible for the timing of the signals on physical media.
Answer:
A
Explanation:
The Link layer, also known as the Data Link layer in the OSI model, is responsible for encapsulating
packets from the Network layer into frames suitable for transmission over the physical medium. This
process includes adding headers and trailers to the packet to create a frame, which contains
necessary information for error detection, addressing, and control.
According to the OSI model, the Data Link layer serves as the intermediary between the Network
layer and the Physical layer. It ensures that data is packaged into frames and manages the access to
the physical transmission medium.
Option A correctly describes this function.
Option B pertains to the Network layer, which is responsible for encapsulating data into IP datagrams
and determining the routing of these datagrams across networks.
Option C relates to the Transport layer, which handles the encapsulation of application data into
transport layer segments, such as TCP or UDP messages.
Option D is a function of the Physical layer, which deals with the transmission and reception of raw
bitstreams over a physical medium, including the timing and synchronization of signals.
Reference:
GeeksforGeeks:
Data Link Layer in OSI Model
TechTarget:
What is the data link layer in the OSI model?
Question 3
Which of the following is NOT a characteristic of a Virtual Private Network (VPN)?
- A. Each customer's traffic is isolated from other customers.
- B. Service providers utilize a shared infrastructure to support multiple VPNs.
- C. Customer data is altered as it traverses a VPN.
- D. A VPN is created specifically to meet the requirements of each customer.
Answer:
C
Explanation:
A Virtual Private Network (VPN) is designed to provide secure and private communication over a
shared or public infrastructure. Key characteristics of VPNs include:
Traffic Isolation: Each customer's traffic is kept separate from others, ensuring privacy and security.
Shared Infrastructure: Service providers can support multiple VPNs over the same physical
infrastructure, optimizing resource utilization.
Customization: VPNs can be tailored to meet the specific requirements of individual customers,
including security policies, routing, and quality of service.
However, customer data is not altered as it traverses a VPN. Instead, VPNs employ encryption and
tunneling protocols to protect data integrity and confidentiality during transmission. The primary
goal is to ensure that data remains unchanged and secure from end to end.
Reference: Nokia IP Networks and Services Study Guide – Chapter on VPN Services
Question 4
Which of the following Nokia 7750 SR components is NOT part of the data plane?
- A. The Media Dependent Adapter (MDA)
- B. The Input/Output Module (IOM)
- C. The eXpandable Media Adapter (XMA)
- D. The Control Processor Module (CPM)
Answer:
D
Explanation:
The Nokia 7750 SR architecture separates its operations into control plane and data plane functions.
The Data Plane includes hardware components responsible for forwarding traffic at line rate. These
components include:
MDA (Media Dependent Adapter) – interfaces with physical media.
IOM (Input/Output Module) – performs high-speed packet forwarding and processing.
XMA (eXpandable Media Adapter) – extends port capacity and media support.
The Control Plane includes the CPM (Control Processor Module), which is responsible for running
routing protocols, managing configuration, system operations, and other control-related functions.
The CPM does not participate in data forwarding and is thus not part of the data plane.
Reference:
Nokia SRA Study Guide, Chapter: "System Architecture – 7750 SR Components"
Nokia IP Networks and Services Fundamentals – Section: Control and Data Plane Functions in SR
Architecture
Question 5
Which compact flash on a control processing module (CPM) of a Nokia 7750 SR stores the runtime
software image and the configuration file?
- A. CF1
- B. CF2
- C. CF3
- D. Both CF1 and CF2
Answer:
C
Question 6
Which of the following statements about MD-CLI is FALSE?
- A. It allows atomic transactions.
- B. Configuration changes are activated when the running configuration datastore is saved to a file.
- C. To achieve transactional configuration, it is necessary to have multiple configuration datastores.
- D. Multiple users may enter the global configuration mode concurrently.
Answer:
B
Explanation:
The Model-Driven Command Line Interface (MD-CLI) in Nokia SR OS provides a structured and
programmatic way to manage configurations. It is based on a transactional model, meaning changes
are made in a candidate configuration before being committed to the running configuration.
Let's review each statement:
A. It allows atomic transactions –
True. MD-CLI uses atomic transactions to apply multiple changes
✔
at once, ensuring consistency and rollback if a failure occurs.
B. Configuration changes are activated when the running configuration datastore is saved to a file –
❌
False. In MD-CLI, changes are committed to the running datastore when a user issues the commit
command, not when saving to a file. Saving to a file is a separate action (e.g., admin save) and does
not trigger configuration activation.
C. To achieve transactional configuration, it is necessary to have multiple configuration datastores –
True. MD-CLI uses candidate, running, and operational datastores to implement transaction-
✔
based configuration.
D. Multiple users may enter the global configuration mode concurrently –
True. MD-CLI supports
✔
multi-user access to global configuration with locking mechanisms to prevent conflicts.
Reference:
Nokia SR OS MD-CLI User Guide
Nokia SRA Study Guide – Chapter: "Model-Driven Configuration and Transactions"
Question 7
Which configuration edit mode allows only one user to modify the global candidate configuration?
- A. Private
- B. Global
- C. Read-only
- D. Exclusive
Answer:
D
Explanation:
In Nokia SR OS, the MD-CLI provides multiple configuration edit modes to allow different types of
user interaction with the configuration system:
Private mode allows multiple users to create individual configuration candidates, which are then
merged with the global candidate during commit.
Global mode enables multiple users to edit the same candidate configuration at the same time, with
a shared commit session.
Read-only mode allows the user to view the configuration without making changes.
Exclusive mode restricts access to the global candidate configuration such that only one user at a
time can enter and make changes. This prevents conflicts and is useful in environments where strict
control over configuration changes is necessary.
Therefore, the correct answer is Exclusive mode, as it exclusively locks access to the global candidate
for a single user.
Reference:
Nokia SR OS MD-CLI User Guide – Section: "Configuration Edit Modes"
Nokia SRA Study Guide – MD-CLI Configuration Concepts
Question 8
On the Nokia 7750 SR, which key displays all command options and their descriptions?
- A. ?
- B. Tab
- C. Space bar
- D. Return
Answer:
A
Explanation:
Comprehensive and Detailed Explanation From Exact Extract:
In the Nokia SR OS CLI, specifically in both classic CLI and MD-CLI, the "?" key is used to display a list
of all possible command options at a given point in the CLI, along with a brief description of each
option.
This functionality helps the user in command discovery and reduces the chances of syntactical errors
by showing only valid options.
The "Tab" key, while helpful, is primarily used for auto-completion and not for displaying detailed
descriptions.
"Space bar" is used for command continuation, and "Return" executes the command or moves to the
next line.
Correct usage example in classic CLI:
*A:SR1>config>router>interface# ?
- Shows all the valid commands and parameters under interface
Reference:
Nokia SRA Study Guide – Chapter: "CLI Fundamentals"
Nokia SR OS Fundamentals Guide – Section: "Using the CLI Help System"
Question 9
Which of the following is NOT a valid event logging destination?
- A. SNMP
- B. NETCONF
- C. Syslog
- D. BOF
Answer:
D
Explanation:
In Nokia SR OS, event logging allows the router to report system events, alarms, and operational
changes to external systems or users. The valid logging destinations include:
SNMP – Used to send traps or informs to SNMP managers.
Syslog – Sends logs to centralized syslog servers, a standard for log management.
NETCONF – Can be used for event notification in model-driven management setups, although it is
more frequently used for configuration and state management.
However, BOF (Boot Options File) is not a valid logging destination. The BOF is used to store critical
system boot configurations, such as:
Which image to boot from
Network interface settings
Auto-boot parameters
BOF plays no role in the logging infrastructure.
Reference:
Nokia SR OS Fundamentals Guide – Section: “Event Logging”
Nokia SRA Study Guide – Chapter: "Logging and Event Monitoring"
Question 10
Which of the following statements best describes a hub?
- A. A device used to connect cables with signal amplification.
- B. A device that receives and replicates data without layer-2 header inspection.
- C. A device that receives and forwards data based on the MAC destination address.
- D. A device that receives and forwards data based on the layer-3 destination address.
Answer:
B
Explanation:
A hub is a physical layer (Layer 1) networking device used to connect multiple Ethernet devices in a
network. Unlike switches or routers, hubs do not inspect or process frame headers. Instead, they
perform a simple task:
Receive a signal (electrical or optical) on one port
Replicate that signal identically to all other ports
This means the hub does not examine Layer 2 (MAC addresses) or Layer 3 (IP addresses) and does
not perform intelligent forwarding. It merely broadcasts all incoming traffic to every other connected
device, often resulting in high collision domains and poor efficiency.
Option A describes a repeater, not a hub.
Option C describes a switch (Layer 2 device).
Option D describes a router (Layer 3 device).
Option B is correct: A hub does not inspect headers and replicates traffic blindly.
Reference:
Nokia IP Networking Fundamentals Study Guide – Chapter: "Network Devices and OSI Model"
CompTIA Network+ and Cisco CCNA foundational guides (for universally accepted hardware
behavior)
Question 11
In MAC address 00-20-60-CE-2B-28, which part is the Organisationally Unique Identifier (OUI)?
- A. 2B-28
- B. 00-20
- C. CE-2B-28
- D. 00-20-60
Answer:
D
Explanation:
A MAC address (Media Access Control address) is a 48-bit identifier typically expressed in six groups
of two hexadecimal digits (e.g., 00-20-60-CE-2B-28). It consists of two key parts:
OUI (Organizationally Unique Identifier) – The first 24 bits (or first 3 octets, e.g., 00-20-60) are
assigned by the IEEE to hardware manufacturers. This identifies the vendor or manufacturer.
Device Identifier (NIC Specific) – The remaining 24 bits (e.g., CE-2B-28) are assigned uniquely by the
vendor to each device/interface.
So in the address 00-20-60-CE-2B-28:
00-20-60 is the OUI
CE-2B-28 is the device-specific portion
Thus, the correct answer is D. 00-20-60.
Reference:
IEEE MAC Address Standard (IEEE 802)
Nokia IP Networking Fundamentals Study Guide – Chapter: "Ethernet Addressing"
Question 12
Refer to the exhibit.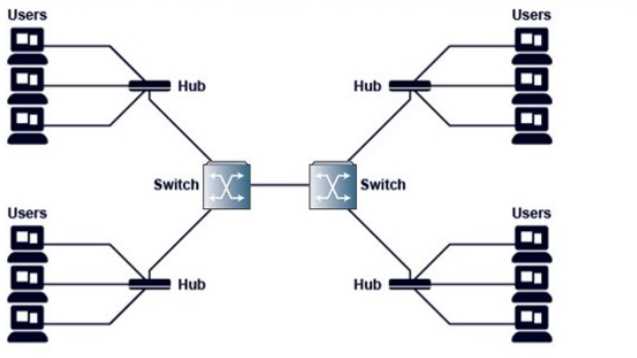
An Ethernet Local Area Network (LAN) consists of the components shown in the diagram. Assuming
there are no VLANs, how many broadcast domains are on this LAN?
- A. 1
- B. 2
- C. 5
- D. 6
Answer:
A
Explanation:
A broadcast domain is a logical division of a network in which all nodes can reach each other with
broadcast frames (Layer 2). Devices within the same broadcast domain receive broadcast packets
sent by others.
In the diagram:
Multiple users connect to hubs.
Hubs are Layer 1 devices and do not break broadcast domains. They simply replicate incoming
electrical signals to all ports.
Hubs are then connected to switches.
Switches, unless VLANs are configured, forward broadcasts to all ports except the incoming one,
effectively keeping all devices in the same broadcast domain.
The two switches are connected together without VLAN segmentation.
Therefore:
The entire LAN depicted is a single Layer 2 broadcast domain.
There are no routers or VLANs to break or separate the domain.
Correct answer: A. 1
Reference:
Nokia IP Networking Fundamentals Study Guide – Chapter: "LAN Switching and Broadcast Domains"
Cisco and CompTIA Network+ materials on "Hubs vs Switches vs Routers in Broadcast Domains"
Question 13
Which of the following is required if devices on different VLANs wish to communicate with each
other?
- A. They can communicate if they are connected to the same switch.
- B. They can communicate if they are in the same broadcast domain.
- C. They can communicate if there is a router to connect them.
- D. They cannot communicate.
Answer:
C
Explanation:
A Virtual Local Area Network (VLAN) is a logical separation of devices at Layer 2, even if those
devices are connected to the same physical switch. Each VLAN forms its own broadcast domain, and
traffic cannot cross from one VLAN to another without Layer 3 routing.
Option A is incorrect – devices on the same switch but in different VLANs still cannot communicate
directly.
Option B is incorrect – VLANs explicitly create separate broadcast domains.
Option D is technically incorrect – communication is possible with the right setup.
Option C is correct – to enable communication between different VLANs, a router or a Layer 3 switch
with inter-VLAN routing capability is required.
This process is called inter-VLAN routing, and it's a fundamental task in enterprise networks using
VLANs.
Reference:
Nokia IP Networking Fundamentals Study Guide – Chapter: "LAN Segmentation and VLANs"
Cisco CCNA and CompTIA Network+ – Inter-VLAN Routing Concepts
Question 14
Which of the following enables service providers to support multiple customers with the same VLAN
ID over the same backbone?
- A. VLAN Trunking
- B. VLAN Stacking
- C. VLAN Tagging
- D. VLAN Routing
Answer:
B
Explanation:
VLAN Stacking, also known as Q-in-Q tunneling, is a technology that allows multiple customers to
use overlapping VLAN IDs while being transported over a shared service provider network.
Key Concepts:
Customer VLAN (C-VLAN): The VLAN used by the customer in their own network.
Service VLAN (S-VLAN): The VLAN used by the service provider to encapsulate the customer VLAN.
When VLAN stacking is applied:
A customer's Ethernet frame already tagged with a C-VLAN is encapsulated with an additional outer
S-VLAN tag.
This way, multiple customers can use the same C-VLAN ID, but remain isolated by the unique S-VLAN
assigned to them by the service provider.
Why Other Options Are Incorrect:
A . VLAN Trunking: Used to carry multiple VLANs over a single physical link but doesn’t allow reuse of
VLAN IDs across customers.
C . VLAN Tagging: Refers to the general process of adding a VLAN tag; it doesn't provide the isolation
needed across shared infrastructure.
D . VLAN Routing: Refers to Layer 3 routing between VLANs, not to ID reuse or transport over a
shared provider backbone.
Reference:
Nokia Service Architecture and VPNs Study Guide – Section: “Q-in-Q VLAN Stacking”
IEEE 802.1ad Standard – Provider Bridges (Q-in-Q)
Question 15
In which of the following types of network would STP be used?
- A. An MPLS network with multiple LSPs to the same LER.
- B. An Ethernet network with redundant paths.
- C. An OSPF network with multiple equal-cost paths.
- D. An eBGP network with multiple ASes.
Answer:
B
Explanation:
Spanning Tree Protocol (STP) is used specifically in Ethernet Layer 2 networks to prevent loops
caused by redundant paths.
STP detects loops and blocks one or more redundant paths to ensure there is a loop-free topology in
a bridged network.
STP dynamically recalculates the topology if a link fails, reactivating previously blocked paths.
Explanation of other options:
A . MPLS with LSPs: MPLS uses its own mechanisms for path management, such as RSVP or Segment
Routing. STP is not applicable here.
C . OSPF with ECMP (Equal-Cost Multi-Path): OSPF is a Layer 3 protocol that inherently supports
multiple paths without loops; STP is not involved.
D . eBGP (Exterior Border Gateway Protocol): Operates at Layer 3 for inter-AS communication; STP is
not used in BGP routing.
Therefore, Option B is correct, as STP is explicitly designed for Layer 2 Ethernet networks with
redundant paths.
Reference:
Nokia IP Networking Fundamentals Study Guide – Chapter: "Layer 2 Technologies"
IEEE 802.1D Standard – Spanning Tree Protocol Overview