netskope nsk200 practice test
Netskope Certified Cloud Security Integrator (NCCSI)
Question 1
To which three event types does Netskope's REST API v2 provide access? (Choose three.)
- A. application
- B. alert
- C. client
- D. infrastructure
- E. user
Answer:
ABD
Explanation:
Netskope’s REST API v2 provides access to various event types via URI paths. The event types include
application, alert, infrastructure, audit, incident, network, and page. These event types can be used
to retrieve data from Netskope’s cloud security platform. The event types client and user are not
supported by the REST API v2. Reference:
REST API v2 Overview
,
Cribl Netskope Events and Alerts
Integration
,
REST API Events and Alerts Response Descriptions
Question 2
Review the exhibit.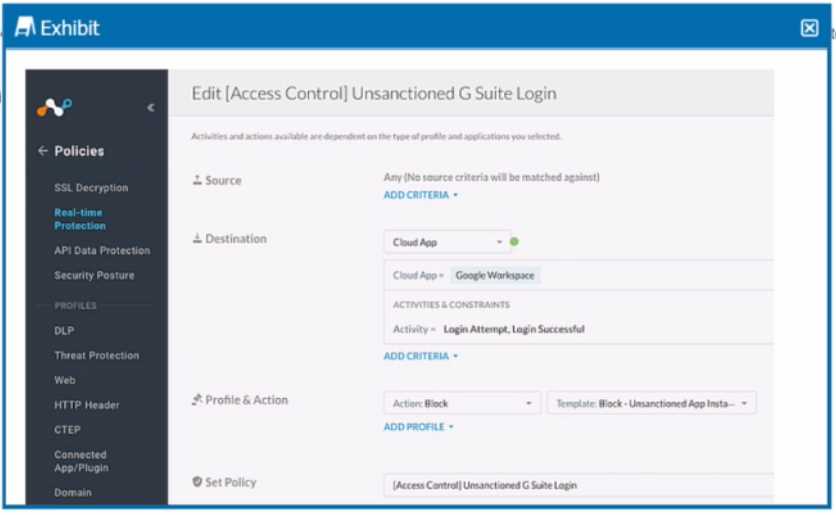
Your company uses Google as the corporate collaboration suite; however, corporate policy restricts
the use of personal Google services. The exhibit provides a partially completed policy to ensure that
users cannot log into their personal account.
What should be added to achieve the desired outcome in this scenario?
- A. Google Gmail app
- B. User Constraint
- C. DLP profile
- D. Device classification
Answer:
B
Explanation:
In order to restrict users from logging into their personal Google accounts, the policy should include
a user constraint. This will ensure that only users with corporate accounts can access the corporate
collaboration suite. The user constraint can be added by selecting the “User” option in the “Source”
field and then choosing the appropriate user group or identity provider. The other options are not
relevant for this scenario. Reference: [Creating a Policy to Block Personal Google Services], [Policy
Creation], [User Constraint]
Question 3
You have deployed a development Web server on a public hosting service using self-signed SSL
certificates. After some troubleshooting, you determined that when the Netskope client is enabled,
you are unable to access the Web server over SSL. The default Netskope tenant steering
configuration is in place.
In this scenario, which two settings are causing this behavior? (Choose two.)
- A. SSL pinned certificates are blocked.
- B. Untrusted root certificates are blocked.
- C. Incomplete certificate trust chains are blocked.
- D. Self-signed server certificates are blocked.
Answer:
BD
Explanation:
The default Netskope tenant steering configuration blocks untrusted root certificates and self-signed
server certificates. These settings are intended to prevent man-in-the-middle attacks and ensure the
validity of the SSL connection. However, they also prevent the access to the development Web server
that uses self-signed SSL certificates. To allow access to the Web server, the settings need to be
changed or an exception needs to be added for the Web server domain.
Question 4
Your customer currently only allows users to access the corporate instance of OneDrive using SSO
with the Netskope client. The users are not permitted to take their laptops when vacationing, but
sometimes they must have access to documents on OneDrive when there is an urgent request. The
customer wants to allow employees to remotely access OneDrive from unmanaged devices while
enforcing DLP controls to prohibit downloading sensitive files to unmanaged devices.
Which steering method would satisfy the requirements for this scenario?
- A. Use a reverse proxy integrated with their SSO.
- B. Use proxy chaining with their cloud service providers integrated with their SSO.
- C. Use a forward proxy integrated with their SSO.
- D. Use a secure forwarder integrated with an on-premises proxy.
Answer:
A
Explanation:
A reverse proxy integrated with their SSO would satisfy the requirements for this scenario. A reverse
proxy intercepts requests from users to cloud apps and applies policies based on user identity, device
posture, app, and data context. It can enforce DLP controls to prohibit downloading sensitive files to
unmanaged devices. It can also integrate with the customer’s SSO provider to authenticate users and
allow access only to the corporate instance of OneDrive. The other steering methods are not suitable
for this scenario because they either require the Netskope client or do not provide granular control
over cloud app activities.
Question 5
An engineering firm is using Netskope DLP to identify and block sensitive documents, including
schematics and drawings. Lately, they have identified that when these documents are blocked,
certain employees may be taking screenshots and uploading them. They want to block any
screenshots from being uploaded.
Which feature would you use to satisfy this requirement?
- A. exact data match (EDM)
- B. document fingerprinting
- C. ML image classifier
- D. optical character recognition (OCR)
Answer:
C
Explanation:
To block any screenshots from being uploaded, the engineering firm should use the ML image
classifier feature of Netskope DLP. This feature uses machine learning to detect sensitive information
within images, such as screenshots, whiteboards, passports, driver’s licenses, etc. The firm can
create a DLP policy that blocks any image upload that matches the screenshot classifier. This will
prevent employees from circumventing the DLP controls by taking screenshots of sensitive
documents. Reference:
Improved DLP Image Classifiers
,
Netskope Data Loss Prevention
,
The
Importance of a Machine Learning-Based Source Code Classifier
Question 6
Review the exhibit.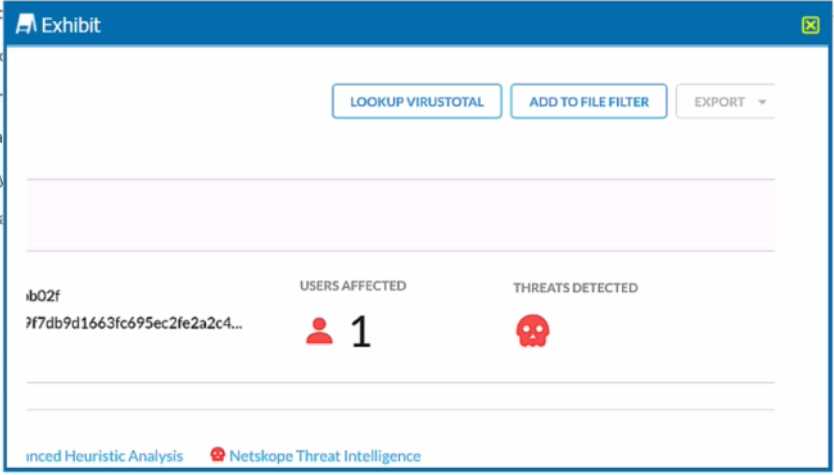
You are at the Malware Incident page. A virus was detected by the Netskope Heuristics Engine. Your
security team has confirmed that the virus was a test data file You want to allow the security team to
use this file
Referring to the exhibit, which two statements are correct? (Choose two.)
- A. Click the "Add To File Filter button to add the IOC to a file list.
- B. Contact the CrowdStrike administrator to have the file marked as safe.
- C. Click the ''Lookup VirusTotal" button to verify if this IOC is a false positive.
- D. Create a malware detection profile and update the file hash list with the IOC.
Answer:
AC
Explanation:
To allow the security team to use the test data file that was detected as a virus by the Netskope
Heuristics Engine, the following two steps are correct:
Click the “Add To File Filter” button to add the IOC to a file list. This will exclude the file from future
malware scans and prevent false positive alerts.
The file list can be managed in the Settings > File
Filter page1
.
Click the “Lookup VirusTotal” button to verify if this IOC is a false positive. This will open a new tab
with the VirusTotal report for the file hash. VirusTotal is a service that analyzes files and URLs for
viruses, worms, trojans, and other kinds of malicious content.
The report will show how many
antivirus engines detected the file as malicious and provide additional information about the file2
.
https://docs.netskope.com/en/netskope-help/admin-console/incidents/
Question 7
Which object would be selected when creating a Malware Detection profile?
- A. DLP profile
- B. File profile
- C. Domain profile
- D. User profile
Answer:
B
Explanation:
A file profile is an object that contains a list of file hashes that can be used to create a malware
detection profile. A file profile can be configured as an allowlist or a blocklist, depending on whether
the files are known to be benign or malicious.
A file profile can be created in the Settings > File Profile
page1
. A malware detection profile is a set of rules that define how Netskope handles malware
incidents.
A malware detection profile can be created in the Policies > Threat Protection > Malware
Detection Profiles page2
. To create a malware detection profile, one needs to select a file profile as
an allowlist or a blocklist, along with the Netskope malware scan option. The other options are not
objects that can be selected when creating a malware detection profile.
Question 8
Your learn is asked to Investigate which of the Netskope DLP policies are creating the most incidents.
In this scenario, which two statements are true? (Choose two.)
- A. The Skope IT Applications tab will list the top five DLP policies.
- B. You can see the top Ave DLP policies triggered using the Analyze feature
- C. You can create a report using Reporting or Advanced Analytics.
- D. The Skope IT Alerts tab will list the top five DLP policies.
Answer:
BC
Explanation:
To investigate which of the Netskope DLP policies are creating the most incidents, the following two
statements are true:
You can see the top five DLP policies triggered using the Analyze feature. The Analyze feature allows
you to create custom dashboards and widgets to visualize and explore your data.
You can use the DLP
Policy widget to see the top five DLP policies that generated the most incidents in a given time
period3
.
You can create a report using Reporting or Advanced Analytics. The Reporting feature allows you to
create scheduled or ad-hoc reports based on predefined templates or custom queries.
You can use
the DLP Incidents by Policy template to generate a report that shows the number of incidents per
DLP policy4
. The Advanced Analytics feature allows you to run SQL queries on your data and export
the results as CSV or JSON files.
You can use the DLP_INCIDENTS table to query the data by policy
name and incident count5
.
The other two statements are not true because:
The Skope IT Applications tab will not list the top five DLP policies. The Skope IT Applications tab
shows the cloud app usage and risk summary for your organization.
It does not show any information
about DLP policies or incidents6
.
The Skope IT Alerts tab will not list the top five DLP policies. The Skope IT Alerts tab shows the alerts
generated by various policies and profiles, such as DLP, threat protection, IPS, etc.
It does not show
the number of incidents per policy, only the number of alerts per incident7
.
Question 9
You want to secure Microsoft Exchange and Gmail SMTP traffic for DLP using Netskope. Which
statement is true about this scenario when using the Netskope client?
- A. Netskope can inspect outbound SMTP traffic for Microsoft Exchange and Gmail.
- B. Enable Cloud Firewall to Inspect Inbound SMTP traffic for Microsoft Exchange and Gmail.
- C. Netskope can inspect inbound and outbound SMTP traffic for Microsoft Exchange and Gmail.
- D. Enable REST API v2 to Inspect inbound SMTP traffic for Microsoft Exchange and Gmail.
Answer:
A
Explanation:
Netskope can inspect outbound SMTP traffic for Microsoft Exchange and Gmail using the Netskope
client. The Netskope client intercepts the SMTP traffic from the user’s device and forwards it to the
Netskope cloud for DLP scanning. The Netskope client does not inspect inbound SMTP traffic, as this
is handled by the cloud email service or the MTA. Therefore, option A is correct and the other options
are incorrect. Reference:
Configure Netskope SMTP Proxy with Microsoft O365 Exchange
,
Configure
Netskope SMTP Proxy with Gmail
,
SMTP DLP
,
Best Practices for Email Security with SMTP proxy
Question 10
Your company needs to keep quarantined files that have been triggered by a DLP policy. In this
scenario, which statement Is true?
- A. The files are stofed remotely In your data center assigned In the Quarantine profile.
- B. The files are stored In the Netskope data center assigned in the Quarantine profile.
- C. The files are stored In the Cloud provider assigned In the Quarantine profile.
- D. The files are stored on the administrator console PC assigned In the Quarantine profile.
Answer:
B
Explanation:
When a policy flags a file to be quarantined, that file is placed in a quarantine folder and a tombstone
file is put in the original location in its place. The quarantine folder is located in the Netskope data
center assigned in the Quarantine profile. The Quarantine profile is configured in Settings > Threat
Protection > API-enabled Protection. The quarantined file is zipped and protected with a password to
prevent users from inadvertently downloading the file.
Netskope then notifies the admin specified in
the profile1
. Therefore, option B is correct and the other options are
incorrect. Reference:
Quarantine - Netskope Knowledge Portal
,
Threat Protection - Netskope
Knowledge Portal
Question 11
Review the exhibit.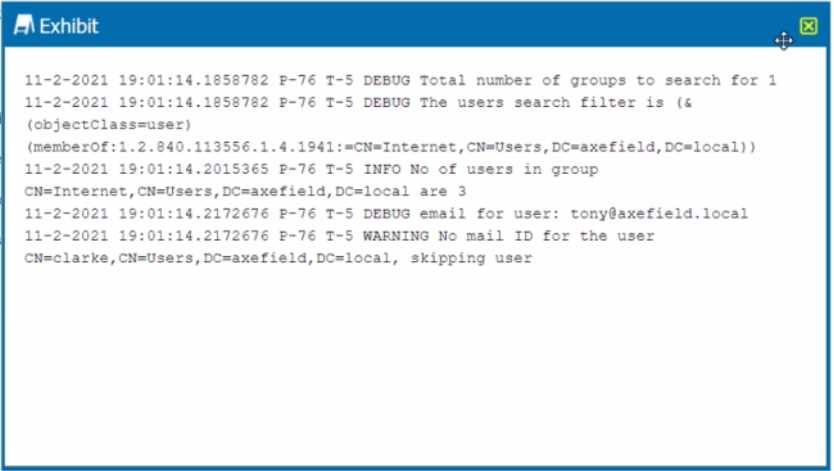
You are troubleshooting a Netskope client for user Clarke which remains in a disabled state after
being installed. After looking at various logs, you notice something which might explain the problem.
The exhibit is an excerpt from the nsADImporterLog.log.
Referring to the exhibit, what is the problem?
- A. The client was not Installed with administrative privileges.
- B. The Active Directory user is not synchronized to the Netskope tenant.
- C. This is normal; it might take up to an hour to be enabled.
- D. The client traffic is decrypted by a network security device.
Answer:
B
Explanation:
The problem is B. The Active Directory user is not synchronized to the Netskope tenant. This is
evident from the log message “WARNING No mail ID for the user: Clarke, Daxmeifield, DC=local,
skipping use”. This means that the user Clarke does not have a valid email address in the Active
Directory, which is required for the Netskope client to work. The Netskope client uses the email
address of the user to authenticate and enable the client. Therefore, option B is correct and the other
options are incorrect.
Question 12
You are having issues with fetching user and group Information periodically from the domain
controller and posting that information to your tenant instance in the Netskope cloud. To begin the
troubleshooting process, what would you Investigate first in this situation?
- A. On-Premises Log Parser
- B. Directory Importer
- C. DNS Connector
- D. AD Connector
Answer:
B
Explanation:
The Directory Importer is a component of the Netskope Adapters that connects to the domain
controller and periodically fetches user and group information to post that info to your tenant
instance in the Netskope cloud1
. If you are having issues with this process, the first thing you should
investigate is the Directory Importer itself.
You can check the status of the Directory Importer service,
the configuration file, the logs, and the connectivity to the domain controller and the Netskope
cloud2
. Therefore, option B is correct and the other options are incorrect. Reference:
Configure
Directory Importer - Netskope Knowledge Portal
,
Troubleshooting Directory Importer - Netskope
Knowledge Portal
Question 13
You are troubleshooting an issue with Microsoft where some users complain about an issue
accessing OneDrive and SharePoint Online. The configuration has the Netskope client deployed and
active for most users, but some Linux machines are routed to Netskope using GRE tunnels. You need
to disable inspection for all users to begin troubleshooting the issue.
In this scenario, how would you accomplish this task?
- A. Create a Real-time Protection policy to isolate Microsoft 365.
- B. Create a Do Not Decrypt SSL policy for the Microsoft 365 App Suite.
- C. Create a steering exception for the Microsoft 365 domains.
- D. Create a Do Not Decrypt SSL policy for OneDrive.
Answer:
B
Explanation:
To disable inspection for all users accessing Microsoft 365, you need to create a Do Not Decrypt SSL
policy for the Microsoft 365 App Suite.
This policy will prevent Netskope from decrypting and
analyzing the traffic for any Microsoft 365 app, regardless of the access method (Netskope client or
GRE tunnel)3
.
This policy will also allow SNI-based policies to apply, but no deep analysis performed
via Real-time Protection policies4
. Therefore, option B is correct and the other options are
incorrect. Reference:
Add a Policy for SSL Decryption - Netskope Knowledge Portal
,
Default Microsoft
appsuite SSL do not decrypt rule - Netskope Community
Question 14
Your company has many users that are remote and travel often. You want to provide the greatest
visibility into their activities, even while traveling. Using Netskope. which deployment method would
be used in this scenario?
- A. Use proxy chaining.
- B. Use a Netskope client.
- C. Use an IPsec tunnel.
- D. Use a GRE tunnel.
Answer:
B
Explanation:
The best deployment method for remote and traveling users is to use a Netskope client.
The
Netskope client is a lightweight software agent that runs on the user’s device and steers web and
cloud traffic to the Netskope cloud for real-time inspection and policy enforcement1
.
The Netskope
client provides an always-on end user remote access experience and avoids backhauling (or
hairpinning) remote users through the corporate network to access applications in public cloud
environments2
.
The Netskope client also supports offline mode, which allows users to work offline
and sync their policies when they reconnect to the internet
Question 15
Your company has Microsoft Azure ADFS set up as the Identity Provider (idP). You need to deploy the
Netskope client to all company users on Windows laptops without user intervention.
In this scenario, which two deployment options would you use? (Choose two.)
- A. Deploy the Netskope client with SCCM.
- B. Deploy the Netskope client with Microsoft GPO.
- C. Deploy the Netskope client using IdP.
- D. Deploy the Netskope client using an email Invitation.
Answer:
AB
Explanation:
To deploy the Netskope client to all company users on Windows laptops without user intervention,
you can use either SCCM or GPO.
These are two methods of packaging the application and pushing it
silently to the user’s device using Microsoft tools4
. These methods do not require the user to have
local admin privileges or to initiate the installation themselves. They also allow enforcing the use of
the client through company policy.
The Netskope client can authenticate the user using Azure ADFS
as the identity provider, as long as the UPN of the logged in user matches the directory5