microsoft sc-900 practice test
Microsoft Security. Compliance and Identity Fundamentals
Question 1 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
DRAG DROP
Match the Microsoft 365 insider risk management workflow step to the appropriate task.
To answer, drag the appropriate step from the column on the left to its task on the right. Each step may be used once, more
than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place: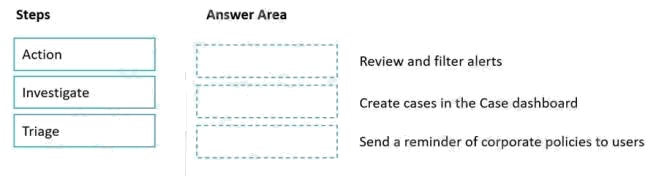
Answer:
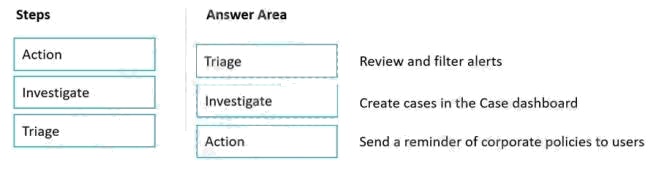
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/insider-risk-management?view=o365-worldwide
Question 2 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: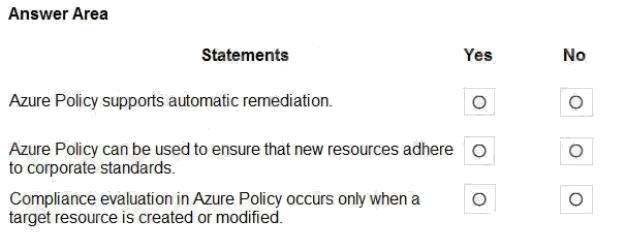
Answer:
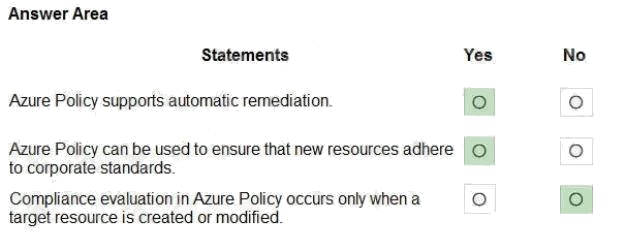
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/governance/policy/overview
Question 3 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:

Explanation:
Box 1: No
Phishing scams are external threats.
Box 2: Yes
Insider risk management is a compliance solution in Microsoft 365.
Box 3: Yes
Insider risk management helps minimize internal risks from users. These include:
Leaks of sensitive data and data spillage
Confidentiality violations
Intellectual property (IP) theft
Fraud
Insider trading
Regulatory compliance violations
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/insider-risk-management?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/microsoft-365-compliance-center?view=o365-worldwide
Question 4 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: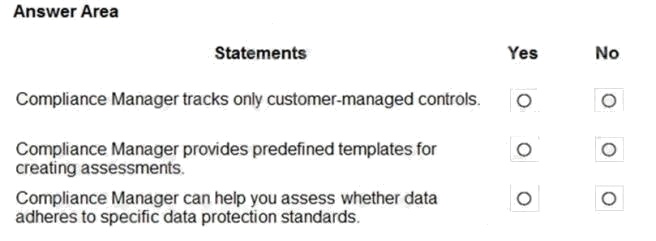
Answer:
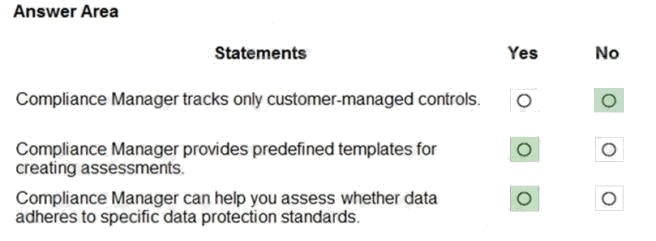
Explanation:
Box 1: No
Compliance Manager tracks Microsoft managed controls, customer-managed controls, and shared controls.
Box 2: Yes
Box 3: Yes
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide
Question 5 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
Which Microsoft 365 compliance feature can you use to encrypt content automatically based on specific conditions?
- A. Content Search
- B. sensitivity labels
- C. retention policies
- D. eDiscovery
Answer:
B
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
Question 6 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: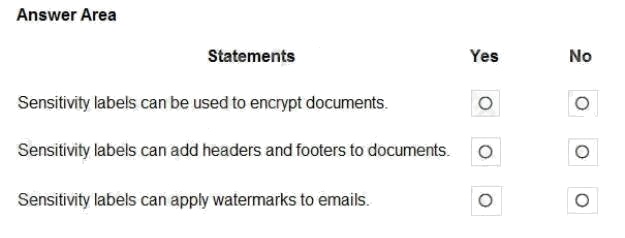
Answer:
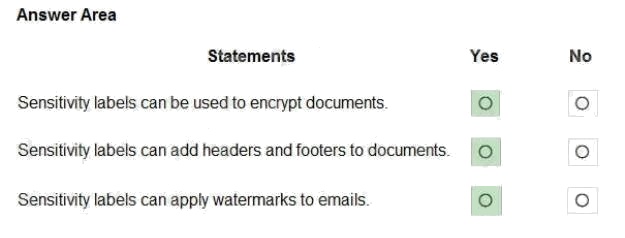
Explanation:
Box 1: Yes
You can use sensitivity labels to provide protection settings that include encryption of emails and documents to prevent
unauthorized people from accessing this data.
Box 2: Yes
You can use sensitivity labels to mark the content when you use Office apps, by adding watermarks, headers, or footers to
documents that have the label applied.
Box 3: Yes
You can use sensitivity labels to mark the content when you use Office apps, by adding headers, or footers to email that
have the label applied.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
Question 7 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:
Answer:
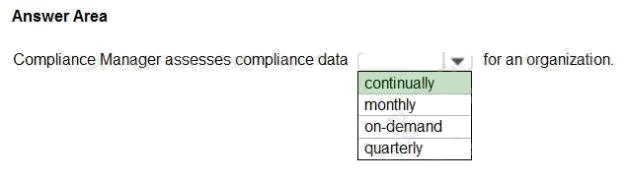
Explanation:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation?view=o365worldwide#how-
compliance-manager-continuously-assesses-controls
Question 8 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
Which two tasks can you implement by using data loss prevention (DLP) policies in Microsoft 365? Each correct answer
presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Display policy tips to users who are about to violate your organization’s policies.
- B. Enable disk encryption on endpoints.
- C. Protect documents in Microsoft OneDrive that contain sensitive information.
- D. Apply security baselines to devices.
Answer:
A C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
Question 9 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: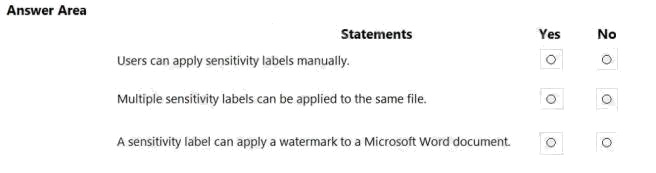
Answer:
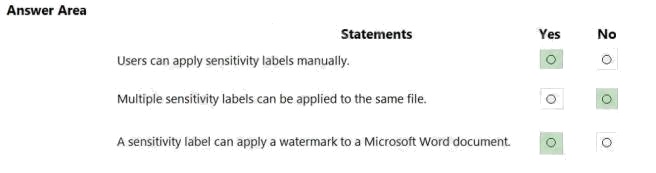
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-sensitivity-labels?view=o365-
worldwide
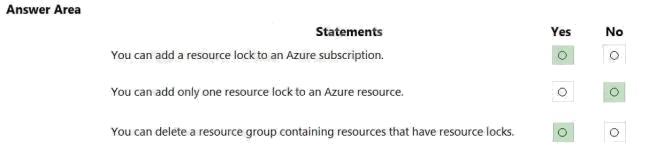
Question 10 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: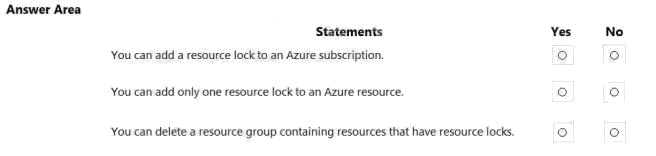
Answer:
Question 11 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: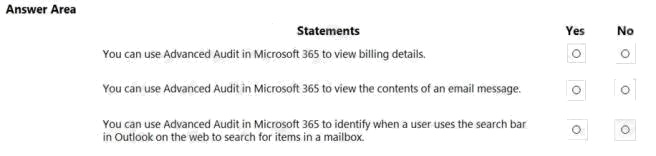
Answer:
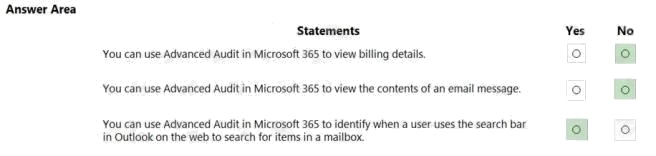
Explanation:
Box 1: No
Advanced Audit helps organizations to conduct forensic and compliance investigations by increasing audit log retention.
Box 2: No Box 3: Yes
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/advanced-audit?view=o365-worldwide
Question 12 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
What can you specify in Microsoft 365 sensitivity labels?
- A. how long files must be preserved
- B. when to archive an email message
- C. which watermark to add to files
- D. where to store files
Answer:
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
Question 13 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
What can you protect by using the information protection solution in the Microsoft 365 compliance center?
- A. computers from zero-day exploits
- B. users from phishing attempts
- C. files from malware and viruses
- D. sensitive data from being exposed to unauthorized users
Answer:
D
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
Question 14 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
Which Microsoft portal provides information about how Microsoft manages privacy, compliance, and security?
- A. Microsoft Service Trust Portal
- B. Compliance Manager
- C. Microsoft 365 compliance center
- D. Microsoft Support
Answer:
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-service-trust-portal?view=o365-
worldwide
Question 15 Topic 4, Describe the Capabilities of Microsoft Compliance Solutions
In a Core eDiscovery workflow, what should you do before you can search for content?
- A. Create an eDiscovery hold.
- B. Run Express Analysis.
- C. Configure attorney-client privilege detection.
- D. Export and download results.
Answer:
A
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-core-ediscovery?view=o365-worldwide
triage
investigate
action