The default retention period for Audit (Standard) has changed from 90 days to 180 days. Audit (Standard) logs generated before October 17, 2023 are retained for 90 days.
https://learn.microsoft.com/en-us/purview/audit-get-started
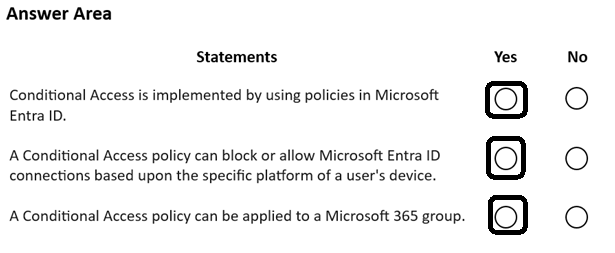
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.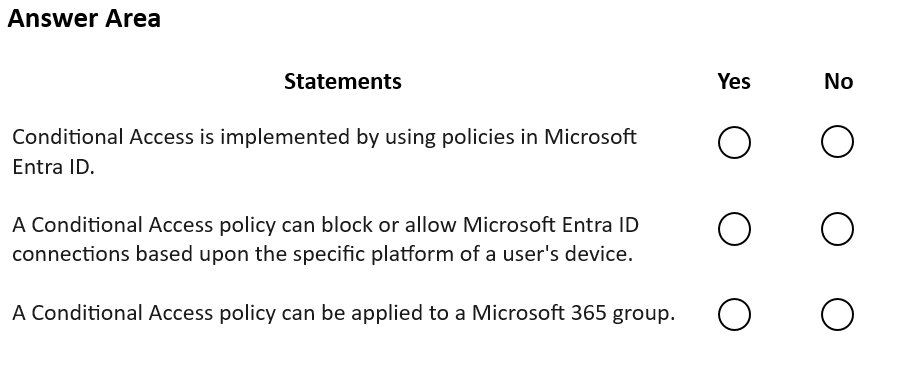
DRAG DROP Match the Microsoft 365 insider risk management workflow step to the appropriate task.
To answer, drag the appropriate step from the column on the left to its task on the right. Each step may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place: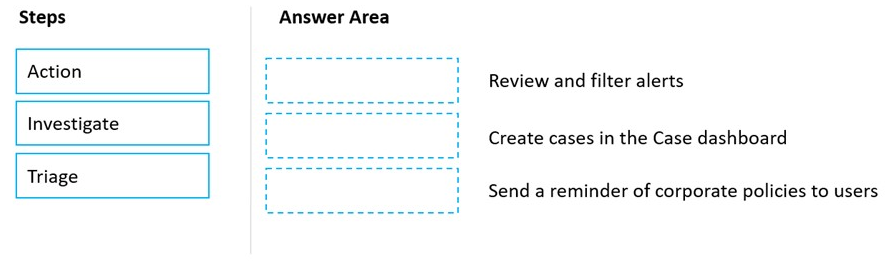
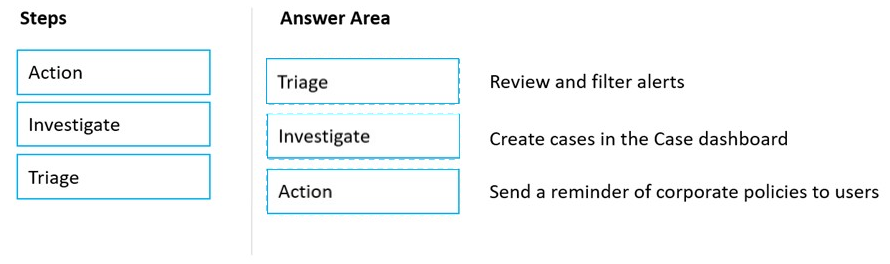
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/insider-risk-management?view=o365-worldwide
What is a use case for implementing information barrier policies in Microsoft 365?
c
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-barriers-policies?view=o365-worldwide
HOTSPOT
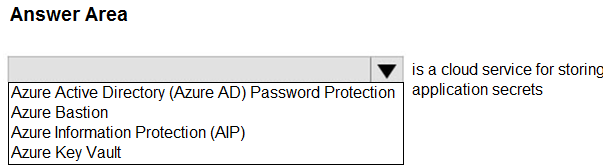
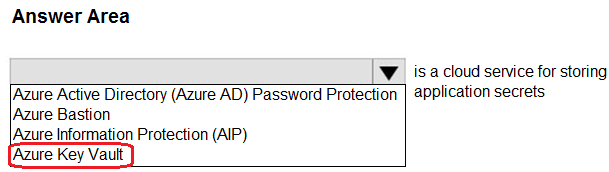
Select the answer that correctly completes the sentence.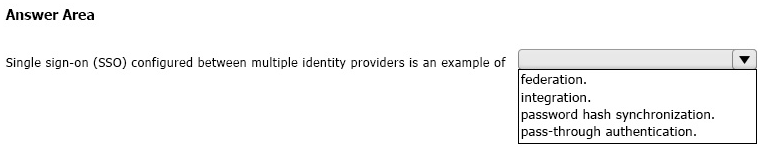
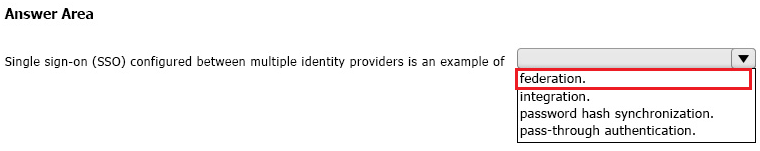
HOTSPOT
Select the answer that correctly completes the sentence.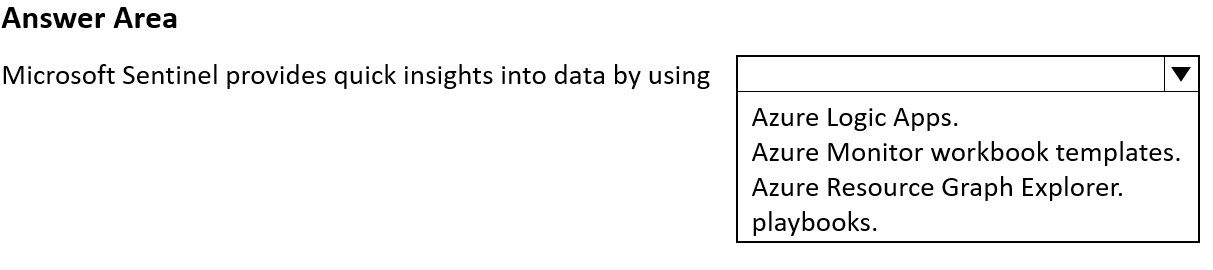
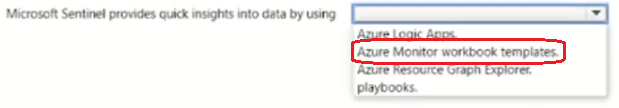
You have a Microsoft 365 E3 subscription.
You plan to audit user activity by using the unified audit log and Basic Audit.
For how long will the audit records be retained?
c
The default retention period for Audit (Standard) has changed from 90 days to 180 days. Audit (Standard) logs generated before October 17, 2023 are retained for 90 days.
https://learn.microsoft.com/en-us/purview/audit-get-started
HOTSPOT For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: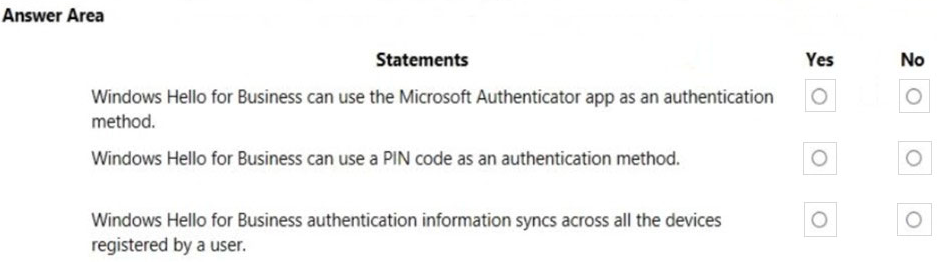
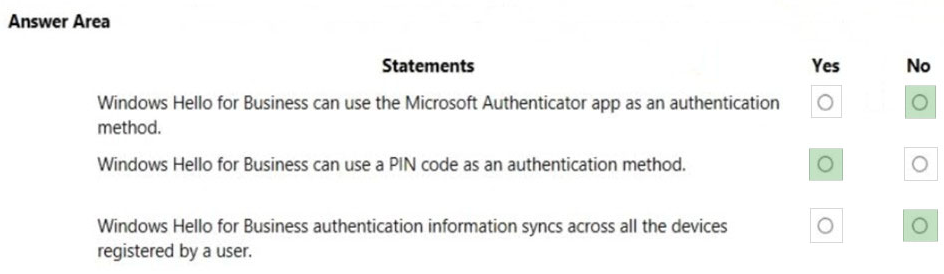
Box 1: No -
The Microsoft Authenticator app helps you sign in to your accounts when you're using two-factor verification. Two-factor verification helps you to use your accounts more securely because passwords can be forgotten, stolen, or compromised. Two-factor verification uses a second factor like your phone to make it harder for other people to break in to your account.
Box 2: Yes -
In Windows 10, Windows Hello for Business replaces passwords with strong two-factor authentication on devices. This authentication consists of a new type of user credential that is tied to a device and uses a biometric or PIN.
Box 3: No -
Windows Hello credentials are based on certificate or asymmetrical key pair. Windows Hello credentials can be bound to the device, and the token that is obtained using the credential is also bound to the device.
Reference:
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview
Which two Azure resources can a network security group (NSG) be associated with? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
ab
Association of network security groups
You can associate a network security group with virtual machines, NICs, and subnets, depending on the deployment model you use.
Reference:
https://aviatrix.com/learn-center/cloud-security/create-network-security-groups-in-azure/
DRAG DROP You are evaluating the compliance score in Compliance Manager.
Match the compliance score action subcategories to the appropriate actions.
To answer, drag the appropriate action subcategory from the column on the left to its action on the right. Each action subcategory may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place:
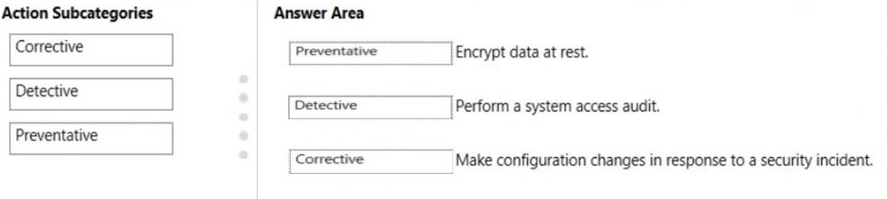
Box 1: Preventative -
Preventative actions address specific risks. For example, protecting information at rest using encryption is a preventative action against attacks and breaches.
Separation of duties is a preventative action to manage conflict of interest and guard against fraud.
Box 2: Detective -
Detective actions actively monitor systems to identify irregular conditions or behaviors that represent risk, or that can be used to detect intrusions or breaches.
Examples include system access auditing and privileged administrative actions. Regulatory compliance audits are a type of detective action used to find process issues.
Box 3: Corrective -
Corrective actions try to keep the adverse effects of a security incident to a minimum, take corrective action to reduce the immediate effect, and reverse the damage if possible. Privacy incident response is a corrective action to limit damage and restore systems to an operational state after a breach.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation
HOTSPOT
Select the answer that correctly completes the sentence.