microsoft az-220 practice test
Microsoft Azure IoT Developer
Note: Test Case questions are at the end of the exam
Question 1 Topic 4, Mixed Questions
You have IoT devices that connect to an Azure IoT hub.
From IoT Hub, you create an Event subscription to be notified when devices are registered to IoT Hub. You select webhook
endpoint as a handler for the Event subscription.
Which two types of Event Grid messages will be received by the webhook? Each correct answer presents a complete
solution.
NOTE: Each correct selection is worth one point.
- A. Microsoft.Devices.DeviceCreated
- B. Microsoft.Resources.ResourceWriteSuccess
- C. Microsoft.EventGrid.SubscriptionValidationEvent
- D. Microsoft.Devices.DeviceConnected
Answer:
A C
Explanation:
Microsoft.Devices.DeviceCreated: Published when a device is registered to an IoT hub.
The first thing you want to do is handle Microsoft.EventGrid.SubscriptionValidationEvent events. Every time someone
subscribes to an event, Event Grid sends a validation event to the endpoint with a validationCode in the data payload.
Reference:
https://docs.microsoft.com/en-us/azure/iot-hub/iot-hub-event-grid https://docs.microsoft.com/en-us/azure/event-grid/receive-
events
Question 2 Topic 4, Mixed Questions
You need to route events in Azure Digital Twins to a downstream service for additional processing.
Which type of output endpoint can you use?
- A. Azure Event Hubs
- B. Azure Queue storage
- C. Microsoft Power BI
- D. Azure Table storage
Answer:
A
Explanation:
Create an endpoint for Azure Digital Twins.
These are the supported types of endpoints that you can create for your instance: Event Grid
Event Hubs
Service Bus
Note: In Azure Digital Twins, you can route event notifications to downstream services or connected compute resources.
This is done by first setting up endpoints that can receive the events. You can then create event routes that specify which
events generated by Azure Digital Twins are delivered to which endpoints. Reference:
https://docs.microsoft.com/en-us/azure/digital-twins/how-to-manage-routes
Question 3 Topic 4, Mixed Questions
You have an Azure IoT solution.
You need to create a digital twin model.
Which language should you use?
- A. XHTML
- B. DTDL
- C. YAML
- D. XML
Answer:
B
Explanation:
Azure Digital Twins models are represented in the JSON-LD-based Digital Twin Definition Language (DTDL). Reference:
https://docs.microsoft.com/en-us/azure/digital-twins/concepts-models
Question 4 Topic 4, Mixed Questions
You deploy an Azure Digital Twins instance.
You are developing client code that will modify digital twin data.
You run the client code and receive the following response for an Azure Digital Twins API.
403 (Forbidden)
You need to configure access control for the Azure Digital Twins instance to ensure that the client code can modify the data.
Which role should you assign?
- A. Contributor
- B. Azure Digital Twins Data Owner
- C. Owner
- D. Managed Application Operator Role
Answer:
B
Explanation:
Most often, this error indicates that your Azure role-based access control (Azure RBAC) permissions for the service aren't
set up correctly. Many actions for an Azure Digital Twins instance require you to have the Azure Digital Twins Data Owner
role on the instance you are trying to manage. Reference:
https://docs.microsoft.com/en-us/azure/digital-twins/troubleshoot-error-403
Question 5 Topic 4, Mixed Questions
You need to recommend a solution to keep device properties synced to IoT Hub. The solution must minimize data loss
caused by the connectivity issues.
What should you include in the recommendation?
- A. Azure Event Grid
- B. a cloud-to-device message
- C. IoT Hub device twins
- D. the IoT Hub direct method
Answer:
C
Explanation:
Scenario: You discover connectivity issues between the IoT gateway devices and iothub1, which cause IoT devices to lose
connectivity and messages.
To synchronize state information between a device and an IoT hub, you use device twins. A device twin is a JSON
document, associated with a specific device, and stored by IoT Hub in the cloud where you can query them. A device twin
contains desired properties, reported properties, and tags. Reference:
https://docs.microsoft.com/en-us/azure/iot-hub/tutorial-device-twins
Question 6 Topic 4, Mixed Questions
You have an Azure IoT hub that is being taken from prototype to production.
You plan to connect IoT devices to the IoT hub. The devices have hardware security modules (HSMs).
You need to use the most secure authentication method between the devices and the IoT hub. Company policy prohibits the
use of internally generated certificates.
Which authentication method should you use?
- A. an X.509 self-signed certificate
- B. a certificate thumbprint
- C. a symmetric key
- D. An X.509 certificate signed by a root certification authority (CA).
Answer:
D
Explanation:
Purchase X.509 certificates from a root certificate authority (CA). This method is recommended for production environments.
The hardware security module, or HSM, is used for secure, hardware-based storage of device secrets, and is the most
secure form of secret storage. Both X.509 certificates and SAS tokens can be stored in the HSM Reference:
https://docs.microsoft.com/en-us/azure/iot-dps/concepts-security
Question 7 Topic 4, Mixed Questions
You have an Azure IoT solution that includes an Azure IoT hub, 100 Azure IoT Edge devices, and 500 leaf devices.
You need to perform a key rotation across the devices.
Which three types of entities should you update? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. the $edgeHub module identity
- B. the $edgeAgent module identity
- C. the leaf module identities
- D. the IoT Edge device identities
- E. the iothubowner policy credentials
- F. the leaf device identities
Answer:
A D F
Explanation:
To get authorization to connect to IoT Hub, devices and services must send security tokens signed with either a shared
access or symmetric key. These keys are stored with a device identity in the identity registry.
An IoT Hub identity registry can be accessed like a dictionary, by using the deviceId or moduleId as the key. Reference:
https://docs.microsoft.com/bs-latn-ba/azure/iot-dps/how-to-control-access https://docs.microsoft.com/en-us/azure/iot-hub/iot-
hub-devguide-identity-registry
Question 8 Topic 4, Mixed Questions
You enable Azure Security Center for IoT.
You need to onboard a device to Azure Security Center.
What should you do?
- A. Add the azureiotsecurity module identity to the Azure IoT Hub device identity.
- B. Open incoming TCP port 8883 on the device.
- C. Modify the connection string of the device.
- D. Install an X.509 certificate on the hardware security module (HSM) of the device.
Answer:
A
Explanation:
Use the following workflow to deploy and test your Azure Security Center for IoT security agents:
1. Enable Azure Security Center for IoT service to your IoT Hub
2. If your IoT Hub has no registered devices, Register a new device.
3. Create an azureiotsecurity security module for your devices.
Azure Security Center for IoT makes use of the module twin mechanism and maintains a security module twin named
azureiotsecurity for each of your devices.
Note: To manually create a new azureiotsecurity module twin for a device use the following instructions:
1. In your IoT Hub, locate and select the device you wish to create a security module twin for.
2. Click on your device, and then on Add module identity.
3. In the Module Identity Name field, enter azureiotsecurity.
4. Click Save. Reference:
https://docs.microsoft.com/en-us/azure/asc-for-iot/quickstart-create-security-twin
Question 9 Topic 4, Mixed Questions
You have an Azure IoT Edge device.
You need to modify the credentials used to access the container registry.
What should you modify?
- A. the $edgeHub module twin
- B. the IoT Edge module
- C. the $edgeAgent module twin
- D. the Azure IoT Hub device twin
Answer:
C
Explanation:
The module twin for the IoT Edge agent is called $edgeAgent and coordinates the communications between the IoT Edge
agent running on a device and IoT Hub. The desired properties are set when applying a deployment manifest on a specific
device as part of a single-device or at-scale deployment.
These properties include:
runtime.settings.registryCredentials.{registryId}.username runtime.settings.registryCredentials.registryId}.password
Reference:
https://docs.microsoft.com/en-us/azure/iot-edge/module-edgeagent-edgehub
Question 10 Topic 4, Mixed Questions
HOTSPOT
You are planning a proof of concept (POC) that will use an Azure IoT hub.
You have two self-signed client authentication certificates named Cert1 and Cert2. Cert1 has a basic constraint that contains
Subject Type=CA. Cert2 has a basic constraint that contains Subject Type=End Entity.
You need to identify which certificates to use.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: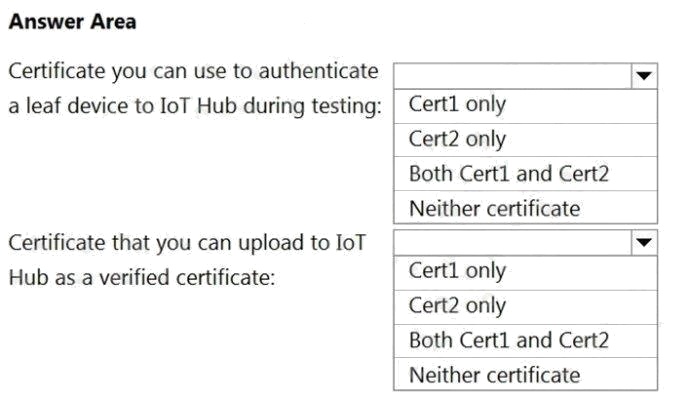
Answer:
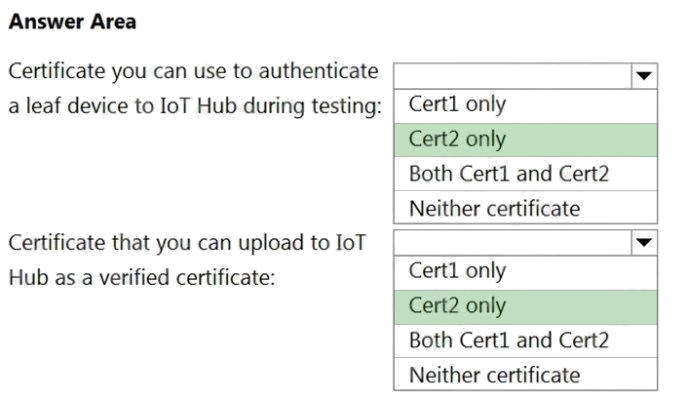
Explanation:
Box 1: Cert2 only
Cert2: The leaf certificate, or end-entity certificate, identifies the certificate holder. It has the root certificate in its certificate
chain as well as zero or more intermediate certificates. The leaf certificate is not used to sign any other certificates. It
uniquely identifies the device to the provisioning service and is sometimes referred to as the device certificate.
Box 2: Cert1 only
Cert1: A root certificate is a self-signed X.509 certificate representing a certificate authority (CA). It is the terminus, or trust
anchor, of the certificate chain. Root certificates can be self-issued by an organization or purchased from a root certificate
authority.
Reference:
https://docs.microsoft.com/en-us/azure/iot-dps/concepts-x509-attestation
Question 11 Topic 4, Mixed Questions
You have an Azure IoT hub that has a hostname of contoso-hub.azure-devices.net and an MCU-based IoT device named
Device1. Device1 does NOT support Azure IoT SDKs.
You plan to connect Device1 to the IoT hub by using the Message Queuing Telemetry Transport (MQTT) protocol and to
authenticate by using X.509 certificates.
You need to ensure that Device1 can authenticate to the IoT hub.
What should you do?
- A. Create an Azure key vault and enable the encryption of data at rest for the IoT hub by using a customer-managed key.
- B. Enable a hardware security module (HSM) on Device1.
- C. From the Azure portal, create an IoT Hub Device Provisioning Service (DPS) instance and add a certificate enrollment for Device1.
- D. Add the DigiCert Baltimore Root Certificate to Device1.
Answer:
D
Explanation:
The connection to Azure IoT Hub with MQTT is secured using TLS.
The Azure IoT Hub library requires the provisioning of the following certificates and a private key for a successful TLS
connection:
1. Baltimore CyberTrust Root certificate - Server certificate, used to verify the servers certificate while connecting.
2. Device certificate - generated by the procedures described in Creating Azure IoT Hub certificates , used by Azure IoT Hub
to authenticate the device.
3. Private key of the device. Reference:
https://developer.nordicsemi.com/nRF_Connect_SDK/doc/latest/nrf/include/net/azure_iot_hub.html
Question 12 Topic 4, Mixed Questions
DRAG DROP
You have an Azure IoT Edge solution.
You plan to deploy an Azure Security Center for IoT security agent. You need to configure the security agent to meet the
following requirements:
Connection events must be reported as high priority.
High priority events must be collected every seven minutes.
How should you configure the azureiotsecurity module twin? To answer, drag the appropriate values to the correct locations.
Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to
view content.
NOTE: Each correct selection is worth one point.
Select and Place: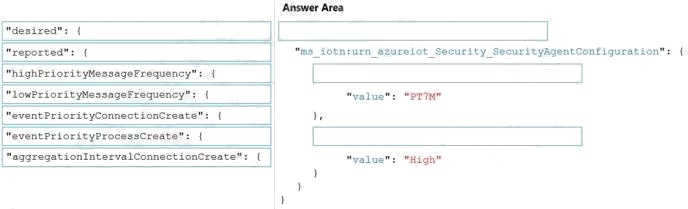
Answer:
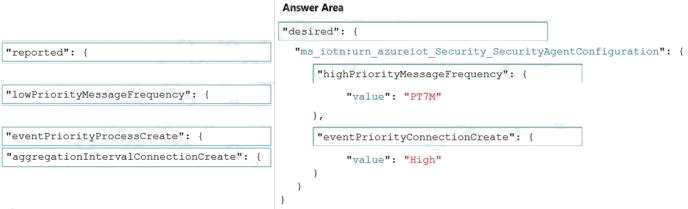
Explanation:
Box 1: "desired": {
To configure connection events as high priority and collect high priority events every 7 minutes, use the following
configuration.
"desired": {
"ms_iotn:urn_azureiot_Security_SecurityAgentConfiguration": {
"highPriorityMessageFrequency": {
"value": "PT7M"
},
"eventPriorityConnectionCreate": {
"value": "High"
}
Box 2: "highPriorityMessageFrequency ": {
Box 3: "eventPriorityConnectionCreate": {
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-iot/how-to-agent-configuration
Question 13 Topic 4, Mixed Questions
From the Device Provisioning Service, you create an enrollment as shown in the exhibit.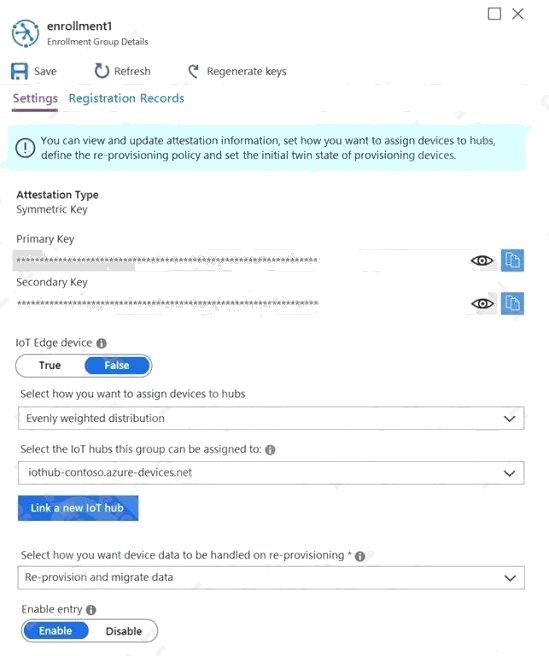
You need to deploy a new IoT device.
What should you use as the device identity during attestation?
- A. a self-signed X.509 certificate
- B. the random string of alphanumeric characters
- C. the HMAC-SHA256 hash of the device's registration ID
- D. the endorsement key of the device's Trusted Platform Module (TPM)
Answer:
C
Explanation:
Each device uses its derived device key with your unique registration ID to perform symmetric key attestation with the
enrollment during provisioning. To generate the device key, use the key you copied from your DPS enrollment to compute an
HMAC-SHA256 of the unique registration ID for the device and convert the result into Base64 format. Reference:
https://docs.microsoft.com/en-us/azure/iot-edge/how-to-auto-provision-symmetric-keys
Question 14 Topic 4, Mixed Questions
You have an Azure IoT hub that uses a Device Provisioning Service instance.
You have 1,000 legacy IoT devices that only support MAC address or serial number identities. The devices do NOT have a
security feature that can be used to securely identify the device or a hardware security module (HSM).
You plan to deploy the devices to a secure environment.
You need to configure the Device Provisioning Service instance to ensure that all the devices are identified securely before
they receive updates.
Which attestation mechanism should you choose?
- A. Trusted Platform Module (TPM) 1.2 attestation
- B. symmetric key attestation
- C. X.509 certificates
Answer:
B
Explanation:
A common problem with many legacy devices is that they often have an identity that is composed of a single piece of
information. This identity information is usually a MAC address or a serial number. Legacy devices may not have a
certificate, TPM, or any other security feature that can be used to securely identify the device. The Device Provisioning
Service for IoT hub includes symmetric key attestation. Symmetric key attestation can be used to identify a device based off
information like the MAC address or a serial number. Reference:
https://docs.microsoft.com/bs-latn-ba/azure/iot-dps/how-to-legacy-device-symm-key
Question 15 Topic 4, Mixed Questions
You use Azure Security Center in an Azure IoT solution.
You need to exclude some security events. The solution must minimize development effort.
What should you do?
- A. Create an Azure function to filter security messages.
- B. Add a configuration to the code of the physical IoT device.
- C. Add configuration details to the device twin object.
- D. Create an azureiotsecurity module twin and add configuration details to the module twin object.
Answer:
D
Explanation:
Properties related to every Azure Security Center for IoT security agent are located in the agent configuration object, within
the desired properties section, of the azureiotsecurity module.
To modify the configuration, create and modify this object inside the azureiotsecurity module twin identity.
Note: Azure Security Center for IoT's security agent twin configuration object is a JSON format object. The configuration
object is a set of controllable properties that you can define to control the behavior of the agent.
These configurations help you customize the agent for each scenario required. For example, automatically excluding some
events, or keeping power consumption to a minimal level are possible by configuring these properties. Reference:
https://docs.microsoft.com/en-us/azure/asc-for-iot/how-to-agent-configuration