Juniper jn0-334 practice test
Security, Specialist Exam
Question 1
Which three statements are correct about fabric interfaces on the SRX5800? (Choose three.)
- A. Fabric interfaces must be user-assigned interfaces.
- B. Fabric interfaces must have a user-assigned IP address.
- C. Fabric interfaces must be same interface type.
- D. Fabric interfaces must be on the same Layer 2 segment.
- E. Fabric interfaces must be system-assigned interfaces.
Answer:
CDE
Reference:
<
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-chassis-cluster-data-plane-interfaces.html
>
Question 2
You want to support reth LAG interfaces on a chassis cluster.
What must be enabled on the interconnecting switch to accomplish this task?
- A. RSTP
- B. 802.3ad
- C. LLDP
- D. swfab
Answer:
B
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-chassis-cluster-redundant-ethernet-lag-interfaces.html
Question 3
What are three primary functions of JATP? (Choose three.)
- A. detection
- B. encryption
- C. optimization
- D. analytics
- E. mitigation
Answer:
ADE
Question 4
You must deploy AppSecure in your network to block risky applications.
In this scenario, which two AppSecure features are required? (Choose two.)
- A. AppFW
- B. AppID
- C. APBR
- D. AppTrack
Answer:
BD
Question 5
Which two statements describe IPS? (Choose two.)
- A. IPS can be used to prevent future attacks from occurring.
- B. IPS dynamically sends policy changes to SRX Series devices.
- C. IPS inspects up to Layer 4 in the OSI model.
- D. IPS inspects up to Layer 7 in the OSI model.
Answer:
AD
Question 6
What is the correct step sequence used when Sky ATP analyzes a file?
- A. static analysis -> cache lookup -> antivirus scanning -> dynamic analysis
- B. cache lookup -> static analysis -> antivirus scanning -> dynamic analysis
- C. cache lookup -> antivirus scanning -> static analysis -> dynamic analysis
- D. dynamic analysis -> static analysis -> antivirus scanning -> cache lookup
Answer:
C
Reference:
https://www.juniper.net/documentation/en_US/release-independent/sky-
atp/information-products/
pathway-pages/sky-atp-admin-guide.pdf page 9
Question 7
Which two statements about JIMS high availability are true? (Choose two.)
- A. JIMS supports high availability through the installation of the primary and secondary JIMS servers.
- B. SRX clients are configured with the shared virtual IP (VIP) address of the JIMS server.
- C. SRX clients are configured with the unique IP addresses of the primary and secondary JIMS servers.
- D. SRX clients synchronize authentication tables with both the primary and secondary JIMS servers.
Answer:
AC
Question 8
Where is AppSecure executed in the flow process on an SRX Series device?
- A. screens
- B. security policy
- C. zones
- D. services
Answer:
D
Question 9
Data plane logging operates in which two modes? (Choose two.)
- A. syslog
- B. binary
- C. event
- D. stream
Answer:
CD
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/system-logging-for-a-security-device.html
Question 10
Which statement about the control link in a chassis cluster is correct?
- A. A cluster can have redundant control links.
- B. Recovering from a control link failure requires a reboot.
- C. The control link heartbeats contain the configuration file of the nodes.
- D. The control messages sent over the link are encrypted by default.
Answer:
A
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-chassis-cluster-dual-control-links.html
Question 11
Which default protocol and port are used for JIMS to SRX client communication?
- A. WMI over TCP; port 389
- B. ADSI over TCP; port 389
- C. HTTPS over TCP: port 443
- D. RPC over TCP, port 135
Answer:
C
Reference:
https://www.juniper.net/documentation/en_US/jims/topics/task/configuration/jims-
certificate-configuring.html#:~:text=By%20default%2C%20the%20HTTPS%20port%20is%20443.&text=The%20JI
MS% 20server%20communicates%20with,Firewall%20to%20allow%20this%20communication
Question 12
Click the Exhibit button.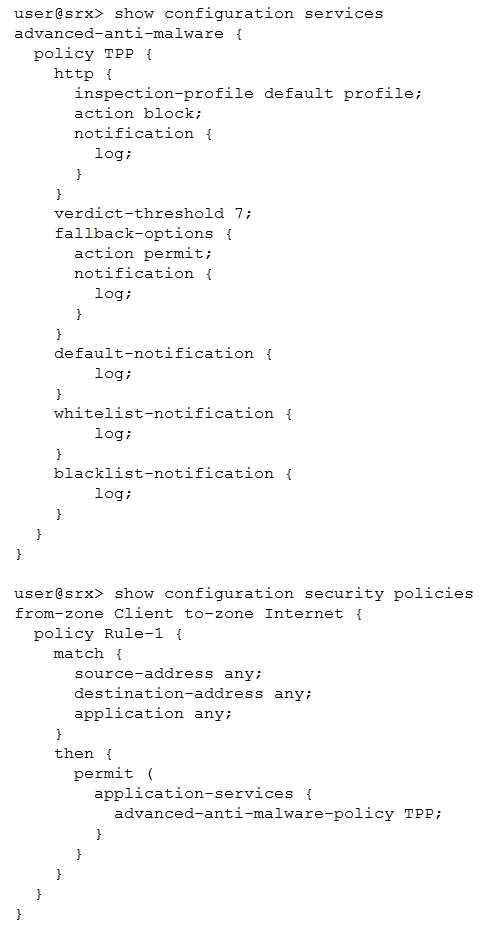
You have deployed Sky ATP to protect your network from attacks so that users are unable to
download malicious files. However, after a user attempts to download a malicious file, they are still
able to communicate through the SRX Series device.
Referring to the exhibit, which statement is correct?
- A. Change the security policy from a standard security policy to a unified security policy.
- B. Remove the fallback options in the advanced anti-malware policy.
- C. Configure a security intelligence policy and apply it to the security policy.
- D. Lower the verdict threshold in the advanced anti-malware policy.
Answer:
C
Question 13
Which two statements apply to policy scheduling? (Choose two.)
- A. A policy refers to many schedules.
- B. A policy refers to one schedule.
- C. Multiple policies can refer to the same schedule.
- D. A policy stays active regardless of when the schedule is active.
Answer:
BC
Reference:
https://www.juniper.net/documentation/en_US/cso5.4.0/topics/concept/cp-about-schedule-overview.html
Question 14
Click the Exhibit button.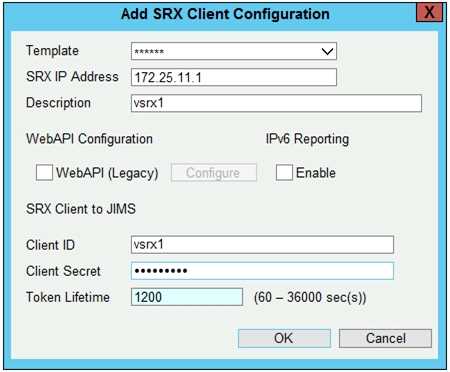
Referring to the exhibit, which two values in the JIMS SRX client configuration must match the values
configured on the SRX client? (Choose two.)
- A. IPv6 Reporting
- B. Client ID
- C. Client Secret
- D. Token Lifetime
Answer:
BC
Reference:
https://www.juniper.net/documentation/en_US/jims/topics/task/configuration/jims-srx-configuring.html
Question 15
Which two statements describe SSL proxy on SRX Series devices? (Choose two.)
- A. SSL proxy supports TLS version 1.2.
- B. Client-protection is also known as reverse proxy.
- C. SSL proxy is supported when enabled within logical systems.
- D. SSL proxy relies on Active Directory to provide secure communication.
Answer:
AC
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-user-auth-ssl-tls.html