Juniper jn0-212 practice test
Cloud, Associate Exam
Question 1
According to the juniper network, what is the recommended external routing protocol for the
underlay network?
- A. IS-IS
- B. EGP
- C. OSPF
- D. BGP
Answer:
D
Question 2
Which two capabilities are supported with the cSRX firewall?(choose two)
- A. IPS
- B. routing instances
- C. chassis clustering
- D. Layer 2 deployment
Answer:
A, B
Question 3
Which cloud CPE component manages the end-to-end path from the CPE to the central office or to
another CPE?
- A. service orchestration
- B. infrastructure orchestration
- C. physica telco cloud infrastructure
- D. virtual network functions
Answer:
A
Question 4
What are two objectives of SDN?(choose two)
- A. centralization of control plane
- B. physical separation of the control plane from the data plane
- C. centralization of the forwarding plane
- D. centralization of the services plane
Answer:
A, B
Explanation: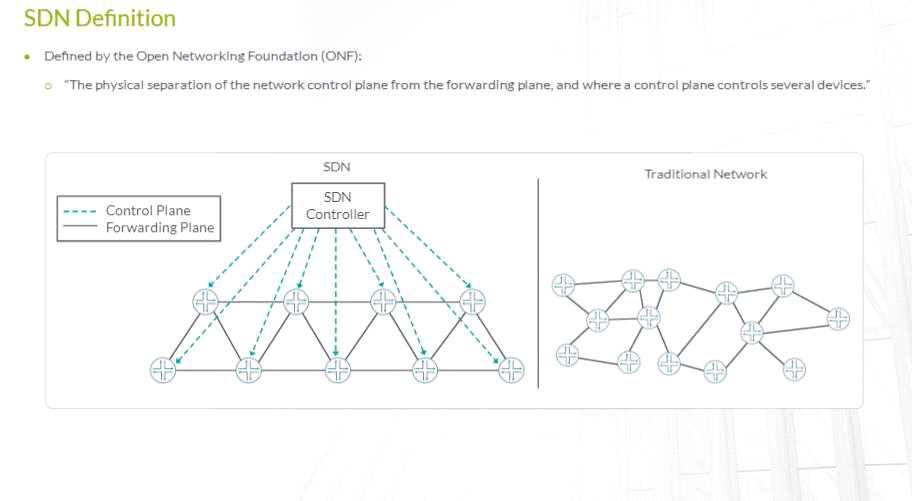
Question 5
What is an advantage of the Junos Telemetry Interface(JTI) over SNMP?
- A. JTI can pull data more frequently
- B. JTI always transfers data over HTTP
- C. JTI never transfers data over UDP
- D. JTI can push data more frequently
Answer:
D
Explanation:
Question 6
You have 100 small branch offices around the world. You must use a single pane of glass to monitor
EX Series devices for port status, ports exceeding maximum bandwidth, ports with maximum errors,
and ports with maximum packet loss
In this scenario, which product would satisfy the requirement?
- A. Contrail SD-WAN
- B. Contrail SD-LAN
- C. Contrail Networking
- D. Contrail Cloud
Answer:
A
Question 7
Which two statements are correct about the NFV framework?(Choose two)
- A. The NFV framework is defined by ANSI
- B. The NFV framework is defined by ETSI
- C. The NFV framework enables horizontally scalable deployments of services
- D. A spine and leaf implementation is an example of the NFV framework
Answer:
B, C
Question 8
Which mechanism allows tenants to interconnect across an overlay network?
- A. tunnels
- B. subnets
- C. EBGP connections
- D. P2P OSPF adjacencies
Answer:
A
Explanation: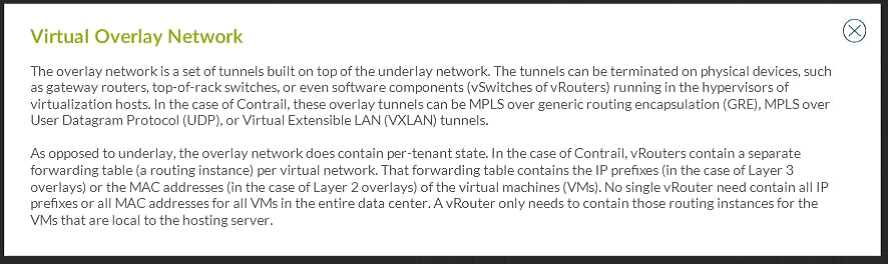
Question 9
What are two examples of SaaS?(Choose two)
- A. Amazon Web Services
- B. SalesForce
- C. Google Apps
- D. IBM Cloud
Answer:
A, B
Question 10
Which two Juniper devices are used as a CSO CPE devices(Choose two.)
- A. SRX
- B. NFX
- C. QFX
- D. MX
Answer:
A, B
Question 11
What are two characteristics of Juniper's Connected Security Solution?(Choose two.)
- A. manual secure policy control
- B. dynamic VPN connections
- C. centralized management
- D. enforcement everywhere on the network
Answer:
C, D
Question 12
Which two statements are true about virtualized platforms?(Choose two.)
- A. The vSRX must have two vCPU dedicated to the vCP
- B. The vMX used separate VMs to host the vCP and vFP
- C. The vSRX must have one vCPU dedicated to the vCP
- D. The vMX uses one VM to host the vCP and vFP
Answer:
B, C
Explanation: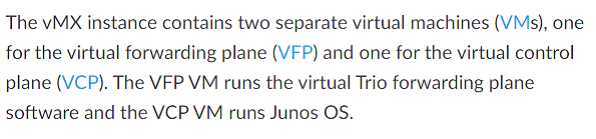
Question 13
You are responsible for optimizing a global MPLS WAN. You must determine the optimal MPLS
forwarding paths and automate the provisioning of the forwarding paths into the network
Which Juniper Networks SDN solution will satisfy the requirements?
- A. NorthStar Controller
- B. Policy Enforcer
- C. Contrail
- D. Network Director
Answer:
A
Question 14
Which two benefits does the Junos Telemetry Interface(JTI) provide in an AppFormix
architecture?(Choose two.)
- A. JTI enables you to deploy security policies to vSRX devices
- B. JTI uses a push model to deliver data asynchronously
- C. JTI enables you to collect and export data from resources such as firewall filters
- D. JTI uses an SNMP pull model to eliminate additional processing
Answer:
B, C
Explanation:

Question 15
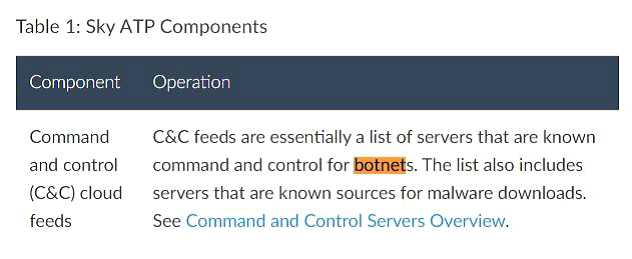
Devices in your data center have become unwilling participants of botnet attacks.
In this scenario, which security technology should you use to stop this behavior?
- A. Policy Enhancer
- B. Sky ATP GeoIP threat protection
- C. Sky ATP C&C threat protection
- D. IPsec
Answer:
C
Explanation: