IBM c1000-003 practice test
IBM Mobile Foundation v8.0 Application Development Exam
Question 1
Which files are required to be included to enable Mobile Foundation Analytics for a Web
Application?
- A. controller.js and mobile.js
- B. ibmmfpf.js and ibmmfpfanalytics.js
- C. ibmmfpfanalytics.js and controller.js
- D. ibmmobilefirst.js and ibmmobilefirstfanalytics.js
Answer:
B
Question 2
The figure below shows the use of HTTP client(postman) to obtain a Mobile Foundation test token.
Which two parameters must be defined in the body?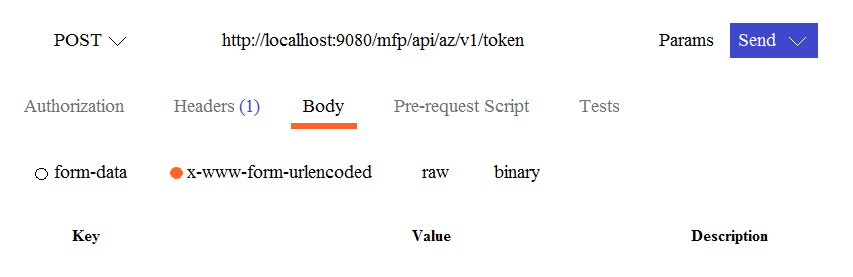
- A. scope
- B. grant_type
- C. content-type
- D. registeredclient
- E. client_credentials
Answer:
C
Question 3
Which object stores system messages that can be translated in an IBM Mobile Foundation Cordova
application?
- A. WL.Messages
- B. MPF.Messages
- C. MPF.ClientMessages
- D. WL.ClientMessages
Answer:
D
Question 4
MFP.Server.invokeHttp(options) Mobile Foundation API is used to call an HTTP service inside a
procedure declared within an HTTP adapter.
In the options parameter, which two parameters are mandatory? (Choose two.)
- A. path
- B. headers
- C. function
- D. transformation
- E. returnedContentType
Answer:
A,C
Question 5
What component can a developer use to control the URL structure, request and response headers,
content, and encoding of a request?
- A. SQL adapter
- B. Java adapter
- C. HTTP adapter
- D. Resource request
Answer:
B
Question 6
As part of registering a confidential client with IBM Mobile Foundation Server, what two credentials
must a developer provide? (Choose two.)
- A. ID
- B. Name
- C. Secret
- D. Element
- E. Display Name
Answer:
A,C
Explanation:
You begin by registering a confidential client with MobileFirst Server. As part of the registration, you
provide the credentials of the confidential client, which consist of an ID and a secret. In addition, you
set the clients allowed scope, which determines the scopes that can be granted to this client. When
a registered confidential client requests an access token from the authorization server, the server
authenticates the client by using the registered credentials, and verifies that the requested scope
matches the clients allowed scope.
Question 7
In the example below, what is the correct code that should be placed in line 6 to return the
registration data for the given clientId?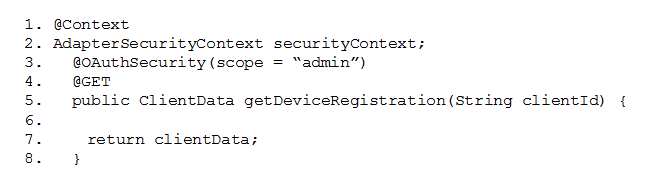
- A. ClientData clientData = adapterSecurityContext.getRegistrationData (clientId);
- B. ClientData clientData = securityContext.getRegisteredData (clientId);
- C. ClientData clientData = adapterSecurityContext.getClientRegisteredData (clientId);
- D. ClientData clientData = securityContext.getClientRegistrationData (clientId);
Answer:
D
Question 8
Which application development approach would a developer use to create a cross-platform mobile
application that utilizes customized native components?
- A. Agile
- B. Native
- C. Hybrid
- D. Mobile Web Application
Answer:
B
Question 9
When adding custom Java code to an adapter, which is a valid start name for the custom package?
- A. www
- B. ibm
- C. gov
- D. com
Answer:
D
Question 10
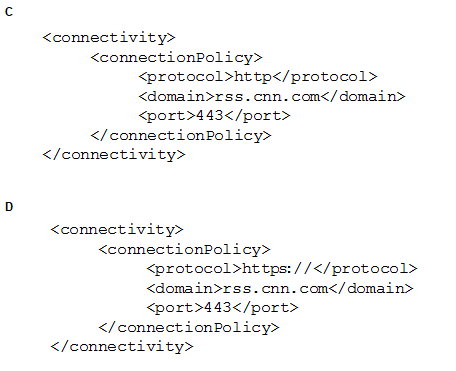
A Mobile Foundation developer intends to develop a HTTP adapter that calls an SSL secured
endpoint.
Which would be a correct connectivity configuration?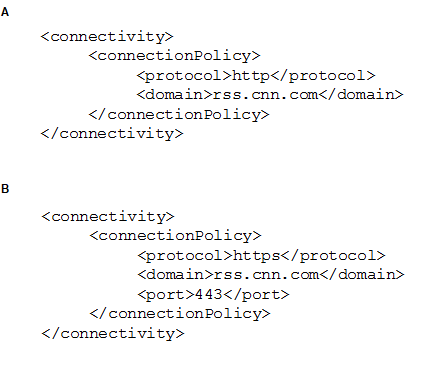
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Question 11
What command must a developer run prior to deploying an adapter that was just created?
- A. mfpdev config
- B. mfpdev app register
- C. mfpdev adapter build
- D. mfpdev build <adapter_name>
Answer:
B
Question 12
How can a Mobile Foundation application developer override properties during run time, without
having to redeploy adapters?
- A. Properties cannot be overridden at runtime
- B. Use the built-in connection policy properties
- C. Declare instance variables in the Java adapter
- D. Use the Mobile Foundation Operations Console
Answer:
B
Question 13
Which platform requires registration in their developer programs in order to deploy a Mobile
Foundation application to a device?
- A. iOS
- B. Android
- C. Xamarin
- D. Windows Mobile
Answer:
A
Question 14
In reference to IBM Mobile Foundation, what is an Adapter Mashup?
- A. Making several adapter requests at the same time
- B. Defining adapter procedure as a variable in another adapter
- C. Overriding an adapter procedure parameter in another adapter
- D. A single adapter procedure that uses multiple endpoints to generate one processed result
Answer:
D
Question 15
What client side SDK method is used to track individual users in Mobile Foundation Analytics?
- A. trackUser()
- B. recordUser()
- C. setUserName()
- D. setUserContext()
Answer:
D