Huawei h12-711 practice test
Constructing Basic Security Network)
Question 1
DRAG DROP
Match each of the following application layer service protocols with the correct transport layer
protocols and port numbers.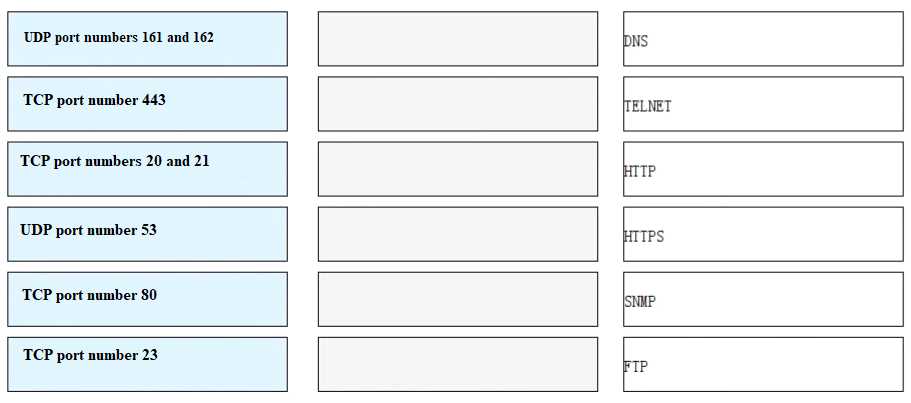
Answer:
Explanation: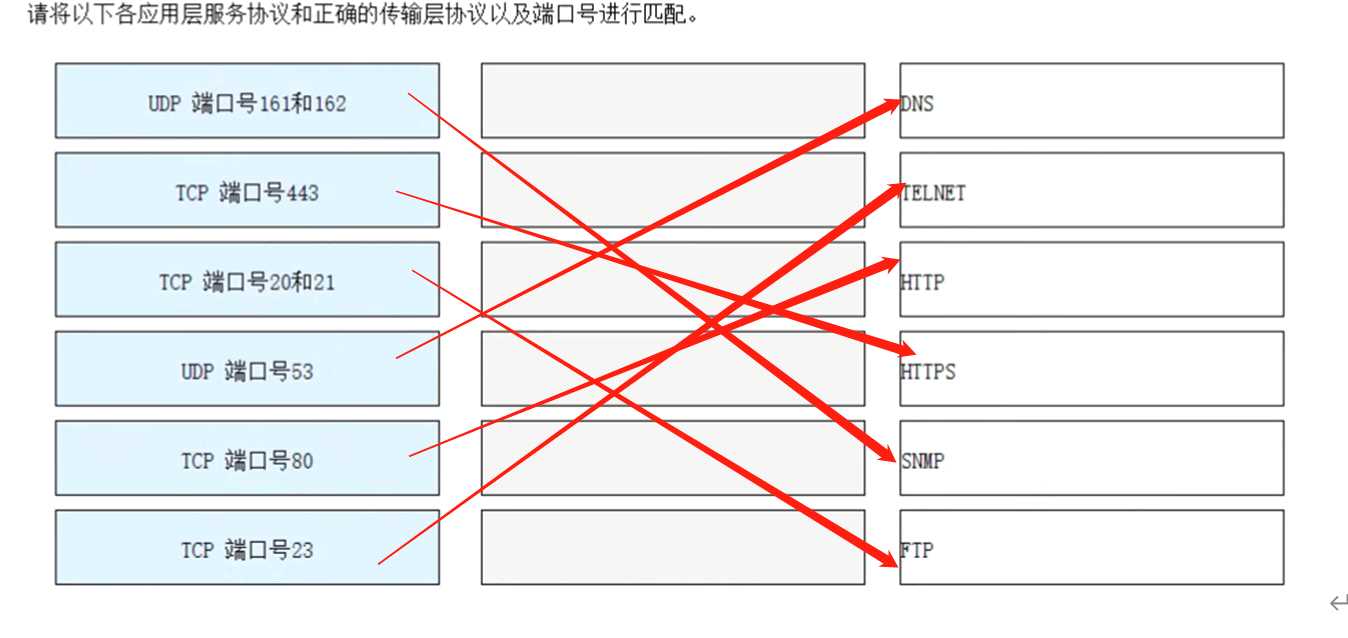
Question 2
Which of the following attack methods is to construct special SQL statements and submit sensitive
information to exploit program vulnerabilities
- A. Buffer overflow attack
- B. SQL injection attacks
- C. Worm attack
- D. Phishing attacks
Answer:
B
Question 3
A Web server is deployed in an enterprise intranet to provide Web access services to Internet users,
and in order to protect the access security of the server, it should be divided into the _____ area of
the firewall.
- A. DMZ
- B. DMY
Answer:
A
Question 4
At what layer does packet filtering technology in the firewall filter packets?
- A. Transport layer
- B. Network layer
- C. Physical layer
- D. Data link layer
Answer:
B
Question 5
As shown in the figure, the administrator needs to test the network quality of the 20.0.0/24 CIDR
block to the 40.0.0/24 CIDR block on Device B, and the device needs to send large packets for a long
time to test the network connectivity and stability.
- A. tracert -a 20.0.0.1 -f 500 -q 9600 40.0.0.2
- B. ping -a 20.0.0.1 -c 500 -s 9600 40.0.0.2
- C. ping -s 20.0.0.1 -h 500-f 9600 40.0.0.2
- D. tracert -a 20.0.0.1 -c 500 -w 9600 40.0.0.2
Answer:
B
Question 6
WAF can accurately control and manage users' online behavior and user traffic.
- A. TRUE
- B. FALSE
Answer:
A
Question 7
ARP man-in-the-middle attacks are a type of spoofing attack technique.
- A. TRUE
- B. FALSE
Answer:
A
Question 8
DRAG DROP
Please classify the following security defenses into the correct classification.
Answer:
Explanation: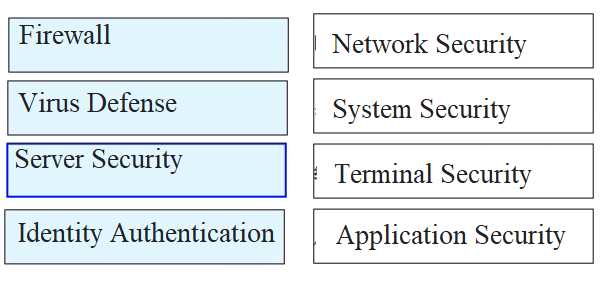
Question 9
Regarding the characteristics of the routing table, which of the following items is described correctly
- A. Port When a packet matches multiple entries in the routing table, it is forwarded based on the route entry with the largest metric.
- B. Port In the global routing table, there is at most one next hop to the same destination CIDR block.
- C. There may be multiple next hops in the global routing table to the same destination.
- D. Port When a packet matches multiple entries in the routing table, it is forwarded according to the longest mask.
Answer:
C, D
Question 10
When the Layer 2 switch receives a unicast frame and the MAC address table entry of the switch is
empty, the switch discards the unicast frame.
- A. TRUE
- B. FALSE
Answer:
B
Question 11
Among the various aspects of the risk assessment of IS027001, which of the following does not
belong to the system design and release process?
- A. Hold a summary meeting of the project in the information security management stage
- B. Determine risk disposal measures and implement rectification plans
- C. Determine risk tolerance and risk appetite
- D. System integration and information security management system document preparation
Answer:
A
Question 12
Which of the following types of malicious code on your computer includes?
- A. Oral virus
- B. Trojan horses
- C. Port SQL injection
- D. Oral spyware
Answer:
A, B, C, D
Question 13
For which of the following parameters can the packet filtering firewall filter?
- A. Port packet payload
- B. IP address of the port source destination
- C. The MAC address of the source destination
- D. Port number and protocol number of the port source
Answer:
B, D
Question 14
What is the security level of the Untrust zone in Huawei firewalls?
- A. 10
- B. 20
- C. 5
- D. 15
Answer:
C
Question 15
Which layer of the protocol stack does SSL provide end-to-end encrypted transmission services?
- A. Application layer
- B. Data link layer
- C. Network layer
- D. Transport layer
Answer:
D