HP hpe7-a07 practice test
HPE Campus Access Mobility Expert
Question 1
A customer is evaluating device profiles on a CX 6300 switch. The test device has the following
attribute: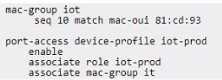
• MAC address=81:cd:93:13:ab:31
The test device needs to be assigned the "lot-prod'' role, in addition the "lot-default" role must be
applied for any other device connected lo interface 1/1/1. This is a lab environment with no
configuration of any external authentication server for the test.
Given the configuration example, what is required to meet this testing requirement?
- A. Enter the command "pot-access device-profile mode block-until-profile-applied"" for interface 1/1/1.
- B. Enter the command "port-access fallback-role lot-default globally
- C. Enter the command "port-access onboarding-method precedence" to set device profiles with a lower precedence.
- D. Enter the command "port-access device-profile mode block-until-profile-applied" globally.
Answer:
B
Explanation:
The fallback role is used as a default role in the absence of a specified role or when an authentication
server is not available. Given the scenario, where the test device with MAC address
81:cd:93:13:ab:31 needs to be assigned to "iot-prod" and other devices to "iot-default", and
considering there is no external authentication server configured for the test, the appropriate action
would be to set a global fallback role that applies to all devices connecting to the network. This
ensures that any device that does not match the specific device profile will inherit the "iot-default"
role. Since the configuration for a specific MAC address (81:cd:93:xx:xx:xx) to associate with the "iot-
prod" role is already in place, setting the fallback role globally accommodates the requirement for
other devices.
Question 2
Exhibit.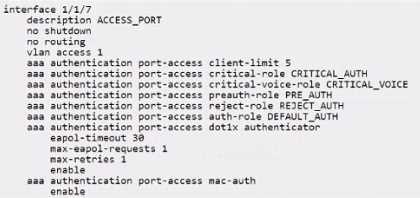
Which user role will be assigned when a voice client tries to connect for the first time, but the
RADIUS server is unavailable?
- A. CRITICAl_AUTH
- B. DEFAULT_AUTH
- C. CRIT1CAL_V0ICE
- D. PRE_AUTH
Answer:
C
Explanation:
In the provided configuration for interface 1/1/7, there are roles specified for different scenarios
concerning authentication. When a voice client attempts to connect and the RADIUS server is
unreachable, the role that is assigned is the one specified as the "critical-voice-role". In this case, the
"CRITICAL_VOICE" role is configured to be assigned under such circumstances, ensuring that voice
clients receive appropriate network access permissions even when the RADIUS server is not available
to authenticate them.
Question 3
You configured a WPA3-SAE with the following MAC Authentication Role Mapping in Cloud
Authentication and Policy: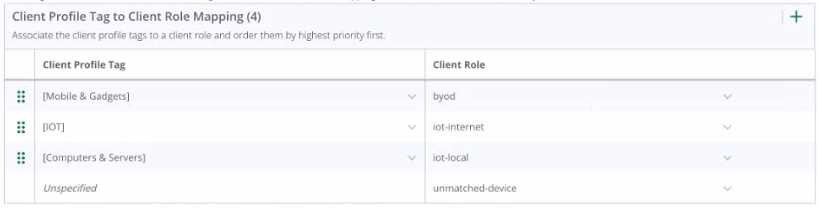
With further default settings assume a new Android phone is connected to the network. Which role
will the client be assigned after connecting for the first time?
- A. byod
- B. client will be rejected network access
- C. lot-local
- D. unmatched-device
Answer:
D
Explanation:
The configuration shown in the third exhibit details a client role mapping that associates different
client profile tags with specific client roles. When a new device, such as an Android phone, connects
to the network, it will be profiled and assigned a role based on the mappings defined. If the device
does not match any predefined profiles, it would be assigned the "unmatched-device" role. This is
under the assumption that default settings are in place and the client does not match the criteria for
any of the specific roles like "byod", "iot-internet", or "iot-local". Therefore, an Android phone
connecting for the first time and not matching any specific profile tag would be assigned to the
"unmatched-device" role.
Question 4
You are testing the use of the automated port-access role configuration process using RadSec
authentication over VXLAN. During your testing you observed that the RadSec connection will fan
during the digital certificate exchange
What would be the cause of this Issue?
- A. The RadSec server was defined on the switch using an IPv6 address that was unreachable
- B. Tracking mode was set to "dead-only", and the RadSec server was marked as unreachable.
- C. The switch is configured to establish a TLS connection with a proxy server, not the radius server.
- D. The RADIUS TCP packets are Being dropped and the TLS tunnel is not established.
Answer:
D
Explanation:
During the testing of RadSec authentication over VXLAN, if the RadSec connection fails during the
digital certificate exchange, it typically indicates an issue with the establishment of the TLS tunnel,
which is required for RadSec's secure communication. The failure of TLS tunnel establishment can
occur due to RADIUS TCP packets being dropped, preventing the secure exchange of digital
certificates necessary for RadSec authentication. The other options, such as IPv6 address reachability,
tracking mode settings, and proxy server misconfiguration, are not directly related to the failure of
the TLS tunnel establishment during the certificate exchange process
Question 5
An OSPF router has learned a pain 10 an external network by Doth an E1 and an E2 advertisement
Both routes have the same path cost Which path will the router prefer?
- A. The router will prefer the E1 path.
- B. The router will use Doth paths equally utilizing ECMP.
- C. The router will prefer the E2 path.
- D. Both routes will be suppressed until the path conflict has been resolved.
Answer:
A
Explanation:
In OSPF, when a router learns about an external network through both E1 and E2 advertisements,
and if both have the same path cost, the router will prefer the E1 path. This is because E1 routes
consider both the external cost to reach the external network and the internal cost to reach the
ASBR, providing a more comprehensive metric. E2 routes only consider the external cost and ignore
the internal cost to the ASBR, which could potentially lead to suboptimal routing. Therefore, the
router will choose the E1 path due to its more accurate representation of the total path cost.
Question 6
You recently added ClearPass as an authentication server to an HPE Aruba Networking Central group.
RADIUS authentication with Local User Roles (LUR) works fine Out the same access points cannot use
Downloadable User Roles (DUR).
What should he corrected in this configuration to fa the issue with DUR?
- A. Add a new Enforcement Policy of type ‘’WEBAUTH’’ on ClearPass and associate it with the matching service on ClearPass
- B. Add the correct IP addresses or IP subnets of the Network Access Devices (NADs) under the "Devices" tab on ClearPass
- C. Replace the AP's expiree digital certificate using the "crypto pki-import pem serverCert" command.
- D. Add the correct values for "CPPM username" and "CPPM Password" m the authentication server configuration on HPE Aruba Networking Central
Answer:
B
Explanation:
For Downloadable User Roles (DUR) to function correctly with ClearPass, the Network Access Devices
(NADs) need to be correctly defined in ClearPass under the "Devices" tab. This ensures that ClearPass
can identify and communicate with the NADs to deliver the appropriate user roles. If the NADs are
not correctly defined, ClearPass will not be able to provide the DURs to the access points for
enforcement. This is a common configuration step that is required to integrate ClearPass with
network devices for advanced role-based access control.
Question 7
Which data transmission method provides the most efficient use of airtime for VoIP traffic?
- A. FDMA
- B. OFDM
- C. MU-MIMO
- D. TWT
Answer:
C
Explanation:
MU-MIMO (Multi-User, Multiple Input, Multiple Output) provides the most efficient use of airtime
for VoIP traffic among the options listed. MU-MIMO allows multiple users to receive multiple data
streams simultaneously, improving the overall efficiency of the network, especially in dense
environments where VoIP applications need consistent and reliable connectivity.
Question 8
You deployed UBT to securely tunnel traffic from user desktop PCs connected behind VOIP phones Ail
other non-UBT dents are connected to a different network. After the deployment users reported
interruptions lo their phone service
- A. The VLAN on which UBT clients are placed is not configured on the switch uplink and traffic from the VoIP phones is being dropped
- B. You tailed to correctly configure a user-defined VRF to support the UBT clients behind the VoIP phones, causing traffic to drop.
- C. Broadcast/multicast packets are copied to both the tunnel and locally, causing duplicate packets and network instability
- D. The UBT client broadcast/multicast packets returned to the same switch port and corrupted the phones IMC table
Answer:
A
Explanation:
If users report interruptions to their phone service after the deployment of User-Based Tunneling
(UBT), it can be due to the VLAN designated for UBT clients not being configured on the switch
uplink. As a result, traffic from VoIP phones, which may be trying to use the same VLAN, could be
dropped, leading to service interruptions. Ensuring that the VLAN is properly configured on the
switch uplink is crucial for the seamless operation of UBT clients and VoIP services.
Question 9
An ACME company employee complained about a recent poor-quality VoIP call while moving around
their office environment HPE Aruba Networking Central reported a fair UCC score for this call while
your VoIP engineer reported that their systems reported a MOS of 2, 3. The VoIP devices are
operating over the 5GHz frequency band.
What are the possible contributing factors? (Select two.)
- A. Coverage AP deployment plans generally don't support enough cell overlap for VoIP.
- B. 802.tr is enabled in the WLAN Security settings.
- C. There was localized interference at the caller’s location
- D. 802.1K is disabled in the WLAN Security settings
- E. The client roamed into an area that continuously operates Zigbee.
Answer:
AE
Explanation:
VoIP quality can be negatively impacted by insufficient cell overlap in AP deployment plans, which
can cause poor handoffs between APs as a user moves around. This results in a degraded VoIP
experience. Additionally, roaming into an area with continuous Zigbee operation can cause
interference with the 5GHz frequency band, further contributing to poor VoIP call quality. The Zigbee
communication protocol operates on the same frequency band as Wi-Fi and can introduce noise and
interference, which leads to a reduced MOS score, as reported by the VoIP engineer.
Question 10
The wireless administrator for a college campus is gelling reports of connectivity issues when
students are working outdoors.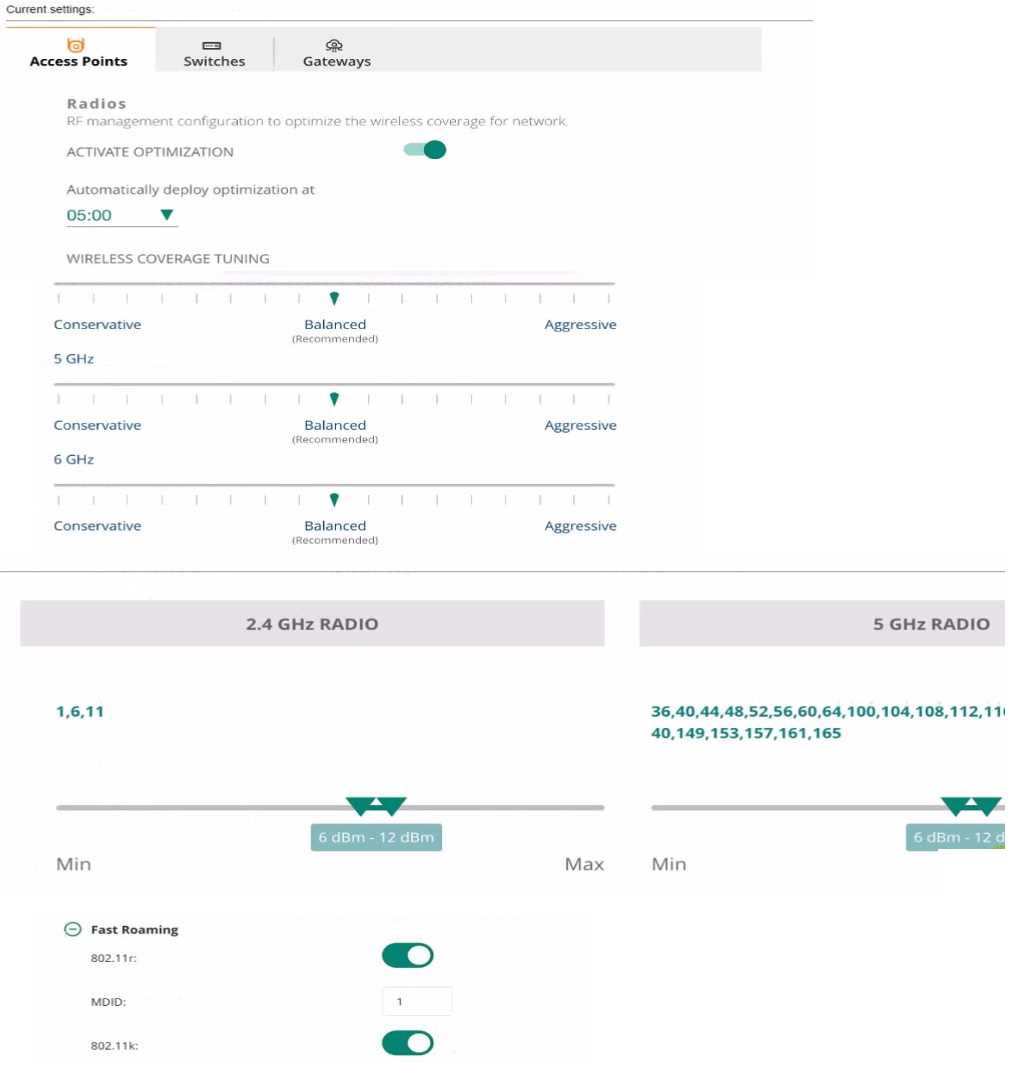
Reviewing the settings above, watch change is needed to align with best practices?
- A. Disable 802 11r.
- B. Disable 802 11k.
- C. increase 5Gnz TX power range Min/Max.
- D. increase 5 GHz wireless coverage tuning to Aggressive.
Answer:
C
Explanation:
To address connectivity issues when students are working outdoors, increasing the transmission (TX)
power range for the 5GHz radios can help improve signal strength and coverage. The setting shown
indicates a conservative approach to power settings, which might not provide sufficient coverage for
outdoor areas. By increasing the power range, you can extend the wireless signal reach, which aligns
with best practices for outdoor wireless coverage.
Question 11
Refer to the CLI output below: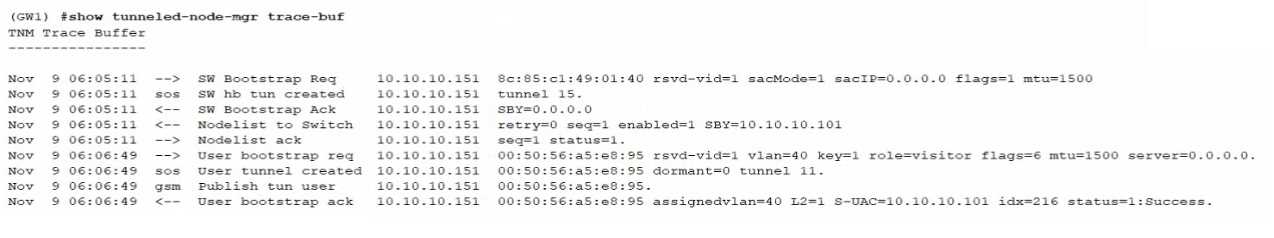
What statement about the output above is correct?
- A. The port-access role was configured with gateway-role visitor
- B. The secondary tunnel endpoint IP is 10.10-10.151.
- C. The client authenticated using dot1x.
- D. The UBT zone was configured to use a user-defined VRF
Answer:
B
Explanation:
The CLI output indicates a tunnel creation process, where "SW hw tun created" refers to the switch
hardware tunnel being created. The line mentioning "BYP-10.10.10.101 -> SW hw tun created to
10.10.10.151 tunnel 15." implies that a tunnel was established to the secondary tunnel endpoint
with the IP address 10.10.10.151. This is a common configuration for User-Based Tunneling (UBT)
setups where traffic is tunneled to a specific endpoint.
Question 12
Which statement is true given the following CLI output from a CX 6300?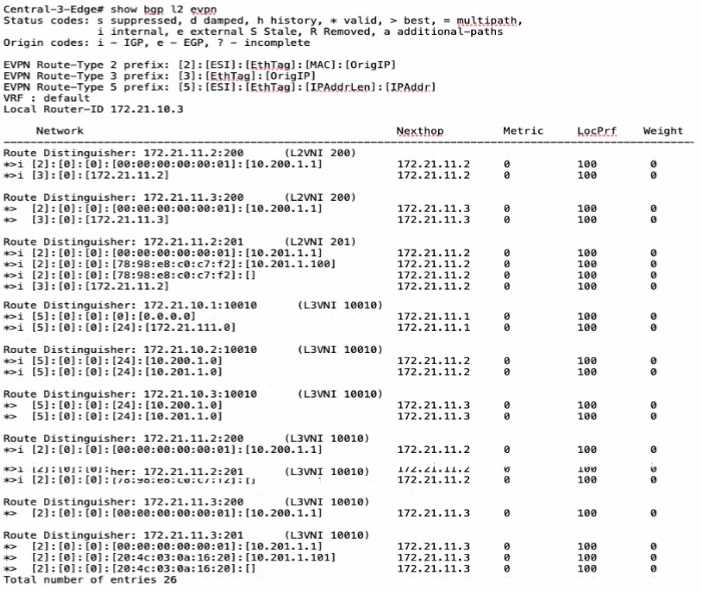
- A. The underlay loopback addresses are in the 172 21 11 x range.
- B. There are two anycast addresses m me overlay fabric.
- C. Duplicate MAC addresses were detected in the overlay fabric
- D. There are three active client overlay VLANs in the overlay fabric
Answer:
A
Explanation:
The CLI output displays EVPN routes and their corresponding next hops. The "Route Distinguisher"
entries followed by IP addresses in the 172.21.11.x range indicate these are loopback addresses used
by the underlay network. The underlay network provides the basic routing and forwarding plane for
the overlay network that EVPN is part of. These loopback addresses are crucial for the proper
functioning of the EVPN control plane.
Question 13
DRAG DROP
Your customer is requesting a 4-ciass LAN queuing model tor QoS. Following best practices, match
the PHB/DSCP values to the application types.
Answer:
Explanation:
Best Effort and Scavenger = DF (0)
Bulk and Transactional Data = AF21 (18)
Multimedia Streaming = AF31 (26)
Real-Time Interactive = EF (46)
Question 14
You configured" a bridged mode SSID with WPA3-Enterprise and EAP-TLS security. When you connect
an Active Directory joined client that has valid client certificates. ClearPass shows the following error.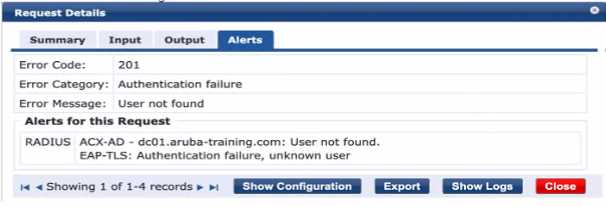
What is needed to resolve this issue?
- A. Enable authorization in your Authentication Method.
- B. Recreate the SSID m tunneled mode.
- C. Modify your ACX-AD authentication source to include the UPN in the search.
- D. Configure ClearPass to trust the client certificate.
Answer:
C
Explanation:
The error message "User not found" indicates that the authentication source, in this case, Active
Directory (AD), is not able to locate the user account based on the current search parameters. This
often occurs when the User Principal Name (UPN) that the client is using to authenticate is not
included in the search parameters of the AD authentication source within ClearPass. By modifying
the AD authentication source to include the UPN in the search, ClearPass will be able to correctly
locate the user account and proceed with the authentication using the valid client certificates.
Question 15
Refer to the exhibit.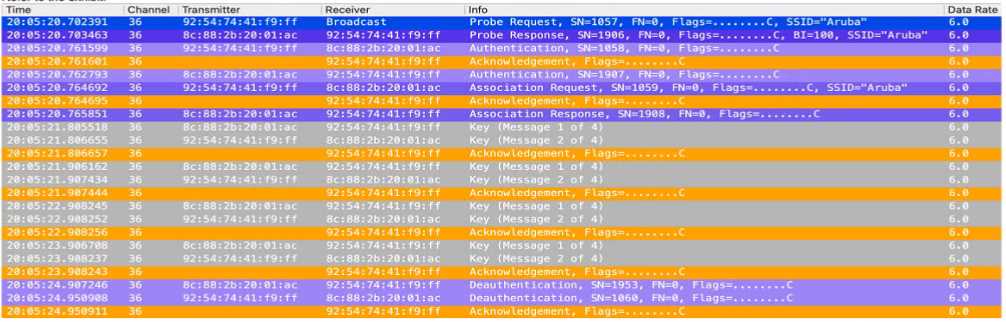
Which statement is true?
- A. The client performed passive scanning
- B. The client is using BSS Fast Transition
- C. The client is failing 802.1X authentication
- D. The client used an incorrect passphrase
Answer:
C
Explanation:
The exhibit shows a series of 802.1X authentication steps with multiple "Deauthentication" frames,
which indicate that the client is not successfully completing the authentication process. Since the
frames show repeated attempts at authentication followed by deauthentication, this suggests that
the client is failing the 802.1X authentication process, which is required for network access in a
WPA2/WPA3-Enterprise security environment.