HP hpe6-a84 practice test
Aruba Certified Network Security Expert Written Exam
Question 1
You are designing an Aruba ClearPass Policy Manager (CPPM) solution for a customer. You learn that
the customer has a Palo Alto firewall that filters traffic between clients in the campus and the data
center.
Which integration can you suggest?
- A. Sending Syslogs from the firewall to CPPM to signal CPPM to change the authentication status for misbehaving clients
- B. Importing clients' MAC addresses to configure known clients for MAC authentication more quickly
- C. Establishing a double layer of authentication at both the campus edge and the data center DMZ
- D. Importing the firewall's rules to program downloadable user roles for AOS-CX switches more quickly
Answer:
A
Explanation:
This option allows CPPM to receive real-time information about the network activity and security
posture of the clients from the firewall, and then apply appropriate enforcement actions based on
the configured policies 12
.
For example, if a client is detected to be infected with malware or
violating the network usage policy, CPPM can quarantine or disconnect the client from the
network 2
.
Question 2
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement
802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba
gateway cluster. The gateway cluster should assign these clients to the “eth-internet" role. The
gateway should also handle assigning clients to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below: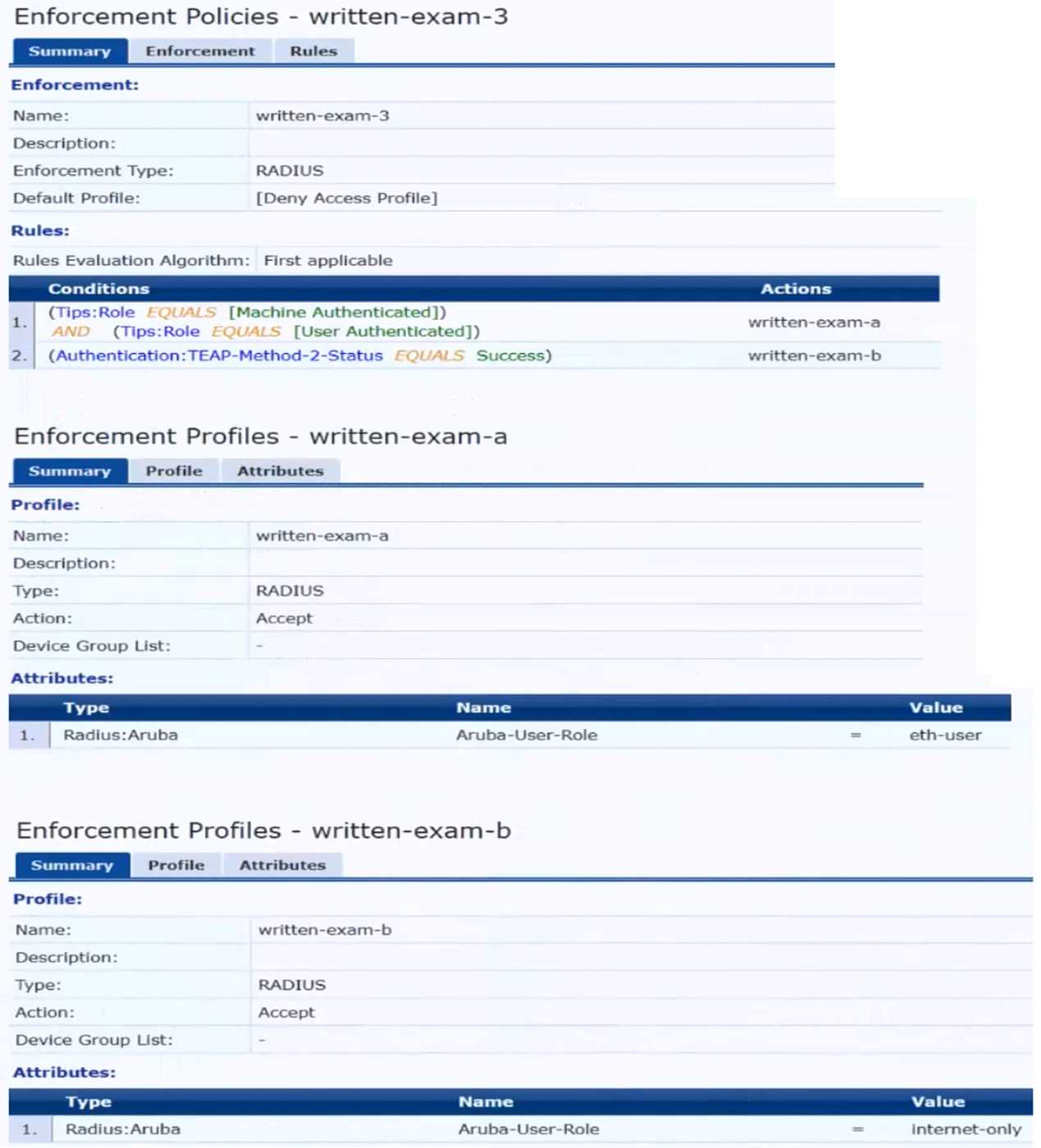
The gateway cluster has two gateways with these IP addresses:
• Gateway 1
o VLAN 4085 (system IP) = 10.20.4.21
o VLAN 20 (users) = 10.20.20.1
o VLAN 4094 (WAN) = 198.51.100.14
• Gateway 2
o VLAN 4085 (system IP) = 10.20.4.22
o VLAN 20 (users) = 10.20.20.2
o VLAN 4094 (WAN) = 198.51.100.12
• VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster.
If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able
to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
You are setting up the UBT zone on an AOS-CX switch.
Which IP addresses should you define in the zone?
- A. Primary controller = 10.20.4.21; backup controller = 10.20.4.22
- B. [Primary controller = 198.51.100.14; backup controller = 10.20.4.21
- C. Primary controller = 10 20 4 21: backup controller not defined
- D. Primary controller = 10.20.20.254; backup controller, not defined
Answer:
A
Explanation:
To configure user-based tunneling (UBT) on an AOS-CX switch, you need to specify the IP addresses
of the mobility gateways that will receive the tunneled traffic from the switch 1
.
The primary
controller is the preferred gateway for the switch to establish a tunnel, and the backup controller is
the alternative gateway in case the primary controller fails or becomes unreachable 1
.
The IP
addresses of the gateways should be their system IP addresses, which are used for inter-controller
communication and cluster discovery 2
.
In this scenario, the customer has a gateway cluster with two gateways, each with a system IP
address on VLAN 4085. Therefore, the switch should use these system IP addresses as the primary
and backup controllers for UBT.
The IP addresses of the gateways on VLAN 20 and VLAN 4094 are not
relevant for UBT, as they are used for user traffic and WAN connectivity, respectively 2
.
The VRRP IP
address on VLAN 20 is also not applicable for UBT, as it is a virtual IP address that is not associated
with any specific gateway 3
.
Therefore, the best option is to use 10.20.4.21 as the primary controller and 10.20.4.22 as the backup
controller for UBT on the switch.
This will ensure high availability and cluster discovery for the
tunneled traffic from the switch to the gateway cluster 12
.
Question 3
Refer to the scenario.
A customer requires these rights for clients in the “medical-mobile” AOS firewall role on Aruba
Mobility Controllers (MCs):
Permitted to receive IP addresses with DHCP
Permitted access to DNS services from 10.8.9.7 and no other server
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
Denied access to other 10.0.0.0/8 subnets
Permitted access to the Internet
Denied access to the WLAN for a period of time if they send any SSH traffic
Denied access to the WLAN for a period of time if they send any Telnet traffic
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with “medical-mobile” clients, only
send return traffic.
The exhibits below show the configuration for the role.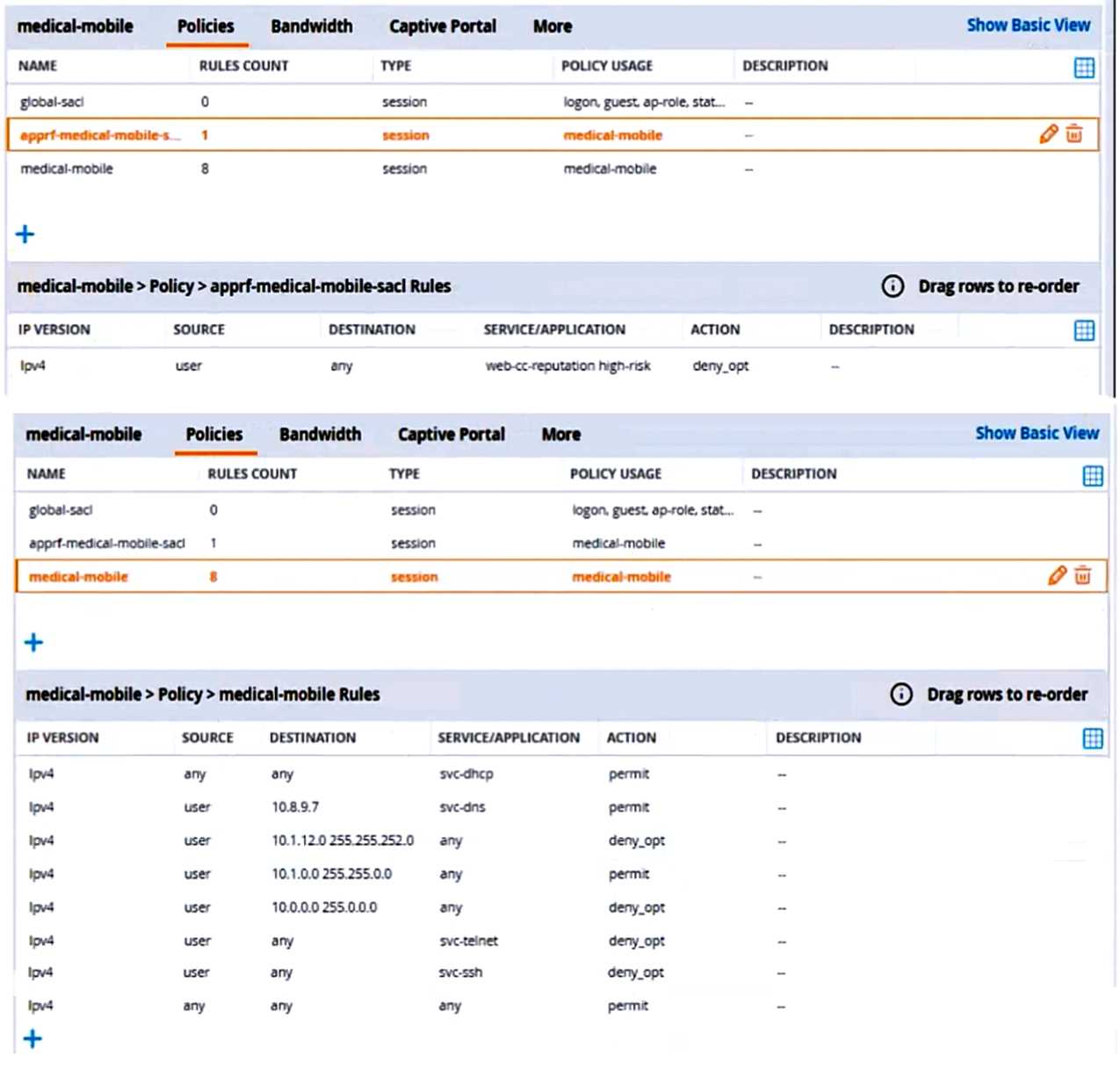
There are multiple issues with this configuration. What is one change you must make to meet the
scenario requirements? (In the options, rules in a policy are referenced from top to bottom. For
example, “medical-mobile” rule 1 is “ipv4 any any svc-dhcp permit,” and rule 8 is “ipv4 any any any
permit”.)
- A. In the “medical-mobile” policy, move rules 2 and 3 between rules 7 and 8.
- B. In the “medical-mobile” policy, change the subnet mask in rule 3 to 255.255.248.0.
- C. Move the rule in the “apprf-medical-mobile-sacl” policy between rules 7 and 8 in the “medical- mobile” policy.
- D. In the “medical-mobile” policy, change the source in rule 8 to “user.”
Answer:
B
Explanation:
The subnet mask in rule 3 of the “medical-mobile” policy is currently 255.255.252.0, which means
that the rule denies access to the 10.1.12.0/22 subnet as well as the adjacent 10.1.16.0/22 subnet 1
.
This is not consistent with the scenario requirements, which state that only the 10.1.12.0/22 subnet
should be denied access, while the rest of the 10.1.0.0/16 range should be permitted access.
To fix this issue, the subnet mask in rule 3 should be changed to 255.255.248.0, which means that the
rule only denies access to the 10.1.8.0/21 subnet, which includes the 10.1.12.0/22 subnet 1
. This
way, the rule matches the scenario requirements more precisely.
Question 4
A company has an Aruba ClearPass server at 10.47.47.8, FQDN radius.acnsxtest.local. This exhibit
shows ClearPass Policy Manager's (CPPM's) settings for an Aruba Mobility Controller (MC).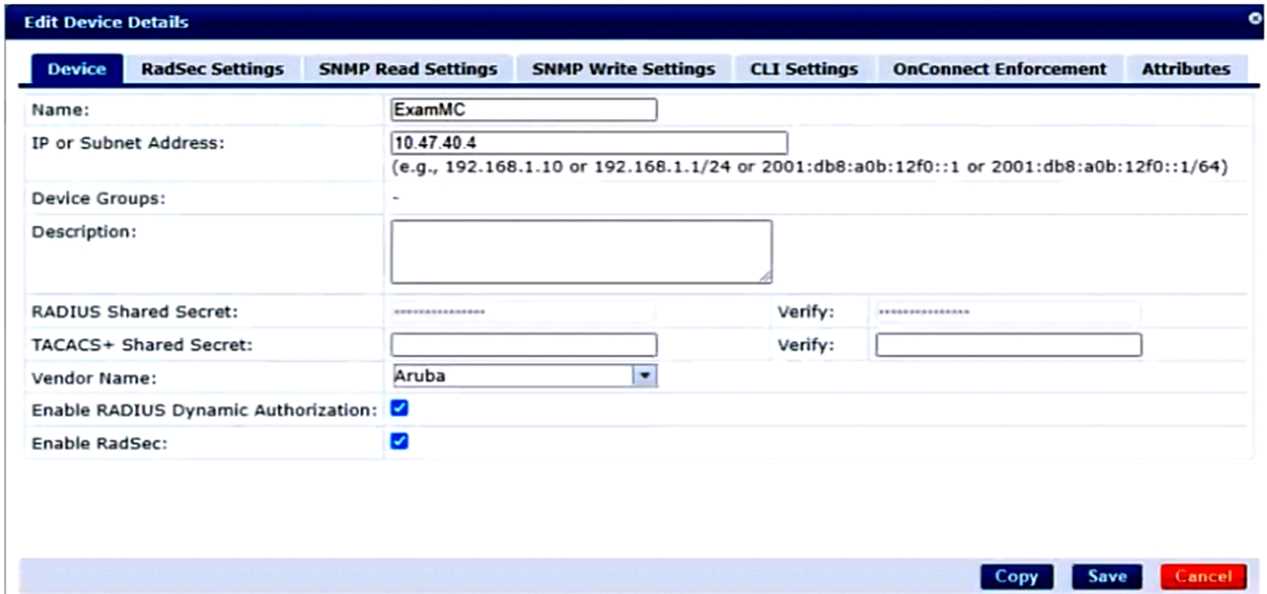
The MC is already configured with RADIUS authentication settings for CPPM, and RADIUS requests
between the MC and CPPM are working. A network admin enters and commits this command to
enable dynamic authorization on the MC:
aaa rfc-3576-server 10.47.47.8
But when CPPM sends CoA requests to the MC, they are not working. This exhibit shows the RFC
3576 server statistics on the MC: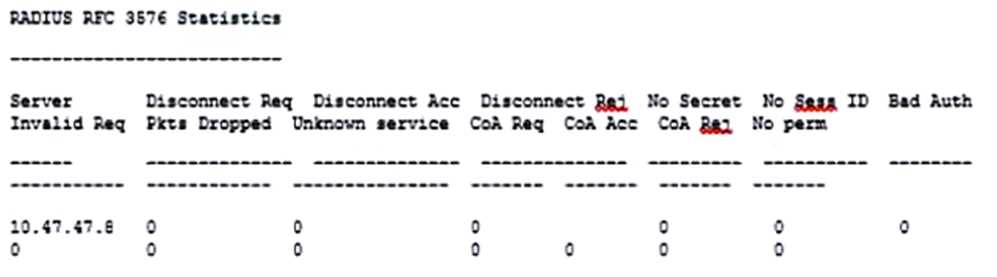
How could you fix this issue?
- A. Change the UDP port in the MCs’ RFC 3576 server config to 3799.
- B. Enable RadSec on the MCs’ RFC 3676 server config.
- C. Configure the MC to obtain the time from a valid NTP server.
- D. Make sure that CPPM is using an ArubaOS Wireless RADIUS CoA enforcement profile.
Answer:
A
Explanation:
Dynamic authorization is a feature that allows CPPM to send change of authorization (CoA) or
disconnect messages to the MC to modify or terminate a user session based on certain conditions or
events 1
.
Dynamic authorization uses the RFC 3576 protocol, which is an extension of the RADIUS
protocol 2
.
To enable dynamic authorization on the MC, you need to configure the IP address and UDP port of
the CPPM server as the RFC 3576 server on the MC 3
. The default UDP port for RFC 3576 is 3799, but
it can be changed on the CPPM server .
The MC and CPPM must use the same UDP port for dynamic
authorization to work properly 3
.
In this scenario, the MC is configured with the IP address of the CPPM server (10.47.47.8) as the RFC
3576 server, but it is using the default UDP port of 3799. However, according to the exhibit, the
CPPM server is using a different UDP port of 1700 for dynamic authorization . This mismatch causes
the CoA requests from CPPM to fail on the MC, as shown by the statistics .
To fix this issue, you need to change the UDP port in the MCs’ RFC 3576 server config to match the
UDP port used by CPPM, which is 1700 in this case. Alternatively, you can change the UDP port in
CPPM to match the default UDP port of 3799 on the MC.
Either way, you need to ensure that both
devices use the same UDP port for dynamic authorization 3
.
Question 5
Refer to the scenario.
A customer requires these rights for clients in the “medical-mobile” AOS firewall role on Aruba
Mobility Controllers (MCs):
Permitted to receive IP addresses with DHCP
Permitted access to DNS services from 10.8.9.7 and no other server
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
Denied access to other 10.0.0.0/8 subnets
Permitted access to the Internet
Denied access to the WLAN for a period of time if they send any SSH traffic
Denied access to the WLAN for a period of time if they send any Telnet traffic
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with “medical-mobile” clients, only
send return traffic.
The exhibits below show the configuration for the role.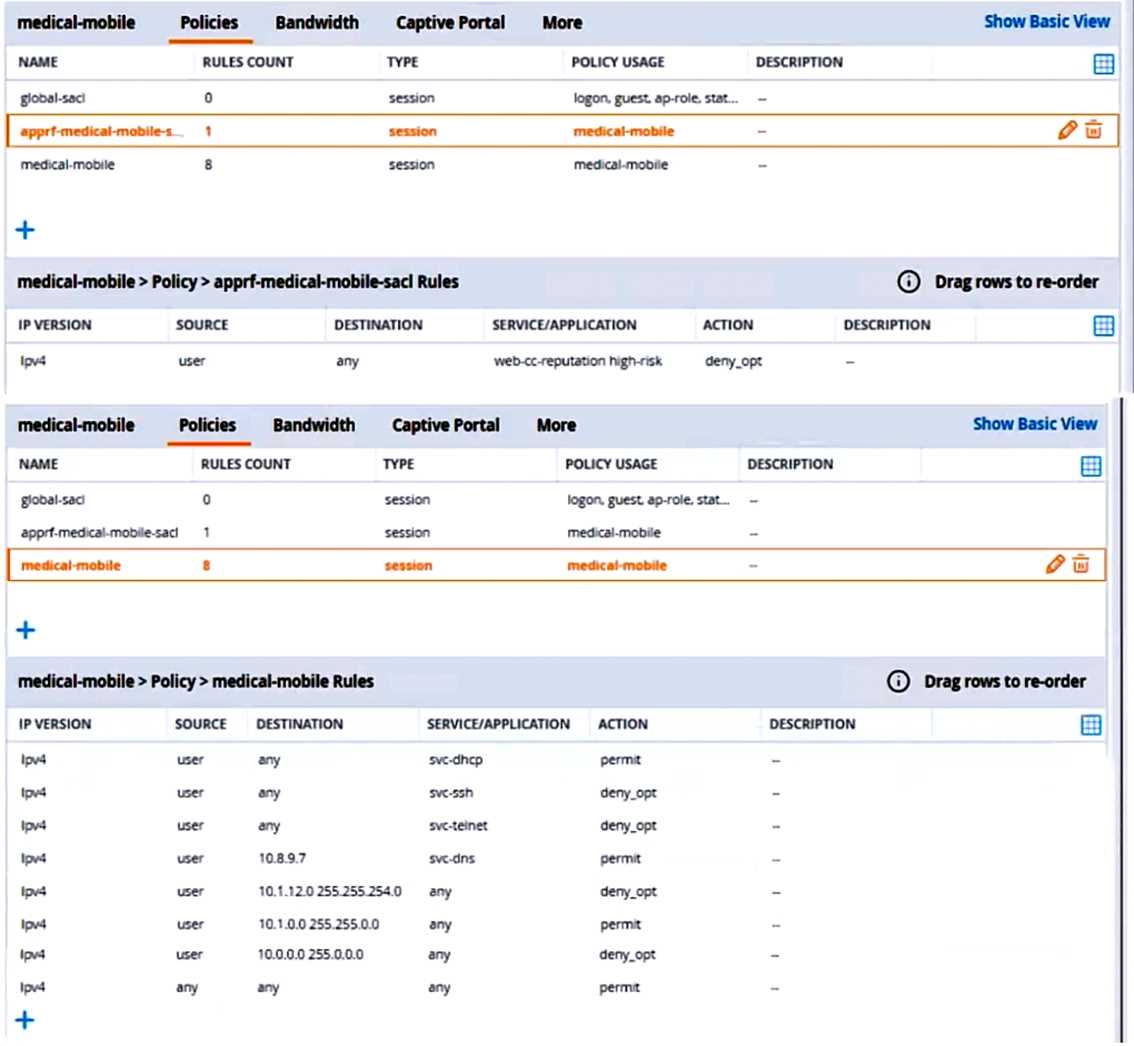
What setting not shown in the exhibit must you check to ensure that the requirements of the
scenario are met?
- A. That denylisting is enabled globally on the MCs’ firewalls
- B. That stateful handling of traffic is enabled globally on the MCs’ firewalls and on the medical- mobile role.
- C. That AppRF and WebCC are enabled globally and on the medical-mobile role
- D. That the MCs are assigned RF Protect licenses
Answer:
C
Explanation:
AppRF and WebCC are features that allow the MCs to classify and control application traffic and web
content based on predefined or custom categories 12
. These features are required to meet the
scenario requirements of denying access to all high-risk websites and denying access to the WLAN
for a period of time if they send any SSH or Telnet traffic.
To enable AppRF and WebCC, you need to check the following settings:
On the global level, you need to enable AppRF and WebCC under Configuration > Services >
AppRF and Configuration > Services > WebCC, respectively 12
.
On the role level, you need to enable AppRF and WebCC under Configuration > Security > Access
Control > Roles > medical-mobile > AppRF and Configuration > Security > Access Control > Roles >
medical-mobile > WebCC, respectively 12
.
You also need to make sure that the MCs have valid licenses for AppRF and WebCC, which are
included in the ArubaOS PEFNG license 3
.
Question 6
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement
802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba
gateway cluster. The gateway cluster should assign these clients to the “eth-internet" role. The
gateway should also handle assigning clients to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below:
The gateway cluster has two gateways with these IP addresses:
• Gateway 1
o VLAN 4085 (system IP) = 10.20.4.21
o VLAN 20 (users) = 10.20.20.1
o VLAN 4094 (WAN) = 198.51.100.14
• Gateway 2
o VLAN 4085 (system IP) = 10.20.4.22
o VLAN 20 (users) = 10.20.20.2
o VLAN 4094 (WAN) = 198.51.100.12
• VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster.
If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able
to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
Assume that you have configured the correct UBT zone and port-access role settings. However, the
solution is not working.
What else should you make sure to do?
- A. Assign VLAN 20 as the access VLAN on any edge ports to which tunneled clients might connect.
- B. Create a new VLAN on the AOS-CX switch and configure that VLAN as the UBT client VLAN.
- C. Assign sufficient VIA licenses to the gateways based on the number of wired clients that will connect.
- D. Change the port-access auth-mode mode to client-mode on any edge ports to which tunneled clients might connect.
Answer:
B
Explanation:
The correct answer is B. Create a new VLAN on the AOS-CX switch and configure that VLAN as the
UBT client VLAN.
User-based tunneling (UBT) is a feature that allows the AOS-CX switches to tunnel the traffic from
wired clients to a mobility gateway cluster, where they can be assigned a role and a VLAN based on
their authentication and authorization 1
.
To enable UBT, the switches need to have a UBT zone
configured with the IP addresses of the gateways, and a UBT client VLAN configured with the ubt-
client-vlan command 2
.
The UBT client VLAN is a special VLAN that is used to encapsulate the traffic from the tunneled clients
before sending it to the gateways.
The UBT client VLAN must be different from any other VLANs used
on the switch or the network, and it must not be assigned to any ports or interfaces on the switch 2
.
The UBT client VLAN is only used internally by the switch for UBT, and it is not visible to the clients or
the gateways.
In this scenario, the customer wants to tunnel the clients that pass user authentication to the
gateway cluster, where they will be assigned to VLAN 20. Therefore, the switch must have a UBT
client VLAN configured that is different from VLAN 20 or any other VLANs on the network.
For
example, the switch can use VLAN 4000 as the UBT client VLAN, as shown in one of the web search
results 3
. The switch must also have a UBT zone configured with the system IP addresses of the
gateways as the primary and backup controllers, as explained in question 3.
The other options are not correct or relevant for this issue:
Option A is not correct because assigning VLAN 20 as the access VLAN on any edge ports to which
tunneled clients might connect would conflict with UBT.
The access VLAN is the VLAN that is assigned
to untagged traffic on a port, and it is used for local switching on the switch 4
. If VLAN 20 is assigned
as the access VLAN, then the traffic from the clients will not be tunneled to the gateways, but rather
switched locally on VLAN 20. This would defeat the purpose of UBT and cause inconsistency in role
and VLAN assignment.
Option C is not correct because VIA licenses are not required for UBT. VIA licenses are required for
enabling VPN services on Aruba Mobility Controllers for remote access clients using Aruba Virtual
Intranet Access (VIA) software . VIA licenses are not related to UBT or wired clients.
Option D is not correct because changing the port-access auth-mode mode to client-mode on any
edge ports to which tunneled clients might connect would not affect UBT. The port-access auth-mode
mode determines how a port handles authentication requests from multiple clients connected to a
single port . Client-mode is the default mode that allows only one client per port, while multi-client-
mode allows multiple clients per port. The port-access auth-mode mode does not affect how UBT
works or how traffic is tunneled from a port.
Question 7
A company has Aruba gateways and wants to start implementing gateway IDS/IPS. The customer has
selected Block for the Fail Strategy.
What might you recommend to help minimize unexpected outages caused by using this particular
fall strategy?
- A. Configuring a relatively high threshold for the gateway threat count alerts
- B. Making sure that the gateways have formed a cluster and operate in default gateway mode
- C. Setting the IDS or IPS policy to the least restrictive option, Lenient
- D. Enabling alerts and email notifications for events related to gateway IPS engine utilization and errors
Answer:
D
Explanation:
The correct answer is D. Enabling alerts and email notifications for events related to gateway IPS
engine utilization and errors.
Gateway IDS/IPS is a feature that allows the Aruba gateways to monitor and block malicious or
unwanted traffic based on predefined or custom rules 1
.
The Fail Strategy is a setting that determines
how the gateways handle traffic when the IPS engine fails or crashes 2
.
The Block option means that
the gateways will stop forwarding traffic until the IPS engine recovers, while the Bypass option
means that the gateways will continue forwarding traffic without inspection 2
.
The Block option provides more security, but it also increases the risk of network outages if the IPS
engine fails frequently or for a long time 2
.
To minimize this risk, it is recommended to enable alerts
and email notifications for events related to gateway IPS engine utilization and errors 3
.
This way, the
network administrators can be informed of any issues with the IPS engine and take appropriate
actions to restore or troubleshoot it 3
.
The other options are not correct or relevant for this issue:
Option A is not correct because configuring a relatively high threshold for the gateway threat count
alerts would not help minimize unexpected outages caused by using the Block option.
The gateway
threat count alerts are used to notify the network administrators of the number of threats detected
by the IPS engine, but they do not affect how the gateways handle traffic when the IPS engine fails 4
.
Option B is not correct because making sure that the gateways have formed a cluster and operate in
default gateway mode would not help minimize unexpected outages caused by using the Block
option. The gateway cluster mode is used to provide high availability and load balancing for the
gateways, but it does not affect how the gateways handle traffic when the IPS engine fails . The
default gateway mode is used to enable routing and NAT functions on the gateways, but it does not
affect how the gateways handle traffic when the IPS engine fails .
Option C is not correct because setting the IDS or IPS policy to the least restrictive option, Lenient,
would not help minimize unexpected outages caused by using the Block option.
The IDS or IPS policy
is used to define what rules are applied by the IPS engine to inspect and block traffic, but it does not
affect how the gateways handle traffic when the IPS engine fails 2
. The Lenient option contains fewer
and older rules than the Moderate or Strict options, which means that it provides less security and
more false negatives .
Question 8
A company has Aruba gateways that are Implementing gateway IDS/IPS in IDS mode. The customer
complains that admins are receiving too frequent of repeat email notifications for the same threat.
The threat itself might be one that the admins should investigate, but the customer does not want
the email notification to repeat as often.
Which setting should you adjust in Aruba Central?
- A. Report scheduling settings
- B. Alert duration and threshold settings
- C. The IDS policy setting (strict, medium, or lenient)
- D. The allowlist settings in the IDS policy
Answer:
B
Explanation:
Alert duration and threshold settings are used to control how often and under what conditions email
notifications are sent for gateway IDS/IPS events 1
. By adjusting these settings, the customer can
reduce the frequency of repeat email notifications for the same threat, while still being informed of
any critical or new threats.
To adjust the alert duration and threshold settings in Aruba Central, the customer can follow these
steps 1
:
In the Aruba Central app, set the filter to Global, a group, or a device.
Under Analyze, click Alerts & Events.
Click the Config icon to open the Alert Severities & Notifications page.
Select the Gateway IDS/IPS tab to view the alert categories and severities for gateway IDS/IPS
events.
Click on an alert category to expand it and view the alert duration and threshold settings for each
severity level.
Enter a value in minutes for the alert duration. This is the time period during which the alert is active
and email notifications are sent.
Enter a value for the alert threshold. This is the number of times the alert must be triggered within
the alert duration before an email notification is sent.
Click Save.
By increasing the alert duration and/or threshold values, the customer can reduce the number of
email notifications for recurring threats, as they will only be sent when the threshold is reached
within the duration. For example, if the customer sets the alert duration to 60 minutes and the alert
threshold to 10 for a Critical severity level, then an email notification will only be sent if the same
threat occurs 10 times or more within an hour.
Question 9
Refer to the scenario.
A customer is migrating from on-prem AD to Azure AD as its sole domain solution. The customer also
manages both wired and wireless devices with Microsoft Endpoint Manager (Intune).
The customer wants to improve security for the network edge. You are helping the customer design a
ClearPass deployment for this purpose. Aruba network devices will authenticate wireless and wired
clients to an Aruba ClearPass Policy Manager (CPPM) cluster (which uses version 6.10).
The customer has several requirements for authentication. The clients should only pass EAP-TLS
authentication if a query to Azure AD shows that they have accounts in Azure AD. To further refine
the clients’ privileges, ClearPass also should use information collected by Intune to make access
control decisions.
Assume that the Azure AD deployment has the proper prerequisites established.
You are planning the CPPM authentication source that you will reference as the authentication
source in 802.1X services.
How should you set up this authentication source?
- A. As Kerberos type
- B. As Active Directory type
- C. As HTTP type, referencing the Intune extension
- D. AS HTTP type, referencing Azure AD's FODN
Answer:
D
Explanation:
An authentication source is a configuration element in CPPM that defines how to connect to an
external identity provider and retrieve user or device information . CPPM supports various types of
authentication sources, such as Active Directory, LDAP, SQL, Kerberos, and HTTP .
To authenticate wireless and wired clients to Azure AD, you need to set up an authentication source
as HTTP type, referencing Azure AD’s FQDN . This type of authentication source allows CPPM to use
REST API calls to communicate with Azure AD and validate the user or device credentials . You also
need to configure the OAuth 2.0 settings for the authentication source, such as the client ID, client
secret, token URL, and resource URL .
To use information collected by Intune to make access control decisions, you need to set up another
authentication source as HTTP type, referencing the Intune extension . This type of authentication
source allows CPPM to use REST API calls to communicate with Intune and retrieve the device
compliance status . You also need to configure the OAuth 2.0 settings for the authentication source,
such as the client ID, client secret, token URL, and resource URL .
Question 10
Refer to the scenario.
A customer requires these rights for clients in the “medical-mobile” AOS firewall role on Aruba
Mobility Controllers (MCs):
Permitted to receive IP addresses with DHCP
Permitted access to DNS services from 10.8.9.7 and no other server
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
Denied access to other 10.0.0.0/8 subnets
Permitted access to the Internet
Denied access to the WLAN for a period of time if they send any SSH traffic
Denied access to the WLAN for a period of time if they send any Telnet traffic
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with “medical-mobile” clients, only
send return traffic.
The exhibits below show the configuration for the role.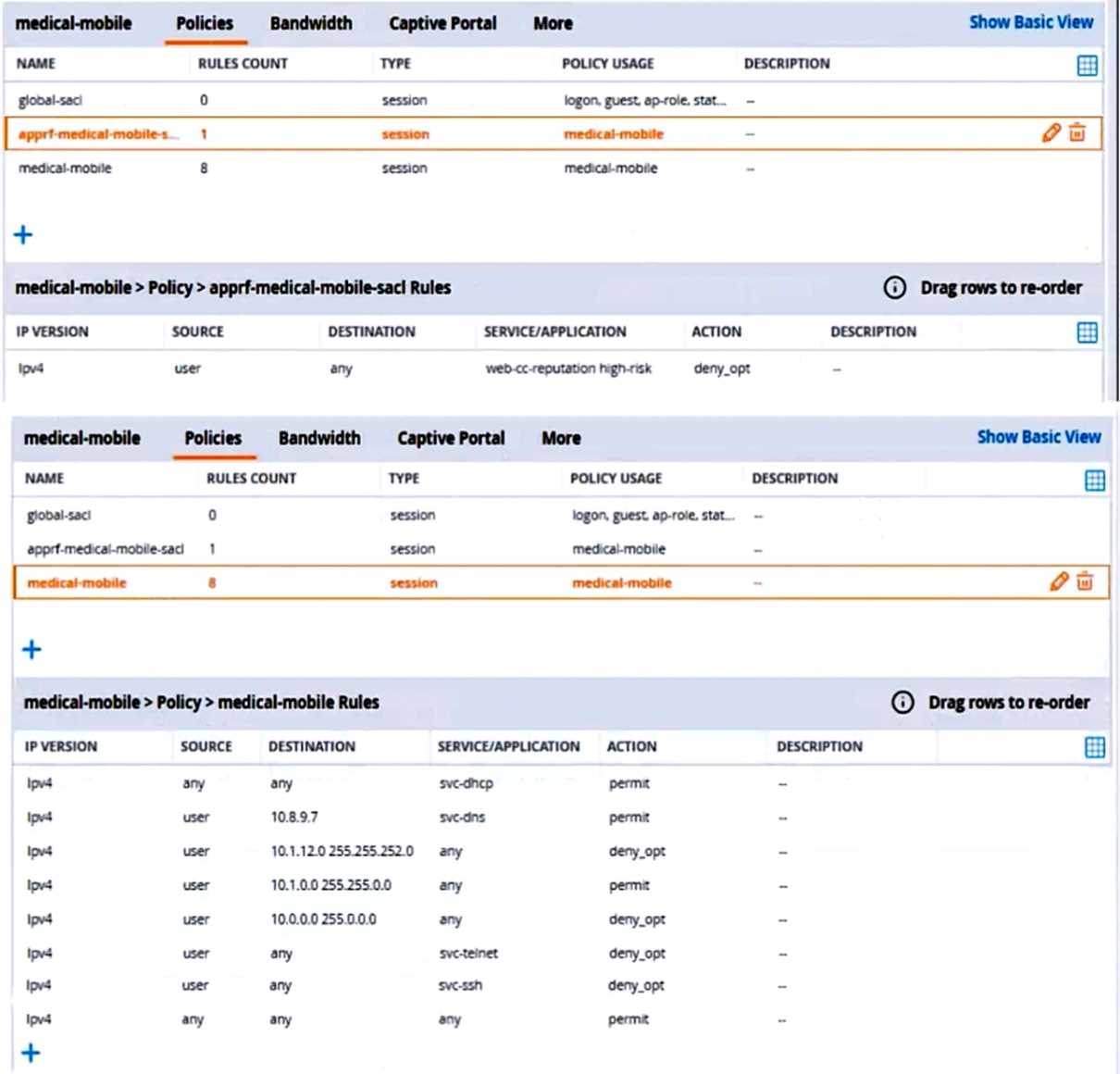
There are multiple issues with the configuration.
What is one of the changes that you must make to the policies to meet the scenario requirements?
(In the options, rules in a policy are referenced from top to bottom. For example, “medical-mobile”
rule 1 is “ipv4 any any svc-dhcp permit,” and rule 8 is “ipv4 any any any permit’.)
- A. In the “medical-mobile” policy, change the source in rule 1 to “user.”
- B. In the “medical-mobile” policy, change the subnet mask in rule 3 to 255.255.248.0.
- C. In the “medical-mobile” policy, move rules 6 and 7 to the top of the list.
- D. Move the rule in the “apprf-medical-mobile-sacl” policy between rules 7 and 8 in the “medical- mobile” policy.
Answer:
C
Explanation:
Rules 6 and 7 in the “medical-mobile” policy are used to deny access to the WLAN for a period of
time if the clients send any SSH or Telnet traffic, as required by the scenario. However, these rules
are currently placed below rule 5, which permits access to the Internet for any traffic. This means
that rule 5 will override rules 6 and 7, and the clients will not be denied access to the WLAN even if
they send SSH or Telnet traffic.
To fix this issue, rules 6 and 7 should be moved to the top of the list, before rule 5. This way, rules 6
and 7 will take precedence over rule 5, and the clients will be denied access to the WLAN if they send
SSH or Telnet traffic, as expected.
Question 11
What is a common characteristic of a beacon between a compromised device and a command and
control server?
- A. Use of IPv6 addressing instead of IPv4 addressing
- B. Lack of encryption
- C. Use of less common protocols such as SNAP
- D. Periodic transmission of small, identically sized packets
Answer:
D
Explanation:
A beacon is a type of network traffic that is sent from a compromised device to a command and
control (C2) server, which is a remote system that controls the malicious activities of the device . A
beacon is used to establish and maintain communication between the device and the C2 server, as
well as to receive instructions or exfiltrate data .
A common characteristic of a beacon is that it is periodic, meaning that it is sent at regular intervals,
such as every few minutes or hours . This helps the C2 server to monitor the status and availability of
the device, as well as to avoid detection by network security tools .
Another common characteristic of a beacon is that it is small and identically sized, meaning that it
contains minimal or fixed amount of data, such as a simple acknowledgment or a random string . This
helps the device to conserve bandwidth and resources, as well as to avoid detection by network
security tools .
Question 12
Refer to the scenario.
A hospital has an AOS10 architecture that is managed by Aruba Central. The customer has deployed a
pair of Aruba 9000 Series gateways with Security licenses at each clinic. The gateways implement
IDS/IPS in IDS mode.
The Security Dashboard shows these several recent events with the same signature, as shown below: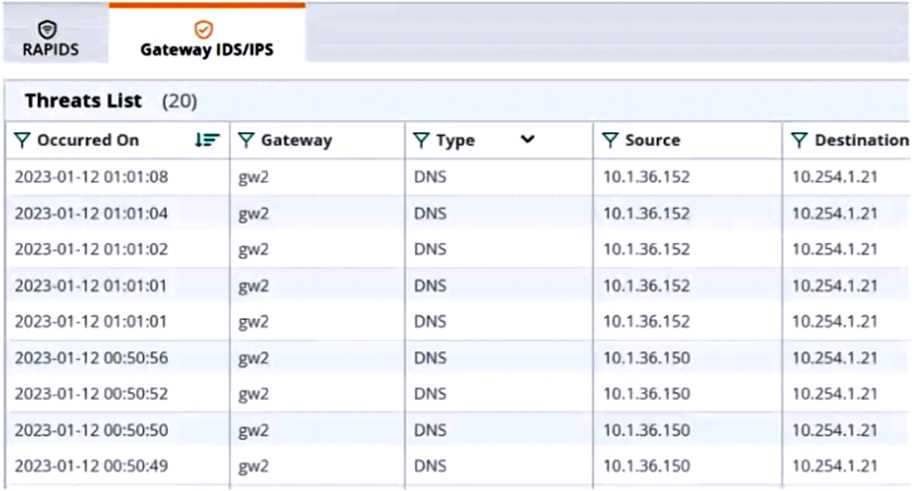
Which step could give you valuable context about the incident?
- A. View firewall sessions on the APs and record the threat sources' type and OS.
- B. View the user-table on APs and record the threat sources' 802.11 settings.
- C. View the RAPIDS Security Dashboard and see if the threat sources are listed as rogues.
- D. Find the Central client profile for the threat sources and note their category and family.
Answer:
C
Explanation:
The RAPIDS Security Dashboard is a feature of Aruba Central that provides a comprehensive view of
the network security status, including IDS/IPS events, rogue APs, and wireless intrusion detection. By
viewing the RAPIDS Security Dashboard, you can see if the threat sources are rogue APs that are
spoofing legitimate DNS servers or clients.
This can give you valuable context about the incident and
help you identify the root cause of the attack1
Reference:
Aruba Central User Guide
Question 13
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement
802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba
gateway cluster. The gateway cluster should assign these clients to the “eth-internet" role. The
gateway should also handle assigning clients to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below: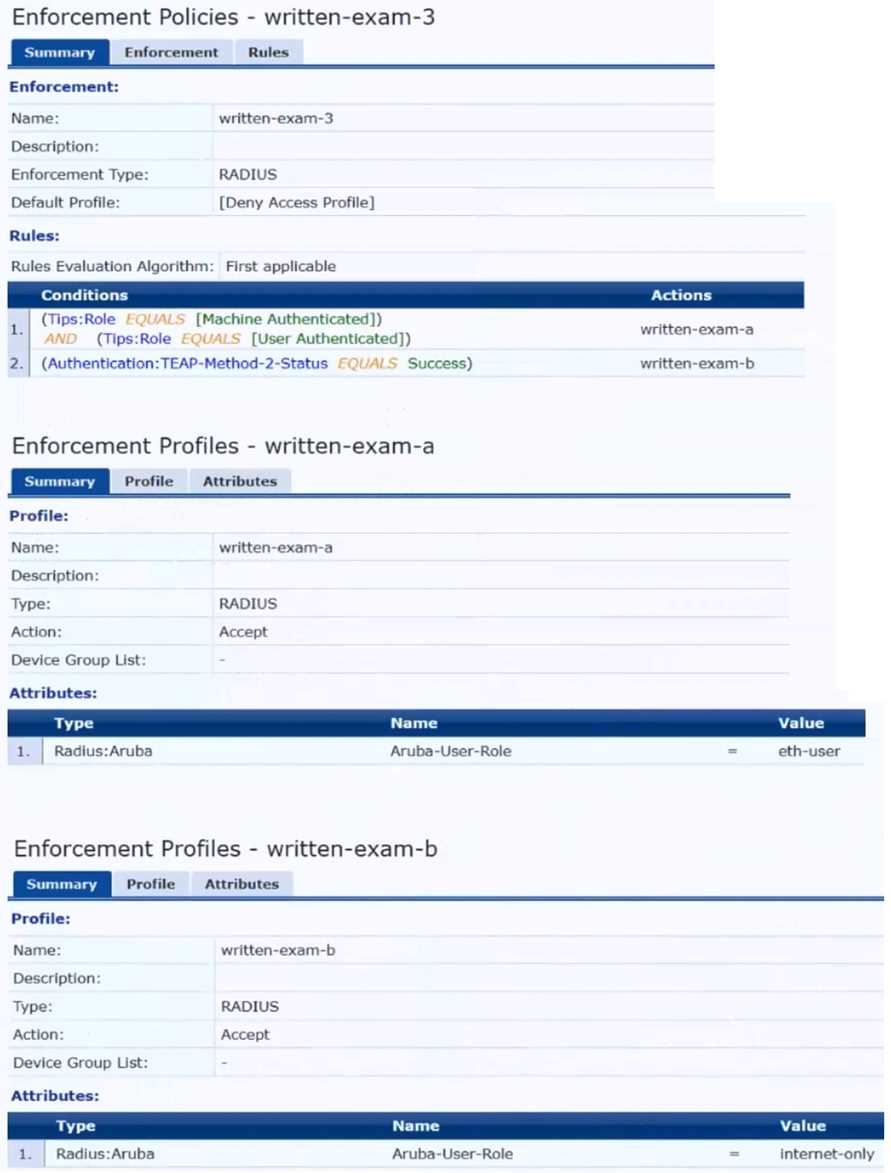
The gateway cluster has two gateways with these IP addresses:
• Gateway 1
o VLAN 4085 (system IP) = 10.20.4.21
o VLAN 20 (users) = 10.20.20.1
o VLAN 4094 (WAN) = 198.51.100.14
• Gateway 2
o VLAN 4085 (system IP) = 10.20.4.22
o VLAN 20 (users) = 10.20.20.2
o VLAN 4094 (WAN) = 198.51.100.12
• VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster.
If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able
to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
What is one change that you should make to the solution?
- A. Change the ubt-client-vlan to VLAN 13.
- B. Configure edge ports in VLAN trunk mode.
- C. Remove VLAN assignments from role configurations on the gateways.
- D. Configure the UBT solution to use VLAN extend mode.
Answer:
C
Explanation:
The UBT solution requires that the VLAN assignments for the wired clients are done by the gateway,
not by the switch. Therefore, the role configurations on the gateways should not have any VLAN
assignments, as they would override the VLAN 20 that is specified in the enforcement profile.
Instead, the role configurations should only have policies that define the access rights for the clients
in the “eth-internet” role.
This way, the gateway can assign the clients to VLAN 20 and apply the
appropriate policies based on their role1
Reference:
: Aruba Certified Network Technician (ACNT) | HPE Aruba Networking, section “Get the Edge: An
Introduction to Aruba Networking Solutions”
Question 14
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement
802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba
gateway cluster. The gateway cluster should assign these clients to the “eth-internet" role. The
gateway should also handle assigning clients to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below: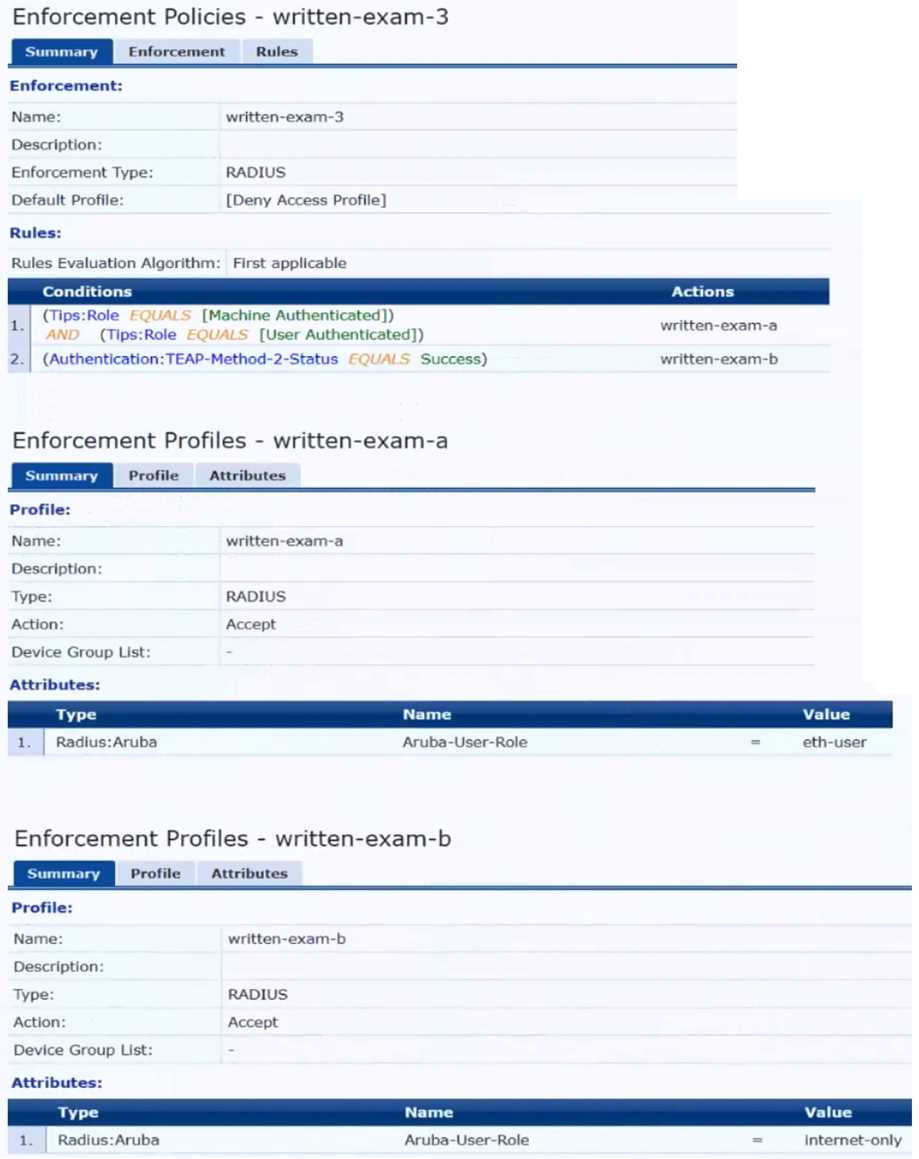
The gateway cluster has two gateways with these IP addresses:
• Gateway 1
o VLAN 4085 (system IP) = 10.20.4.21
o VLAN 20 (users) = 10.20.20.1
o VLAN 4094 (WAN) = 198.51.100.14
• Gateway 2
o VLAN 4085 (system IP) = 10.20.4.22
o VLAN 20 (users) = 10.20.20.2
o VLAN 4094 (WAN) = 198.51.100.12
• VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster.
If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able
to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
Assume that you are using the “myzone” name for the UBT zone.
Which is a valid minimal configuration for the AOS-CX port-access roles?
- A. port-access role eth-internet gateway-zone zone myzone gateway-role eth-user
- B. port-access role internet-only gateway-zone zone myzone gateway-role eth-internet
- C. port-access role eth-internet gateway-zone zone myzone gateway-role eth-internet vlan access 20
- D. port-access role internet-only gateway-zone zone myzone gateway-role eth-internet vlan access
Answer:
B
Explanation:
The UBT solution requires that the edge ports on the switches are configured in VLAN trunk mode,
not access mode. This is because the UBT solution uses a special VLAN (VLAN 4095 by default) to
encapsulate the user traffic and tunnel it to the gateway. The edge ports need to allow this VLAN as
well as any other VLANs that are used for management or control traffic.
Therefore, the edge ports
should be configured as VLAN trunk ports and allow the necessary VLANs1
Reference:
: Aruba Certified Network Technician (ACNT) | HPE Aruba Networking, section “Get the Edge: An
Introduction to Aruba Networking Solutions”
Question 15
Refer to the scenario.
A customer requires these rights for clients in the “medical-mobile” AOS firewall role on Aruba
Mobility Controllers (MCs):
Permitted to receive IP addresses with DHCP
Permitted access to DNS services from 10.8.9.7 and no other server
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
Denied access to other 10.0.0.0/8 subnets
Permitted access to the Internet
Denied access to the WLAN for a period of time if they send any SSH traffic
Denied access to the WLAN for a period of time if they send any Telnet traffic
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with “medical-mobile” clients, only
send return traffic.
The line below shows the effective configuration for the role.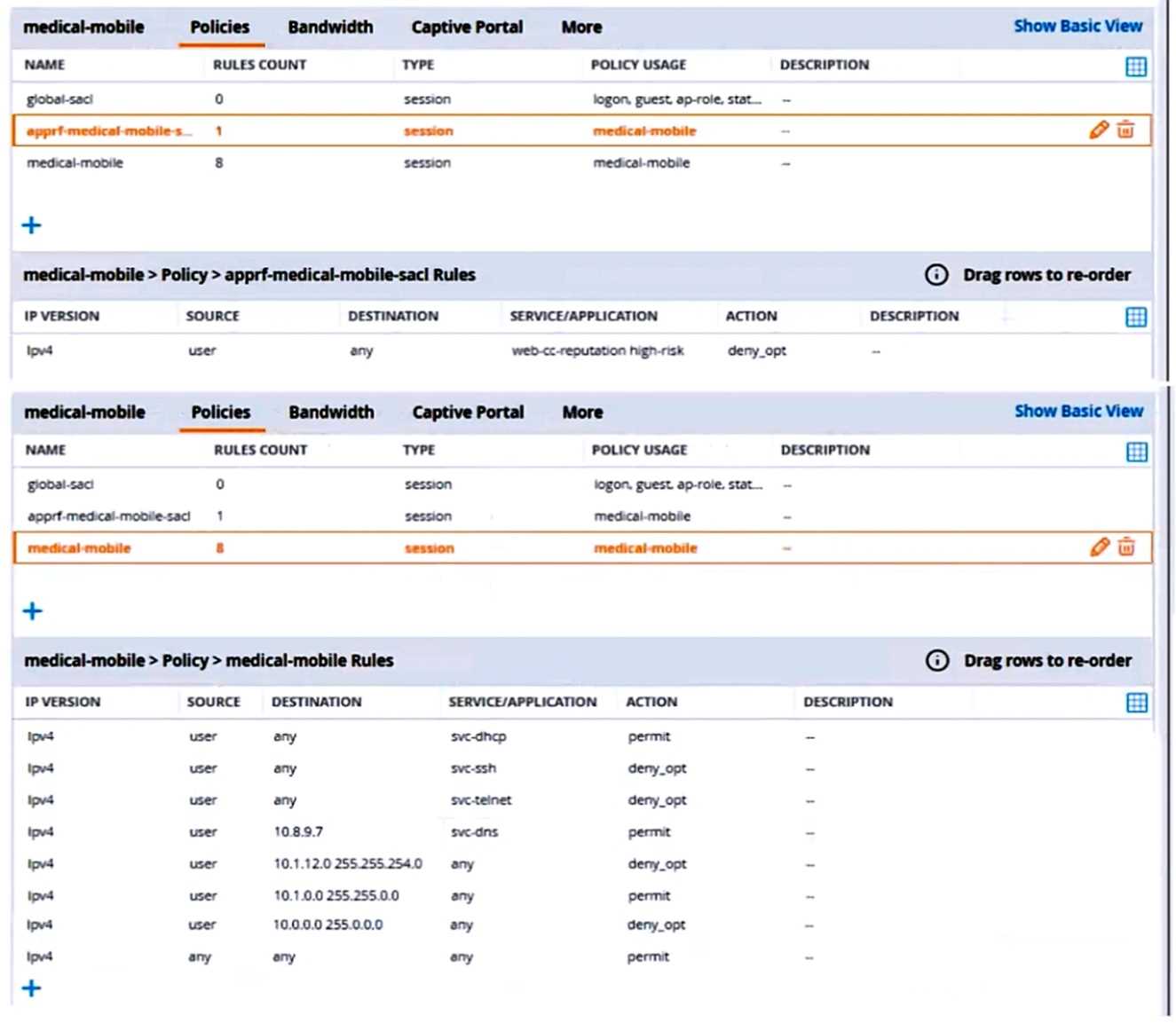
There are multiple issues with this configuration. What is one change you must make to meet the
scenario requirements? (In the options, rules in a policy are referenced from top to bottom. For
example, “medical-mobile” rule 1 is “ipv4 any any svc-dhcp permit,” and rule 6 is “ipv4 any any any
permit’.)
- A. Apply the "apprf-medical-mobile-sjcT policy explicitly to the 'medical-mobile' user-role under the 'medical-mobile" policy.
- B. In the "medical-mobile" policy, change the action for rules 2 and 3 to reject.
- C. In the "medical-mobile" policy, move rule 5 under rule 6.
- D. In the "medical-mobile* policy, change the subnet mask in rule 5 to 255.255.252.0.
Answer:
D
Explanation:
The scenario requires that the clients in the “medical-mobile” role are denied access to the
10.1.12.0/22 subnet, which is a range of IP addresses from 10.1.12.0 to 10.1.15.255. However, the
current configuration in rule 5 has a subnet mask of 255.255.240.0, which means that it matches any
IP address from 10.1.0.0 to 10.1.15.255. This is too broad and would deny access to other subnets in
the 10.1.0.0/16 range that should be permitted according to the scenario.
Therefore, the subnet
mask in rule 5 should be changed to 255.255.252.0, which would match only the IP addresses from
10.1.12.0 to 10.1.15.255 and deny access to them as required by the scenario.1
Reference:
: Configuring Firewall Policies - Aruba, section “Firewall Policies”