HP hpe6-a79 practice test
Aruba Certified Mobility Expert Written Exam
Question 1
Refer to the exhibit.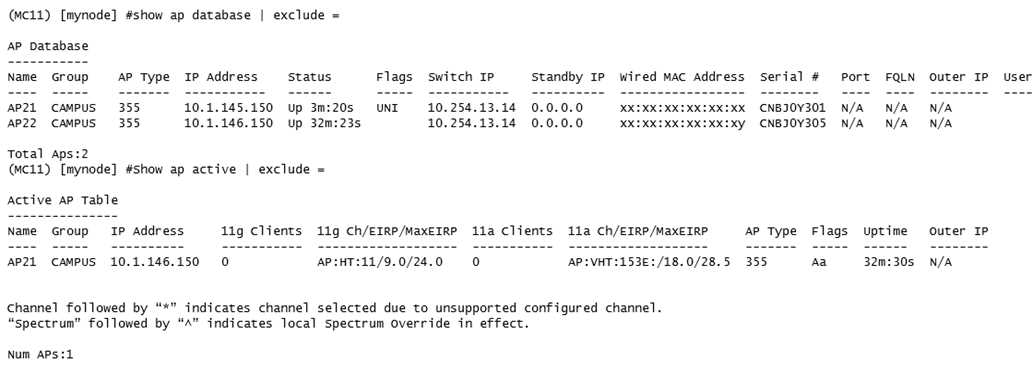
A network administrator deploys a new Mobility Master (MM) - Mobility Controller (MC) network. To
test the solution, the network administrator accesses the console of a pair of APs and statically
provisions them. However, one of the APs does not propagate the configured SSIDs. The network
administrator looks at the logs and sees the output shown in the exhibit.
Which actions must the network administrator take to solve the problem?
- A. Create another AP group in the MC's configuration, and re-provision one AP with a different group.
- B. Re-provision one of the APs with a different name, and add new entries with the proper group in the whitelist.
- C. Re-provision the AP with a different group, and modify the name of one AP in the whitelist.
- D. Re-provision one of the APs with a different name or modify the name in the whitelist.
Answer:
D
Question 2
Refer to the exhibit.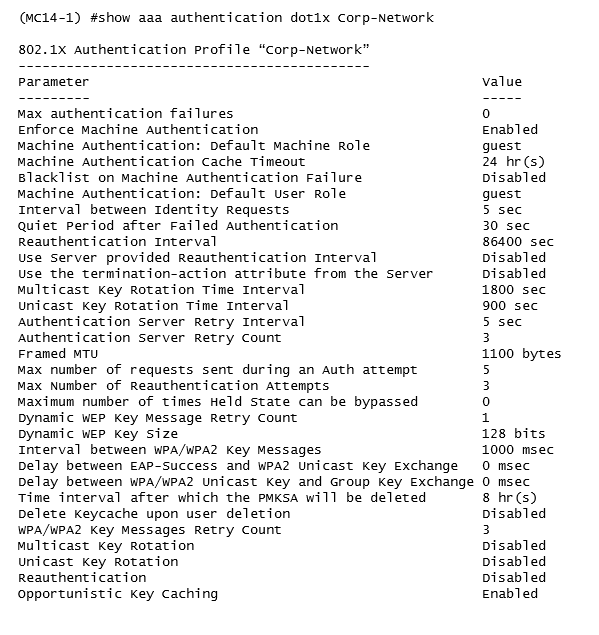
The network administrator must ensure that the configuration will force users to authenticate
periodically every eight hours. Which configuration is required to effect this change?
- A. Set the reauth-period to 28800 enable reauthentication in the dotlx profile.
- B. Set the reauth-period to 28800 enable reauthentication in the AAA profile.
- C. Set the reauth-period to 28800 enable reauthentication in both dotlx and AAA profile.
- D. Set the reauth-period to 28800 in the dotlx profile and enable reauthentication in the AAA profile.
Answer:
A
Question 3
Refer to the exhibit.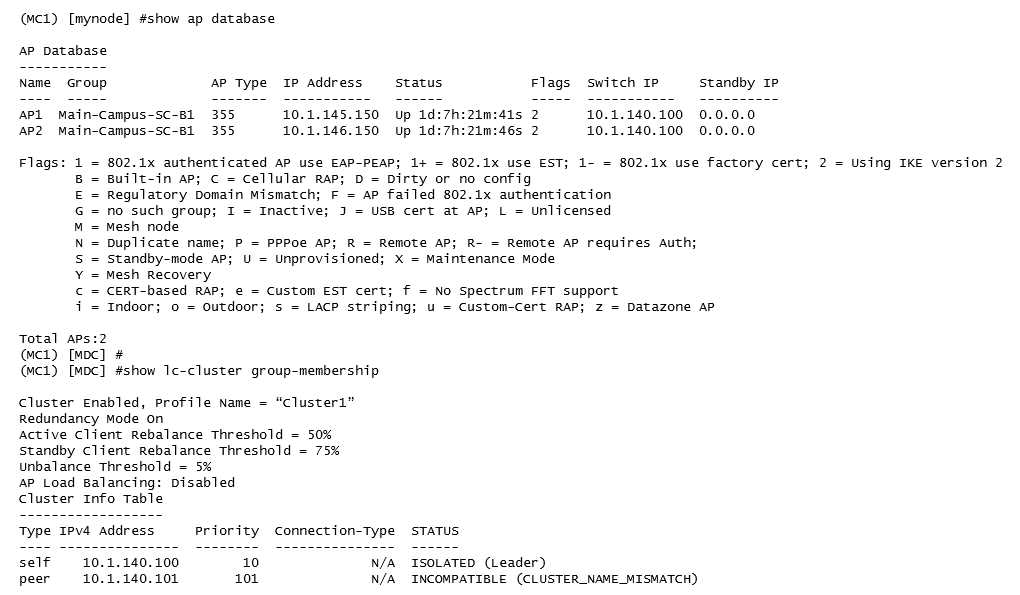
After deploying several cluster pairs, the network administrator notices that all APs assigned to
Cluster1 communicate with MC1 instead of being distributed between members of the cluster. Also,
no IP addresses are shown under the Standby IP column.
What should the network administrator do to fix this situation?
- A. Apply the same cluster profile to both members.
- B. Enable Cluster AP load balancing.
- C. Rename the cluster profile as "CLUSTER1".
- D. Place MCs at the same hierarchical group level.
Answer:
C
Question 4
Refer to the exhibits.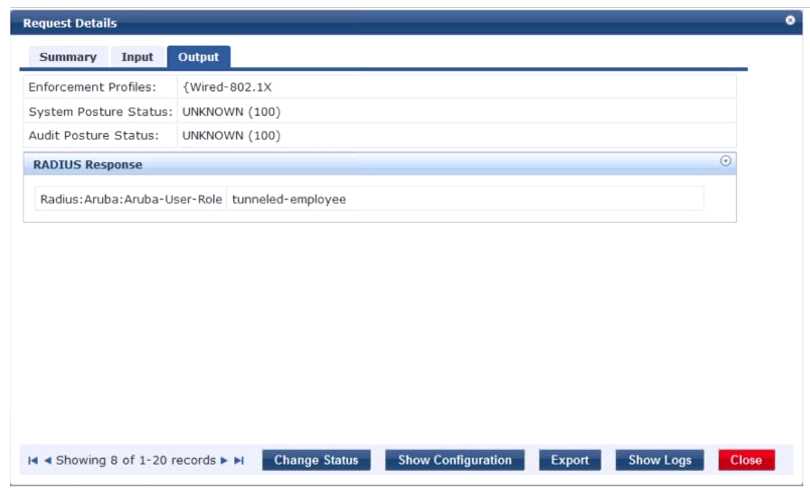
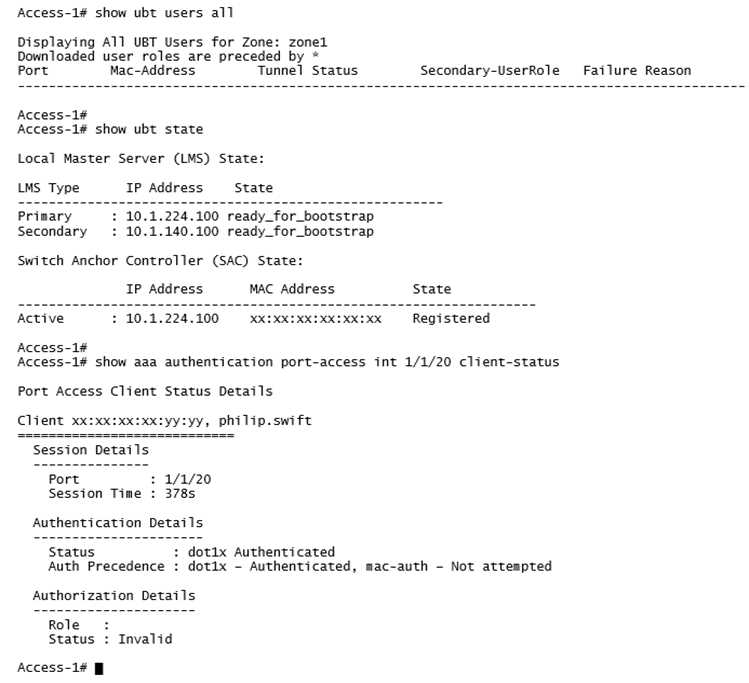
A network administrator deploys User Based Tunneling (UBT) in a corporate network to unify the
security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results,
and sends the Aruba-User-Role attribute as expected. However, the AOS-CX based switch does not
seem to build the tunnel to the Mobility Controller (MC) for this user.
Why does the switch fail to run UBT for the user?
- A. The switch has not fully associated to the MC.
- B. ClearPass is sending the wrong Vendor ID.
- C. The switch is not configured with the gateway-role.
- D. ClearPass is sending the wrong VSA type.
- E. The switch is not configured with the port-access role.
Answer:
B
Question 5
Refer to the exhibit.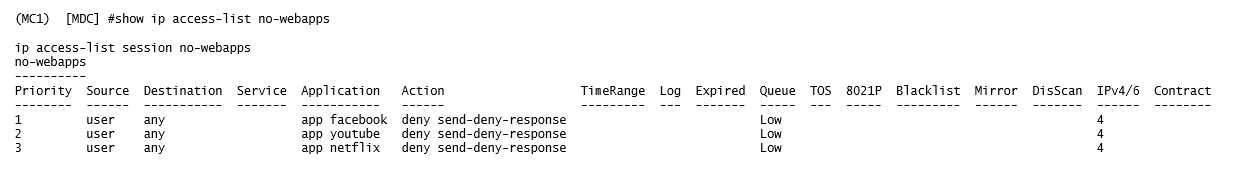
A network administrator completes the initial configuration dialog of the Mobility Controllers (MCs)
and they join the Mobility Master (MM) for the first time. After the MM-MC association process,
network administrator only creates AP groups, VAPs, and roles. Next, the network administrator
proceeds with the configuration of the policies and creates the policy shown in the exhibit.
Which additional steps must be done to make sure this configuration takes effect over the contractor
users?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
C
Question 6
Refer to the exhibit.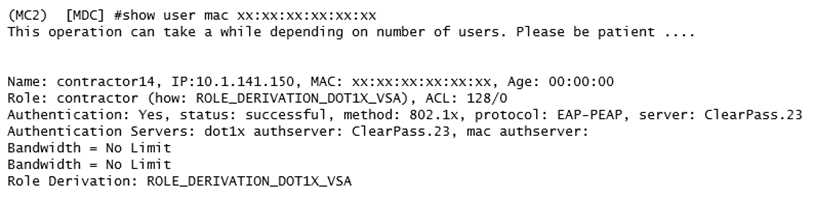
A network administrator is evaluating a deployment to validate that a user is assigned the proper
role and reviews the output in the exhibit. How is the role assigned to user?
- A. The MC assigned the role based on Aruba VSAs.
- B. The MC assigned the machine authentication default user role.
- C. The MC assigned the default role based on the authentication method.
- D. The MC assigned the role based on server derivation rules.
Answer:
C
Question 7
A network administrator is in charge of a Mobility Master (MM) Mobility Controller (MC) based
network security. Recently the Air Monitors detected a Rogue AP in the network and the
administrator wants to enable Tarpit based wireless containment.
What profile must the administrator enable tarpit wireless containment on?
- A. IDS Unauthorized device profile
- B. IDS profile
- C. IDS General profile
- D. IDS DOS profile
Answer:
A
Question 8
Refer to the exhibit.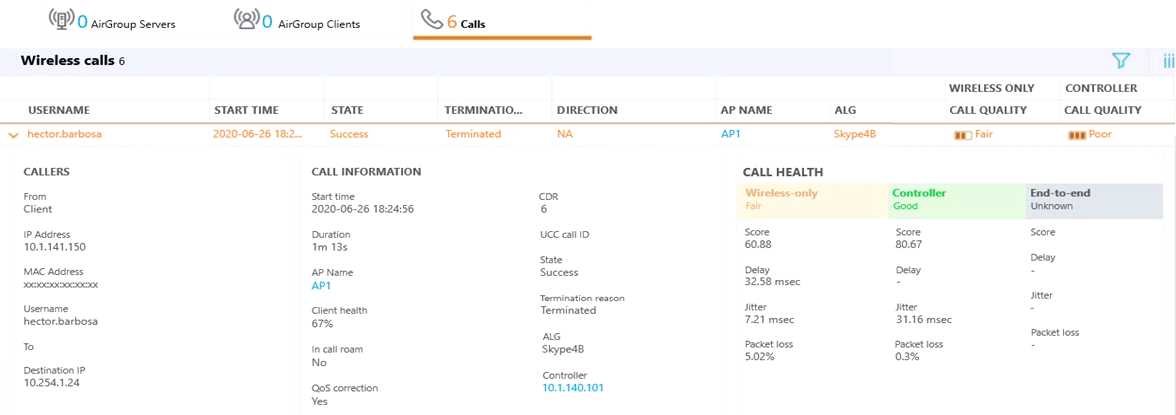
A network administrator has recently enabled WMM on the VAPs SSID profile and enabled UCC
Skype4B ALG at the Mobility Master level. During testing, some voice and video conference calls
were made, and it was concluded that the call quality has dramatically improved. However, end to
end information isnt displayed in the calls details. Also, Skype4B app-sharings performance is poor
at times.
What must the administrator do next in order to enable end to end call visibility and QoS correction
to app-sharing service?
- A. Deploy the SDN API Software in the Skype4B Solution and point to the MM.
- B. Increase the app-sharing DSCP value in the Skype4B ALG profile.
- C. Enable UCC monitoring on the "default-controller' mgmt.-server profile.
- D. Enable the App-sharing ALG profile at both MM and MD hierarchy levels.
Answer:
D
Question 9
Refer to the exhibit.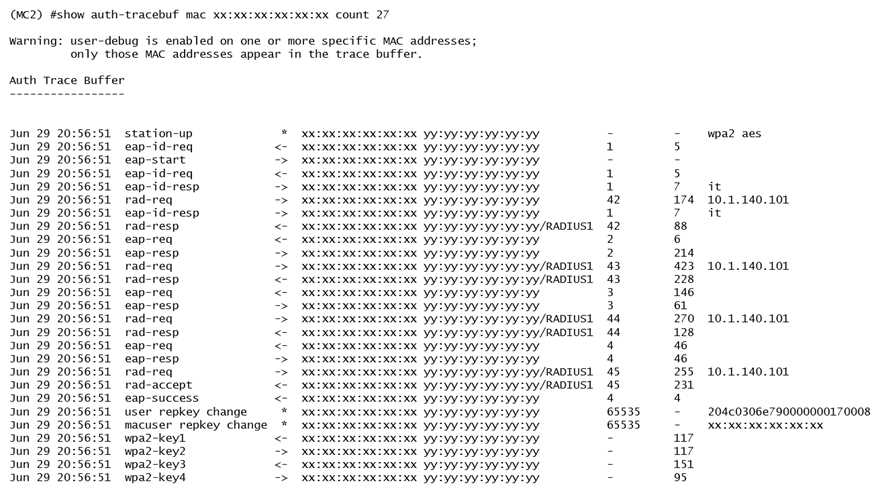
A network administrator is validating client connectivity and executes the show command shown in
the exhibit. Which authentication method was used by a wireless station?
- A. EAP authentication
- B. 802.1X machine authentication
- C. MAC authentication
- D. 802.1X user authentication
Answer:
D
Question 10
Refer to the exhibit.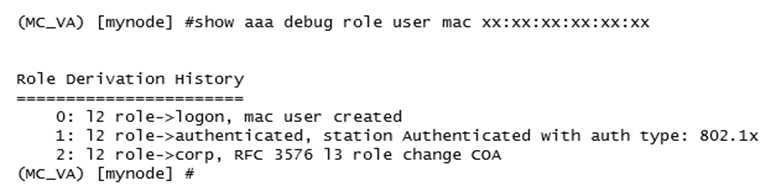
A network administrator has Mobility Master (MM) - Mobility Controller (MC) based network and
has fully integrated the MCs with ClearPass for RADIUS-based AAA services. The administrator is
testing different ways to run user role derivation.
Based on the show command output, what method has the administrator use for assigning the
corp role to client with MAC xx:xx:xx:xx:xx:xx?
- A. Dynamic Authorization using VSA attributes.
- B. Dynamic Authorization using IETF attributes.
- C. Server Derivation Rules using IETF attributes.
- D. User Derivation Rules using the client's MAC.
Answer:
A
Question 11
Refer to the exhibits.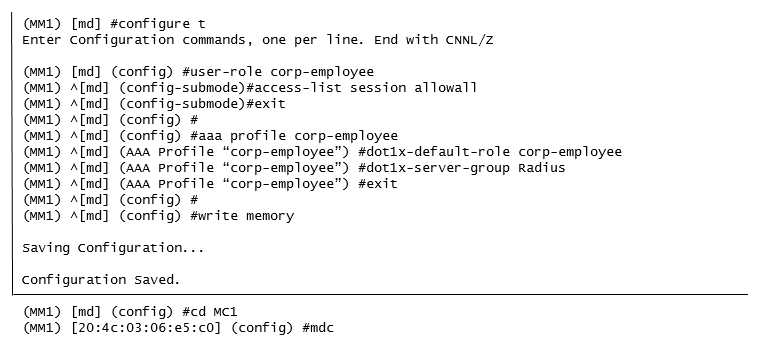
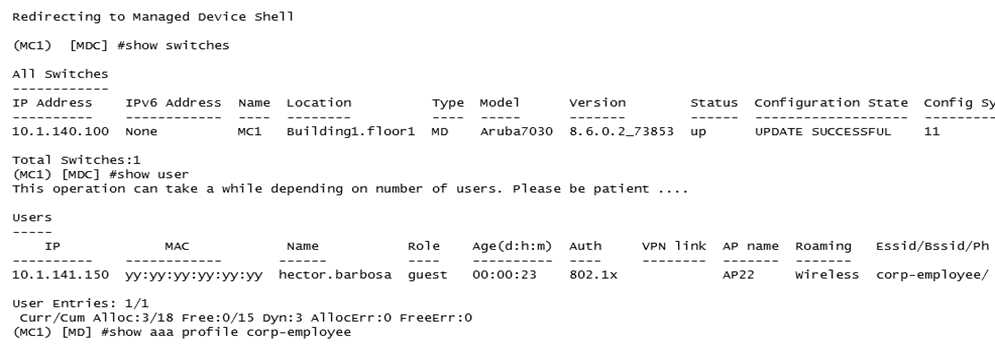
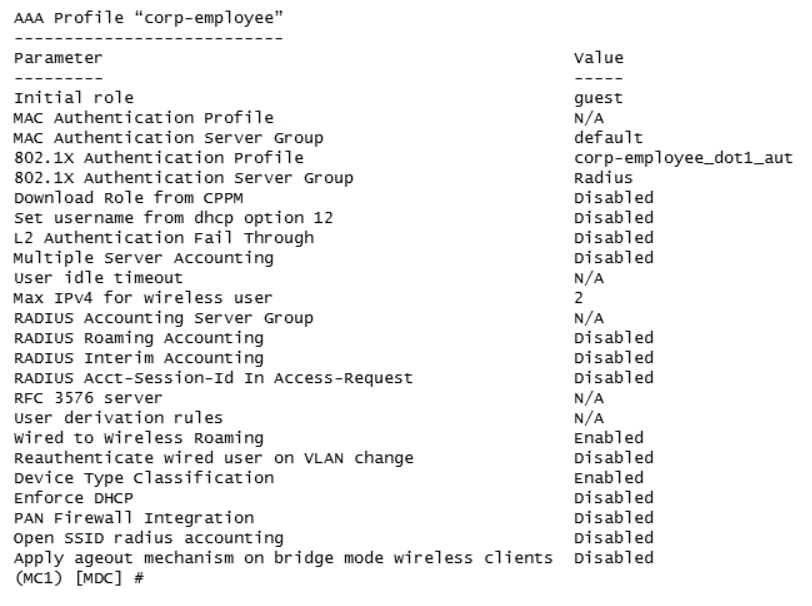
A network administrator has fully deployed a WPA3 based WLAN with 802.1X authentication. Later
he defined corp-employee as the default user-role for the 802.1X authentication method in the aaa
profile. When testing the setup he realizes the client gets the guest role.
What is the reason corp-employee user role was not assigned?
- A. The administrator forgot to map a dotlx profile to the corp-employee aaa profile.
- B. The administrator forgot to enable PEFNG feature set on the Mobility Master.
- C. MC 1 has not received the configuration from the mobility master yet.
- D. The Mobility Master lacks MM-VA licenses; therefore, it shares partial configuration only.
Answer:
C
Question 12
A company with 535 users deploys an Aruba solution with more than 1000 Aruba APs, two 7220
Mobility Controllers, and a single Mobility Master (MM) virtual appliance at the campus server farm.
The MCs run a HA Fast failover group in dual mode and operate at 50% AP capacity.
If there is an MM or MC failure, the network administrator must ensure that the network is fully
manageable and the MC load does not exceed 80%.
What can the network administrator do to meet these requirements?
- A. Place the APs in the same hierarchy level.
- B. Create a cluster with AP load balancing.
- C. Enable oversubscription in the HA group.
- D. Add an MC and an MM in the server farm.
- E. Add an MM and enable DC redundancy.
- F. Place the APs in two different AP-Groups.
Answer:
E
Question 13
Users run Skype for Business on wireless clients with no WMM support over an Aruba Mobility
Master (MM) - Mobility Controller (MC) based network. When traffic arrives at the wired network, it
does not include either L2 or L3 markings.
Which configuration steps should the network administrator take to classify and mark voice and
video traffic with UCC heuristics mode?
- A. Enable WMM in a VAP profile, and explicitly permit voice and video UDP ports in a firewall policy.
- B. Confirm OpenFlow is enabled in the user role and VAP profile. Then enable WMM in a SSID profile, and explicitly permit voice and video UDP ports in a firewall policy.
- C. Confirm the MC is the Openflow controller of the MMs and Openflow is enabled in VAP and firewall roles. Enable Skype4Business ALG in UCC profiles.
- D. Confirm MM is the Openflow controller of MCs and Openflow is enabled in VAP and firewall roles. Enable Skype4Business ALG in UCC profiles.
Answer:
A
Question 14
A network administrator wants to permit explicit SSH, FTP and HHTP(s) access to servers in the
10.100.20.5 to 10.100.20.31 range, all devices in 10.100.21.0/24 network, and a host with IP address
10.100.22.70. The services must work properly at all times.
Which configuration scripts accomplish this task with the fewer number of lines, while avoiding
access to other devices not included in these ranges? (Choose two.)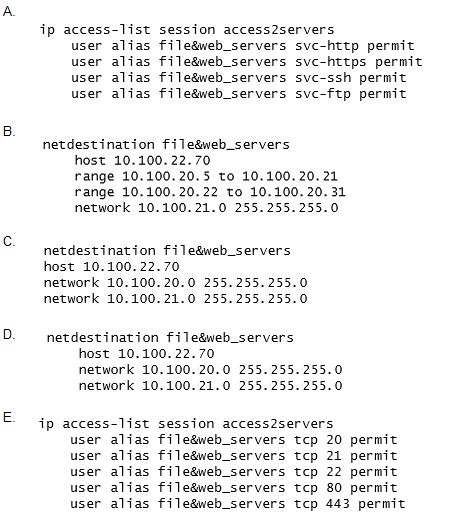
- A. Option A
- B. Option B
- C. Option C
- D. Option D
- E. Option E
Answer:
AB
Question 15
Refer to the exhibits.
Exhibit 1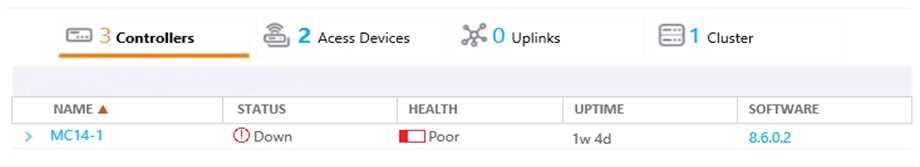
Exhibit 2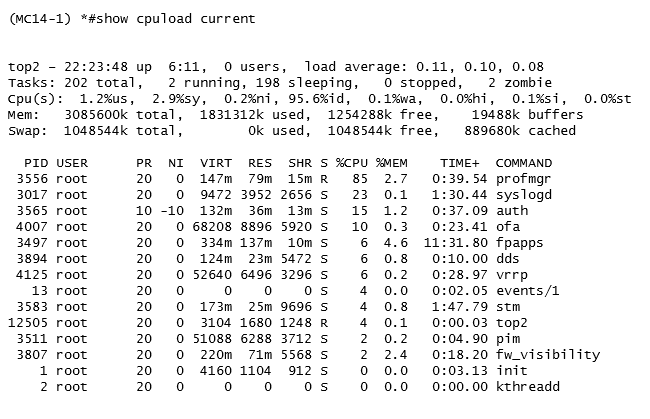
A network administrator adds a new Mobility Controller (MC) to the production Mobility Master
(MM) and deploys APs that start broadcasting the employee SSID in the West wing of the building.
Suddenly, the employees report client disconnects. When accessing the MM the network
administrator notices that the MC is unreachable, then proceeds to access the MCs console and
obtains the outputs shown in the exhibits.
What should the network administrator do next to solve the current problem?
- A. Open a TAC case and send the output of tar crash.
- B. Kill two zombie processes then reboot the MC.
- C. Verify the license pools in the MM.
- D. Decommission the MC from the MM, and add it again.
Answer:
C