HP hpe6-a75 practice test
Aruba Certified Edge Professional Exam
Question 1
A university wants to deploy ClearPass with the Guest module. They have two types of users that
need to use web login authentication. The first type of users are students whose accounts are in an
Active Directory server. The second type of users are friends of students who need to self-register to
access the network.
How should the service be setup in the Policy Manager for this Network?
- A. Guest User Repository and Active Directory server both as authentication sources
- B. Active Directory server as the authentication source, and Guest User Repository as the authorization source
- C. Guest User Repository as the authentication source, and Guest User Repository and Active Directory server as authorization sources
- D. Either the Guest User Repository or Active Directory server should be the single authentication source
- E. Guest User Repository as the authentication source and the Active Directory server as the authorization source
Answer:
A
Question 2
Refer to the exhibit.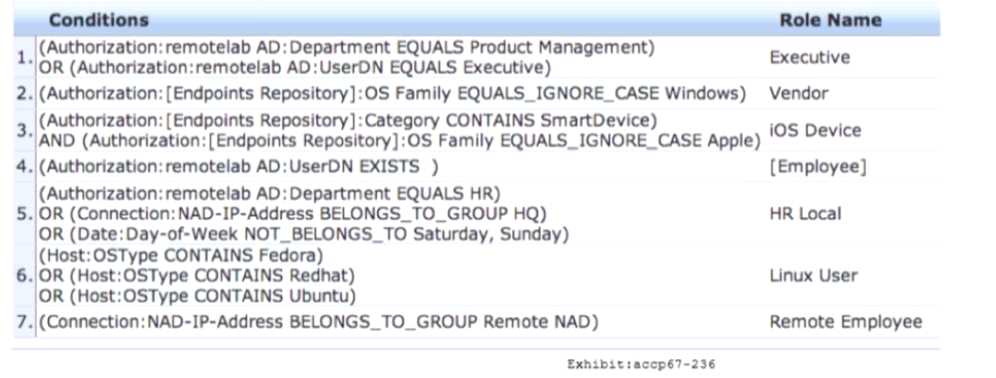
An AD user's department attribute is configured as *HR". The user connects on Monday using their
Windows Laptop to a switch that belongs to the Device Group HQ. Which role is assigned to the user
in ClearPass?
- A. Executive
- B. iOS Device
- C. Vendor
- D. Remote Employee
- E. HR Local
Answer:
D,E
Question 3
When is it necessary to use an SNMP based Enforcement profile to send a VIAN?
- A. When we have to assign a vlan to a wired user on a third party wired switch that doesn't support RADIUS return attributes.
- B. When we have to assign a VLAN to a wired user on an Aruba Mobility Access Switch.
- C. When we have to assign a VIAN to a wired user on an Aruba Mobility Controller.
- D. When we have to assign a VLAN to a wired user on a third party wired switch that doesn't support RADIUS authentication.
- E. When we have to assign a VLAN to a wireless user on an Aruba Mobility Controller.
Answer:
B
Question 4
Refer to the exhibit.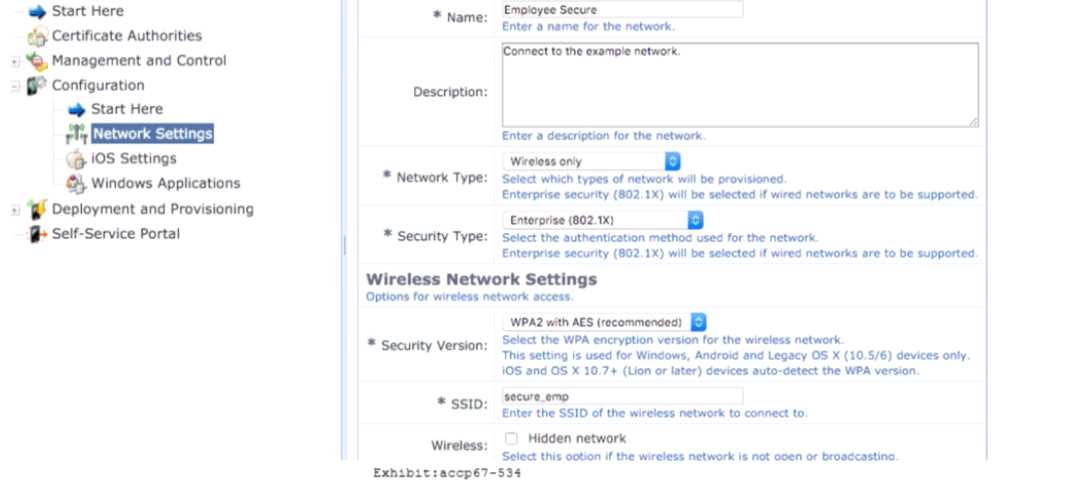
Which statements accurately describe the status of the Onboarded devices in the configuration tor
the network settings shown? (Select two.)
- A. They will connect to Employee_Secure SSID after provisioning.
- B. They will connect to Employee_Secure SSID for provisioning their devices.
- C. They will use WPA2-PSK with AES when connecting to the SSID.
- D. They will connect to secure_emp SSID after provisioning.
- E. They will perform 802.1X authentication when connecting to the SSID.
Answer:
D,E
Question 5
What are Operator Profiles used for?
- A. to enforce role based access control for Aruba Controllers
- B. to enforce role based access control for ClearPass Policy Manager admin users
- C. to enforce role based access control for ClearPass Guest Admin users
- D. to assign ClearPass roles to guest users
- E. to map AD attributes to admin privilege levels in ClearPass Guest
Answer:
C
Question 6
Refer to the exhibit.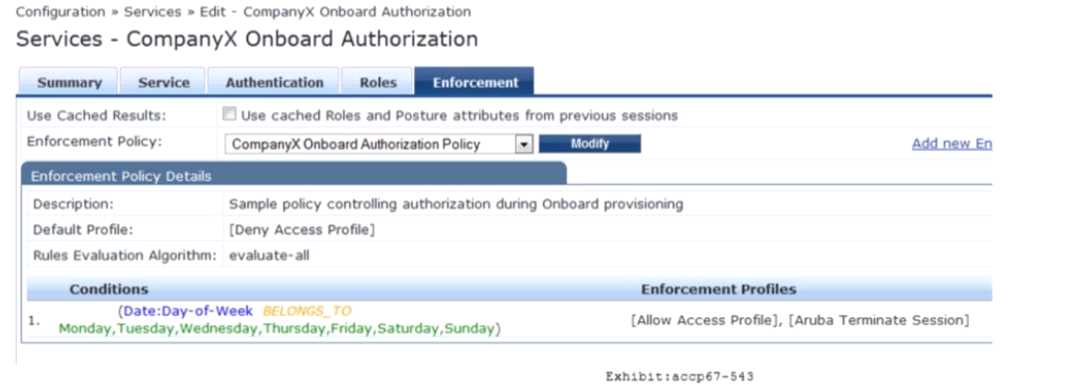
Based on the configuration of the Enforcement Profiles In the Onboard Authorization service shown,
which Onboarding action will occur?
- A. The device will be disconnected from the network after Onboarding so that an EAP-TLS authentication is not performed.
- B. The device will be disconnected from and reconnected to the network after Onboarding is completed.
- C. The device’s onboard authorization request will be denied.
- D. The device will be disconnected after post-Onboarding EAP-TLS authentication, so a second EAP- TLS authentication is performed.
- E. After logging in on the Onboard web login page, the device will be disconnected form and reconnected to the network before Onboard begins.
Answer:
B
Question 7
Which is a valid policy simulation types in ClearPass? (Select three.)
- A. Enforcement Policy
- B. Posture token derivation
- C. Role Mapping
- D. Endpoint Profiler
- E. Chained simulation
Answer:
ACE
Question 8
Refer to the exhibit.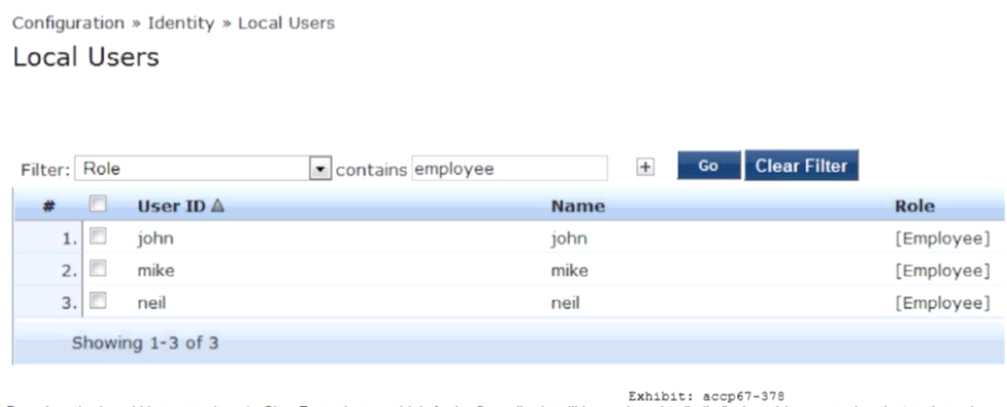
- A. mike
- B. We can't know this from the screenshot above.
- C. Employee
- D. john
Answer:
B
Question 9
Why is a terminate session enforcement profile used during posture checks with 802.1 x
authentication?
- A. To send a RADIUS CoA message from the ClearPass server to the client
- B. To disconnect the user for 30 seconds when they are in an unhealthy posture state
- C. To blacklist the user when they are in an unhealthy posture state
- D. To force the user to re-authenticate and run through the service flow again
- E. To remediate the client applications and firewall do that updates can be installed
Answer:
A
Question 10
Which statement is true about the databases in ClearPass?
- A. Entries in the guest user database do not expire.
- B. A Static host list can only contain a list of IP addresses.
- C. Entries in the guest user database can be deleted.
- D. Entries in the local user database cannot be modified.
- E. The endpoints database can only be populated by manually adding MAC addresses to the table.
Answer:
A
Question 11
Refer to the exhibit.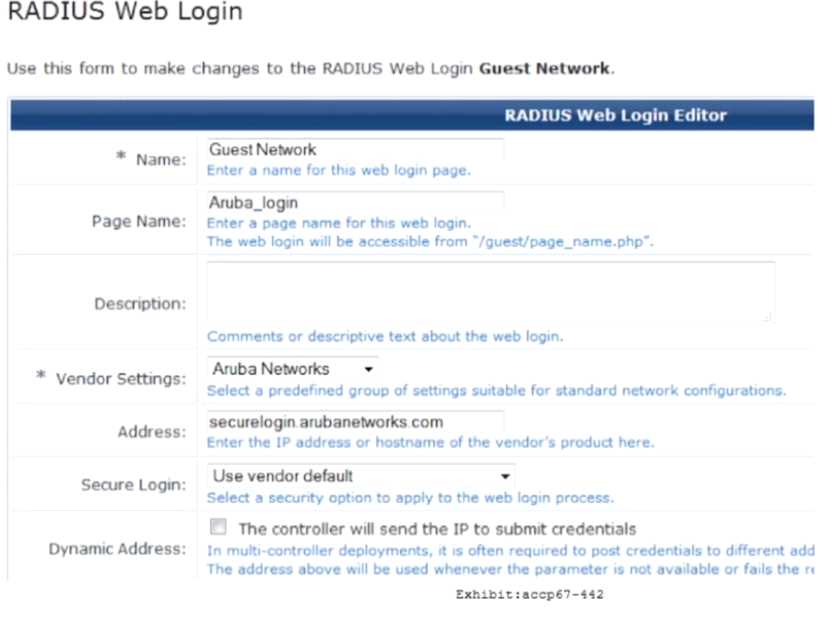
When configuring a Web Login Page in ClearPass Guest, the information shown is displayed. What is
the Address field value 'securelogin.arubanetworks.com' used for?
- A. for ClearPass to send a TACACS+ request to the NAD
- B. for appending to the Web Login URL, before the page name
- C. for the client to POST the user credentials to the NAD
- D. for ClearPass to send a RADIUS request to the NAD
- E. for appending to the Web Login URL, after the page name.
Answer:
C
Question 12
Refer to the exhibit.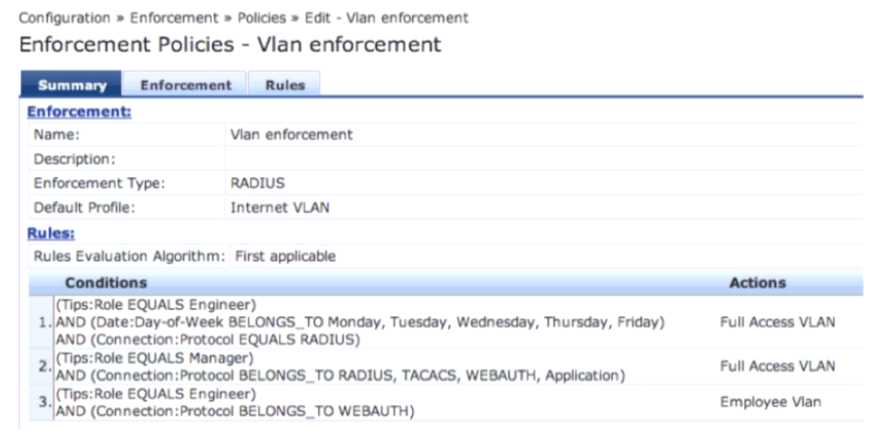
Based on the Policy configuration shown, which VLAN will be assigned when a user with ClearPass
role Engineer authenticates to the network successfully on Saturday using connection protocol
WEBAUTH?
- A. Deny Access
- B. Employee VLAN
- C. Internet VLAN
- D. Full Access VLAN
Answer:
B
Question 13
Refer to the exhibit.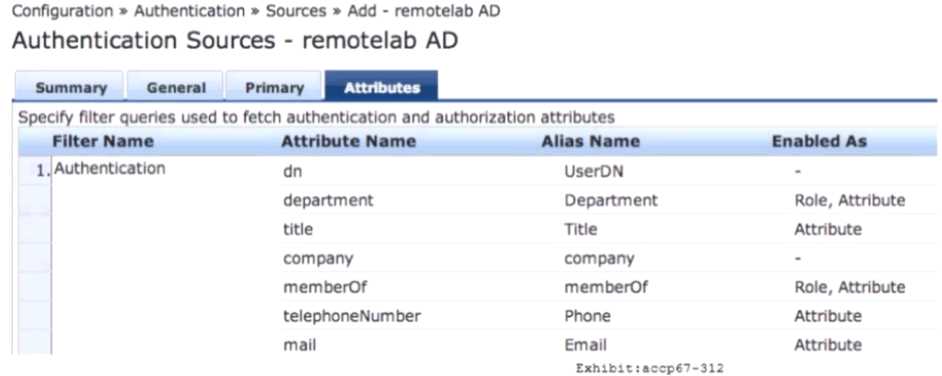
Based on the Attribute configuration shown, which statement accurately describes the status of
attribute values?
- A. Only the attribute values of department and memberOf can be used in role mapping policies.
- B. The attribute values of department, title, memberOf, telephoneNumber, and mail are directly applied as ClearPass.
- C. Only the attribute value of company can be used in role mapping policies, not the other attributes.
- D. The attribute values of department and memberOf are directly applied as ClearPass roles.
- E. Only the attribute values of title, telephoneNumber, and mail can be used in role mapping policies.
Answer:
D
Question 14
A customer wants to implement Virtual IP redundancy, such that in case of a ClearPass server
outage, 802.1x authentications will not be interrupted. The administrator has enabled a single
Virtual IP address on two ClearPass servers.
Which statements accurately describe next steps? (Select two.)
- A. The NAD should be configured with the primary node IP address for RADIUS authentication on the 802.1x network.
- B. A new Virtual IP address should be created for each NAD.
- C. Both the primary and secondary nodes will respond to authentication requests sent to the Virtual IP address when the primary node is active.
- D. The primary node will respond to authentication requests sent to the Virtual IP address when the primary node is active.
- E. The NAD should be configured with the Virtual IP address for RADIUS authentications on the 802.1x network.
Answer:
D,E
Question 15
Which statement is true about the Endpoint Profiler? (Select two.)
- A. The Endpoint Profiler uses DHCP fingerprinting for device categorization.
- B. Data obtained from the Endpoint Profiler can be used in Enforcement Policy.
- C. Endpoint Profiler requires a profiling license.
- D. The Endpoint Profiler requires the Onboard license to be enabled.
- E. The Endpoint Profiler can only categorize laptops and desktops.
Answer:
AB