HP hpe6-a68 practice test
Aruba Certified Clearpass Professional 6.7 Exam
Question 1
What does the Posture Token QUARANTINE imply?
- A. The client is compliant. However, there is an update available to remediate the client to HEALTHY state.
- B. The posture of the client is unknown.
- C. The client is infected and is a threat to other systems in the network.
- D. The client is out of compliance, but has HEALTHY state.
- E. The client is out of compliance.
Answer:
E
Question 2
During a web login authentication, what is expected to happen as part of the Automated NAS login?
- A. NAD sends TACACS+ request to ClearPass.
- B. ClearPass sends TACACS+ request to NAD.
- C. Client device sends RADIUS request to NAD.
- D. NAD sends RADIUS request to ClearPass.
- E. ClearPass sends RADIUS request to NAD.
Answer:
D
Question 3
Which statement is true about the configuration of a generic LDAP server as an External
Authentication server in ClearPass? (Choose three.)
- A. Generic LDAP Browser can be used to search the Base DN.
- B. An administrator can customize the selection of attributes fetched from an LDAP server.
- C. The bind DN can be in the administrator@domain format.
- D. A maximum of one generic LDAP server can be configured in ClearPass.
- E. A LDAP Browser can be used to search the Base DN.
Answer:
A,B,E
Question 4
Refer to the exhibit.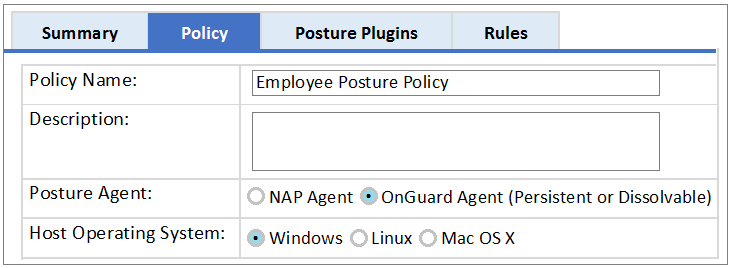
Based on the Posture Policy configuration shown, above, which statement is true?
- A. This Posture Policy can only be applied to an 802.1x wired service not 802.1x wireless.
- B. This Posture Policy checks the health status of devices running Windows, Linux and Mac OS X.
- C. This Posture Policy can use either the persistent or dissolvable Onguard agent to obtain the statement of health.
- D. This Posture Policy checks for presence of a firewall application in Windows devices.
- E. This Posture Policy checks with a Windows NPS server for posture tokens.
Answer:
C
Question 5
Exhibit: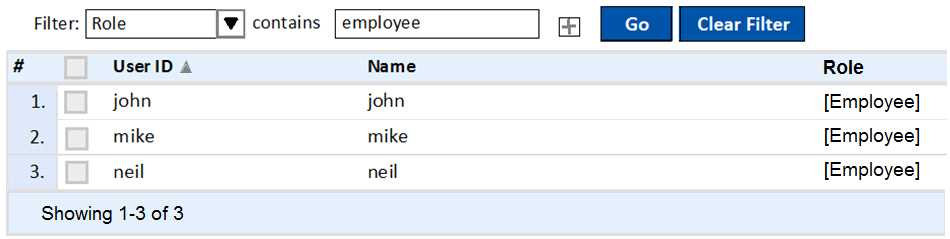
Based on the Local User repository in ClearPass shown, which Aruba firewall role will be assigned to
mike when this user authenticates Aruba Controller?
- A. We can’t know this from the screenshot above.
- B. mike
- C. Employee
- D. john
Answer:
A
Question 6
Refer to the exhibit.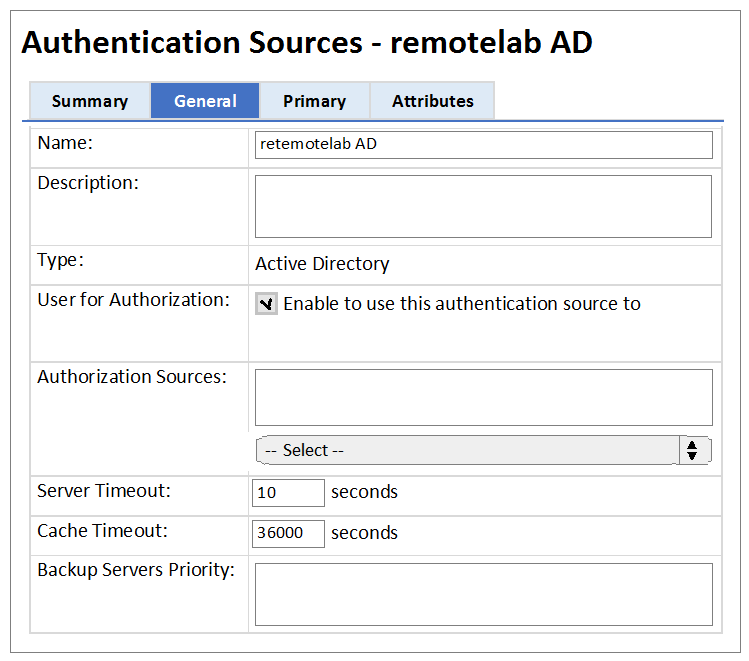
What does the Cache Timeout Value refer to?
- A. The amount of time the Policy Manager caches the user credentials stored in the Active Directory.
- B. The amount of time the Policy Manager waits for a response from the Active Directory before checking the backup authentication source.
- C. The amount of time the Policy Manager caches the user attributes fetched from Active Directory.
- D. The amount of time the Policy Manager waits for response from the Active Directory before sending a timeout message to the Network Access Device.
- E. The amount of time the Policy Manager caches the user\s client certificate.
Answer:
C
Question 7
Which statement is true? (Choose two.)
- A. Mobile device Management is the result of Onboarding.
- B. Third party Mobile Device Management solutions can be integrated with ClearPass.
- C. Mobile Device Management is the authentication that happens before Onboarding.
- D. Mobile Device Management is an application container that is used to provision work applications.
- E. Mobile Device Management is used to control device functions post-Onboarding.
Answer:
BE
Question 8
Which is a valid policy simul-ation types in ClearPass? (Choose three.)
- A. Enforcement Policy
- B. Posture token derivation
- C. Role Mapping
- D. Endpoint Profiler
- E. Chained simulation
Answer:
ACE
Question 9
Which statement is true about the databases in ClearPass?
- A. Entries in the guest user database do not expire.
- B. A Static host list can only contain a list of IP addresses.
- C. Entries in the guest user database can be deleted.
- D. Entries in the local user database cannot be modified.
- E. The endpoints database can only be populated by manually adding MAC addresses to the table.
Answer:
A
Question 10
A bank would like to deploy ClearPass Guest with web login authentication so that their customers
can selfregister on the network to get network access when they have meetings with bank
employees. However, theyre concerned about security.
What is true? (Choose three.)
- A. If HTTPS is used for the web login page, after authentication is completed guest Internet traffic will all be encrypted as well.
- B. During web login authentication, if HTTPS is used for the web login page, guest credentials will be encrypted.
- C. After authentication, an IPSEC VPN on the guest’s client be used to encrypt Internet traffic.
- D. HTTPS should never be used for Web Login Page authentication.
- E. If HTTPS is used for the web login page, after authentication is completed some guest Internet traffic may be unencrypted.
Answer:
BCE
Question 11
Refer to the exhibit.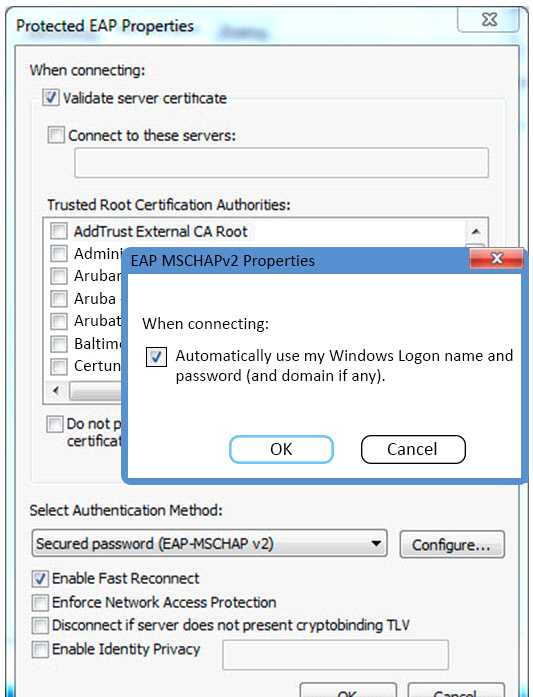
Based on the configuration of a Windows 802.1X supplicant shown, what will be the outcome when
Automatically use my Windows logon name and password are selected?
- A. The client will use machine authentication.
- B. The clients Windows login username and password will be sent inside a certificate to the Active Directory server.
- C. The client’s Windows login username and password will be sent to the Authentication server.
- D. The client will need to re-authenticate every time they connect to the network.
- E. The client will prompt the user to enter the logon username and password.
Answer:
C
Question 12
What is the purpose of ClearPass Onboard?
- A. to provide MAC authentication for devices that don’t support 802.1x
- B. to run health checks on end user devices
- C. to provision personal devices to securely connect to the network
- D. to configure self-registration pages for guest users
- E. to provide guest access for visitors to connect to the network
Answer:
C
Question 13
Refer to the exhibit.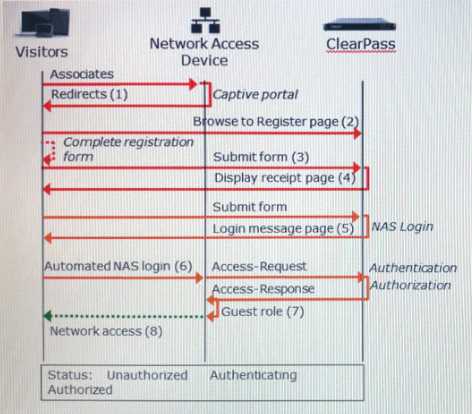
Based on the guest Self-Registration with Sponsor Approval workflow shown, at which stage does the
sponsor approve the users request?
- A. After the RADIUS Access-Request
- B. After the NAS login, but before the RADIUS Access-Request
- C. Before the user can submit the registration form
- D. After the RADIUS Access-Response
- E. After the receipt page is displayed, before the NAS login
Answer:
E
Question 14
Use this form to make changes to the RADIUS Web Login Guest Network.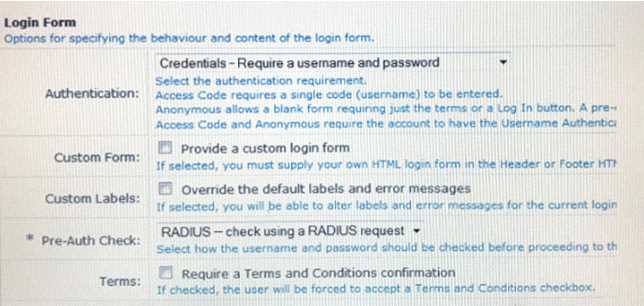
A Web Login page is configured in Clear Pass Guest as shown.
What is the purpose of the Pre-Auth Check?
- A. To authenticate users after the NAD sends an authentication request to ClerPass
- B. To authenticate users before the client sends the credentials to the NAD
- C. To authenticate users when they are roaming from one NAD to another
- D. To authenticate users before they launch the Web Login Page
- E. To replace the need for the NAD to send an authentication request to ClearPass
Answer:
B
Question 15
Refer to the exhibit.
An Enforcement Profile has been created in the Policy Manager as shown.
Which action will ClearPass take based on the Enforcement Profile?
- A. It will send the Session-Timeout attribute in the RADIUS Access-Request packet to the NAD and the NAD will end the users session after 600 seconds.
- B. It will send the Session-Timeout attribute in the RADIUS Access-Accept packet to the User and the users session will be terminated after 600 seconds.
- C. It will count down 600 seconds and send a RADUIS CoA message to the NAD to end the users session after this time is up.
- D. It will count down 600 seconds and send a RADUIUS CoA message to the user to end the users session after this time is up.
- E. It will send the session –Timeout attribute in the RADIUS Access-Accept packet to the NAD and the NAD will end the user’s session after 600 seconds.
Answer:
E