HashiCorp terraform associate 003 practice test
HashiCorp Certified: Terraform Associate (003)
Question 1
Module version is required to reference a module on the Terraform Module Registry.
- A. True
- B. False
Answer:
B
Explanation:
Module version is optional to reference a module on the Terraform Module Registry. If you omit the
version constraint, Terraform will automatically use the latest available version of the module
Question 2
You ate creating a Terraform configuration which needs to make use of multiple providers, one for
AWS and one for Datadog. Which of the following provider blocks would allow you to do this?
A)
B)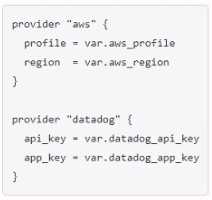
C)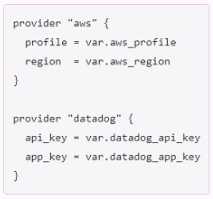
D)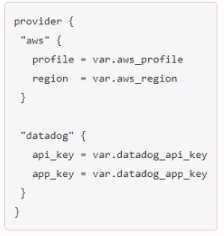
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
C
Explanation:
Option C is the correct way to configure multiple providers in a Terraform configuration. Each
provider block must have a name attribute that specifies which provider it configures2. The other
options are either missing the name attribute or using an invalid syntax.
Question 3
terraform validate confirms that your infrastructure matches the Terraform state file.
- A. True
- B. False
Answer:
B
Explanation:
terraform validate does not confirm that your infrastructure matches the Terraform state file. It only
checks whether the configuration files in a directory are syntactically valid and internally consistent3.
To confirm that your infrastructure matches the Terraform state file, you need to use terraform plan
or terraform apply with the -refresh-only option.
Question 4
Which command must you first run before performing further Terraform operations in a working
directory?
- A. terraform import
- B. terraform workspace
- C. terraform plan
- D. terraform init
Answer:
D
Explanation:
terraform init is the first command that should be run after writing a new Terraform configuration or
cloning an existing one from version control. It initializes a working directory containing Terraform
configuration files and downloads any required providers and modules. The other commands are
used for different purposes, such as importing existing resources, switching between workspaces,
generating execution plans, etc.
Question 5
A developer accidentally launched a VM (virtual machine) outside of the Terraform workflow and
ended up with two servers with the same name. They don't know which VM Terraform manages but
do have a list of all active VM IDs.
Which of the following methods could you use to discover which instance Terraform manages?
- A. Run terraform state list to find the names of all VMs, then run terraform state show for each of them to find which VM ID Terraform manages
- B. Update the code to include outputs for the ID of all VMs, then run terraform plan to view the outputs
- C. Run terraform taint/code on all the VMs to recreate them
- D. Use terraform refresh/code to find out which IDs are already part of state
Answer:
A
Explanation:
The terraform state list command lists all resources that are managed by Terraform in the current
state file1. The terraform state show command shows the attributes of a single resource in the state
file2. By using these two commands, you can compare the VM IDs in your list with the ones in the
state file and identify which one is managed by Terraform.
Question 6
When does Sentinel enforce policy logic during a Terraform Cloud run?
- A. Before the plan phase
- B. During the plan phase
- C. Before the apply phase
- D. After the apply phase
Answer:
C
Explanation:
Sentinel policies are checked after the plan stage of a Terraform run, but before it can be confirmed
or the terraform apply is executed3. This allows you to enforce rules on your infrastructure before it
is created or modified.
Question 7
You have provisioned some virtual machines (VMs) on Google Cloud Platform (GCP) using the gcloud
command line tool. However, you are standardizing with Terraform and want to manage these VMs
using Terraform instead. What are the two things you must do to achieve this? Choose two correct
answers.
- A. Run the terraform Import-gcp command
- B. Write Terraform configuration for the existing VMs
- C. Use the terraform import command for the existing VMs
- D. Provision new VMs using Terraform with the same VM names
Answer:
B,C
Explanation:
To import existing resources into Terraform, you need to do two things1:
Write a resource configuration block for each resource, matching the type and name used in your
state file.
Run terraform import for each resource, specifying its address and ID. There is no such command as
terraform Import-gcp, and provisioning new VMs with the same names will not import them into
Terraform.
Question 8
Which of the following ate advantages of using infrastructure as code (laC) instead of provisioning
with a graphical user interface (GUI)? Choose two correct answers.
- A. Lets you version, reuse, and share infrastructure configuration
- B. Provisions the same resources at a lower cost
- C. Secures your credentials
- D. Reduces risk of operator error
- E. Prevents manual modifications to your resources
Answer:
A,D
Explanation:
It lets you version, reuse, and share infrastructure configuration as code files, which can be stored in
a source control system and integrated with your CI/CD pipeline.
It reduces risk of operator error by automating repetitive tasks and ensuring consistency across
environments. IaC does not necessarily provision resources at a lower cost, secure your credentials,
or prevent manual modifications to your resources - these depend on other factors such as your
cloud provider, your security practices, and your access policies.
Question 9
Outside of the required_providers block, Terraform configurations always refer to providers by their
local names.
- A. True
- B. False
Answer:
B
Explanation:
Outside of the required_providers block, Terraform configurations can refer to providers by either
their local names or their source addresses. The local name is a short name that can be used
throughout the configuration, while the source address is a global identifier for the provider in the
format registry.terraform.io/namespace/type. For example, you can use either aws or
registry.terraform.io/hashicorp/aws to refer to the AWS provider.
Question 10
Terraform providers are always installed from the Internet.
- A. True
- B. False
Answer:
B
Explanation:
Terraform providers are not always installed from the Internet. There are other ways to install
provider plugins, such as from a local mirror or cache, from a local filesystem directory, or from a
network filesystem. These methods can be useful for offline or air-gapped environments, or for
customizing the installation process. You can configure the provider installation methods using the
provider_installation block in the CLI configuration file.
Question 11
What feature stops multiple users from operating on the Terraform state at the same time?
- A. State locking
- B. Version control
- C. Provider constraints
- D. Remote backends
Answer:
A
Explanation:
State locking prevents other users from modifying the state file while a Terraform operation is in
progress. This prevents conflicts and data loss1.
Question 12
Which of the following is not a valid string function in Terraform?
- A. chomp
- B. join
- C. slice
- D. split
Answer:
C
Explanation:
Referencing Terraform Built-in Functions:
✅
chomp: removes trailing newlines
✅
join: combines list into string
✅
split: splits string into list
❌
slice:is nota valid Terraform string function (it's used in other languages like Python)
Question 13
What does the default "local" Terraform backend store?
- A. tfplan files
- B. State file
- C. Provider plugins
- D. Terraform binary
Answer:
B
Explanation:
The default “local” Terraform backend stores the state file in a local file named terraform.tfstate,
which can be used to track and manage the state of your infrastructure3.
Question 14
How can you trigger a run in a Terraform Cloud workspace that is connected to a Version Control
System (VCS) repository?
- A. Only Terraform Cloud organization owners can set workspace variables on VCS connected workspaces
- B. Commit a change to the VCS working directory and branch that the Terraform Cloud workspace is connected to
- C. Only Terraform Cloud organization owners can approve plans in VCS connected workspaces
- D. Only members of a VCS organization can open a pull request against repositories that are connected to Terraform Cloud workspaces
Answer:
B
Explanation:
This will trigger a run in the Terraform Cloud workspace, which will perform a plan and apply
operation on the infrastructure defined by the Terraform configuration files in the VCS repository.
Question 15
You're building a CI/CD (continuous integration/continuous delivery) pipeline and need to inject
sensitive variables into your Terraform run. How can you do this safely?
- A. Copy the sensitive variables into your Terraform code
- B. Store the sensitive variables in a secure_varS.tf file
- C. Store the sensitive variables as plain text in a source code repository
- D. Pass variables to Terraform with a -var flag
Answer:
D
Explanation:
This is a secure way to inject sensitive variables into your Terraform run, as they will not be stored in
any file or source code repository. You can also use environment variables or variable files with
encryption to pass sensitive variables to Terraform.