google professional cloud developer practice test
Professional Cloud Developer
Question 1
Your application takes an input from a user and publishes it to the user's contacts. This input is stored in a table in Cloud
Spanner. Your application is more sensitive to latency and less sensitive to consistency.
How should you perform reads from Cloud Spanner for this application?
- A. Perform Read-Only transactions.
- B. Perform stale reads using single-read methods.
- C. Perform strong reads using single-read methods.
- D. Perform stale reads using read-write transactions.
Answer:
D
Explanation:
Reference: https://cloud.google.com/solutions/best-practices-cloud-spanner-gaming-database
Question 2
Your API backend is running on multiple cloud providers. You want to generate reports for the network latency of your API.
Which two steps should you take? (Choose two.)
- A. Use Zipkin collector to gather data.
- B. Use Fluentd agent to gather data.
- C. Use Stackdriver Trace to generate reports.
- D. Use Stackdriver Debugger to generate report.
- E. Use Stackdriver Profiler to generate report.
Answer:
C E
Question 3
You are a SaaS provider deploying dedicated blogging software to customers in your Google Kubernetes Engine (GKE)
cluster. You want to configure a secure multi-tenant platform to ensure that each customer has access to only their own blog
and cant affect the workloads of other customers. What should you do?
- A. Enable Application-layer Secrets on the GKE cluster to protect the cluster.
- B. Deploy a namespace per tenant and use Network Policies in each blog deployment.
- C. Use GKE Audit Logging to identify malicious containers and delete them on discovery.
- D. Build a custom image of the blogging software and use Binary Authorization to prevent untrusted image deployments.
Answer:
B
Explanation:
Reference: https://cloud.google.com/kubernetes-engine/docs/concepts/multitenancy-overview
Question 4
Your website is deployed on Compute Engine. Your marketing team wants to test conversion rates between 3 different
website designs.
Which approach should you use?
- A. Deploy the website on App Engine and use traffic splitting.
- B. Deploy the website on App Engine as three separate services.
- C. Deploy the website on Cloud Functions and use traffic splitting.
- D. Deploy the website on Cloud Functions as three separate functions.
Answer:
A
Explanation:
Reference: https://cloud.google.com/appengine/docs/standard/python/splitting-traffic
Question 5
You are planning to migrate a MySQL database to the managed Cloud SQL database for Google Cloud. You have Compute
Engine virtual machine instances that will connect with this Cloud SQL instance. You do not want to whitelist IPs for the
Compute Engine instances to be able to access Cloud SQL.
What should you do?
- A. Enable private IP for the Cloud SQL instance.
- B. Whitelist a project to access Cloud SQL, and add Compute Engine instances in the whitelisted project.
- C. Create a role in Cloud SQL that allows access to the database from external instances, and assign the Compute Engine instances to that role.
- D. Create a CloudSQL instance on one project. Create Compute engine instances in a different project. Create a VPN between these two projects to allow internal access to CloudSQL.
Answer:
C
Explanation:
Reference: https://cloud.google.com/sql/docs/mysql/connect-external-app
Question 6
You are developing an ecommerce application that stores customer, order, and inventory data as relational tables inside
Cloud Spanner. During a recent load test, you discover that Spanner performance is not scaling linearly as expected. Which
of the following is the cause?
- A. The use of 64-bit numeric types for 32-bit numbers.
- B. The use of the STRING data type for arbitrary-precision values.
- C. The use of Version 1 UUIDs as primary keys that increase monotonically.
- D. The use of LIKE instead of STARTS_WITH keyword for parameterized SQL queries.
Answer:
B
Question 7
You support an application that uses the Cloud Storage API. You review the logs and discover multiple HTTP 503 Service
Unavailable error responses from the API. Your application logs the error and does not take any further action. You want to
implement Google-recommended retry logic to improve success rates. Which approach should you take?
- A. Retry the failures in batch after a set number of failures is logged.
- B. Retry each failure at a set time interval up to a maximum number of times.
- C. Retry each failure at increasing time intervals up to a maximum number of tries.
- D. Retry each failure at decreasing time intervals up to a maximum number of tries.
Answer:
C
Question 8
You are using Cloud Build build to promote a Docker image to Development, Test, and Production environments. You need
to ensure that the same Docker image is deployed to each of these environments.
How should you identify the Docker image in your build?
- A. Use the latest Docker image tag.
- B. Use a unique Docker image name.
- C. Use the digest of the Docker image.
- D. Use a semantic version Docker image tag.
Answer:
D
Question 9
You are designing a schema for a Cloud Spanner customer database. You want to store a phone number array field in a
customer table. You also want to allow users to search customers by phone number.
How should you design this schema?
- A. Create a table named Customers. Add an Array field in a table that will hold phone numbers for the customer.
- B. Create a table named Customers. Create a table named Phones. Add a CustomerId field in the Phones table to find the CustomerId from a phone number.
- C. Create a table named Customers. Add an Array field in a table that will hold phone numbers for the customer. Create a secondary index on the Array field.
- D. Create a table named Customers as a parent table. Create a table named Phones, and interleave this table into the Customer table. Create an index on the phone number field in the Phones table.
Answer:
C
Question 10
You recently developed a new service on Cloud Run. The new service authenticates using a custom service and then writes
transactional information to a Cloud Spanner database. You need to verify that your application can support up to 5,000 read
and 1,000 write transactions per second while identifying any bottlenecks that occur. Your test infrastructure must be able to
autoscale. What should you do?
- A. Build a test harness to generate requests and deploy it to Cloud Run. Analyze the VPC Flow Logs using Cloud Logging.
- B. Create a Google Kubernetes Engine cluster running the Locust or JMeter images to dynamically generate load tests. Analyze the results using Cloud Trace.
- C. Create a Cloud Task to generate a test load. Use Cloud Scheduler to run 60,000 Cloud Task transactions per minute for 10 minutes. Analyze the results using Cloud Monitoring.
- D. Create a Compute Engine instance that uses a LAMP stack image from the Marketplace, and use Apache Bench to generate load tests against the service. Analyze the results using Cloud Trace.
Answer:
B
Question 11
Your teammate has asked you to review the code below. Its purpose is to efficiently add a large number of small rows to a
BigQuery table.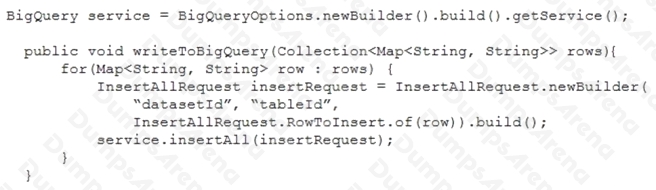
Which improvement should you suggest your teammate make?
- A. Include multiple rows with each request.
- B. Perform the inserts in parallel by creating multiple threads.
- C. Write each row to a Cloud Storage object, then load into BigQuery.
- D. Write each row to a Cloud Storage object in parallel, then load into BigQuery.
Answer:
B
Question 12
You have two tables in an ANSI-SQL compliant database with identical columns that you need to quickly combine into a
single table, removing duplicate rows from the result set.
What should you do?
- A. Use the JOIN operator in SQL to combine the tables.
- B. Use nested WITH statements to combine the tables.
- C. Use the UNION operator in SQL to combine the tables.
- D. Use the UNION ALL operator in SQL to combine the tables.
Answer:
C
Explanation:
Reference: https://www.techonthenet.com/sql/union_all.php
Question 13
You are developing a corporate tool on Compute Engine for the finance department, which needs to authenticate users and
verify that they are in the finance department. All company employees use G Suite.
What should you do?
- A. Enable Cloud Identity-Aware Proxy on the HTTP(s) load balancer and restrict access to a Google Group containing users in the finance department. Verify the provided JSON Web Token within the application.
- B. Enable Cloud Identity-Aware Proxy on the HTTP(s) load balancer and restrict access to a Google Group containing users in the finance department. Issue client-side certificates to everybody in the finance team and verify the certificates in the application.
- C. Configure Cloud Armor Security Policies to restrict access to only corporate IP address ranges. Verify the provided JSON Web Token within the application.
- D. Configure Cloud Armor Security Policies to restrict access to only corporate IP address ranges. Issue client side certificates to everybody in the finance team and verify the certificates in the application.
Answer:
C
Question 14
Your application is deployed in a Google Kubernetes Engine (GKE) cluster. When a new version of your application is
released, your CI/CD tool updates the spec.template.spec.containers[0].image value to reference the Docker image of your
new application version. When the Deployment object applies the change, you want to deploy at least 1 replica of the new
version and maintain the previous replicas until the new replica is healthy.
Which change should you make to the GKE Deployment object shown below?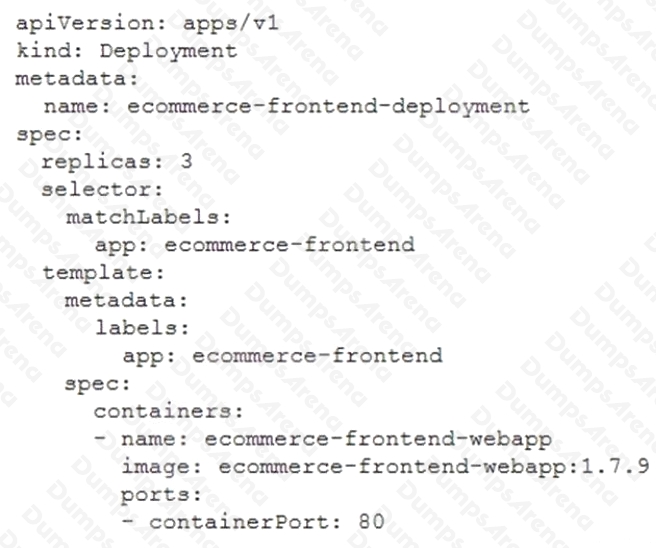
- A. Set the Deployment strategy to RollingUpdate with maxSurge set to 0, maxUnavailable set to 1.
- B. Set the Deployment strategy to RollingUpdate with maxSurge set to 1, maxUnavailable set to 0.
- C. Set the Deployment strategy to Recreate with maxSurge set to 0, maxUnavailable set to 1.
- D. Set the Deployment strategy to Recreate with maxSurge set to 1, maxUnavailable set to 0.
Answer:
D
Question 15
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete
each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure
that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study.
Case studies might contain exhibits and other resources that provide more information about the scenario that is described
in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make
changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of
the case study before you answer the questions. Clicking these buttons displays information such as business requirements,
existing environment, and problem statements. If the case study has an All Information tab, note that the information
displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click
the Question button to return to the question.
Company Overview
HipLocal is a community application designed to facilitate communication between people in close proximity. It is used for
event planning and organizing sporting events, and for businesses to connect with their local communities. HipLocal
launched recently in a few neighborhoods in Dallas and is rapidly growing into a global phenomenon. Its unique style of
hyper-local community communication and business outreach is in demand around the world.
Executive Statement
We are the number one local community app; it's time to take our local community services global. Our venture capital
investors want to see rapid growth and the same great experience for new local and virtual communities that come online,
whether their members are 10 or 10000 miles away from each other.
Solution Concept
HipLocal wants to expand their existing service, with updated functionality, in new regions to better serve their global
customers. They want to hire and train a new team to support these regions in their time zones. They will need to ensure that
the application scales smoothly and provides clear uptime data.
Existing Technical Environment
HipLocal's environment is a mix of on-premises hardware and infrastructure running in Google Cloud Platform. The HipLocal
team understands their application well, but has limited experience in global scale applications. Their existing technical
environment is as follows:
Existing APIs run on Compute Engine virtual machine instances hosted in GCP.
State is stored in a single instance MySQL database in GCP.
Data is exported to an on-premises Teradata/Vertica data warehouse.
Data analytics is performed in an on-premises Hadoop environment.
The application has no logging.
There are basic indicators of uptime; alerts are frequently fired when the APIs are unresponsive.
Business Requirements
HipLocal's investors want to expand their footprint and support the increase in demand they are seeing. Their requirements
are:
Expand availability of the application to new regions.
Increase the number of concurrent users that can be supported.
Ensure a consistent experience for users when they travel to different regions.
Obtain user activity metrics to better understand how to monetize their product.
Ensure compliance with regulations in the new regions (for example, GDPR).
Reduce infrastructure management time and cost.
Adopt the Google-recommended practices for cloud computing.
Technical Requirements
The application and backend must provide usage metrics and monitoring.
APIs require strong authentication and authorization.
Logging must be increased, and data should be stored in a cloud analytics platform.
Move to serverless architecture to facilitate elastic scaling.
Provide authorized access to internal apps in a secure manner.
HipLocal's .net-based auth service fails under intermittent load.
What should they do?
- A. Use App Engine for autoscaling.
- B. Use Cloud Functions for autoscaling.
- C. Use a Compute Engine cluster for the service.
- D. Use a dedicated Compute Engine virtual machine instance for the service.
Answer:
D
Explanation:
Reference: https://www.qwiklabs.com/focuses/611?parent=catalog