giac gpen practice test
GIAC Certified Penetration Tester
Question 1
ACME corporation has decided to setup wireless (IEEE 802.11) network in it's sales branch at Tokyo
and found that channels 1, 6, 9,11 are in use by the neighboring offices. Which is the best channel
they can use?
- A. 4
- B. 5
- C. 10
- D. 2
Answer:
D
Question 2
Which Metasploitvncinject stager will allow VNC communications from the attacker to a listening
port of the attacker's choosing on the victim machine?
- A. Vncinject/find.lag
- B. Vncinject/reverse.tcp
- C. Vncinject/reverse-http
- D. Vncinject /bind.tcp
Answer:
B
Explanation:
Reference:
http://www.rapid7.com/db/modules/payload/windows/vncinject/reverse_tcp
Question 3
What is the MOST important document to obtain before beginning any penetration testing?
- A. Project plan
- B. Exceptions document
- C. Project contact list
- D. A written statement of permission
Answer:
A
Explanation:
Reference:
Before starting a penetration test, all targets must be identified. These targets should be obtained
from the customer during the initial questionnaire phase. Targets can be given in the form of specific
IP addresses, network ranges, or domain names by the customer. In some instances, the only target
the customer provides is the name of the organization and expects the testers be able to identify the
rest on their own. It is important to define if systems like firewalls and IDS/IPS or networking
equipment that are between the tester and the final target are also part of the scope. Additional
elements such as upstream providers, and other 3rd party providers should be identified and defined
whether they are in scope or not.
Question 4
While reviewing traffic from a tcpdump capture, you notice the following commands being sent from
a remote system to one of your web servers:
C:\>sc winternet.host.com create ncservicebinpath- "c:\tools\ncexe -I -p 2222 -e cmd.exe"
C:\>sc vJnternet.host.com query ncservice.
What is the intent of the commands?
- A. The first command creates a backdoor shell as a service. It is being started on TCP2222 using cmd.exe. The second command verifies the service is created and itsstatus.
- B. The first command creates a backdoor shell as a service. It is being started on UDP2222 using cmd.exe. The second command verifies the service is created and itsstatus.
- C. This creates a service called ncservice which is linked to the cmd.exe command andits designed to stop any instance of nc.exe being run. The second command verifiesthe service is created and its status.
- D. The first command verifies the service is created and its status. The secondcommand creates a backdoor shell as a service. It is being started on TCP 2222connected to cmd.exe.
Answer:
C
Question 5
Which of the following best describes a client side exploit?
- A. Attack of a client application that retrieves content from the network
- B. Attack that escalates user privileged to root or administrator
- C. Attack of a service listening on a client system
- D. Attack on the physical machine
Answer:
C
Question 6
Which of the following TCP packet sequences are common during a SYN (or half-open) scan?
- A. A,B and C
- B. A and C
- D. C and D
Answer:
C
Question 7
Which of the following describes the direction of the challenges issued when establishing a wireless
(IEEE 802.11) connection?
- A. One-way, the client challenges the access point
- B. One-way, the access point challenges the client
- C. No challenges occur (or wireless connection
- D. Two-way, both the client and the access point challenge each other
Answer:
D
Question 8
You have gained shell on a Windows host and want to find other machines to pivot to, but the rules
of engagement state that you can only use tools that are already available. How could you find other
machines on the target network?
- A. Use the "ping" utility to automatically discover other hosts
- B. Use the "ping" utility in a for loop to sweep the network.
- C. Use the "edit" utility to read the target's HOSTS file.
- D. Use the "net share" utility to see who is connected to local shared drives.
Answer:
B
Explanation:
Reference:
http://www.slashroot.in/what-ping-sweep-and-how-do-ping-sweep
Question 9
A penetration tester obtains telnet access to a target machine using a captured credential. While
trying to transfer her exploit to the target machine, the network intrusion detection systems keeps
detecting her exploit and terminating her connection. Which of the following actions will help the
penetration tester transfer an exploit and compile it in the target system?
- A. Use the http service's PUT command to push the file onto the target machine.
- B. Use the scp service, protocol SSHv2 to pull the file onto the target machine.
- C. Use the telnet service's ECHO option to pull the file onto the target machine
- D. Use the ftp service in passive mode to push the file onto the target machine.
Answer:
D
Question 10
What section of the penetration test or ethical hacking engagement final report is used to detail and
prioritize the results of your testing?
- A. Methodology
- B. Conclusions
- C. Executive Summary
- D. Findings
Answer:
C
Question 11
You are pen testing a Windows system remotely via a raw netcat shell. You want to quickly change
directories to where the Windows operating system resides, what command could you use?
- A. cd systemroot
- B. cd-
- C. cd /systemroot/
- D. cd %systemroot%
Answer:
B
Question 12
A client with 7200 employees in 14 cities (all connected via high speed WAN connections) has
suffered a major external security breach via a desktop which cost them more than SI 72.000 and the
loss of a high profile client. They ask you to perform a desktop vulnerability assessment to identify
everything that needs to be patched. Using Nessus you find tens of thousands of vulnerabilities that
need to be patched. In the report you find workstations running several Windows OS versions and
service pack levels, anti-virus software from multiple vendors several major browser versions and
different versions of Acrobat Reader. Which of the following recommendations should you provide
with the report?
- A. The client should standardize their desktop software
- B. The client should eliminate workstations to reduce workload
- C. The client should hire more people to catch up on patches
- D. The client should perform monthly vulnerability assessments
Answer:
C
Question 13
Which Metasploit payload includes simple upload and download functionality for moving files to and
from compromised systems?
- A. DLL inject
- B. Upexec
- C. Meterpreter
- D. Vncinject
Answer:
D
Explanation:
Reference:
http://www.opensourceforu.com/2011/02/metasploit-meterpreter-payload/
Question 14
A junior penetration tester at your firm is using a non-transparent proxy for the first time to test a
web server. He sees the web site In his browser but nothing shows up In the proxy. He tells you that
he just installed the non-transparent proxy on his computer and didn't change any defaults. After
verifying the proxy is running, you ask him to open up his browser configuration, as shown in the
figure, which of the following recommendations will correctly allow him to use the transparent proxy
with his browser?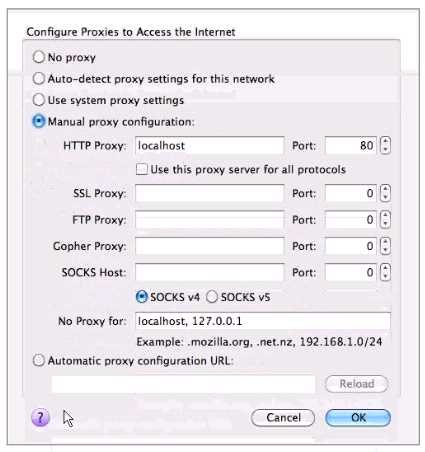
- A. He should change the PORT: value to match the port used by the non-transparentproxy.
- B. He should select the checkbox "use this proxy server for all protocols" for theproxy to function correctly.
- C. He should change the HTTP PROXY value to 127.0.0.1 since the non-transparentproxy is running on the same machine as the browser.
- D. He should select NO PROXY instead of MANUAL PROXY CONFIGURATION as thissetting is only necessary to access the Internet behind protected networks.
Answer:
C
Question 15
Which of the following describe the benefits to a pass-the-hash attack over traditional password
cracking?
- A. No triggering of IDS signatures from the attack privileges at the level of theacquired password hash and no corruption of the LSASS process.
- B. No triggering of IDS signatures from the attack, no account lockout and use ofnative windows file and print sharing tools on the compromised system.
- C. No account lockout, privileges at the level of the acquired password hash and useof native windows file and print Sharif tools on the compromised system.
- D. No account lockout, use of native file and print sharing tools on the compromisedsystem and no corruption of the LSASS process.
Answer:
D