giac gcfr practice test
GIAC Cloud Forensics Responder Exam
Question 1
Below is an extract from a Server Access Log showing a record for a request made to an AWS S3
bucket. What does the first field starting with "385f9e" represent?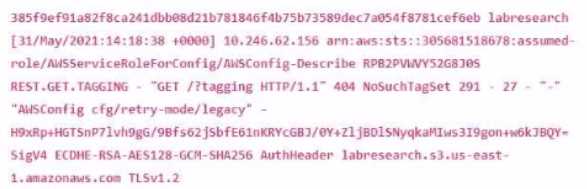
- A. Bucket Owner
- B. Request ID
- C. Host ID
- D. Cipher Suite
Answer:
B
Question 2
Which is the effective access when aws user is assigned to an S3 bucket?
- A. A user must have an employee account
- B. A user must have an account under any AWS account
- C. A user must be under the same AWS account as the S3 bucket
- D. A user must have the AWS IAM role assigned
Answer:
C
Question 3
What logical AWS structure type is used to chain together accounts in a trust relationship which
allows for single sign-on and cross-account management?
- A. Subscription
- B. Organisation
- C. OU
- D. Tenant
Answer:
B
Question 4
An Azure blob is accessed using the link below. What is the name of the blob container?
- A. ex-storage
- B. mov.avi
- C. mymovies
- D. blob.core
Answer:
C
Question 5
In Azure, which of the following describes a "Contributor"?
- A. A collection of permissions such as read, write, and delete
- B. A designation on a PKI certificate
- C. A specification of who can access a resource group
- D. An object representing an entity
Answer:
A
Question 6
What Pub/Sub component is used to forward GCP logs to their final location?
- A. Topic
- B. Log Sink
- C. Publication
- D. Subscription
Answer:
B
Question 7
Which of the following is the smallest unit of computing hardware in Kubernetes?
- A. Cluster
- B. Node
- C. Container
- D. Pod
Answer:
D
Question 8
What is a best practice recommendation when using API keys for AWS access?
- A. Delete the account's default access keys
- B. Define specific role permissions
- C. Enable MFA protection
- D. Configure STS one-time tokens
Answer:
A
Question 9
What would prevent GCP 1AM from linking to Google Workspace to manage users and groups?
- A. A gcp-organization-admins group was not created
- B. The connector was not configured to link the services
- C. Inadequate Identity and Access Management license
- D. Google Workspace cannot be linked to GCP 1AM
Answer:
D
Question 10
What type of AWS log is the following snippet an example of?
- A. Web Application firewall Log
- B. VPC Flow Log
- C. Load Balancer Log
- D. Route 53 Query Log
Answer:
B
Question 11
An investigator confirms that phishing emails sent to users in an organization ate not being sent to
their Gmall Spam folder. What is a possible cause for this?
- A. The default setting for enhanced pre-delivery message scanning was changed
- B. The security sandbox default configuration setting was changed
- C. A third party application needs to be installed to detect phishing emails
- D. Compliance based rules need to be configured to detect phishing emails
Answer:
A
Question 12
How is storage account, cs21003200042c87633, created in an Azure resource group?
- A. PowerShell Cloud Shell audit logging was enabled
- B. A Bash Cloud Shell was used
- C. PowerShelI Cloud Shell was used
- D. Azure CLI was used from a Windows machine
Answer:
B
Question 13
An engineer has set up log forwarding for a new data source and wants to use that data to run
reports and create dashboards in Kiban
a. What needs to be created in order to properly handle these logs?
- A. Row
- B. Parser
- C. ingest script
- D. Beat
Answer:
B
Question 14
At what point of the OAuth delegation process does the Resource Owner approve the scope of access
to be allowed?
- A. After user credentials are accepted by the Authorization Server
- B. Once the OAuth token is accepted by the Application
- C. When the Resource Server receives the OAuth token
- D. Before user credentials are sent to the Authentication Server
Answer:
A
Question 15
Which cloud service provider produces sampled flow logs?
- A. GCP
- B. Azure
- C. AWS
Answer:
A