giac gasf practice test
GIAC Advanced Smartphone Forensics
Question 1
Based on the image below, which file system is being examined?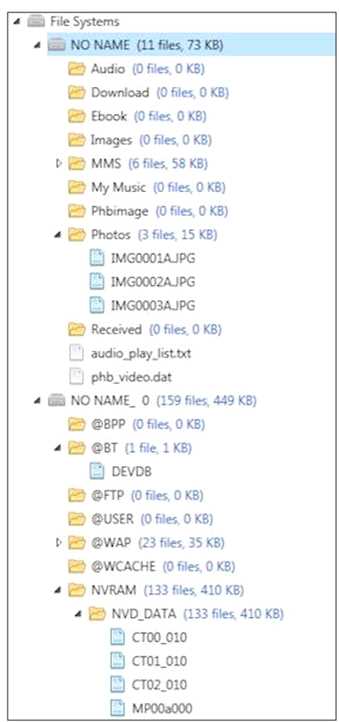
A. Chinese knock-off
B. Windows
C. Android
D. Blackberry
Answer:
A
Explanation
Reference:
https://forums.techguy.org/threads/virus-in-china-mobile.992051/
Question 2
What type of acquisition is being examined in the image below?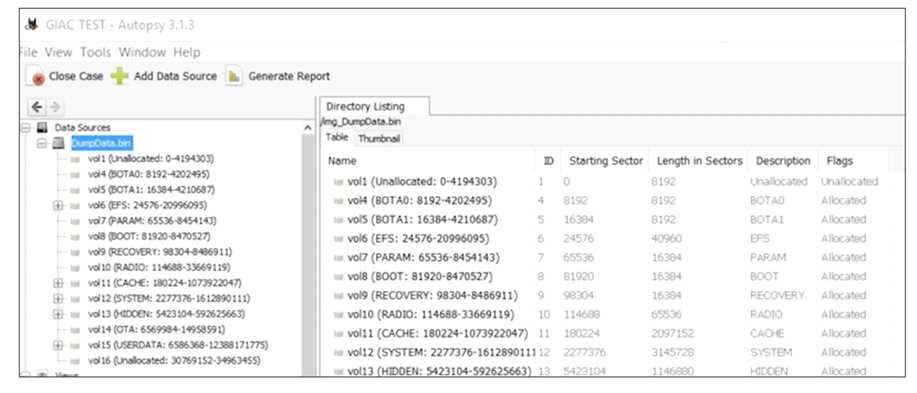
A. iOS bypass lock
B. Blackberry logical
C. Android physical
D. Windows Mobile file system
Answer:
C
Explanation
Reference:
http://www.forensicswiki.org/wiki/How_To_Decrypt_Android_Full_Disk_Encryption
Question 3
Which of the following files contains details regarding the encryption state of an iTunes backup file?
A. Keychain-backup.plist
B. Manifest.mbdb
C. Manifest.plist
D. Status.plist
Answer:
C
Explanation
Explanation: The Manifest.plist lists if the backup is encrypted. This will come into use and be
required should the backup file need to be accessed forensically if it is locked. The Manifest.mbdb
contains a listing of data stored in the backup. Even if the backup is encrypted, this data can be
parsed for more information.
Reference:
http://resources.infosecinstitute.com/ios-5-backups-part-1/#gref
Question 4
In addition to the device passcode, what other essential piece of information is most often required
in order to decrypt the contents of BlackBerry OS 10 handsets?
A. BlackBerry Blend username/pin
B. BlackBerry Balance username/password
C. BlackBerry Link ID/password
D. BBM pin
Answer:
C
Explanation
Explanation: Special considerations when analyzing data from BlackBerry OS 10 devices:
You must have the device passcode as well as the BlackBerry Link password in order to backup or
view
this data This requires an Internet connection on the processing machine because you are
authenticating to the BlackBerry
Link Server to authenticate the username and password
You may encounter issues when attempting to acquire a BES-enabled device.
Question 5
The device pictured below is in Download Mode to attempt a physical acquisition.
What can be ascertained by viewing the Android boot screen below?
A. The Android is not rooted
B. No ROM changes have ever occurred on this device
C. The Original/Factory ROM is booting
D. The Original ROM was at one time modified
Answer:
C
Explanation
Reference:
https://www.digitalforensics.com/blog/physical-acquisition-of-a-locked-android-device/
Question 6
An analyst investigating a Nokia S60 Symbian device wants to know if an Adobe Flash file on the
handset is compromised.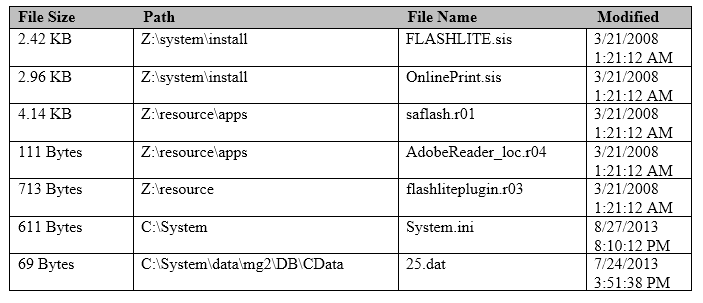
Which file in the image will best target the Adobe Flash files?
A. FLASHLITE.sis
B. flashliteplugin.r03
C. saflash.r01
D. OnlinePrint.sis
Answer:
A
Explanation
Explanation: A sis.file is the package that Symbian uses to install applications on their OS compatible
handsets. Knowing that you are investigating an application that is installed on the handset, first
narrowing the files down to installer packages, or *.sis files, is a good starting point. Flash is an
Adobe product making the most logical of the two remaining* .sis files for review, the FLASHLITE
installer package. There are several other files related to “Flash” but as resource files, they provide
supporting documentation and will not contain the .app file or code that was possibly malicious.
Question 7
As part of your analysis of a legacy BlackBerry device, you examine the installed applications list and
it
appears that no third-party applications were installed on the device. Which other file may provide
you with additional information on applications that were accessed with the handset?
A. BlackBerry NV Items
B. Content Store
C. Event logs
D. BBThumbs.dat
Answer:
C
Explanation
Explanation: Analyzing both the Event Logs (which are accessible in Oxygen Forensic Suite) and/or
the
Installed Applications (which is a feature available in Cellebrite Physical Analyzer) may lead you to
additional
datA. If applications of interest were located in the Event Logs, a Keyword Search across the media
may reveal more data related to the application.
Question 8
Which artifact must be carved out manually when examining a file system acquisition of an Android
device?
A. Deleted images
B. Contacts
C. SMS messages
D. Phone numbers
Answer:
C
Explanation
Question 9
When conducting forensic analysis of an associated media card, one would most often expect to find
this
particular file system format?
A. HFS
B. NTFS
C. Yaffs2
D. FAT
Answer:
D
Explanation
Question 10
Cellebrite Physical Analyzer uses Bit Defender to scan for malware by flagging files who have known
bad hash values. This is an example of which type of mobile malware detection?
A. Specific-based malware detection
B. Signature-based detection
C. Behavioral-based detection
D. Cloud based malware detection
Answer:
B
Explanation
Reference:
https://security.stackexchange.com/questions/95186/what-is-the-precise-difference-
between-asignature-based-vs-behavior-based-antiv
Question 11
Which of the following is required in addition to the Apple ID of the custodian to access IOS backup
files that are stored in ICloud?
A. iTunes password
B. Device passcode
C. Manifest.plist
D. Keychain-backup.plist
Answer:
B
Explanation
Question 12
In 2015, Apple’s iTunes store was found to be hosting several malicious applications that were
infected as a result of hacked version of the developer toolkit used to create applications. Which
Apple developer suite was targeted?
A. Xcode
B. ADB
C. Momentics IDE
D. Xamarin
Answer:
A
Explanation
Reference:
http://money.cnn.com/2015/09/21/technology/apple-xcode-hack/index.html
Question 13
An Android device user is known to use Facebook to communicate with other parties under
examination.
There is no evidence of the Facebook application on the phone. If there was Facebook usage where
would an examiner expect to find these artifacts?
A. com.android.chrome/app_chrome/Default/Local Storage
B. dmappmgr.db
C. /data/system/packages.xml
D. AndroidManifest.xml
Answer:
B
Explanation
Reference:
https://www.ctsforensics.com/assets/news/35550_Web-update.pdf
Question 14
Physical Analyzer provides a function to narrow down a search based on a timestamp, a type, a party
or date.
What is the name of this advanced searching capability?
A. Watchlist Editor
B. Tags
C. Timeline
D. Event of Interest
Answer:
C
Explanation
Explanation: Physical Analyzer offers the Timeline feature to narrow down what happened on the
smartphone during a specific time, type, party, etc. This is commonly used to narrow down time
periods. Data that is manually carved will not be shown here. There is also an option to create a
custom timeline specification.
Question 15
The files pictured below from a BlackBerry OS10 file system have a unique file extension.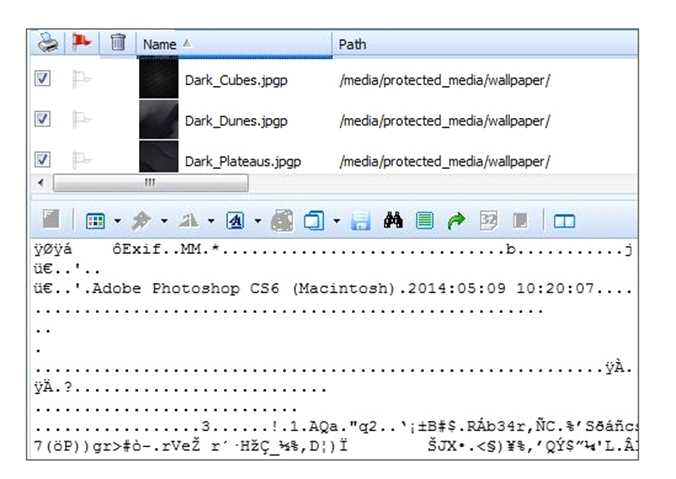
What can be concluded about these files?
A. Files are protected by the file system, so changing the file system makes them less accessible
B. Files are encrypted to prevent them from being viewed without the decryption key
C. Files are encoded for secure transmitting of data
D. Files are located on a media card so they contain a unique file extension
Answer:
A
Explanation
Reference:
https://forums.crackberry.com/blackberry-q10-f272/protected-media-911023/