Fortinet nse8-811 practice test
Fortinet NSE 8 Written Exam (NSE8_811) Exam
Question 1
Click the Exhibit button.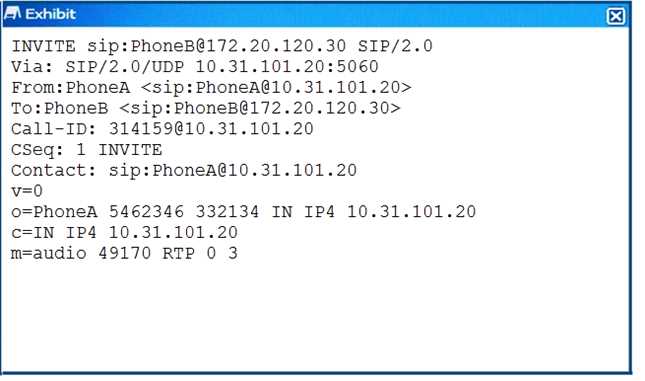
Click the Exhibit button.
A FortiGate with the default configuration is deployed between two IP phones. FortiGate receives
the INVITE request shown in the exhibit form Phone A (internal)to Phone B (external). Which two
actions are taken by the FortiGate after the packet is received? (Choose two.)
- A. A pinhole will be opened to accept traffic sent to FortiGate's WAN IP address and ports 49169 and 49170.
- B. a pinhole will be opened to accept traffic sent to FortiGate's WAN IP address and ports 49l70 and 49171.
- C. The phone A IP address will be translated lo the WAN IP address in all INVITE header fields and the m: field of the SDP statement.
- D. The phone A IP address will be translated for the WAN IP address in all INVITE header fields and the SDP statement remains intact.
Answer:
BC
Explanation:
Also, the FortiGate must translate the addresses contained in the SIP headers and SDP body of the
SIP
messages
The RTP port number as defined in the SIP message and an RTCP port number, which is the RTP port
number plus 1
Question 2
Click the Exhibit button.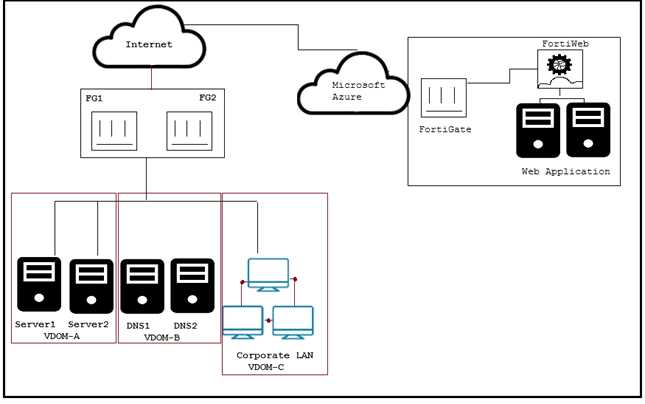
A customer has just finished their Azure deployment to secure a Web application behind a FortiGate
and a FortiWeb. Now they want to add components to protect against advanced threats (zero day
attacks), centrally manage the entire environment, and centrally monitor Fortinet and non-Fortinet
products.
Which Fortinet solutions will satisfy these requirements?
- A. Use FotiAnalyzer lor monitor in Azure, FortiSlEM for managemnet, and FortiSandbox for zero day attacks on their local network.
- B. Use Fortianalyzer for monitor Azure, FortiSiEM for management, and FortiGate has zero day attacks on their local network.
- C. Use FortiManager for management in Azure, FortSIEM for monitoring and FcrtiSandbox for zero day attacks on their local network.
- D. Use FortiSIEM for management Azure, FortiManager for management, and FortrGate for zero day attacks on their local network.
Answer:
C
Question 3
You configure an outgoing firewall policy with a web filter for accessing the internet. The access to
URL https// itacm.co and web belonging to the same category should be blocked. You notice that the
Web server presents a certificate with CN=www acme.com. The
www.it.acme
site is as '' information
Technology and the
www.acme.com
site is categorized as ''Business".
Which statements is correct in this scenario?
- A. Category "information Technology" needs to blocked, the FortiGate is able to inspection the URL with HTTPS sessions.
- B. Category "Business" need a to be block: the certificate name takes precedence over the SNI.
- C. SSL inspection must be configured to deep-inspection: the category "information Technology "needs to be blocked.
- D. Category :information Technology" needs to be blocked, the SNI takes precedence over the certificate name.
Answer:
D
Explanation:
FortiOS parses TLS server name indication (SNI) from TSL Client Hello. When this value has been
retrieved, it will be used for non-deep web filtering inspection, in preference to the existing HTTPS
Server CN web filtering.
Question 4
Refer to the Exhibit button.
You need to run a script in FortiManager against managed FortiGate devices in your organization to
install a configuration for a new static route. Which two scripts will successfully configure the static
route on the managed device? (Choose two.)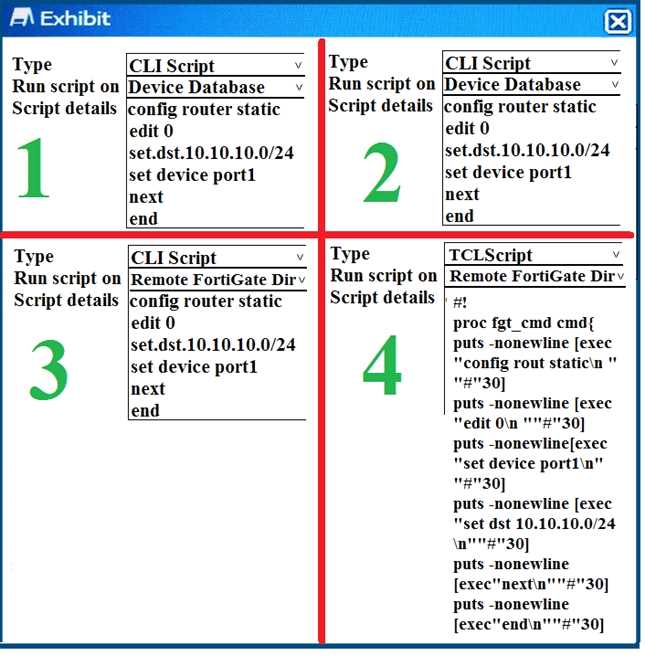
- A. Script 1
- B. Script 2
- C. Script 3
- D. Script 4
Answer:
BC
Question 5
You deploy a FortiGate device in a remote office based on the requirements shown below.
-- Due to company's security policy, management IP of your FortiGate is not allowed to access the
Internet.
-- Apply Web Filtering, Antivirus, IPS and Application control to the protected subnet.
-- Be managed by a central FortiManager in the head office.
Which action will help to achieve the requirements?
- A. Configure a default route and make sure that the FortiGate device can pmg to service fortiguard net.
- B. Configure the FortiGuard override server and use the IP address of the FortiManager
- C. Configure the FortiGuard override server and use the IP address of service, fortiguard net.
- D. Configure FortiGate to use FortiGuard Filtering Port 8888.
Answer:
B
Question 6
Click the Exhibit button.
config system ha
set mode a-a
set group-id 1
set group-name main
set hb_dev port2 100
set session-pickup enable
end
You have configured an HA cluster with two FortiGates. You want to make sure that you are able to
manage the individual cluster members directly using port3.
Referring to the exhibit, what are two ways to accomplish this task? (Choose two.)
- A. Disable the sync feature on porl3: then configure specific IPs for ports on both cluster members.
- B. Configure port3 to be a dedicated HA management interface, then configure specific IPs for port3 on both cluster members.
- C. Create a management VDOM and Disable the HA synchronization for this VDOM, assign ports to this VDOM, then configure specific IPs for ports on both cluster member.
- D. Allow administrative access in the HA heartbeat interfaces.
Answer:
BC
Question 7
An old router has been replaced by a FortiWAN device. The FortiWAN has inherited the routers
management IP address and now the network administrator needs to remove the old router from
the FortiSIEM configuration.
Which two statements are true about this operation? (Choose two.)
- A. FortiSIEM will discover a new device for the FortiWAN with the same IP.
- B. The old router will be completely deleted from FortiSIEM's CMDB.
- C. FotiSEIM needs a special syslog for FortiWAN.
- D. FortiSIM will move the old router device into the Decommission folder.
Answer:
AD
Explanation:
https://www.fortinetguru.com/2017/05/fortisiem-decommissioning-a-device/
Question 8
Exhibit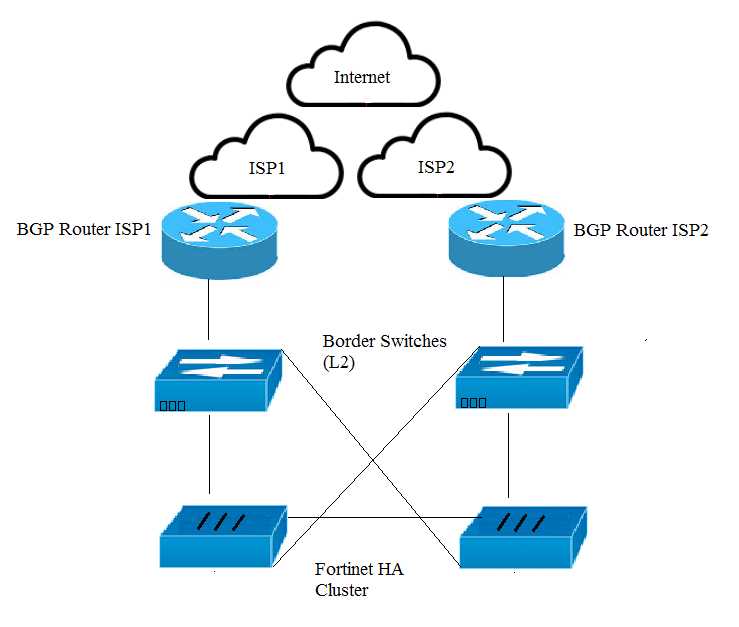
An organization has a FortiGate cluster that is connected to two independent ISPs. You must
configure the FortiGate failover for a single ISP failure to occur without disruption.
Referring to the exhibit, which two FortiGate BGP features are enabled to accomplish this task?
(Choose two.)
- A. EBGP multipath
- B. Graceful restart
- C. Synchronization
- D. BFD
Answer:
BD
Question 9
Refer to the exhibit.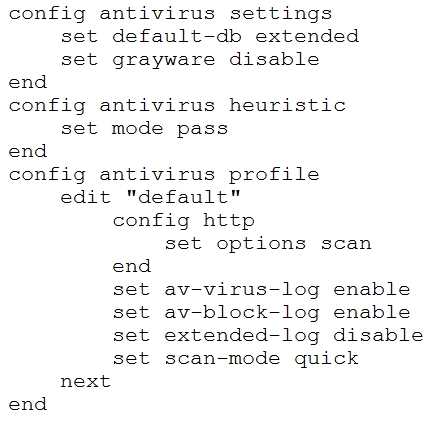
You are working on FortiGate 61E operating in flow-based inspection mode with various settings
optimized for performance. The main Internet firewall policy is using the "default" antivirus profile.
You found that some executable virus samples files downloaded over HTTP are not being blocked by
the FortiGate.
Referring to the exhibit, how can this be fixed?
- A. Change the set scan-mode configuration to full.
- B. Disable the emulator feature.
- C. Change the set default-db configuration to extreme.
- D. Add set content-disarm enable to the configuration.
Answer:
A
Question 10
A company has just rolled out new remote sites and now you need to deploy a single firewall policy
to all of these sites to allow Internet access using FortiManager. For this particular firewall policy, the
source address object is called LAN, but its value will change according to the site the policy is being
installed.
Which statement about creating the object LAN is correct?
- A. Create a new object called LAN and enable per-device mapping.
- B. Create a new object called LAN and promote it to the global database.
- C. Create a new object called LAN and use it as a variable on a TCL script.
- D. Create a new object called LAN and set meta-fields per remote site.
Answer:
A
Question 11
Click the Exhibit button.
Central NAT was configured on a FortiGate firewall. A sniffer shows ICMP packets out to a host on the
Internet egresses with the port1 IP address instead of the virtual IP(VIP) that was configured.
Referring to the exhibit, which configuration will ensure that ICMP traffic is also translated?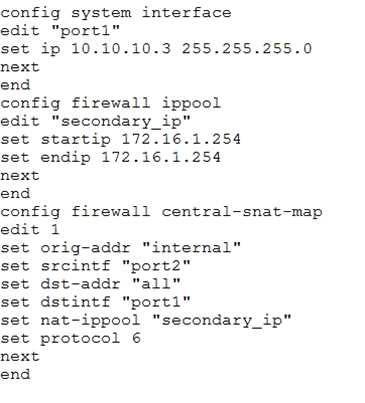
- A. config firewall ippool edit “secondry_ip” set arp-intf ‘port1’ next end
- B. config firewall central-snat-map edit 1 set protocol 1 next end
- C. config firewall central-snat-map edit 1 unset protocol next end
- D. config firewall central-snat-map edit 1 set orig-addr “all” next end
Answer:
C
Question 12
You configured a firewall policy with only a Web filter profile for accessing the Internet. Access to
websites belonging to the "Information Technology" category are blocked and to the "Business"
category are allowed. SSL deep inspection is not enabled on this policy.
A user wants to access the website
https://www.it-acme.com
which presents a certificate with
CN=www.acme.com. The it-acme.com domain is categorized as "Information Technology" and the
acme.com domain is categorized as "Business".
Which statement regarding this scenario is correct?
- A. The FortiGate is able to read the URL within HTTPS sessions when using SSL certificate inspection so the website will be blocked by the "Information Technology".
- B. The website will be blocked by category "Information Technology" as the SNI takes precedence over the certificate name.
- C. The website will be allowed by category "Business" as the certificate name takes precedence over the URL.
- D. Only with SSL deep inspection enabled will the FortiGate be able to categorized this website.
Answer:
B
Question 13
A FortOS devices is used for termination of VPNs for number of remote spoke VPN units (designated
group A spokes) using a phase 1 main mode dial-up tunnel using pre-shared. Your company recently
acquired another organization. You are asked establish VPN correctively for the newly acquired
organization's sites which new devices will be provisioned (designated Group B spokes). Both exiting
(Group A) and new (Group B) spoke units are dynamically addressed. You are asked to ensure that
spokes from the acquired organization (Group B) have different access permission than your existing
VPN spokes (Group A).
Which two solutions meet the represents for the new spoke group? (Choose two.)
- A. Implement a new phase 1 dial-up main mode tunnel with a different pre-shared key than the Group A spokes.
- B. Implement a new phase 1 dial-up main mode tunnel with certificate authentication.
- C. Implement a new phase 1 dial-up main mode tunnel with pre-shared keys and XAuth.
- D. Implement separate phase 1 dial-up aggressive mode tunnels with a distinct peer ID.
Answer:
CD
Question 14
Click the Exhibit button.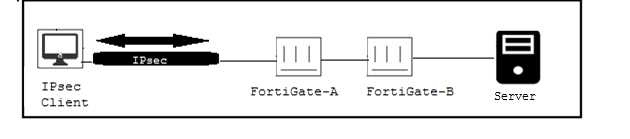
Only users authenticated in FortiGate-B can reach the server. A customer wants to deploy a single
sign-on solution for IPsec VPN users. Once a user is connected and authenticated to the VPN in
FortiGate-A, the user does not need to authenticate again in FortiGate B to reach the server.
Which two actions satisfy this requirement? (Choose two.)
- A. Use Kerberos authentication.
- B. FortiGate-A must generate a RADUIS accounting packets.
- C. Use FortiAuthenticator.
- D. Use the Collector Agent.
Answer:
BC
Question 15
Click the Exhibit button. An administrator implements a multi-chassis link aggregation (MCLAG)
solution using two FortiSwitch 448Ds and one FortiGate 3700D. As describes in the network topology
shown in the exhibit, two links are connected to each FortiSwitch. What is requires to implement this
solution? (Choose two.)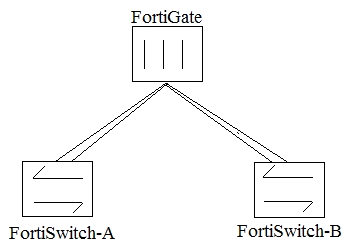
- A. Replace the FortiGate as this one does not have an ISF.
- B. Create two separate link aggregated (LAG) interfaces on the FortiGate side for each FortiSwitch.
- C. Add set fortilink-split-interface disable on the FortiLink interface.
- D. An ICL link between both FortiSwitch devices needs to be added.
Answer:
CD