Fortinet nse7-zta-7-2 practice test
fortinet nse 7 - zero trust access 7.2
Question 1
Which three methods can you use to trigger layer 2 polling on FortiNAC? (Choose three.)
- A. Link traps
- B. Manual polling
- C. Scheduled tasks
- D. Polling using API
- E. Polling scripts
Answer:
abc
Question 2
What happens when FortiClient EMS is configured as an MDM connector on FortiNAC?
- A. FortiNAC sends the host data to FortiClient EMS to update its host database.
- B. FortiClient EMS verifies with FortiNAC that the device is registered.
- C. FortiNAC polls FortiClient EMS periodically to update already registered hosts in FortiNAC.
- D. FortiNAC checks for device vulnerabilities and compliance with FortiClient.
Answer:
c
Question 3
Which statement is true regarding a FortiClient quarantine using FortiAnalyzer playbooks?
- A. FortiGate sends a notification to FortiClient EMS to quarantine the endpoint.
- B. FortiAnalyzer discovers malicious activity in the logs and notifies FortiGate.
- C. FortiAnalyzer sends an API to FortiClient EMS to quarantine the endpoint.
- D. FortiClient sends logs to FortiAnalyzer.
Answer:
c
Question 4
Which statement is true about disabled hosts on FortiNAC?
- A. They are quarantined and placed in the remediation VLAN.
- B. They are placed in the authentication VLAN to reauthenticate.
- C. They are marked as unregistered rogue devices.
- D. They are placed in the dead end VLAN.
Answer:
d
Question 5
Refer to the exhibit.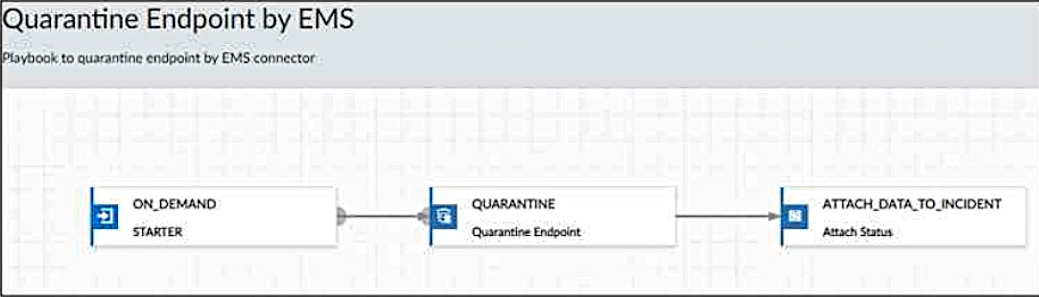
Which statement is true about the FortiAnalyzer playbook configuration shown in the exhibit?
- A. The playbook is run on a configured schedule.
- B. The playbook is run when an incident is created that matches the filters.
- C. The playbook is run when an event is created that matches the filters.
- D. The playbook is manually started by an administrator.
Answer:
d
Question 6
What are the three core principles of ZTA? (Choose three.)
- A. Verify
- B. Be compliant
- C. Certify
- D. Minimal access
- E. Assume breach
Answer:
ade
Question 7
What are two functions of NGFW in a ZTA deployment? (Choose two.)
- A. Acts as segmentation gateway
- B. Endpoint vulnerability management
- C. Device discovery and profiling
- D. Packet Inspection
Answer:
ad
Question 8
Which configuration is required for FortiNAC to perform an automated incident response based on the FortiGate traffic?
- A. FortiNAC should be added as a participant in the Security Fabric.
- B. FortiNAC requires read-write SNMP access to FortiGate.
- C. FortiNAC should be configured as a syslog server on FortiGate.
- D. FortiNAC requires HTTPS access to FortiGate for API calls.
Answer:
d
Question 9
Which two statements are true regarding certificate-based authentication for ZTNA deployment? (Choose two.)
- A. FortiGate signs the client certificate submitted by FortiClient.
- B. The default action for empty certificates is block.
- C. Certificate actions can be configured only on the FortiGate CLI.
- D. Client certificate configuration is a mandatory component for ZTNA.
Answer:
bd
Question 10
Refer to the exhibit.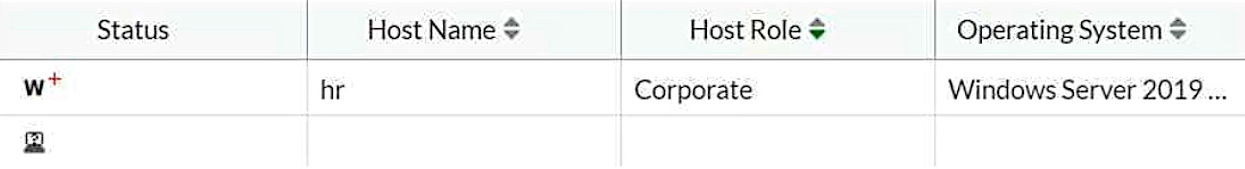
Which two statements are true about the hr endpoint? (Choose two.)
- A. The endpoint application inventory could not be retrieved.
- B. The endpoint is marked as a rogue device.
- C. The endpoint has failed the compliance scan.
- D. The endpoint will be moved to the remediation VLAN.
Answer:
ac