Fortinet nse7-ots-7-2 practice test
Fortinet NSE 7 - OT Security 7.2
Question 1
Operational technology (OT) network analysts run different levels of reports to identify failures that
could put the network at risk Some of these reports may be related to device performance
Which FortiSIEM reporting method helps identify device failures?
- A. Device inventory reports
- B. Payment card industry (PCI) logging reports
- C. Configuration management database (CMDB) operational reports
- D. Business service reports
Answer:
C
Question 2
Which three methods of communication are used by FortiNAC to gather visibility information?
(Choose three.)
- A. SNMP
- B. ICMP
- C. API
- D. RADIUS
- E. TACACS
Answer:
A,C,D
Question 3
Refer to the exhibit.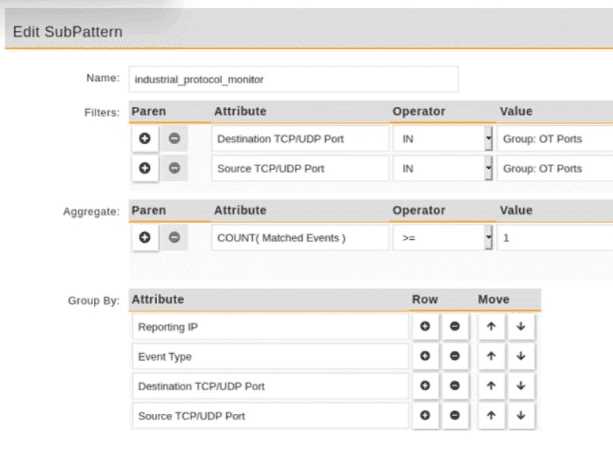
An operational technology rule is created and successfully activated to monitor the Modbus protocol
on FortiSIEM. However, the rule does not trigger incidents despite Modbus traffic and application
logs being received correctly by FortiSIEM.
Which statement correctly describes the issue on the rule configuration?
- A. The first condition on the SubPattern filter must use the OR logical operator.
- B. The attributes in the Group By section must match the ones in Fitters section.
- C. The Aggregate attribute COUNT expression is incompatible with the filters.
- D. The SubPattern is missing the filter to match the Modbus protocol.
Answer:
B
Question 4
What can be assigned using network access control policies?
- A. Layer 3 polling intervals
- B. FortiNAC device polling methods
- C. Logical networks
- D. Profiling rules
Answer:
C
Question 5
A FortiGate device is newly deployed as the edge gateway of an OT network security fabric. The
downstream FortiGate devices are also newly deployed as Security Fabric leafs to protect the control
area zone.
With no additional essential networking devices, and to implement micro-segmentation on this OT
network, what configuration must the OT network architect apply to control intra-VLAN traffic?
- A. Enable transparent mode on the edge FortiGate device.
- B. Enable security profiles on all interfaces connected in the control area zone.
- C. Set up VPN tunnels between downstream and edge FortiGate devices.
- D. Create a software switch on each downstream FortiGate device.
Answer:
D
Question 6
An OT network architect must deploy a solution to protect fuel pumps in an industrial remote
network. All the fuel pumps must be closely monitored from the corporate network for any
temperature fluctuations.
How can the OT network architect achieve this goal?
- A. Configure a fuel server on the remote network, and deploy a FortiSIEM with a single pattern temperature security rule on the corporate network.
- B. Configure a fuel server on the corporate network, and deploy a FortiSIEM with a single pattern temperature performance rule on the remote network.
- C. Configure a fuel server on the remote network, and deploy a FortiSIEM with a single pattern temperature performance rule on the corporate network.
- D. Configure both fuel server and FortiSIEM with a single-pattern temperature performance rule on the corporate network.
Answer:
C
Explanation:
This way, FortiSIEM can discover and monitor everything attached to the remote network and
provide security visibility to the corporate network
Question 7
Refer to the exhibit.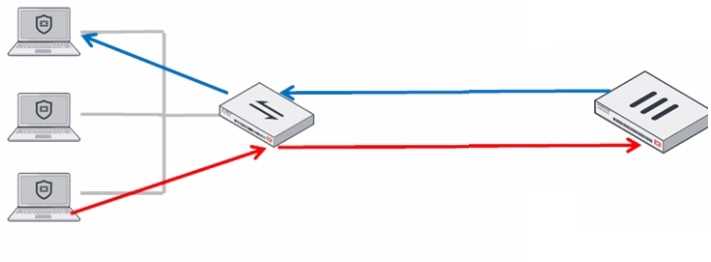
In order for a FortiGate device to act as router on a stick, what configuration must an OT network
architect implement on FortiGate to achieve inter-VLAN routing?
- A. Set a unique forward domain on each interface on the network.
- B. Set FortiGate to operate in transparent mode.
- C. Set a software switch on FortiGate to handle inter-VLAN traffic.
- D. Set a FortiGate interface with the switch to operate as an 802.1 q trunk.
Answer:
D
Question 8
An OT administrator configured and ran a default application risk and control report in FortiAnalyzer
to learn more about the key application crossing the network. However, the report output is empty
despite the fact that some related real-time and historical logs are visible in the FortiAnalyzer.
What are two possible reasons why the report output was empty? (Choose two.)
- A. The administrator selected the wrong logs to be indexed in FortiAnalyzer.
- B. The administrator selected the wrong time period for the report.
- C. The administrator selected the wrong devices in the Devices section.
- D. The administrator selected the wrong hcache table for the report.
Answer:
B,C
Explanation:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/32cb817d-a307-11eb-
b70b-00505692583a/FortiAnalyzer-7.0.0-Administration_Guide.pdf
Question 9
The OT network analyst runs different level of reports to quickly explore threats that exploit the
network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting
method helps to identify these type of exploits of image firmware files?
- A. CMDB reports
- B. Threat hunting reports
- C. Compliance reports
- D. OT/loT reports
Answer:
A
Question 10
In a wireless network integration, how does FortiNAC obtain connecting MAC address information?
- A. RADIUS
- B. Link traps
- C. End station traffic monitoring
- D. MAC notification traps
Answer:
A
Explanation:
FortiNAC can integrate with RADIUS servers to obtain MAC address information for wireless clients
that authenticate through the RADIUS server.
Reference:
Fortinet NSE 7 - OT Security 6.4 Study Guide, Chapter 4: OT Security Devices, page 4-28.
Question 11
How can you achieve remote access and internet availability in an OT network?
- A. Create a back-end backup network as a redundancy measure.
- B. Implement SD-WAN to manage traffic on each ISP link.
- C. Add additional internal firewalls to access OT devices.
- D. Create more access policies to prevent unauthorized access.
Answer:
B
Question 12
What are two critical tasks the OT network auditors must perform during OT network risk assessment
and management? (Choose two.)
- A. Planning a threat hunting strategy
- B. Implementing strategies to automatically bring PLCs offline
- C. Creating disaster recovery plans to switch operations to a backup plant
- D. Evaluating what can go wrong before it happens
Answer:
A,C
Question 13
What is the primary objective of implementing SD-WAN in operational technology (OT) networks'?
- A. Reduce security risk and threat attacks
- B. Remove centralized network security policies
- C. Enhance network performance of OT applications
- D. Replace standard links with lower cost connections
Answer:
C
Question 14
Refer to the exhibit.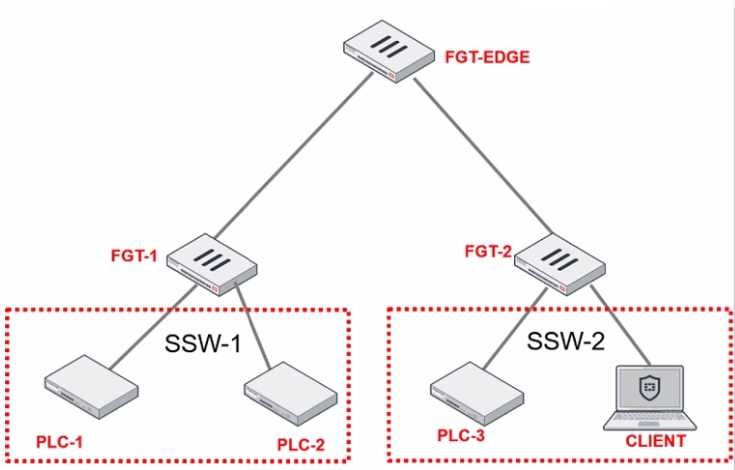
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1)
connecting both PLC-3 and CLIENT. PLC-3 and CLIENT cannot send traffic to each other.
Which two statements about the traffic between PCL-1 and PLC-2 are true? (Choose two.)
- A. The switch on FGT-2 must be hardware to implement micro-segmentation.
- B. Micro-segmentation on FGT-2 prevents direct device-to-device communication.
- C. Traffic must be inspected by FGT-EDGE in OT networks.
- D. FGT-2 controls intra-VLAN traffic through firewall policies.
Answer:
B,D
Question 15
An OT network consists of multiple FortiGate devices. The edge FortiGate device is deployed as the
secure gateway and is only allowing remote operators to access the ICS networks on site.
Management hires a third-party company to conduct health and safety on site. The third-party
company must have outbound access to external resources.
As the OT network administrator, what is the best scenario to provide external access to the third-
party company while continuing to secure the ICS networks?
- A. Configure outbound security policies with limited active authentication users of the third-party company.
- B. Create VPN tunnels between downstream FortiGate devices and the edge FortiGate to protect ICS network traffic.
- C. Split the edge FortiGate device into multiple logical devices to allocate an independent VDOM for the third-party company.
- D. Implement an additional firewall using an additional upstream link to the internet.
Answer:
C