B is the right answer
You are using HTTP content routing on FortiWeb. You want requests for web application A to be
forwarded to a cluster of web servers, which all host the same web application. You want requests
for web application B to be forwarded to a different, single web server.
Which statement about this solution is true?
D
How does FortiWeb protect against defacement attacks?
B
Explanation:
The anti-defacement feature examines a web sites files for changes at specified time intervals. If it
detects a change that could indicate a defacement attack, theFortiWebappliancecan notify you and
quickly react by automatically restoring the web site contents to the previous backup.
Reference:
https://help.fortinet.com/fweb/551/Content/FortiWeb/fortiweb-
admin/anti_defacement.htm
B is the right answer
What is one of the key benefits of the FortiGuard IP reputation feature?
D
Explanation:
FortiGuard IP Reputation service assigns a poor reputation, including virus-infected clients and
malicious spiders/crawlers.
Reference:
https://docs.fortinet.com/document/fortiweb/6.1.1/administration-
guide/137271/blacklisting-whitelisting-clients
Which three statements about HTTPS on FortiWeb are true? (Choose three.)
A, C, E
Reference:
https://docs.fortinet.com/document/fortiweb/6.3.0/administration-
guide/742465/supported-cipher-suites-protocol-versions
ADE is the right answer
When viewing the attack logs on FortiWeb, which client IP address is shown when you are using XFF
header rules?
D
Explanation:
When an XFF header reaches Alteon from a client, Alteon removes all the content from the header
and injects the client IP address. Alteon then forwards the header to the server.
Reference:
https://support.radware.com/app/answers/answer_view/a_id/20925/~/modifying-the-
client-ip-address-in-the-xff-header-using-httpmod
In which two operating modes can FortiWeb modify HTTP packets? (Choose two.)
A, C
Explanation:
FortiWebappliances operating in offline protection mode or either of the transparent modes
Reference:
https://help.fortinet.com/fweb/541/Content/FortiWeb/fortiweb-
admin/planning_topology.htm
CD is the right answer
The FortiWeb machine learning (ML) feature is a two-phase analysis mechanism.
Which two functions does the first layer perform? (Choose two.)
B, D
Explanation:
The first layer uses the Hidden Markov Model (HMM) and monitors access to the application and
collects data to build a mathematical model behind every parameter and HTTP method.
Reference:
https://docs.fortinet.com/document/fortiweb/6.3.0/administration-
guide/193258/machine-learning
In which scenario might you want to use the compression feature on FortiWeb?
D
Explanation:
FortiWebmight expend resources compressing responses that have already been compressed by the
server.
Reference:
https://docs.fortinet.com/document/fortiweb/6.3.7/administration-
guide/650285/compression
A is the right answer
A is the right answer
When is it possible to use a self-signed certificate, rather than one purchased from a commercial
certificate authority?
C
Explanation:
This can include SSL/TLS certificates, code signing certificates, and S/MIME certificates. The reason
why theyre considered different from traditional certificate-authority signed certificates is that
theyre created, issued, and signed by the company or developer who is responsible for the website
or software being signed. This is why self-signed certificates are considered unsafe for public-facing
websites and applications.
Reference:
https://sectigostore.com/page/what-is-a-self-signed-certificate/
D is the right answer
Refer to the exhibits.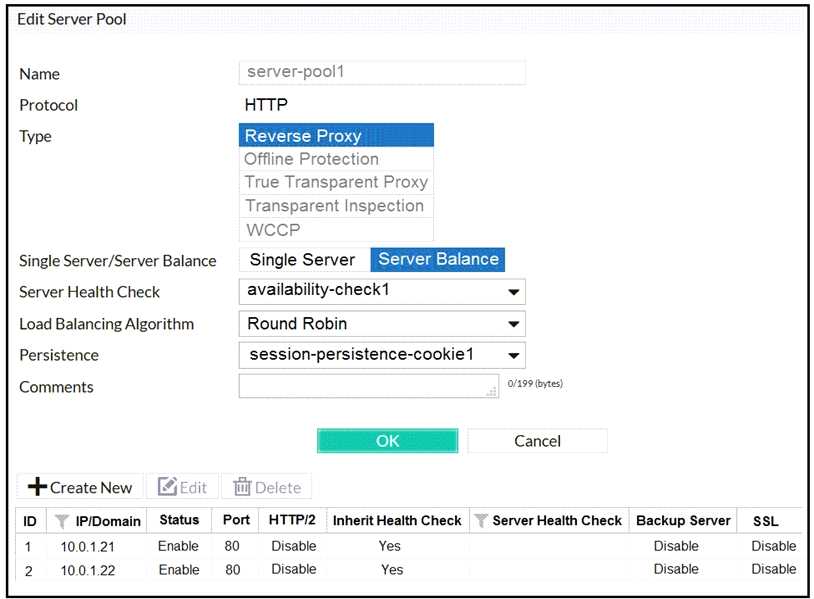
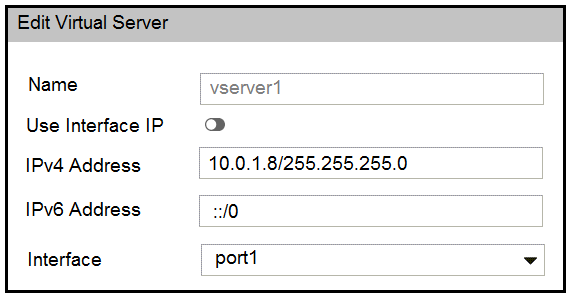
FortiWeb is configured in reverse proxy mode and it is deployed downstream to FortiGate. Based on
the configuration shown in the exhibits, which of the following statements is true?
D
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/ebe2ce28-
5c66-11eb-b9ad-00505692583a/FortiWeb_6.3.10_Administration_Guide.pdf
What key factor must be considered when setting brute force rate limiting and blocking?
D
B is the right answer
Refer to the exhibit.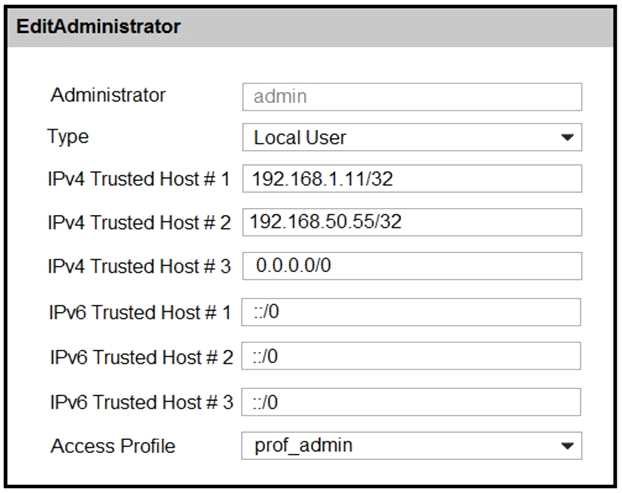
There is only one administrator account configured on FortiWeb. What must an administrator do to
restrict any brute force attacks that attempt to gain access to the FortiWeb management GUI?
A
Reference:
https://docs.fortinet.com/document/fortiweb/6.1.1/administration-
guide/397469/preventing-brute-force-logins
B is the right answer
What role does FortiWeb play in ensuring PCI DSS compliance?
D
Explanation:
FortiWeb protects against attacks that lead to sensitive data exposure such as SQL Injection and other
injection types. Additionally, FortiWeb inspects all web server outgoing traffic for sensitive data such
as Social Security numbers, credit card numbers and other predefined or custom based sensitive
data.
Reference:
https://www.gordion.de/fileadmin/user_upload/SG-PCI-Compliance.pdf
C is the right answer
C is the right answer
What must you do with your FortiWeb logs to ensure PCI DSS compliance?
C
Reference:
https://docplayer.net/8466775-Fortiweb-web-application-firewall-ensuring-compliance-for-pci-dss-requirement-6-6-solution-guide.html
Which two statements about the anti-defacement feature on FortiWeb are true? (Choose two.)
C, D
Explanation:
Anti-defacement backs up web pages only,notdatabases.
If it detects any file changes, theFortiWebappliance will download a new backup revision.
Reference:
https://help.fortinet.com/fweb/551/Content/FortiWeb/fortiweb-
admin/anti_defacement.htm
D is the answer