Fortinet nse6-fnc-8-5 practice test
Fortinet NSE 6 - FortiNAC 8.5
Question 1
Which connecting endpoints are evaluated against all enabled device profiling rules?
- A. All hosts, each time they connect
- B. Rogues devices, only when they connect for the first time
- C. Known trusted devices each time they change location
- D. Rogues devices, each time they connect
Answer:
D
Explanation:
FortiNAC process to classify rogue devices and create an organized inventory of known trusted
registered devices.
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/9529d49c-
892c-11e9-81a4-00505692583a/FortiNAC_Device_Profiler_Configuration.pdf
Question 2
Which agent is used only as part of a login script?
- A. Mobile
- B. Passive
- C. Persistent
- D. Dissolvable
Answer:
B
Explanation:
If the logon script runs the logon application in persistent mode, configure your Active Directory
server not to run scripts synchronously.
Reference:
https://www.websense.com/content/support/library/deployctr/v76/init_setup_creating_and_runni
ng_logon_agent_script_deployment_tasks.aspx
Question 3
What agent is required in order to detect an added USB drive?
- A. Persistent
- B. Dissolvable
- C. Mobile
- D. Passive
Answer:
A
Explanation:
Expand the Persistent Agent folder. Select USB Detection from the tree.
Reference:
https://docs.fortinet.com/document/fortinac/8.5.2/administration-guide/814147/usb-
detection
Question 4
What would occur if both an unknown (rogue) device and a known (trusted) device simultaneously
appeared on a port that is a member of the Forced Registration port group?
- A. The port would be provisioned for the normal state host, and both hosts would have access to that VLAN.
- B. The port would not be managed, and an event would be generated.
- C. The port would be provisioned to the registration network, and both hosts would be isolated.
- D. The port would be administratively shut down.
Answer:
C
Question 5
Which two agents can validate endpoint compliance transparently to the end user? (Choose two.)
- A. Passive
- B. Dissolvable
- C. Mobile
- D. Persistent
Answer:
CD
Explanation:
Mobile agents use the network transparently.
Reference:
https://docs.fortinet.com/document/fortinac/8.3.0/administration-guide/377110/persistent-agent-
certificate-validation
https://docs.fortinet.com/document/fortinac/8.3.0/administration-guide/377110/persistent-agent-
certificate-validation
Question 6
Which three communication methods are used by the FortiNAC to gather information from, and
control, infrastructure devices? (Choose three)
- A. RADIUS
- B. FTP
- C. SNMP
- D. DCLI
- E. SMTP
Answer:
ACD
Explanation:
Set up SNMP communication with FortiNAC
RADIUS Server that is used by FortiNAC to communicate
FortiNAC can be configured via CLI to use HTTP or HTTPS for OS updates instead of FTP.
Reference:
https://docs.fortinet.com/document/fortinac/8.3.0/administration-guide/28966/snmp
https://docs.fortinet.com/document/fortinac/8.8.0/administration-guide/938271/configure-radius-
settings
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/e7ebbdaa-cabf-11ea-
8b7d-00505692583a/FortiNAC_Deployment_Guide.pdf
Question 7
Refer to the exhibit.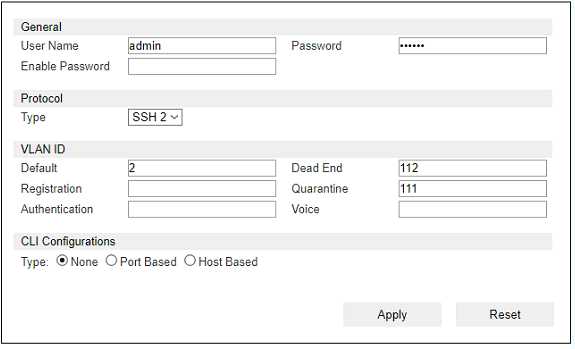
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects
to a port on the switch, what will occur?
- A. No VLAN change is performed
- B. The host is moved to a default isolation VLAN.
- C. The host is disabled.
- D. The host is moved to VLAN 111.
Answer:
C
Explanation:
The ability to limit the number of workstations that can connect to specific ports on the switch is
managed with Port Security. If these limits are breached, or access from unknown workstations is
attempted, the port can do any or all of the following: drop the untrusted data, notify the network
administrator, or disable the port.
Reference:
https://www.alliedtelesis.com/sites/default/files/documents/solutions-
guides/lan_protection_solution_reva.pdf
Question 8
Where are logical network values defined?
- A. In the model configuration view of each infrastructure device
- B. In the port properties view of each port
- C. On the profiled devices view
- D. In the security and access field of each host record
Answer:
A
Reference:
https://www.sciencedirect.com/topics/computer-science/logical-network
Question 9
How should you configure MAC notification traps on a supported switch?
- A. Configure them only after you configure linkup and linkdown traps
- B. Configure them only on ports set as 802 1q trunks
- C. Configure them on all ports except uplink ports
- D. Configure them on all ports on the switch
Answer:
C
Explanation:
Configure SNMP MAC Notification traps on all access ports (do not include uplinks).
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/be7fcde9-
9685-11e9-81a4-00505692583a/Configuring_Traps_for_MAC_Notification.pdf
Question 10
Where do you look to determine what network access policy, if any, is being applied to a particular
host?
- A. The Policy Details view for the host
- B. The Policy Logs view
- C. The network access policy configuration
- D. The Port Properties view of the hosts port
Answer:
C
Reference:
https://docs.microsoft.com/en-us/windows-server/networking/technologies/nps/nps-
np-overview
Question 11
Which three of the following are components of a security rule? (Choose three.)
- A. Security String
- B. Methods
- C. Action
- D. User or host profile
- E. Trigger
Answer:
CDE
Reference:
https://docs.fortinet.com/document/fortinac/8.8.0/administration-guide/167668/add-
or-modify-a-rule
Question 12
Which system group will force at-risk hosts into the quarantine network, based on point of
connection?
- A. Forced Isolation
- B. Physical Address Filtering
- C. Forced Quarantine
- D. Forced Remediation
Answer:
D
Explanation:
A remediation plan is established, including a forensic analysis and a reload of the system. Also, users
are forced to change their passwords as the system held local user accounts.
Reference:
https://oit.rice.edu/quarantining-process-used-it-staff-members-introduction
Question 13
During the on-boarding process through the captive portal, why would a host that successfully
registered remain stuck in the Registration VLAN? (Choose two.)
- A. Bridging is enabled on the host
- B. There is another unregistered host on the same port.
- C. The ports default VLAN is the same as the Registration VLAN.
- D. The wrong agent is installed.
Answer:
BD
Explanation:
Scenario 4: NAT detection disabled, using endpoint compliance policy and agent.
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/868f1267-
7299-11e9-81a4-00505692583a/fortinac-admin-operation-85.pdf
Question 14
In which view would you find who made modifications to a Group?
- A. The Event Management view
- B. The Security Events view
- C. The Alarms view
- D. The Admin Auditing view
Answer:
D
Explanation:
It’s important to audit Group Policy changes in order to determine the details of changes made to
Group Policies by delegated users.
Reference:
https://www.lepide.com/how-to/audit-chnages-made-to-group-policy-objects.html
Question 15
Which two of the following are required for endpoint compliance monitors? (Choose two.)
- A. Persistent agent
- B. Logged on user
- C. Security rule
- D. Custom scan
Answer:
AD
Explanation:
DirectDefense’s analysis of FireEye Endpoint attests that the products help meet the HIPAA Security
Rule.
In the menu on the left click the + sign next to Endpoint Compliance to open it.
Reference:
https://www.fireeye.com/content/dam/fireeye-www/products/pdfs/cg-pci-and-hipaa-
compliances.pdf
https://docs.fortinet.com/document/fortinac/8.5.2/administration-guide/92047/add-or-modify-a-
scan