Fortinet nse5-edr-5-0 practice test
Fortinet NSE 5 - FortiEDR 5.0
Question 1
What is the purpose of the Threat Hunting feature?
- A. Delete any file from any collector in the organization
- B. Find and delete all instances of a known malicious file or hash in the organization
- C. Identify all instances of a known malicious file or hash and notify affected users
- D. Execute playbooks to isolate affected collectors in the organization
Answer:
C
Question 2
How does FortiEDR implement post-infection protection?
- A. By preventing data exfiltration or encryption even after a breach occurs
- B. By using methods used by traditional EDR
- C. By insurance against ransomware
- D. By real-time filtering to prevent malware from executing
Answer:
D
Question 3
Exhibit.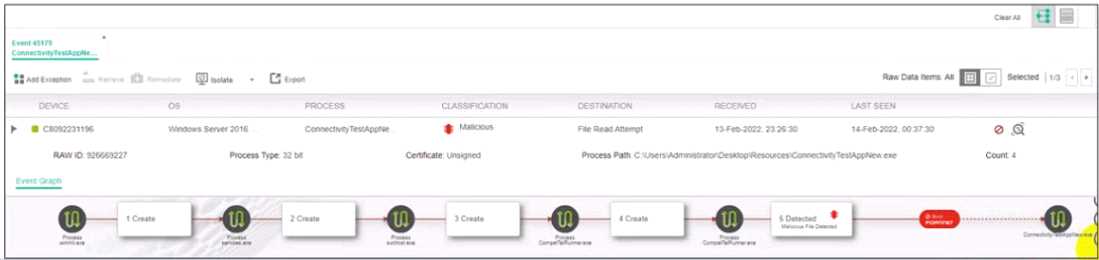
Based on the forensics data shown in the exhibit which two statements are true? (Choose two.)
- A. The device cannot be remediated
- B. The event was blocked because the certificate is unsigned
- C. Device C8092231196 has been isolated
- D. The execution prevention policy has blocked this event.
Answer:
B, C
Question 4
What is the benefit of using file hash along with the file name in a threat hunting repository search?
- A. It helps to make sure the hash is really a malware
- B. It helps to check the malware even if the malware variant uses a different file name
- C. It helps to find if some instances of the hash are actually associated with a different file
- D. It helps locate a file as threat hunting only allows hash search
Answer:
C
Question 5
Exhibit.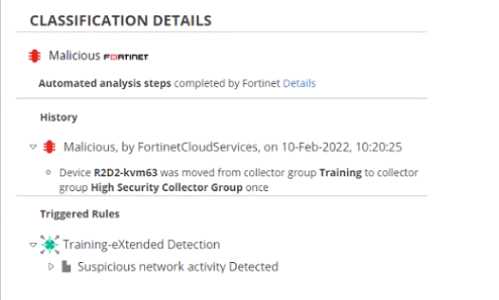
Based on the event shown in the exhibit which two statements about the event are true? (Choose
two.)
- A. The device is moved to isolation.
- B. Playbooks is configured for this event.
- C. The event has been blocked
- D. The policy is in simulation mode
Answer:
B, D
Question 6
An administrator needs to restrict access to the ADMINISTRATION tab in the central manager for a
specific account.
What role should the administrator assign to this account?
- A. Admin
- B. User
- C. Local Admin
- D. REST API
Answer:
C
Question 7
Refer to the exhibit.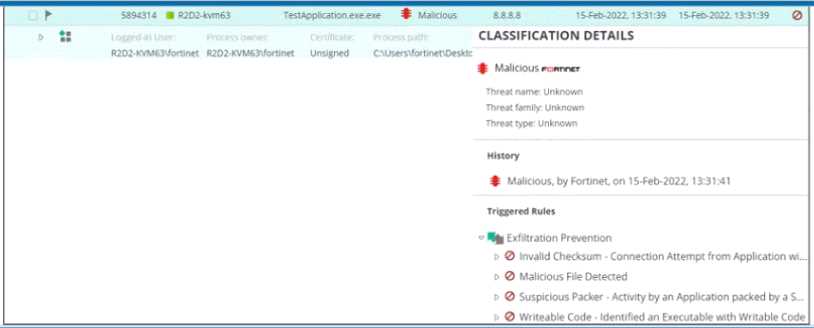
Based on the event shown in the exhibit, which two statements about the event are true? (Choose
two.)
- A. The NGAV policy has blocked TestApplication exe
- B. TestApplication exe is sophisticated malware
- C. The user was able to launch TestApplication exe
- D. FCS classified the event as malicious
Answer:
A, B
Question 8
Refer to the exhibits.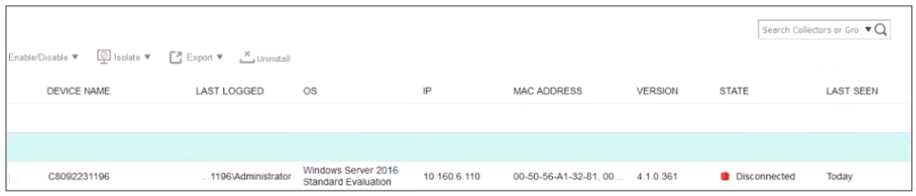
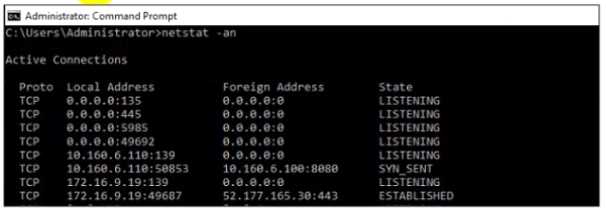
The exhibits show the collector state and active connections. The collector is unable to connect to
aggregator IP address 10.160.6.100 using default port.
Based on the netstat command output what must you do to resolve the connectivity issue?
- A. Reinstall collector agent and use port 443
- B. Reinstall collector agent and use port 8081
- C. Reinstall collector agent and use port 555
- D. Reinstall collector agent and use port 6514
Answer:
B
Question 9
Refer to the exhibits.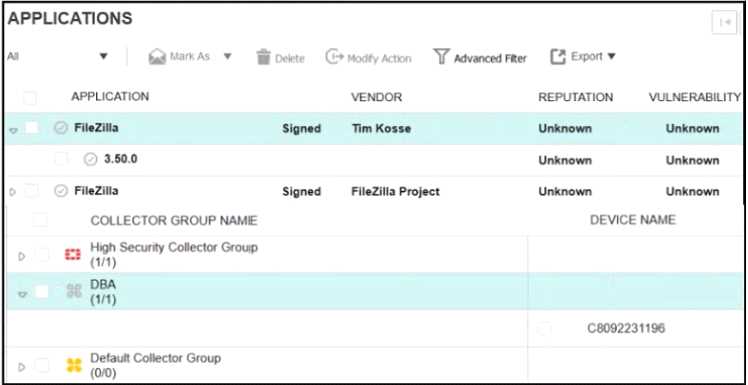
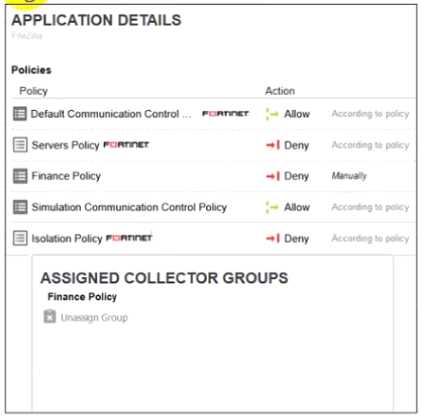
The exhibits show application policy logs and application details Collector C8092231196 is a member
of the Finance group
What must an administrator do to block the FileZilia application?
- A. Deny application in Finance policy
- B. Assign Finance policy to DBA group
- C. Assign Finance policy to Default Collector Group
- D. Assign Simulation Communication Control Policy to DBA group
Answer:
D
Question 10
Refer to the exhibit.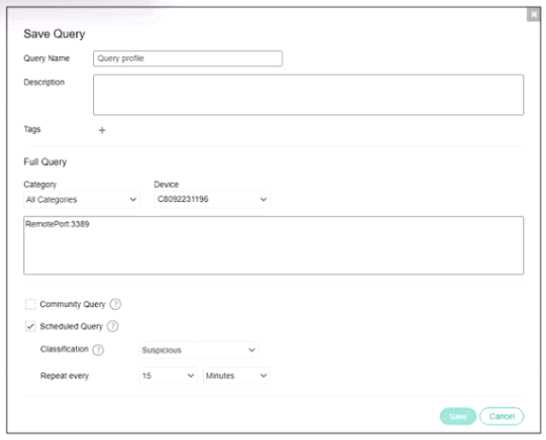
Based on the threat hunting query shown in the exhibit which of the following is true?
- A. RDP connections will be blocked and classified as suspicious
- B. A security event will be triggered when the device attempts a RDP connection
- C. This query is included in other organizations
- D. The query will only check for network category
Answer:
B
Question 11
Which connectors can you use for the FortiEDR automated incident response? (Choose two.)
- A. FortiNAC
- B. FortiGate
- C. FortiSiem
- D. FortiSandbox
Answer:
B, C
Question 12
What is true about classifications assigned by Fortinet Cloud Sen/ice (FCS)?
- A. The core is responsible for all classifications if FCS playbooks are disabled
- B. The core only assigns a classification if FCS is not available
- C. FCS revises the classification of the core based on its database
- D. FCS is responsible for all classifications
Answer:
C
Question 13
Refer to the exhibit.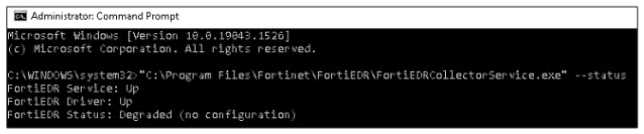
Based on the FortiEDR status output shown in the exhibit, which two statements about the FortiEDR
collector are true? (Choose two.)
- A. The collector device has windows firewall enabled
- B. The collector has been installed with an incorrect port number
- C. The collector has been installed with an incorrect registration password
- D. The collector device cannot reach the central manager
Answer:
B, D
Question 14
A company requires a global communication policy for a FortiEDR multi-tenant environment.
How can the administrator achieve this?
- A. An administrator creates a new communication control policy and shares it with other organizations
- B. A local administrator creates new a communication control policy and shares it with other organizations
- C. A local administrator creates a new communication control policy and assigns it globally to all organizations
- D. An administrator creates a new communication control policy for each organization
Answer:
C
Question 15
Refer to the exhibit.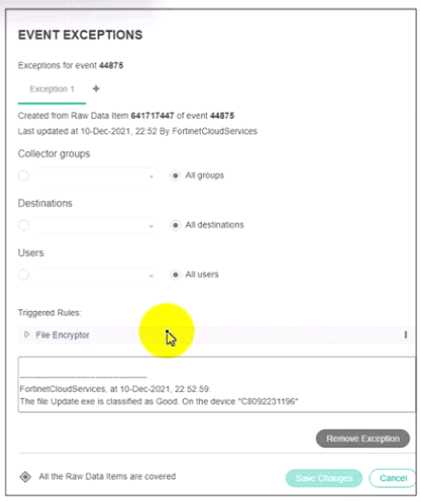
Based on the event exception shown in the exhibit which two statements about the exception are
true? (Choose two)
- A. A partial exception is applied to this event
- B. FCS playbooks is enabled by Fortinet support
- C. The exception is applied only on device C8092231196
- D. The system owner can modify the trigger rules parameters
Answer:
A, C