AB
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
Two PCs, PC1 and PC2, are connected behind FortiGate and can access the internet successfully. However, when the administrator adds a third PC to the network (PC3), the PC cannot connect to the internet.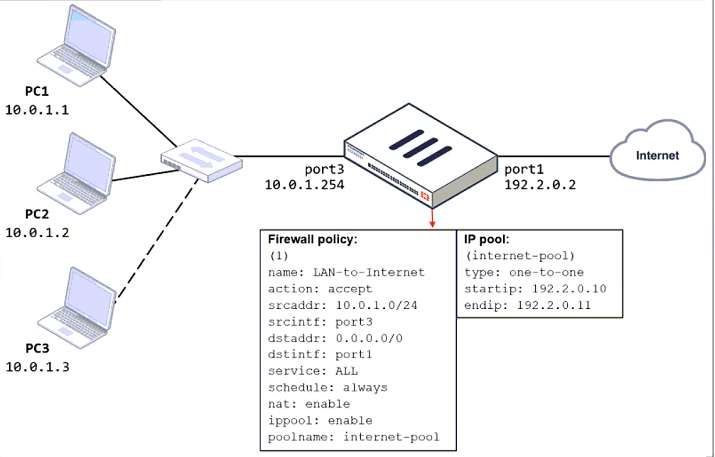
Based on the information shown in the exhibit, which three configuration changes should the administrator make to fix the connectivity issue for PC3? (Choose three.)
ade
Which two configuration settings are synchronized when FortiGate devices are in an active-active HA cluster? (Choose two.)
cd
AB
TOMA EL NOMBRE
dns y ntp ok
CD
C and d.
c-DNS
d-NTP
Which two statements are true about the FGCP protocol? (Choose two.)
ad
Elige el primario y descubre
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?
b
Correct answer is A, check FortiGate_Security_7.2_Study_Guide-Online.pdf, page 296, last paragraph.
A is correct
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
a
Busca de acuerdo a la firmas que tenga en el firewall.
Busca las base de las firmas en el firewall.
Refer to the exhibits.
An administrator creates a new address object on the root FortiGate (Local-FortiGate) in the security fabric. After synchronization, this object is not available on the downstream FortiGate (ISFW).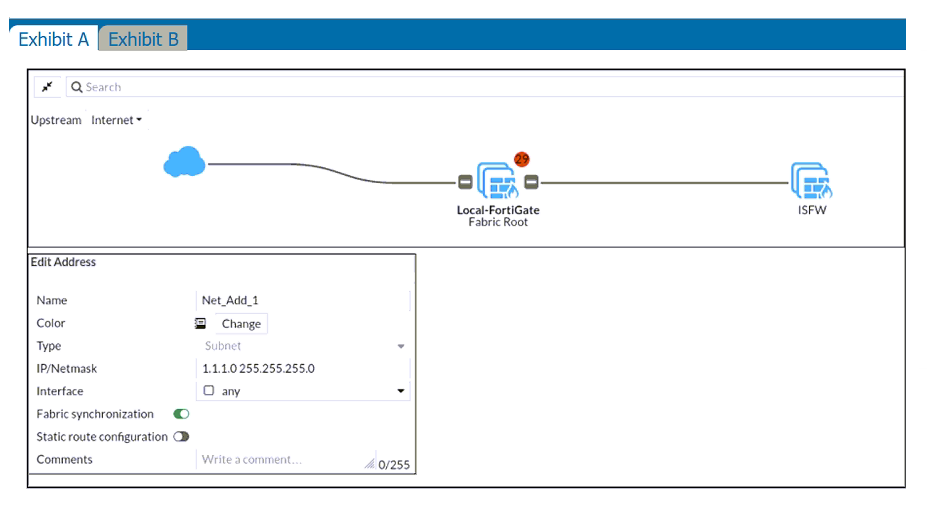
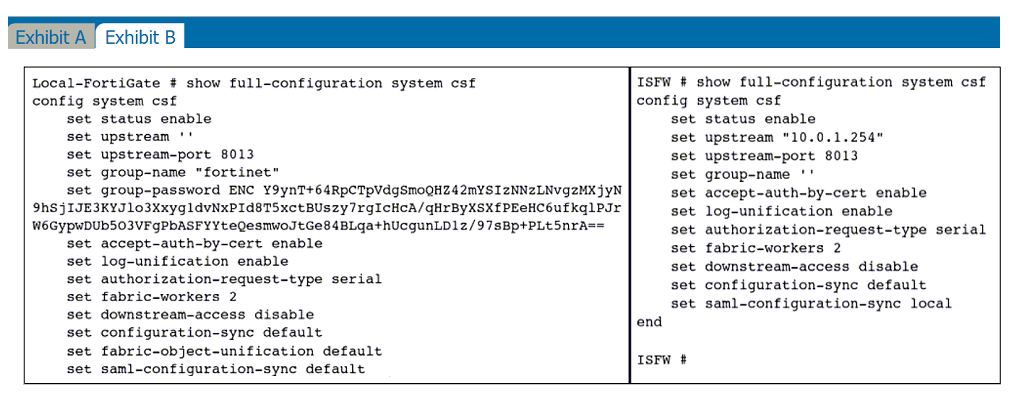
What must the administrator do to synchronize the address object?
d
I guess the correct answer should be: Change the csf setting on ISFW (downstream) to set fabric-object-unification default. Or am I wrong?
Configuracion
Refer to the exhibit.
The exhibit shows the output of a diagnose command.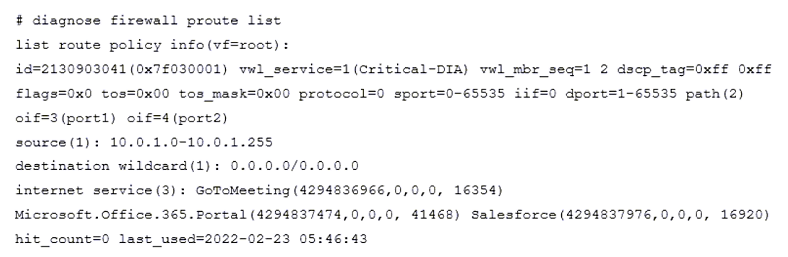
What does the output reveal about the policy route?
c
The correct answer is D. As shown in FortiGate_Infrastructure_7.2_Study_Guide-Online.pdf, page 59. Can't be A,B or C, because neither regular policies or ISDB policies show the vw1_service field.
POLICY ROUTER C
Refer to the exhibit.
The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile.
An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category.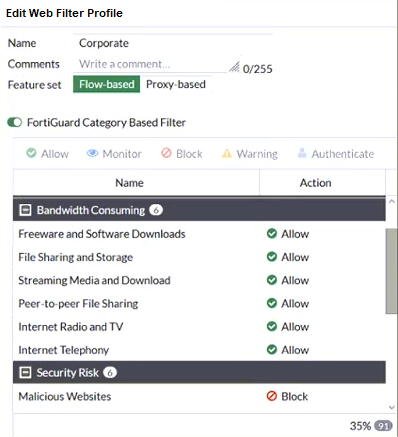
What are two solutions for satisfying the requirement? (Choose two.)
ad
Refer to the exhibits.
Exhibit A shows a topology for a FortiGate HA cluster that performs proxy-based inspection on traffic. Exhibit B shows the HA configuration and the partial output of the get system ha status command.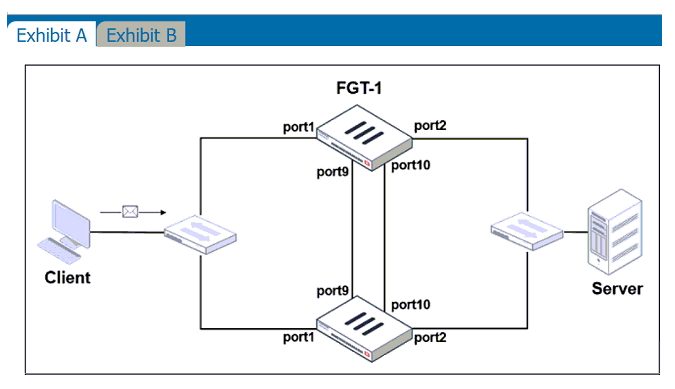
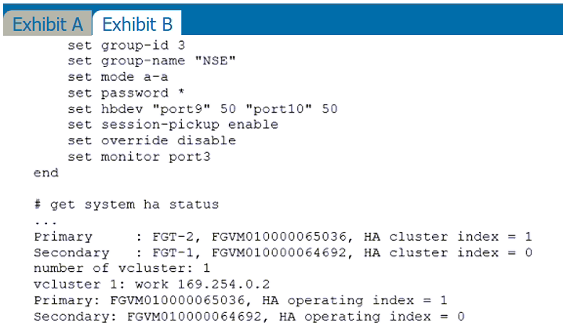
Based on the exhibits, which two statements about the traffic passing through the cluster are true? (Choose two.)
ab
An administrator has configured the following settings:
config system settings
set ses-denied-traffic enable
end
config system global
set block-session-timer 30
end
What are the two results of this configuration? (Choose two.)
ab
C. The number of logs generated by denied traffic is reduced.
D. A session for denied traffic is created.
FortiGate Security 7.2 Study Guide (p.69):
"During the session, if a security profile detects a violation, FortiGate records the attack log immediately. To reduce the number of log messages generated and improve performance, you can enable a session table entry of dropped traffic. This creates the denied session in the session table and, if the session is denied, all packets of that session are also denied. This ensures that FortiGate does not have to do a policy lookup for each new packet matching the denied session, which reduces CPU usage and log generation.
This option is in the CLI, and is called ses-denied-traffic. You can also set the duration for block sessions. This determines how long a session will be kept in the session table by setting block-sessiontimer in the CLI. By default, it is set to 30 seconds."
Reference and download study guide:
...........
i think the answer is ADE
Debe tener mas ip pool para poder navegar
a d and e are the answer
The problem is the IP pool is set to 1 to 1, but there's only 2 IPs in the pool. So when a third connects, there is no more IPs in the pool. The rule itself is fine. Expand the pool, or switch to overload instead of 1 to 1.
In the IP pool configuration, set endip to 192.2.0.12.
the answer is ACD
end ip must be increased so that PC3 can use NAT. Or we can set the type to overload so that it uses same ip address but different ports