Fortinet nse4-fgt-7-0 practice test
Fortinet NSE 4 - FortiOS 7.0 Exam
Question 1
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW
policy-based mode?
- A. It limits the scanning of application traffic to the DNS protocol only.
- B. It limits the scanning of application traffic to use parent signatures only.
- C. It limits the scanning of application traffic to the browser-based technology category only.
- D. It limits the scanning of application traffic to the application category only.
Answer:
C
Question 2
If Internet Service is already selected as Destination in a firewall policy, which other configuration
objects can be selected to the Destination field of a firewall policy?
A User or User Group
B. IP address
C. No other object can be added
D. FQDN address
Answer:
B
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.5/cookbook/179236/using-internet-
service-in-policy
Question 3
In an explicit proxy setup, where is the authentication method and database configured?
- A. Proxy Policy
- B. Authentication Rule
- C. Firewall Policy
- D. Authentication scheme
Answer:
D
Question 4
Which downstream FortiGate VDOM is used to join the Security Fabric when split-task VDOM is
enabled on all FortiGate devices?
- A. Root VDOM
- B. FG-traffic VDOM
- C. Customer VDOM
- D. Global VDOM
Answer:
A
Question 5
Refer to the exhibit, which contains a radius server configuration.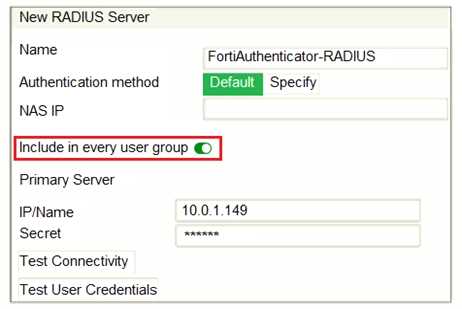
An administrator added a configuration for a new RADIUS server. While configuring, the
administrator selected the Include in every user group option.
What will be the impact of using Include in every user group option in a RADIUS configuration?
- A. This option places the RADIUS server, and all users who can authenticate against that server, into every FortiGate user group.
- B. This option places all FortiGate users and groups required to authenticate into the RADIUS server, which, in this case, is FortiAuthenticator.
- C. This option places all users into every RADIUS user group, including groups that are used for the LDAP server on FortiGate.
- D. This option places the RADIUS server, and all users who can authenticate against that server, into every RADIUS group.
Answer:
A
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.0.0/handbook/634373/authentication-
servers
Question 6
Which two statements are correct about a software switch on FortiGate? (Choose two.)
- A. It can be configured only when FortiGate is operating in NAT mode
- B. Can act as a Layer 2 switch as well as a Layer 3 router
- C. All interfaces in the software switch share the same IP address
- D. It can group only physical interfaces
Answer:
AC
Question 7
Which two statements are true about collector agent advanced mode? (Choose two.)
- A. Advanced mode uses Windows convention—NetBios: Domain\Username.
- B. FortiGate can be configured as an LDAP client and group filters can be configured on FortiGate
- C. Advanced mode supports nested or inherited groups
- D. Security profiles can be applied only to user groups, not individual users.
Answer:
BC
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.0.0/handbook/482937/agent-based-fsso
Question 8
Exhibit: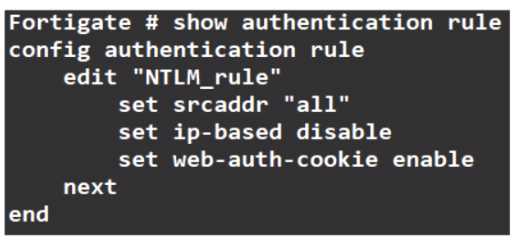
Refer to the exhibit to view the authentication rule configuration In this scenario, which statement is
true?
- A. IP-based authentication is enabled
- B. Route-based authentication is enabled
- C. Session-based authentication is enabled.
- D. Policy-based authentication is enabled
Answer:
C
Explanation:
Reference:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD45387
Question 9
A team manager has decided that, while some members of the team need access to a particular
website, the majority of the team does not Which configuration option is the most effective way to
support this request?
- A. Implement a web filter category override for the specified website
- B. Implement a DNS filter for the specified website.
- C. Implement web filter quotas for the specified website
- D. Implement web filter authentication for the specified website.
Answer:
D
Question 10
Which feature in the Security Fabric takes one or more actions based on event triggers?
- A. Fabric Connectors
- B. Automation Stitches
- C. Security Rating
- D. Logical Topology
Answer:
B
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/286973/fortinet-security-
fabric
Question 11
An administrator has a requirement to keep an application session from timing out on port 80. What
two changes can the administrator make to resolve the issue without affecting any existing services
running through FortiGate? (Choose two.)
- A. Create a new firewall policy with the new HTTP service and place it above the existing HTTP policy.
- B. Create a new service object for HTTP service and set the session TTL to never
- C. Set the TTL value to never under config system-ttl
- D. Set the session TTL on the HTTP policy to maximum
Answer:
BC
Question 12
In which two ways can RPF checking be disabled? (Choose two )
- A. Enable anti-replay in firewall policy.
- B. Disable the RPF check at the FortiGate interface level for the source check
- C. Enable asymmetric routing.
- D. Disable strict-arc-check under system settings.
Answer:
CD
Explanation:
Reference:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD33955
Question 13
Refer to the exhibit to view the application control profile.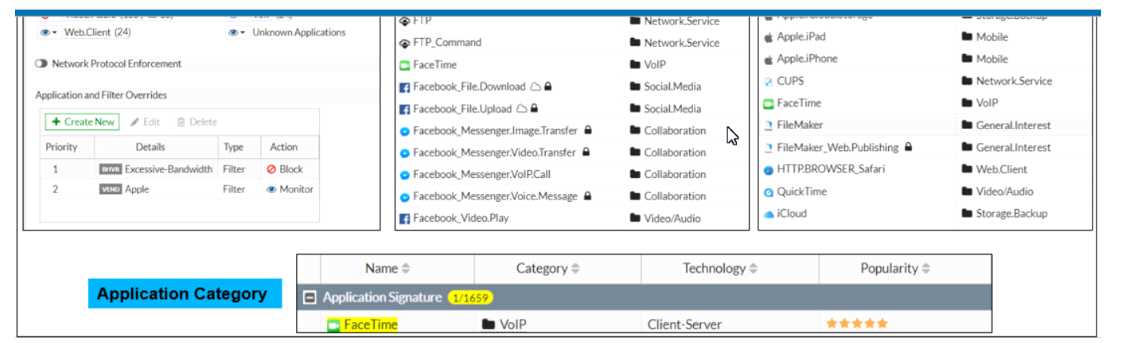
Based on the configuration, what will happen to Apple FaceTime?
- A. Apple FaceTime will be blocked, based on the Excessive-Bandwidth filter configuration
- B. Apple FaceTime will be allowed, based on the Apple filter configuration.
- C. Apple FaceTime will be allowed only if the filter in Application and Filter Overrides is set to Learn
- D. Apple FaceTime will be allowed, based on the Categories configuration.
Answer:
A
Question 14
Which three CLI commands can you use to troubleshoot Layer 3 issues if the issue is in neither the
physical layer nor the link layer? (Choose three.)
- A. diagnose sys top
- B. execute ping
- C. execute traceroute
- D. diagnose sniffer packet any
- E. get system arp
Answer:
BCD
Question 15
Which two VDOMs are the default VDOMs created when FortiGate is set up in split VDOM mode?
(Choose two.)
- A. FG-traffic
- B. Mgmt
- C. FG-Mgmt
- D. Root
Answer:
AD
Explanation:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/758820/split-task-vdom-
mode