Fortinet fcss sase ad 25 practice test
FCSS - FortiSASE 25 Administrator
Question 1
In the Secure Private Access (SPA) use case, which two FortiSASE features facilitate access to
corporate applications? (Choose two.)
- A. cloud access security broker (CASB)
- B. SD-WAN
- C. zero trust network access (ZTNA)
- D. thin edge
Answer:
B,C
Explanation:
SD-WAN allows efficient and secure routing of traffic from users to corporate applications, while
ZTNA enables secure access control and verification for users connecting to internal resources, both
of which are essential for Secure Private Access (SPA) in FortiSASE.
Question 2
Which two components are part of onboarding a secure web gateway (SWG) endpoint for secure
internet access (SIA)? (Choose two.)
- A. proxy auto-configuration (PAC) file
- B. FortiSASE certificate authority (CA) certificate
- C. FortiClient software
- D. tunnel policy
Answer:
A,C
Explanation:
A PAC file is used to redirect client web traffic through the SWG, and FortiClient software is required
to connect endpoints to the FortiSASE service for secure internet access (SIA).
Question 3
Which two advantages does FortiSASE bring to businesses with microbranch offices that have FortiAP
deployed for unmanaged devices? (Choose two.)
- A. It secures internet access both on and off the network.
- B. It uses zero trust network access (ZTNA) tags to perform device compliance checks.
- C. It eliminates the requirement for an on-premises firewall.
- D. It simplifies management and provisioning.
Answer:
A,C
Question 4
Which information can an administrator monitor using reports generated on FortiSASE?
- A. sanctioned and unsanctioned Software-as-a-Service (SaaS) applications usage
- B. FortiClient vulnerability assessment
- C. SD-WAN performance
- D. FortiSASE administrator and system events
Answer:
A
Explanation:
FortiSASE reporting provides visibility into the usage of sanctioned and unsanctioned SaaS
applications, enabling administrators to monitor cloud application activity and enforce security
policies.
Question 5
In a FortiSASE secure web gateway (SWG) deployment, which two features protect against web-
based threats? (Choose two.)
- A. SSL deep inspection for encrypted web traffic
- B. malware protection with sandboxing capabilities
- C. web application firewall (WAF) for web applications
- D. intrusion prevention system (IPS) for web traffic
Answer:
A,B
Explanation:
SSL deep inspection allows FortiSASE to analyze encrypted web traffic for threats, while malware
protection with sandboxing detects and blocks malicious files delivered through web channels.
Question 6
Refer to the exhibits.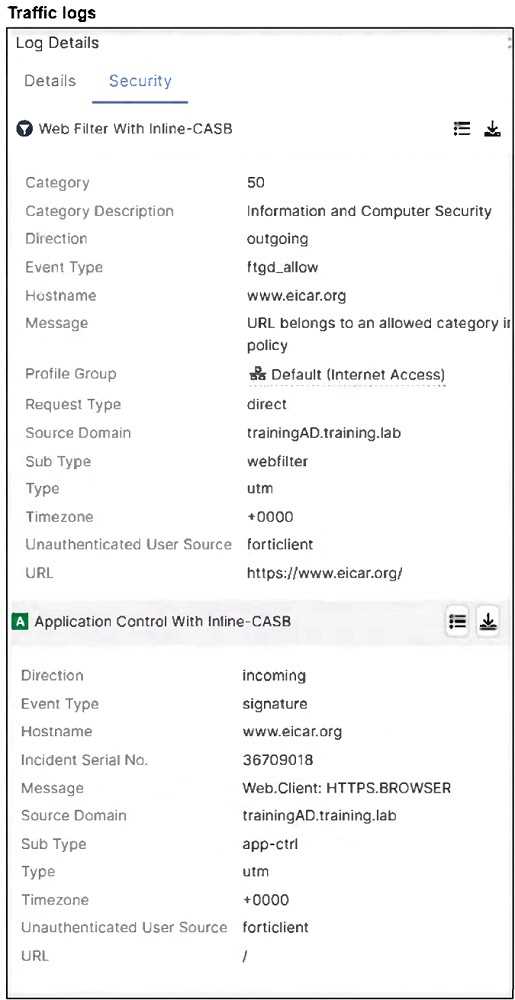
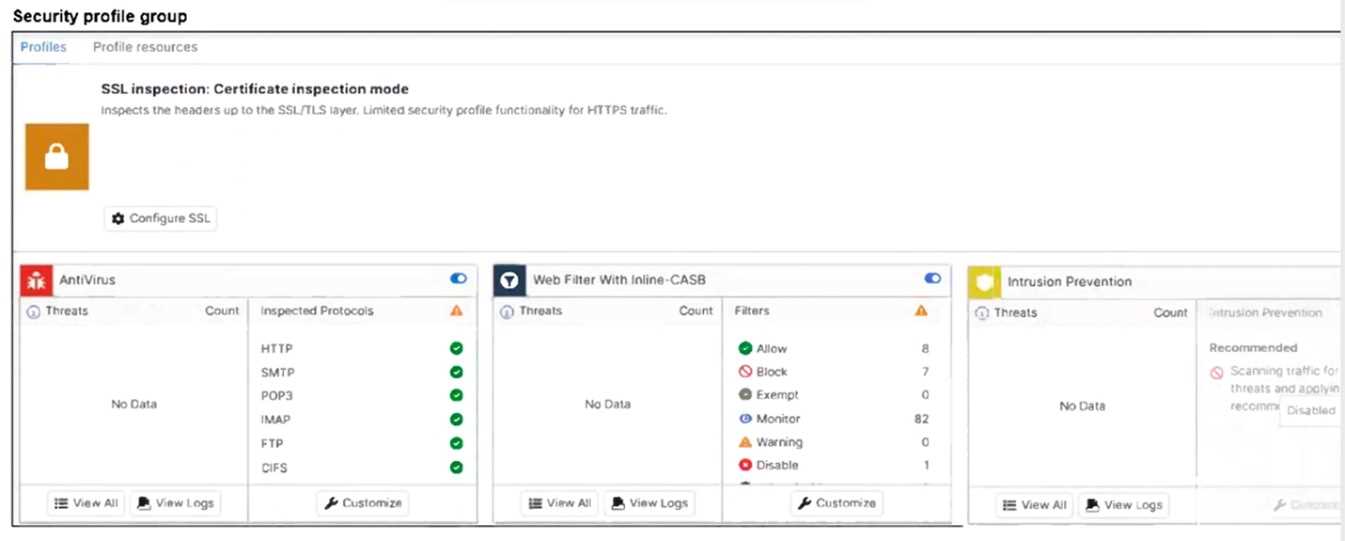
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied
it to the internet access policy. Remote users are still able to download the eicar.com-zip file from
https://eicar.org.
Which configuration on FortiSASE is allowing users to perform the download?
- A. Web filter is allowing the URL.
- B. Deep inspection is not enabled.
- C. Application control is exempting all the browser traffic.
- D. Intrusion prevention is disabled.
Answer:
B
Explanation:
The SSL inspection mode is set to certificate inspection, which only inspects SSL/TLS headers and
does not allow full scanning of encrypted content. Without full (deep) inspection, the antivirus
profile cannot scan or block malicious files (like eicar.com-zip) delivered over HTTPS, allowing the
download to proceed.
Question 7
Refer to the exhibit.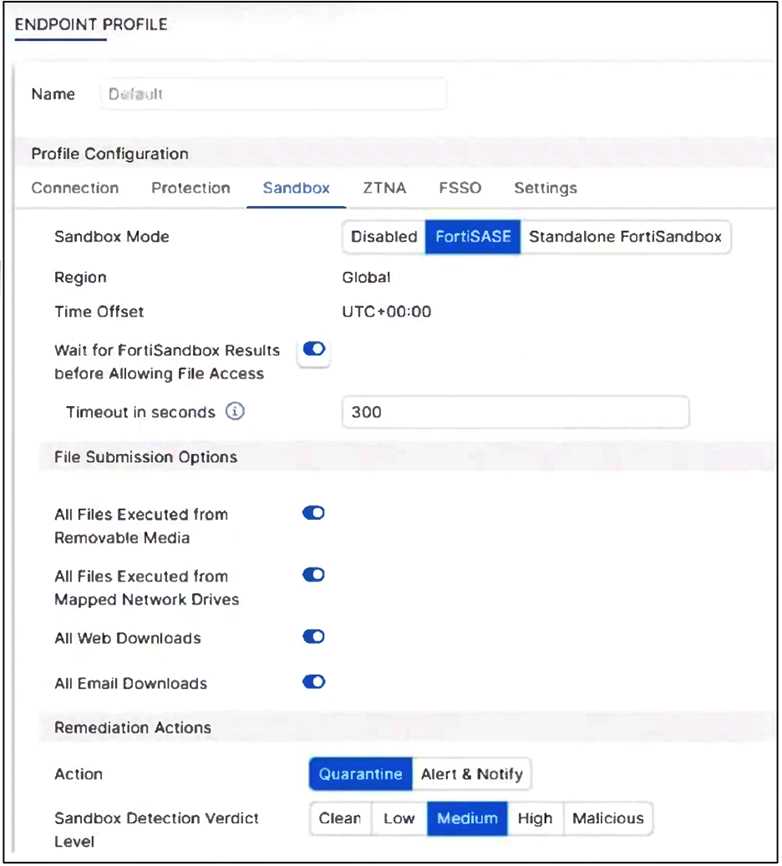
Based on the configuration shown, in which two ways will FortiSASE process sessions that require
FortiSandbox inspection? (Choose two.)
- A. Only endpoints assigned a profile for sandbox detection will be processed by the sandbox feature.
- B. FortiClient quarantines only infected files that FortiSandbox detects as medium level.
- C. All files executed on a USB drive will be sent to FortiSandbox for analysis.
- D. All files will be sent to a on-premises FortiSandbox for inspection.
Answer:
A,C
Explanation:
The sandbox feature applies only to endpoints assigned this profile, and the configuration explicitly
enables the submission of all files executed from removable media (like USB drives) to FortiSandbox
for analysis.
Question 8
An administrator must restrict endpoints from certain countries from connecting to FortiSASE.
Which configuration can achieve this?
- A. Configure a network lockdown policy on the endpoint profiles.
- B. Configure a geography address object as the source for a deny policy.
- C. Configure geofencing to restrict access from the required countries.
- D. Configure source IP anchoring to restrict access from the specified countries.
Answer:
C
Explanation:
Geofencing allows the administrator to restrict or allow access to FortiSASE services based on the
geographic location of the endpoints, effectively blocking connections from specified countries.
Question 9
What is the benefit of SD-WAN on-ramp deployment with FortiSASE?
- A. To provide access to private applications using the bookmark portal
- B. To provide device compliance checks using ZTNA tags
- C. To secure internet traffic for branch users
- D. To manage branch location endpoints
Answer:
C
Explanation:
SD-WAN on-ramp with FortiSASE directs branch user internet traffic to the FortiSASE cloud for
consistent security enforcement and protection, regardless of the branch location.
Question 10
Which two settings are automatically pushed from FortiSASE to FortiClient in a new FortiSASE
deployment with default settings? (Choose two.)
- A. zero trust network access (ZTNA) tags
- B. tunnel profile
- C. FortiSASE certificate authority (CA) certificate
- D. real-time protection
Answer:
B,C
Explanation:
In a default FortiSASE deployment, the tunnel profile (for secure connectivity) and the FortiSASE CA
certificate (for SSL inspection and trusted communication) are automatically pushed to FortiClient
endpoints.
Question 11
Refer to the exhibits.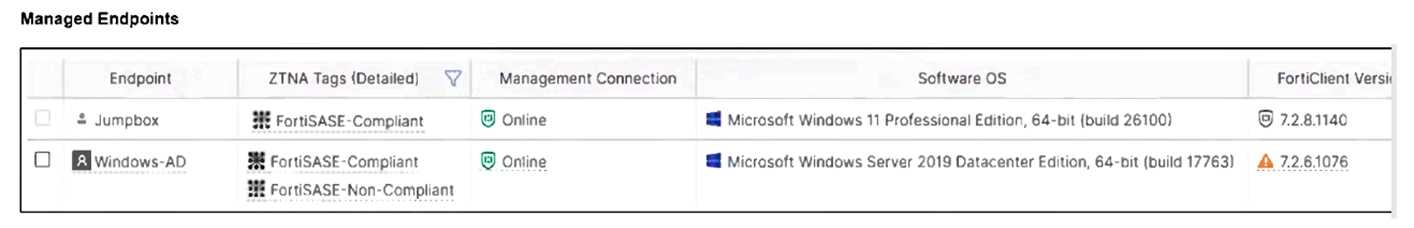
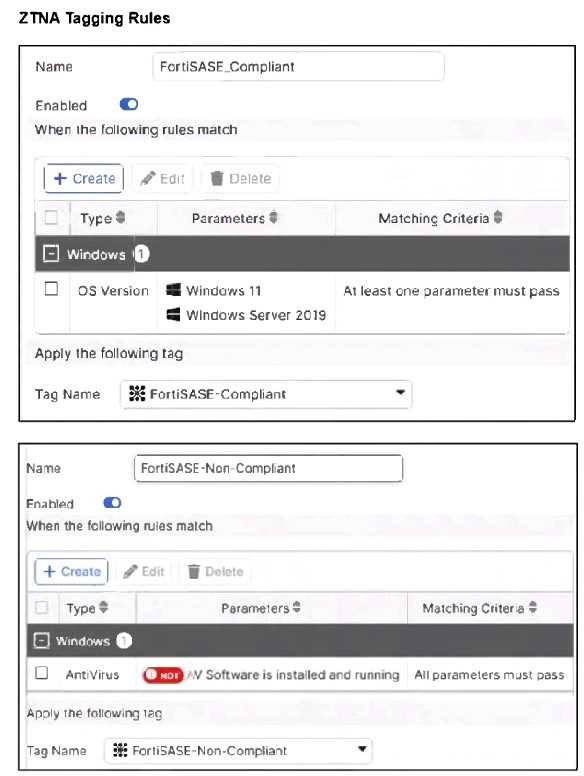
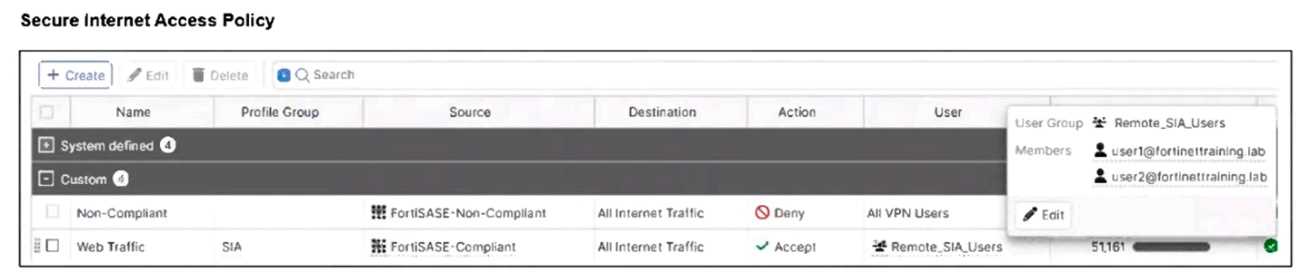
Jumpbox and Windows-AD are endpoints from the same remote location. Jumpbox can access the
internet through FortiSASE, while Windows-AD can no longer access the internet.
Based on the information in the exhibits, which reason explains the outage on Windows-AD?
- A. Windows-AD is excluded from FortiSASE management.
- B. The FortiClient version installed on Windows AD does not match the expected version on FortiSASE.
- C. The device posture for Windows-AD has changed.
- D. The remote VPN user on Windows-AD no longer matches any VPN policy.
Answer:
C
Explanation:
The Windows-AD endpoint now has both "FortiSASE-Compliant" and "FortiSASE-Non-Compliant"
tags due to failing the antivirus software check. As a result, the Secure Internet Access Policy matches
the "Non-Compliant" rule, which is set to Deny, causing the device to lose internet access.
Question 12
Which description of the FortiSASE inline-CASB component is true?
- A. It has limited visibility when data is transmitted.
- B. It detects data in motion.
- C. It is placed outside the traffic path.
- D. It relies on API to integrate with cloud services.
Answer:
B
Explanation:
FortiSASE inline-CASB operates in the traffic path to provide real-time visibility and control over data
in motion as it is transmitted to and from cloud applications.
Question 13
Which authentication method overrides any other previously configured user authentication on
FortiSASE?
- A. MFA
- B. Local
- C. RADIUS
- D. SSO
Answer:
D
Explanation:
Single Sign-On (SSO) overrides any other previously configured user authentication method on
FortiSASE, taking precedence for user authentication.
Question 14
What are two advantages of using zero-trust tags? (Choose two.)
- A. Zero-trust tags can determine the security posture of an endpoint.
- B. Zero-trust tags can be assigned to endpoint profiles based on user groups.
- C. Zero-trust tags can be used to allow or deny access to network resources.
- D. Zero-trust tags can help monitor endpoint system resource usage.
Answer:
A,C
Explanation:
Zero-trust tags assess endpoint compliance based on defined posture rules and are used in access
policies to control whether a device is permitted or denied access to specific network resources.
Question 15
Which FortiSASE feature ensures least-privileged user access to corporate applications that are
protected by an on-premises FortiGate device?
- A. secure web gateway (SWG)
- B. zero trust network access (ZTNA)
- C. cloud access security broker (CASB)
- D. remote browser isolation (RBI)
Answer:
B
Explanation:
ZTNA enforces least-privileged access by verifying user identity and device posture before granting
access to specific corporate applications, even when protected by an on-premises FortiGate.