Fortinet fcss efw ad 7 6 practice test
FCSS - Enterprise Firewall 7.6 Administrator
Question 1
A company that acquired multiple branches across different countries needs to install new FortiGate
devices on each of those branches. However, the IT staff lacks sufficient knowledge to implement the
initial configuration on the FortiGate devices.
Which three approaches can the company take to successfully deploy advanced initial configurations
on remote branches? (Choose three.)
- A. Use metadata variables to dynamically assign values according to each FortiGate device.
- B. Use provisioning templates and install configuration settings at the device layer.
- C. Use the Global ADOM to deploy global object configurations to each FortiGate device.
- D. Apply Jinja in the FortiManager scripts for large-scale and advanced deployments.
- E. Add FortiGate devices on FortiManager as model devices, and use ZTP or LTP to connect to FortiGate devices.
Answer:
A, B, E
Explanation:
Use metadata variables to dynamically assign values according to each FortiGate device:
Metadata variables in FortiManager allow device-specific configurations to be dynamically assigned
without manually configuring each FortiGate. This is especially useful when deploying multiple
devices with similar base configurations.
Use provisioning templates and install configuration settings at the device layer:
Provisioning templates in FortiManager provide a structured way to configure FortiGate devices.
These templates can define interfaces, policies, and settings, ensuring that each device is correctly
configured upon deployment.
Add FortiGate devices on FortiManager as model devices, and use ZTP or LTP to connect to FortiGate
devices:
Zero-Touch Provisioning (ZTP) and Local Touch Provisioning (LTP) help automate the deployment of
FortiGate devices. By adding devices as model devices in FortiManager, configurations can be pushed
automatically when devices connect for the first time, reducing manual effort.
Question 2
An administrator is checking an enterprise network and sees a suspicious packet with the MAC
address e0:23:ff:fc:00:86.
What two conclusions can the administrator draw? (Choose two.)
- A. The suspicious packet is related to a cluster that has VDOMs enabled.
- B. The network includes FortiGate devices configured with the FGSP protocol.
- C. The suspicious packet is related to a cluster with a group-id value lower than 255.
- D. The suspicious packet corresponds to port 7 on a FortiGate device.
Answer:
A, C
Explanation:
The MAC address e0:23:ff:fc:00:86 follows the format used in FortiGate High Availability (HA)
clusters. When FortiGate devices are in an HA configuration, they use virtual MAC addresses for
failover and redundancy purposes.
The suspicious packet is related to a cluster that has VDOMs enabled:
FortiGate devices with Virtual Domains (VDOMs) enabled use specific MAC address ranges to
differentiate HA-related traffic. This MAC address is likely part of that mechanism.
The suspicious packet is related to a cluster with a group-id value lower than 255:
FortiGate HA clusters assign virtual MAC addresses based on the group ID. The last octet (00:86)
corresponds to a group ID that is below 255, confirming this option.
Question 3
A company's guest internet policy, operating in proxy mode, blocks access to Artificial Intelligence
Technology sites using FortiGuard. However, a guest user accessed a page in this category using port
8443.
Which configuration changes are required for FortiGate to analyze HTTPS traffic on nonstandard
ports like 8443 when full SSL inspection is active in the guest policy?
- A. Add a URL wildcard domain to the website CA certificate and use it in the SSL/SSH Inspection Profile.
- B. In the Protocol Port Mapping section of the SSL/SSH Inspection Profile, enter 443, 8443 to analyze both standard (443) and non-standard (8443) HTTPS ports.
- C. To analyze nonstandard ports in web filter profiles, use TLSv1.3 in the SSL/SSH Inspection Profile.
- D. Administrators can block traffic on nonstandard ports by enabling the SNI check in the SSL/SSH Inspection Profile.
Answer:
B
Explanation:
When FortiGate is operating in proxy mode with full SSL inspection enabled, it inspects encrypted
HTTPS traffic by default on port 443. However, some websites may use non-standard HTTPS ports
(such as 8443), which FortiGate does not inspect unless explicitly configured.
To ensure that FortiGate inspects HTTPS traffic on port 8443, administrators must manually add port
8443 in the Protocol Port Mapping section of the SSL/SSH Inspection Profile. This allows FortiGate to
treat HTTPS traffic on port 8443 the same as traffic on port 443, enabling proper inspection and
enforcement of FortiGuard category-based web filtering.
Question 4
An administrator needs to install an IPS profile without triggering false positives that can impact
applications and cause problems with the user's normal traffic flow.
Which action can the administrator take to prevent false positives on IPS analysis?
- A. Use the IPS profile extension to select an operating system, protocol, and application for all the network internal services and users to prevent false positives.
- B. Enable Scan Outgoing Connections to avoid clicking suspicious links or attachments that can deliver botnet malware and create false positives.
- C. Use an IPS profile with action monitor, however, the administrator must be aware that this can compromise network integrity.
- D. Install missing or expired SSUTLS certificates on the client PC to prevent expected false positives.
Answer:
A
Explanation:
False positives in Intrusion Prevention System (IPS) analysis can disrupt legitimate traffic and
negatively impact user experience. To reduce false positives while maintaining security,
administrators can:
● Use IPS profile extensions to fine-tune the settings based on the organization's environment.
● Select the correct operating system, protocol, and application types to ensure that IPS signatures
match the network's actual traffic patterns, reducing false positives.
● Customize signature selection based on the network’s specific services, filtering out unnecessary
or irrelevant signatures.
Question 5
Refer to the exhibit, which shows a hub and spokes deployment.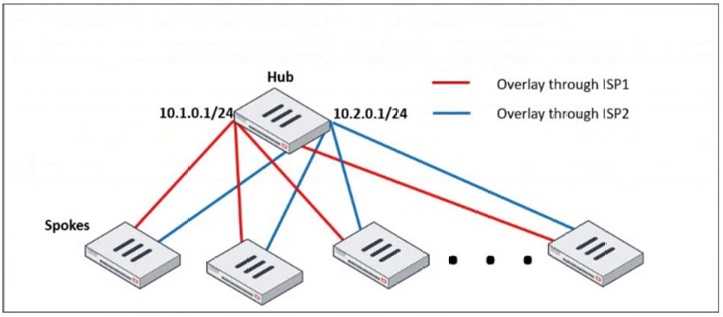
An administrator is deploying several spokes, including the BGP configuration for the spokes to
connect to the hub.
Which two commands allow the administrator to minimize the configuration? (Choose two.)
- A. neighbor-group
- B. route-reflector-client
- C. neighbor-range
- D. ibgp-enforce-multihop
Answer:
A, C
Explanation:
neighbor-group:
● This command is used to group multiple BGP neighbors with the same configuration, reducing
redundant configuration.
● Instead of defining individual BGP settings for each spoke, the administrator can create a
neighbor-group and apply the same policies, reducing manual work.
neighbor-range:
● This command allows the configuration of a range of neighbor IPs dynamically, reducing the need
to manually define each spoke neighbor.
● It automatically adds BGP neighbors that match a given prefix, simplifying deployment.
Question 6
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose
two.)
- A. FortiGate has a predefined list of all IPs and ports for specific applications downloaded from FortiGuard.
- B. The ISDB blocks the IP addresses and ports of an application predefined by FortiGuard.
- C. The ISDB works in proxy mode, allowing the analysis of packets in layers 3 and 4 of the OSI model.
- D. The ISDB limits access by URL and domain.
Answer:
A, B
Explanation:
The Internet Service Database (ISDB) in FortiGate is used to enforce content filtering at Layer 3
(Network Layer) and Layer 4 (Transport Layer) of the OSI model by identifying applications based on
their predefined IP addresses and ports.
FortiGate has a predefined list of all IPs and ports for specific applications downloaded from
FortiGuard:
● FortiGate retrieves and updates a predefined list of IPs and ports for different internet services
from FortiGuard.
● This allows FortiGate to block specific services at Layer 3 and Layer 4 without requiring deep
packet inspection.
The ISDB blocks the IP addresses and ports of an application predefined by FortiGuard:
● ISDB works by matching traffic to known IP addresses and ports of categorized services.
● When an application or service is blocked, FortiGate prevents communication by denying traffic
based on its destination IP and port number.
Question 7
Refer to the exhibits.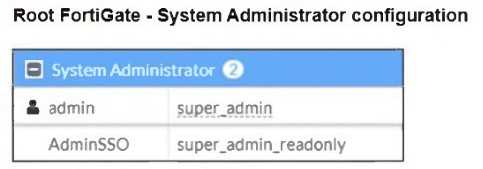

The Administrators section of a root FortiGate device and the Security Fabric Settings section of a
downstream FortiGate device are shown.
When prompted to sign in with Security Fabric in the downstream FortiGate device, a user enters the
AdminSSO credentials.
What is the next status for the user?
- A. The user is prompted to create an SSO administrator account for AdminSSO.
- B. The user receives an authentication failure message.
- C. The user accesses the downstream FortiGate with super_admin_readonly privileges.
- D. The user accesses the downstream FortiGate with super_admin privileges.
Answer:
C
Explanation:
From the Root FortiGate - System Administrator Configuration exhibit:
● The AdminSSO account has the super_admin_readonly role.
From the Downstream FortiGate - Security Fabric Settings exhibit:
● The Security Fabric role is set to Join Existing Fabric, meaning it will authenticate with the root
FortiGate.
● SAML Single Sign-On (SSO) is enabled, and the default admin profile is set to
super_admin_readonly.
When the AdminSSO user logs into the downstream FortiGate using SSO, the authentication request
is sent to the root FortiGate, where AdminSSO has super_admin_readonly permissions. Since the
downstream FortiGate inherits this permission through the Security Fabric configuration, the user
will be granted super_admin_readonly access.
Question 8
A user reports that their computer was infected with malware after accessing a secured HTTPS
website. However, when the administrator checks the FortiGate logs, they do not see that the
website was detected as insecure despite having an SSL certificate and correct profiles applied on the
policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
- A. The administrator must enable reputable websites to allow only SSL/TLS websites rated by FortiGuard web filter.
- B. The administrator must enable URL extraction from SNI on the SSL certificate inspection to ensure the TLS three-way handshake is correctly analyzed by FortiGate.
- C. The administrator must enable DNS over TLS to protect against fake Server Name Indication (SNI) that cannot be analyzed in common DNS requests on HTTPS websites.
- D. The administrator must enable full SSL inspection in the SSL/SSH Inspection Profile to decrypt packets and ensure they are analyzed as expected.
Answer:
D
Explanation:
FortiGate, like other security appliances, cannot analyze encrypted HTTPS traffic unless it decrypts it
first. If only certificate inspection is enabled, FortiGate can see the certificate details (such as the
domain and issuer) but cannot inspect the actual web content.
To fully analyze the traffic and detect potential malware threats:
● Full SSL inspection (Deep Packet Inspection) must be enabled in the SSL/SSH Inspection Profile.
● This allows FortiGate to decrypt the HTTPS traffic, inspect the content, and then re-encrypt it
before forwarding it to the user.
● Without full SSL inspection, threats embedded in encrypted traffic may go undetected.
Question 9
Refer to the exhibit, which shows an ADVPN network.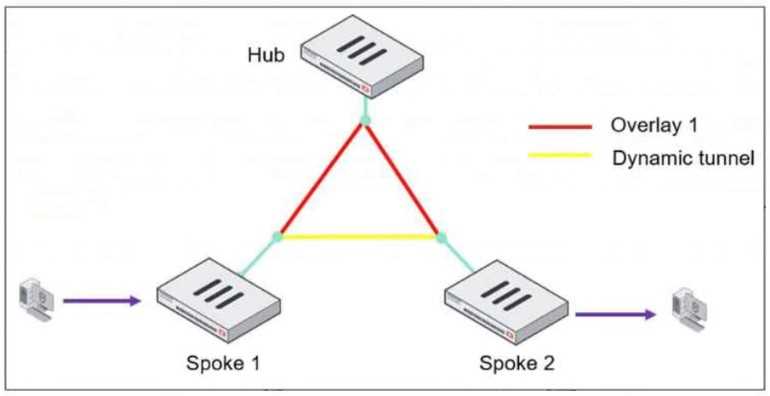
The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?
- A. Shortcut query
- B. Shortcut offer
- C. Shortcut reply
- D. Shortcut forward
Answer:
B
Explanation:
In an ADVPN (Auto-Discovery VPN) network, a dynamic VPN tunnel is established on-demand
between spokes to optimize traffic flow and reduce latency.
Process:
1. Traffic Initiation:
A client behind Spoke-1 sends traffic to a device behind Spoke-2.
The traffic initially flows through the hub, following the pre-established overlay tunnel.
2. Hub Detection:
The hub detects that Spoke-1 is communicating with Spoke-2 and determines that a direct shortcut
tunnel between the spokes can optimize the connection.
3. Shortcut Offer:
The hub sends a "Shortcut Offer" message to Spoke-1, informing it that a direct dynamic tunnel to
Spoke-2 is possible.
4. Tunnel Establishment:
Spoke-1 and Spoke-2 then negotiate and establish a direct IPsec tunnel for communication.
Question 10
What is the initial step performed by FortiGate when handling the first packets of a session?
- A. Installation of the session key in the network processor (NP)
- B. Data encryption and decryption
- C. Security inspections such as ACL, HPE, and IP integrity header checking
- D. Offloading the packets directly to the content processor (CP)
Answer:
C
Explanation:
When FortiGate processes the first packets of a session, it follows a sequence of steps to determine
how the traffic should be handled before establishing a session. The initial step involves:
● Access Control List (ACL) checks: Determines if the traffic should be allowed or blocked based on
predefined security rules.
● Hardware Packet Engine (HPE) inspections: Ensures that packet headers are valid and comply with
protocol standards.
● IP Integrity Header Checking: Verifies if the IP headers are intact and not malformed or spoofed.
Once these security inspections are completed and the session is validated, FortiGate then installs
the session in hardware (if offloading is enabled) or processes it in software.
Question 11
An administrator applied a block-all IPS profile for client and server targets to secure the server, but
the database team reported the application stopped working immediately after.
How can an administrator apply IPS in a way that ensures it does not disrupt existing applications in
the network?
- A. Use an IPS profile with all signatures in monitor mode and verify patterns before blocking.
- B. Limit the IPS profile to server targets only to avoid blocking connections from the server to clients.
- C. Select flow mode in the IPS profile to accurately analyze application patterns.
- D. Set the IPS profile signature action to default to discard all possible false positives.
Answer:
A
Explanation:
Applying an aggressive IPS profile without prior testing can disrupt legitimate applications by
incorrectly identifying normal traffic as malicious. To prevent disruptions while still monitoring for
threats:
● Enable IPS in "Monitor Mode" first:
● This allows FortiGate to log and analyze potential threats without actively blocking traffic.
● Administrators can review logs and fine-tune IPS signatures to minimize false positives before
switching to blocking mode.
● Verify and adjust signature patterns:
● Some signatures might trigger unnecessary blocks for legitimate application traffic.
● By analyzing logs, administrators can disable or modify specific rules causing false positives.
Question 12
An administrator is extensively using VXLAN on FortiGate.
Which specialized acceleration hardware does FortiGate need to improve its performance?
- A. NP7
- B. SP5
- C. СР9
- D. NTurbo
Answer:
A
Explanation:
VXLAN (Virtual Extensible LAN) is an overlay network technology that extends Layer 2 networks over
Layer 3 infrastructure. When VXLAN is used extensively on FortiGate, hardware acceleration is crucial
for maintaining performance.
● NP7 (Network Processor 7) is Fortinet’s latest network processor designed to accelerate high-
performance networking features, including:
● VXLAN encapsulation/decapsulation
● IPsec VPN offloading
● Firewall policy enforcement
● Advanced threat protection at wire speed
NP7 significantly reduces latency and improves throughput when handling VXLAN traffic, making it
the best choice for large-scale VXLAN deployments.
Question 13
Refer to the exhibit, which shows a partial enterprise network.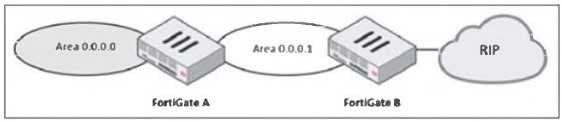
An administrator would like the area 0.0.0.0 to detect the external network.
What must the administrator configure?
- A. Enable RIP redistribution on FortiGate B.
- B. Configure a distribute-route-map-in on FortiGate B.
- C. Configure a virtual link between FortiGate A and B.
- D. Set the area 0.0.0.l type to stub on FortiGate A and B.
Answer:
A
Explanation:
The diagram shows a multi-area OSPF network where:
● FortiGate A is in OSPF Area 0 (Backbone area).
● FortiGate B is in OSPF Area 0.0.0.1 and is connected to an RIP network.
To ensure that OSPF Area 0 (0.0.0.0) learns routes from the external RIP network, FortiGate B must
redistribute RIP routes into OSPF.
Steps to achieve this:
1. Enable route redistribution on FortiGate B to inject RIP-learned routes into OSPF.
2. This allows OSPF Area 0.0.0.1 to forward RIP routes to OSPF Area 0 (0.0.0.0), making the external
network visible.
Question 14
Refer to the exhibit, which shows the ADVPN network topology and partial BGP configuration.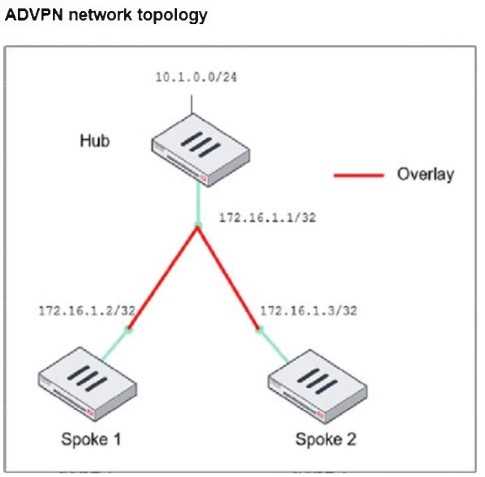

Which two parameters must an administrator configure in the config neighbor range for spokes
shown in the exhibit? (Choose two.)
- A. set max-neighbor-num 2
- B. set neighbor-group advpn
- C. set route-reflector-client enable
- D. set prefix 172.16.1.0 255.255.255.0
Answer:
B, D
Explanation:
In the given ADVPN (Auto-Discovery VPN) topology, BGP is being used to dynamically establish
routes between spokes. The neighbor-range configuration is crucial for simplifying BGP peer setup by
automatically assigning neighbors based on their IP range.
set neighbor-group advpn
● The neighbor-group parameter is used to apply pre-defined settings (such as AS number) to
dynamically discovered BGP neighbors.
● The advpn neighbor-group is already defined in the configuration, and assigning it to the neighbor-
range ensures consistent BGP settings for all spoke neighbors.
set prefix 172.16.1.0 255.255.255.0
● This command allows dynamic BGP peer discovery by defining a range of potential neighbor IPs
(172.16.1.1 - 172.16.1.255).
● Since each spoke has a unique /32 IP within this subnet, this ensures that any spoke within the
172.16.1.0/24 range can automatically establish a BGP session with the hub.
Question 15
Which two statements about IKEv2 are true if an administrator decides to implement IKEv2 in the
VPN topology? (Choose two.)
- A. It includes stronger Diffie-Hellman (DH) groups, such as Elliptic Curve (ECP) groups.
- B. It supports interoperability with devices using IKEv1.
- C. It exchanges a minimum of two messages to establish a secure tunnel.
- D. It supports the extensible authentication protocol (EAP).
Answer:
A, D
Explanation:
IKEv2 (Internet Key Exchange version 2) is an improvement over IKEv1, offering enhanced security,
efficiency, and flexibility in VPN configurations.
It includes stronger Diffie-Hellman (DH) groups, such as Elliptic Curve (ECP) groups.
IKEv2 supports stronger cryptographic algorithms, including Elliptic Curve Diffie-Hellman (ECDH)
groups such as ECP256 and ECP384, providing improved security compared to IKEv1.
It supports the extensible authentication protocol (EAP).
IKEv2 natively supports EAP authentication, which allows integration with external authentication
mechanisms such as RADIUS, certificates, and smart cards. This is particularly useful for remote
access VPNs where user authentication must be flexible and secure.