Fortinet fcss cds ar 7 6 practice test
FCSS - Public Cloud Security 7.6 Architect
Question 1
An administrator would like to use FortiCNP to keep track of sensitive data files located in the
Amazon Web Services (AWS) S3 bucket and protect it from malware.
Which FortiCNP feature should the administrator use?
- A. FortiCNP Threat Detection policies
- B. FortiCNP Risk Management policies
- C. FortiCNP Data Scan policies
- D. FortiCNP Compliance policies
Answer:
C
Question 2
You are using Ansible to modify the configuration of several FortiGate VMs.
What is the minimum number of files you need to create, and in which file should you configure the
target FortiGate IP addresses?
- A. One playbook file for each target and the required tasks, and one inventory file.
- B. One .yaml file with the target IP addresses, and one playbook file with the tasks.
- C. One inventory file for each target device, and one playbook file.
- D. One text file for all target devices, and one playbook file.
Answer:
B
Question 3
Refer to the exhibit.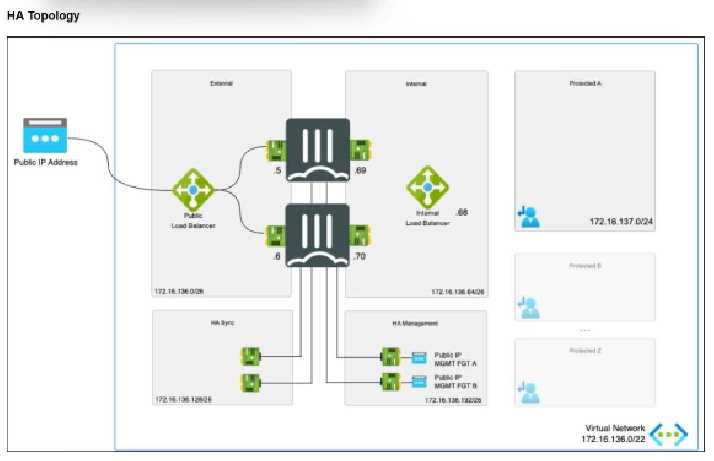
Refer to the exhibit.
The exhibit shows an active-passive high availability FortiGate pair with external and internal Azure
load balancers.
There is no SDN connector used in this solution.
Which configuration must the administrator implement on each FortiGate?
- A. Single BGP route to Azure probe IP address.
- B. One static route to Azure Lambda IP address.
- C. Two static routes to Azure probe IP address.
- D. Two BGP routes to Azure probe IP address.
Answer:
C
Question 4
Your DevOps team is evaluating different Infrastructure as Code (IaC) solutions for deploying complex
Azure environments.
What is an advantage of choosing Azure Bicep over other IaC tools available?
- A. Azure Bicep generates deployment logs that are optimized to improve error handling.
- B. Azure Bicep provides immediate support for all Azure services, including those in preview.
- C. Azure Bicep requires less frequent schema updates than Azure Resource Manager (ARM) templates.
- D. Azure Bicep can reduce deployment costs by limiting resource utilization during testing.
Answer:
B
Question 5
You must add an Amazon Web Services (AWS) network access list (NACL) rule to allow SSH traffic to a
subnet for temporary testing purposes. When you review the current inbound and outbound NACL
rules, you notice that the rules with number 5 deny SSH and Telnet traffic to the subnet.
What can you do to allow SSH traffic?
- A. You do not have to create any NACL rules because the default security group rule automatically allows SSH traffic to the subnet.
- B. You must create a new allow SSH rule anywhere in the network ACL rule base to allow SSH traffic.
- C. You must create two new allow SSH rules, each with a number bigger than 5.
- D. You must create two new allow SSH rules, each with a number smaller than 5.
Answer:
D
Question 6
Refer to the exhibit.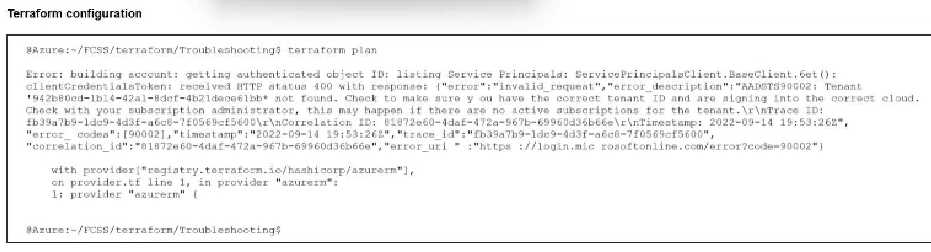
Refer to the exhibit.
After the initial Terraform configuration in Microsoft Azure, the terraform plan command is run.
Which two statements about running the terraform plan command are true? (Choose two.)
- A. The terraform plan command will deploy the rest of the resources except the service principal details.
- B. You cannot run the terraform apply command before the terraform plan command.
- C. The terraform plan command makes Terraform do a dry run.
- D. You must run the terraform init command once, before the terraform plan command.
Answer:
C, D
Question 7
A network security administrator is searching for a solution to secure traffic going in and out of the
container infrastructure.
In which two ways can Fortinet container security help secure container infrastructures? (Choose
two.)
- A. FortiGate NGFW can inspect north-south container traffic with label-aware policies.
- B. FortiGate NGFW and FortiWeb can be used to secure container traffic.
- C. FortiGate NGFW can connect to the worker nodes and protect the containers.
- D. FortiGate NGFW can be placed between each application container for north-south traffic inspection.
Answer:
A, B
Question 8
An organization is deploying FortiDevSec to enhance security for containerized applications, and they
need to ensure containers are monitored for suspicious behavior at runtime.
Which FortiDevSec feature is best for detecting runtime threats?
- A. FortiDevSec Software Composition Analysis (SCA)
- B. FortiDevSec Static Application Security Testing (SAST)
- C. FortiDevSec Dynamic Application Security Testing (DAST)
- D. FortiDevSec Container Scanner
Answer:
D
Question 9
Refer to the exhibit.
You are troubleshooting a Microsoft Azure SDN connector issue on your FortiGate VM in Azure.
Which command can you use to examine details about API calls sent by the connector?
- A. diag debug application cloud-connector -l
- B. diag test application azd 1
- C. diag debug application azd 1
- D. get system sdn-connector
Answer:
C
Question 10
As part of your organization’s monitoring plan, you have been tasked with obtaining and analyzing
detailed information about the traffic sourced at one of your FortiGate EC2 instances.
What can you do to achieve this goal?
- A. Use AWS CloudTrail to capture and then examine traffic from the EC2 instance.
- B. Create a virtual public cloud (VPC) flow log at the network interface level for the EC2 instance.
- C. Add the EC2 instance as a target in CloudWatch to collect its traffic logs.
- D. Configure a network access analyzer scope with the EC2 instance as a match finding.
Answer:
B
Question 11
Refer to the exhibit.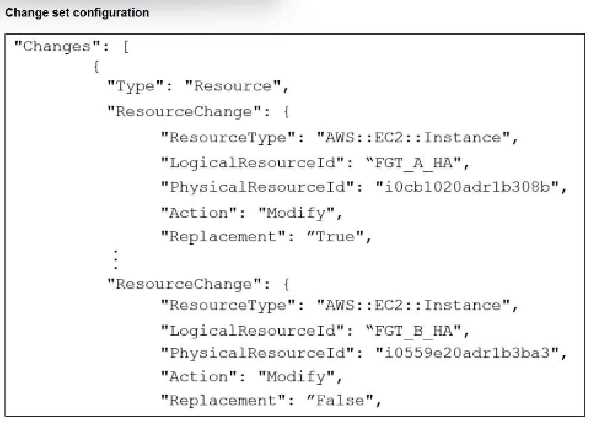
Refer to the exhibit.
You are managing an active-passive FortiGate HA cluster in AWS that was deployed using
CloudFormation. You have created a change set to examine the effects of some proposed changes to
the current infrastructure. The exhibit shows some sections of the change set.
What will happen if you apply these changes?
- A. This deployment can be done without any traffic interruption.
- B. Both FortiGate VMs will get a new PhysicalResourceId.
- C. The updated FortiGate VMs will not have the latest configuration changes.
- D. CloudFormation checks if you will surpass your account quota.
Answer:
B
Question 12
Refer to the exhibit.
What is the purpose of this section of an Azure Bicep file?
- A. To restrict which FortiOS versions are accepted for deployment
- B. To indicate the correct FortiOS upgrade path after deployment
- C. To add a comment with the permitted FortiOS versions that can be deployed
- D. To document the FortiOS versions in the resulting topology
Answer:
A
Question 13
In an SD-WAN TGW Connect topology, which three initial steps are mandatory when routing traffic
from a spoke VPC to a security VPC through a Transit Gateway? (Choose three.)
- A. From the security VPC TGW subnet routing table, point 0.0.0.0/0 traffic to the FortiGate internal port.
- B. From the security VPC TGW subnet routing table, point 0.0.0.0/0 traffic to the TGW.
- C. From both spoke VPCs and the security VPC, point 0.0.0.0/0 traffic to the Internet Gateway.
- D. From the security VPC FortiGate internal subnet routing table, point 0.0.0.0/0 traffic to the TGW.
- E. From the spoke VPC internal routing table, point 0.0.0.0/0 traffic to the TGW.
Answer:
A, D, E
Question 14
An AWS administrator must ensure that each member of the cloud deployment team has the correct
permissions to deploy and manage resources using CloudFormation. The administrator is researching
which tasks must be executed with CloudFormation and therefore require CloudFormation
permissions.
Which task is run using CloudFormation?
- A. Deploying a new pod with a service in an Elastic Kubernetes Service (EKS) cluster using the kubectl command
- B. Installing a Helm chart to deploy a FortiWeb ingress controller in an EKS cluster
- C. Creating an EKS cluster with the eksctl create cluster command
- D. Changing the number of nodes in an EKS cluster from AWS CloudShell
Answer:
D
Question 15
An administrator decides to use the Use managed identity option on the FortiGate SDN connector
with Microsoft Azure. However, the SDN connector is failing on the connection.
What must the administrator do to correct this issue?
- A. Make sure to add the Client Secret on the FortiGate side of the configuration.
- B. Make sure to add the Tenant ID on the FortiGate side of the configuration.
- C. Make sure to enable the system-assigned managed identity on Azure.
- D. Make sure to set the type to system managed identity on FortiGate SDN connector settings.
Answer:
C