Fortinet fcp fsm an 7 2 practice test
FCP - FortiSIEM 7.2 Analyst
Question 1
Which statement about thresholds is true?
- A. FortiSIEM uses fixed, hardcoded global and device thresholds for all performance metrics.
- B. FortiSIEM uses only device thresholds for security metrics.
- C. FortiSIEM uses global and per device thresholds for performance metrics.
- D. FortiSIEM uses only global thresholds for performance metrics.
Answer:
C
Explanation:
FortiSIEM evaluates performance metrics against both global thresholds, which apply system-wide,
and per-device thresholds, which can be customized for individual devices. This dual approach allows
flexibility in monitoring while ensuring consistent baseline alerting.
Question 2
Which running mode takes the most time to perform machine learning tasks?
- A. Local auto
- B. Local
- C. Forecasting
- D. Regression
Answer:
B
Explanation:
In Local mode, FortiSIEM performs machine learning tasks using the full dataset without optimization
shortcuts, making it the most time-consuming mode compared to Local Auto, Forecasting, or
Regression.
Question 3
Refer to the exhibit.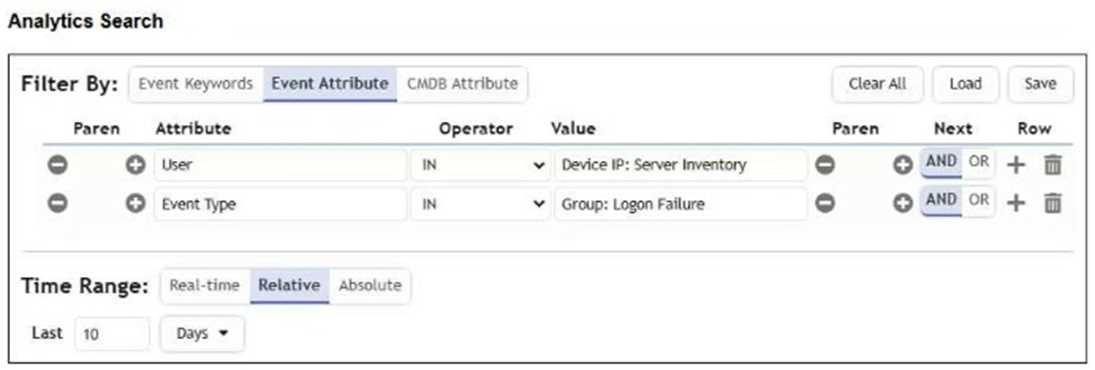
The analyst is troubleshooting the analytics query shown in the exhibit.
Why is this search not producing any results?
- A. The Time Range is set incorrectly.
- B. The inner and outer nested query attribute types do not match.
- C. You cannot reference User and Event Type attributes in the same search.
- D. The Boolean operator is wrong between the attributes.
Answer:
B
Explanation:
The issue is that the "User" attribute is incorrectly assigned a Device IP group value, which is a
mismatch of attribute types. "User" expects a user name or identity, not a device IP group. This
mismatch between the attribute type and the provided value causes the search to return no results.
Question 4
Refer to the exhibit.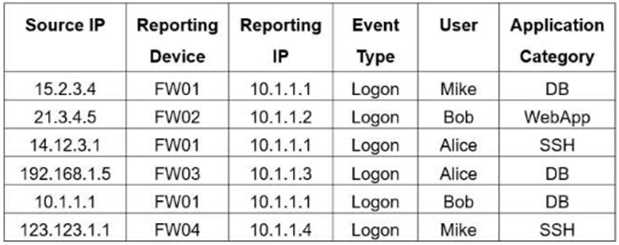
If you group the events by Reporting Device, Reporting IP, and Application Category, how many
results will FortiSIEM display?
- A. Four
- B. Five
- C. One
- D. Six
- E. Two
Answer:
B
Explanation:
Grouping by Reporting Device, Reporting IP, and Application Category yields five unique tuples:
(FW01, 10.1.1.1, DB), (FW02, 10.1.1.2, WebApp), (FW01, 10.1.1.1, SSH), (FW03, 10.1.1.3, DB), and
(FW04, 10.1.1.4, SSH).
Question 5
Which analytics search can be used to apply a user and entity behavior analytics (UEBA) tag to an
event for a failed login by the user JSmith?
- A. User = smith
- B. Username NOT END WITH jsmith
- C. User IS jsmith
- D. Username CONTAIN smit
Answer:
C
Explanation:
The correct syntax to match an exact username in FortiSIEM analytics search is User IS jsmith. This
ensures that the UEBA tag is applied only when the event is specifically tied to the user "jsmith",
which is required for accurate behavioral analytics.
Question 6
Refer to the exhibit.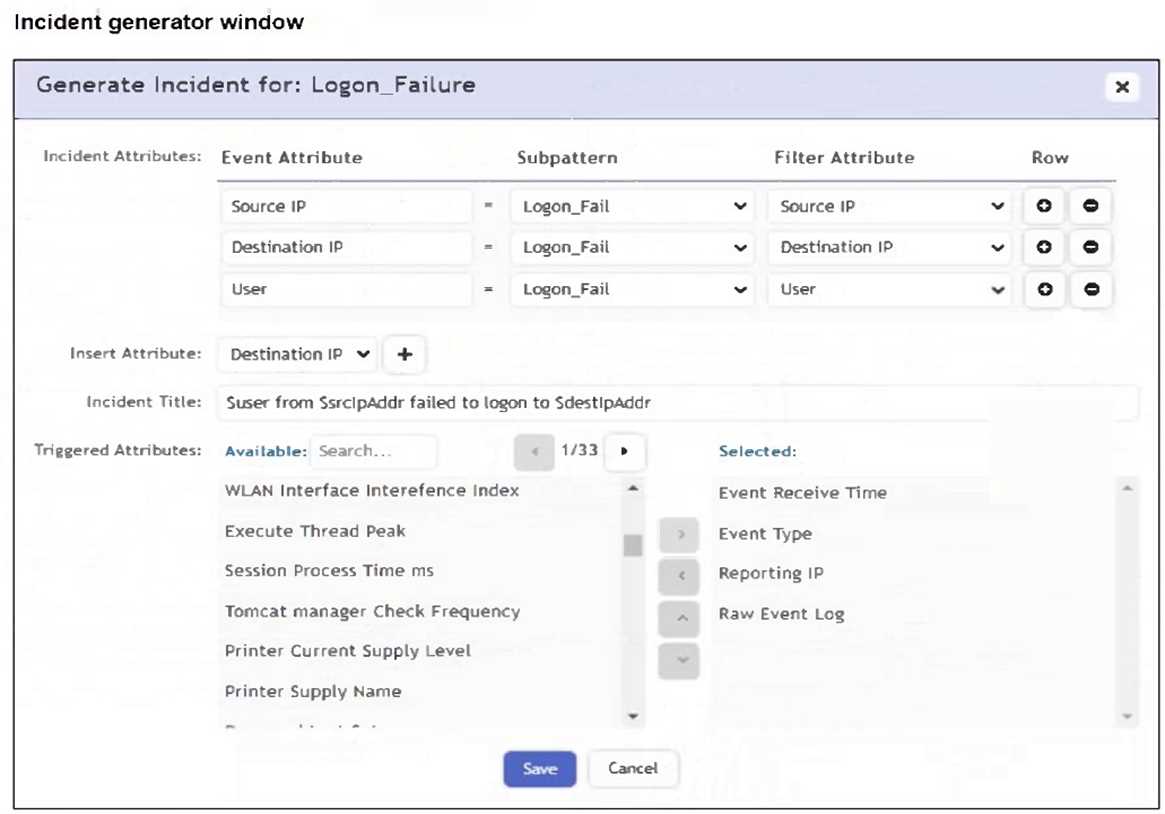
An analyst is trying to generate an incident with a title that includes the Source IP, Destination IP,
User, and Destination Host Name. They are unable to add a Destination Host Name as an incident
attribute.
What must be changed to allow the analyst to select Destination Host Name as an attribute?
- A. The Destination Host Name must be selected as a Triggered Attribute.
- B. The Destination Host Name must be set as an aggregate item in a subpattern.
- C. The Destination Host Name must be added as an Event type in the FortiSIEM.
- D. The Destination IP Event Attribute must be removed.
Answer:
A
Explanation:
For an attribute like Destination Host Name to be used in the incident title, it must first be included in
the Triggered Attributes list. Only attributes listed there are available for substitution in the title
template (e.g., $destIpAddr, $srcIpAddr).
Question 7
Refer to the exhibit.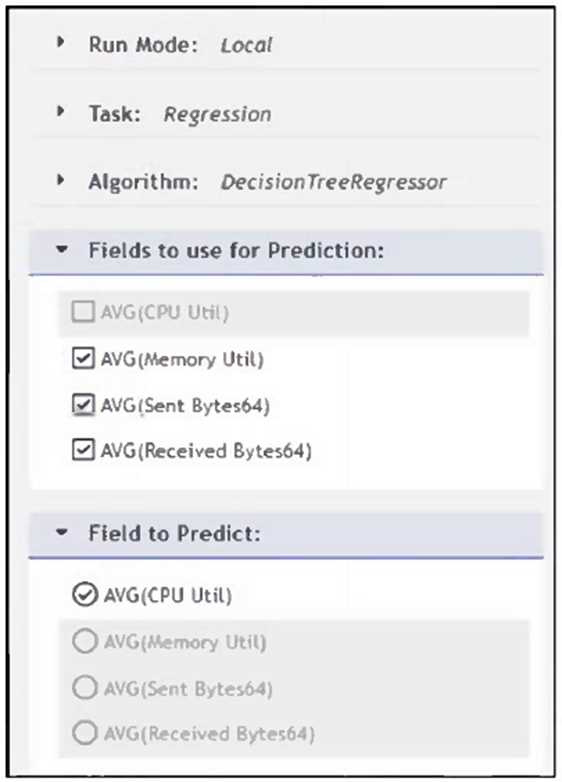
What will happen when a device being analyzed by the machine learning configuration shown in the
exhibit has a consistently high memory utilization?
- A. FortiSIEM will update the regression tables for memory utilization, and average sent and received bytes.
- B. FortiSIEM will trigger an incident for high memory utilization.
- C. FortiSIEM will lower the CPU utilization trigger requirement for CPU utilization.
- D. FortiSIEM will update the model with a higher memory utilization average value.
Answer:
D
Explanation:
In the configuration shown, FortiSIEM uses Memory Util, Sent Bytes, and Received Bytes as input
features to predict CPU Utilization via a regression model. If a device shows consistently high
memory utilization, the model will incorporate that into its training data and update itself with a
higher average value for memory utilization, influencing future CPU utilization predictions.
Question 8
Which two settings must you configure to allow FortiSIEM to apply tags to devices in FortiClient
EMS? (Choose two.)
- A. FortiEMS API credentials defined on FortiSIEM
- B. Remediation script configured
- C. ZTNA tags defined on FortiSIEM
- D. FortiSIEM API credentials defined on FortiEMS\
Answer:
A, D
Explanation:
To allow FortiSIEM to apply tags to devices in FortiClient EMS, FortiEMS API credentials must be
defined on FortiSIEM to enable communication with EMS, and FortiSIEM API credentials must be
defined on FortiEMS to allow EMS to accept tagging instructions from FortiSIEM. This bidirectional
API trust is essential for tag application.
Question 9
What are two required components of a rule? (Choose two.)
- A. Exception policy
- B. Subpattern
- C. Detection Technology
- D. Clear policy
Answer:
B, C
Explanation:
A Subpattern defines the specific conditions or event patterns the rule is designed to detect, and the
Detection Technology specifies the type of detection logic (e.g., real-time, historical). Both are
essential for a rule to function in FortiSIEM.
Question 10
Refer to the exhibit.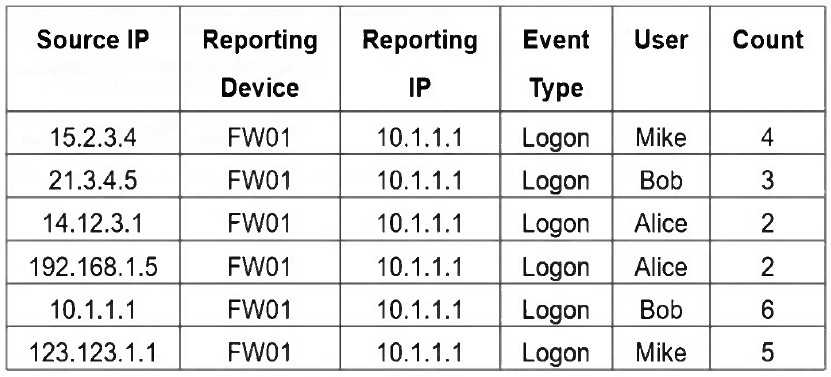
If you group the events by User and Count attributes, how many results will FortiSIEM display?
- A. Two
- B. Six
- C. Three
- D. Five
- E. One
Answer:
D
Explanation:
Grouping by User and Count yields five unique pairs: (Mike,4), (Bob,3), (Alice,2), (Bob,6), (Mike,5).
Question 11
Refer to the exhibit.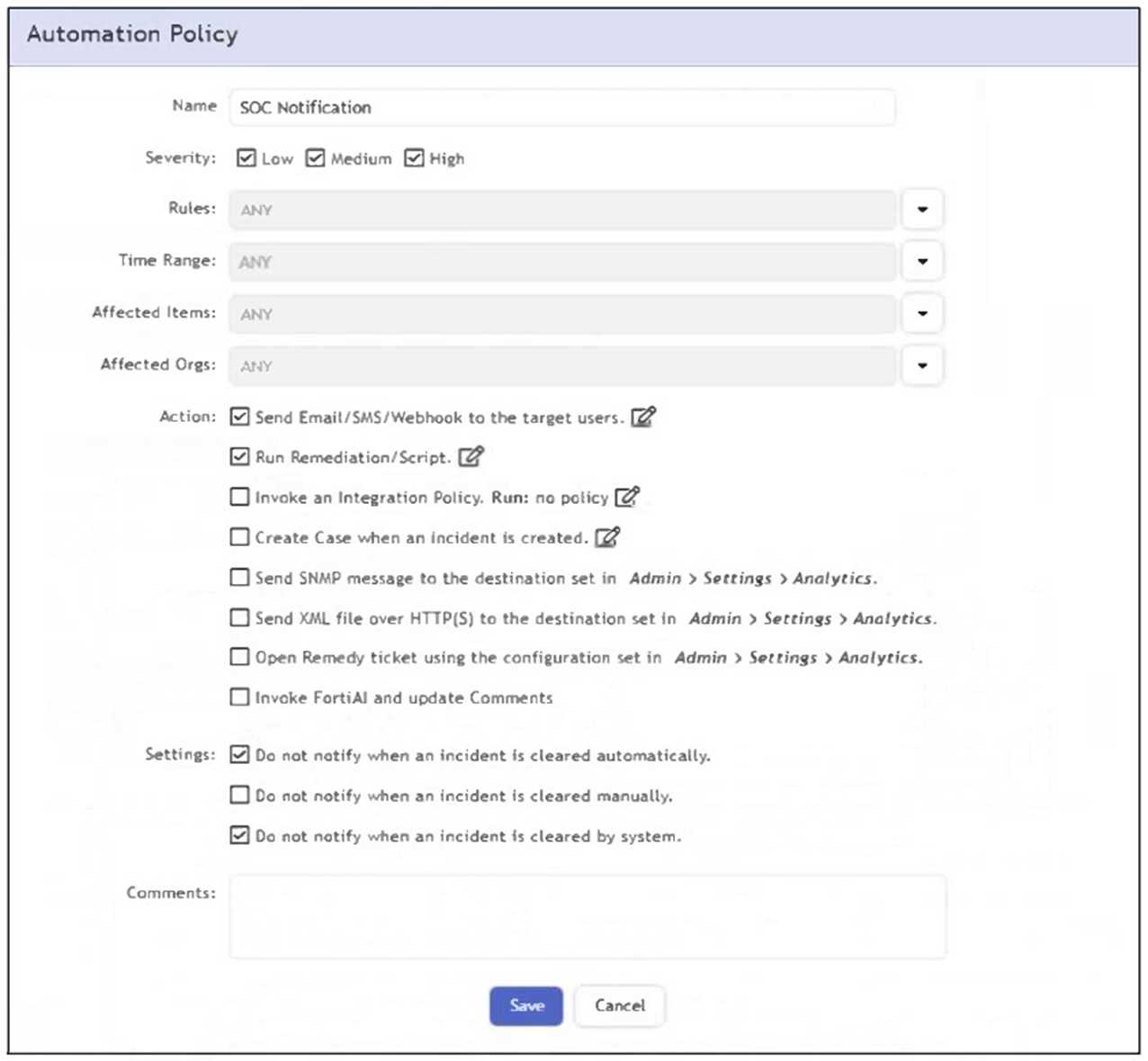
What happens when an analyst clears an incident generated by a rule containing the automation
policy shown in the exhibit?
- A. No notification is sent.
- B. An email is sent to the SOC manager.
- C. The remediation script is run.
- D. A notification is sent to the SOC manager dashboard.
Answer:
A
Explanation:
The automation policy has the option "Do not notify when an incident is cleared manually" enabled.
Therefore, when an analyst manually clears an incident, no notification or automation action is
triggered.
Question 12
Refer to the exhibit.
Which value would you expect the FortiSIEM parser to use to populate the Application Name field?
- A. applist
- B. Network.Service
- C. SSL
- D. wan1
Answer:
C
Explanation:
The Application Name field in FortiSIEM is typically populated using the value of the app field in the
raw log. In this event, app="SSL", so "SSL" is the expected application name parsed by FortiSIEM.
Question 13
Refer to the exhibit.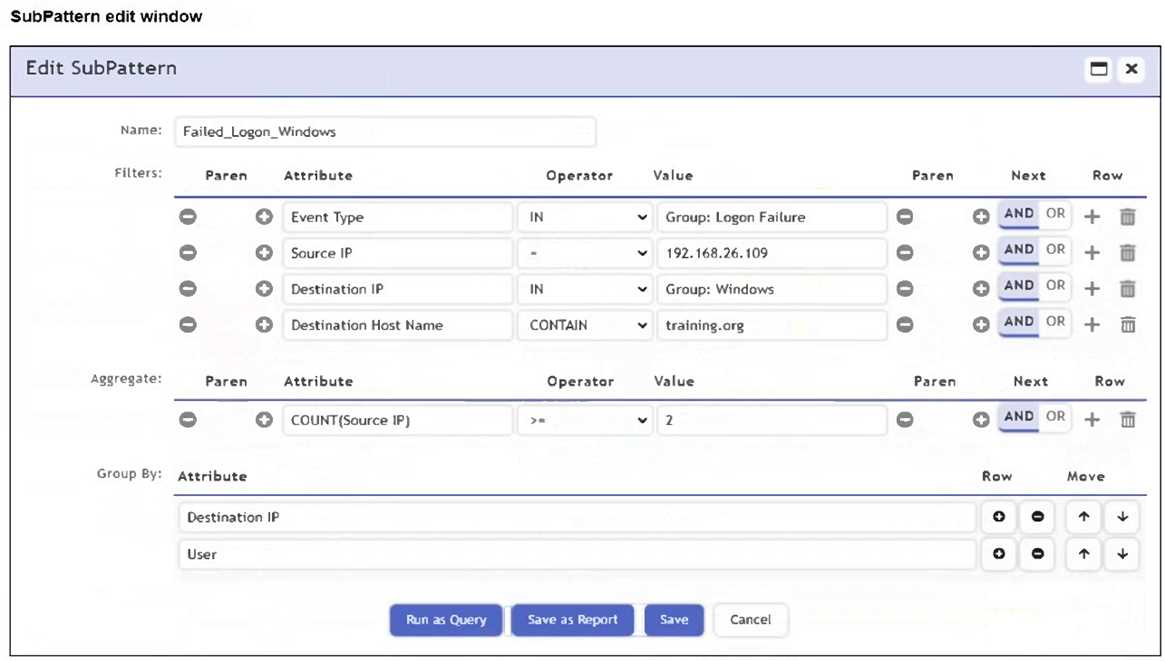
An analyst is troubleshooting the rule shown in the exhibit. It is not generating any incidents, but the
filter parameters are generating events on the Analytics tab.
What is wrong with the rule conditions?
- A. The Event Type refers to a CMDB lookup and should be an Event lookup.
- B. The Destination Host Name value is not fully qualified.
- C. The Group By attributes restricts which events are counted.
- D. The Aggregate attribute is too restrictive.
Answer:
C
Explanation:
The Group By attributes - Destination IP and User - cause the aggregation (COUNT(Source IP) >= 2)
to apply within each unique combination of those groupings. This restricts the count calculation and
can prevent the rule from triggering incidents, even if matching events exist in the Analytics tab.
Question 14
Refer to the exhibit.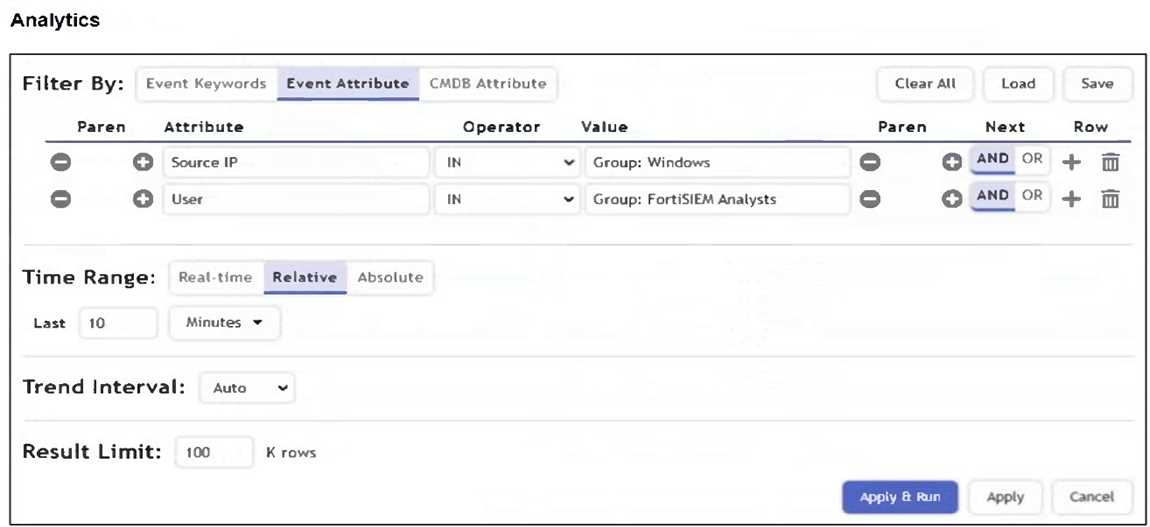
What is the Group: FortiSIEM Analysts value referring to?
- A. FortiSIEM organization group
- B. LDAP user group
- C. CMDB user group
- D. Windows Active Directory user group
Answer:
C
Explanation:
In FortiSIEM, the value Group: FortiSIEM Analysts under the User attribute refers to a CMDB user
group. These groups are defined within FortiSIEM's CMDB and used to logically organize users for
analytics, correlation rules, and reporting.
Question 15
Refer to the exhibit.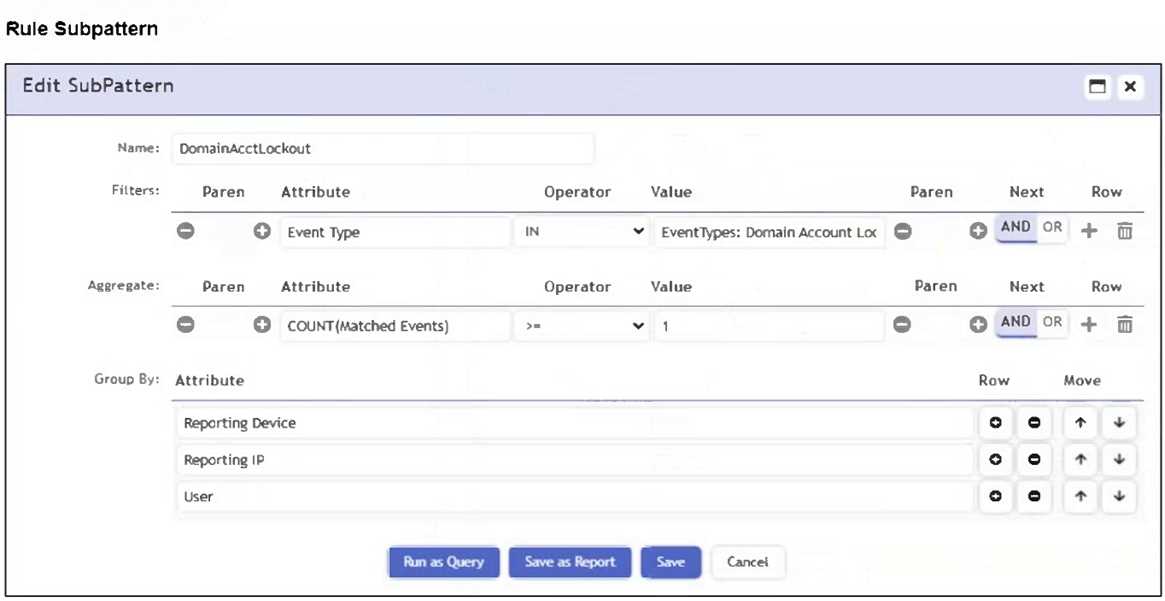
Which section contains the subpattern configuration that determines how many matching events are
needed to trigger the rule?
- A. Aggregate
- B. Group By
- C. Actions
- D. Filters
Answer:
A
Explanation:
The Aggregate section contains the condition COUNT(Matched Events) >= 1, which defines how
many events must match the filter criteria for the rule to trigger. This is the subpattern configuration
that determines the event threshold.