Fortinet fcp fgt ad 7 6 practice test
FCP - FortiGate 7.6 Administrator
Question 1
An administrator wants to configure dead peer detection (DPD) on IPsec VPN for detecting dead
tunnels. The requirement is that FortiGate sends DPD probes only when there is no inbound traffic.
Which DPD mode on FortiGate meets this requirement?
- A. Enabled
- B. On Idle
- C. Disabled
- D. On Demand
Answer:
A
Explanation:
The "On Idle" DPD mode configures FortiGate to send DPD probes only when no inbound traffic is
detected, meeting the requirement to send probes only when the tunnel is idle.
Question 2
Which two statements about equal-cost multi-path (ECMP) configuration on FortiGate are true?
(Choose two.)
- A. If SD-WAN is disabled, you can configure the parameter v4-ecmp-mode to volume-based.
- B. If SD-WAN is enabled, you can configure routes with unequal distance and priority values to be part of ECMP.
- C. If SD-WAN is disabled, you configure the load balancing algorithm in config system settings.
- D. If SD-WAN is enabled, you control the load balancing algorithm with the parameter load-balance- mode.
Answer:
A, D
Explanation:
When SD-WAN is disabled, FortiGate supports volume-based ECMP mode via the v4-ecmp-mode
parameter.
When SD-WAN is enabled, the load balancing algorithm is controlled by the load-balance-mode
parameter within the SD-WAN configuration.
Question 3
You have created a web filter profile named restrict_media-profile with a daily category usage quota.
When you are adding the profile to the firewall policy, the restrict_media-profile is not listed in the
available web profile drop down.
What could be the reason?
- A. The firewall policy is in no-inspection mode instead of deep-inspection.
- B. The inspection mode in the firewall policy is not matching with web filter profile feature set.
- C. The web filter profile is already referenced in another firewall policy.
- D. The naming convention used in the web filter profile is restricting it in the firewall policy.
Answer:
B
Explanation:
Web filter profiles with category usage quotas require the firewall policy to be in proxy-based (deep)
inspection mode; if the inspection mode does not match this requirement, the profile will not appear
in the drop-down list.
Question 4
Refer to the exhibit.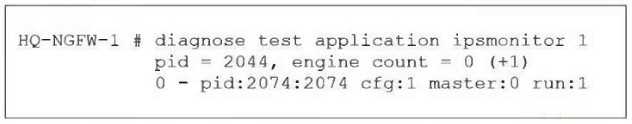
As an administrator you have created an IPS profile, but it is not performing as expected. While
testing you got the output as shown in the exhibit.
What could be the possible reason of the diagnose output shown in the exhibit?
- A. There is a no firewall policy configured with an IPS security profile.
- B. FortiGate entered into IPS fail open state.
- C. Administrator entered the command diagnose test application ipsmonitor 5.
- D. Administrator entered the command diagnose test application ipsmonitor 99.
Answer:
A
Explanation:
The output shows the IPS engine count as 0, indicating no active IPS engines are running. This
typically means no firewall policy is referencing the IPS security profile, so the IPS profile is not being
applied or triggered.
Question 5
Refer to the exhibit.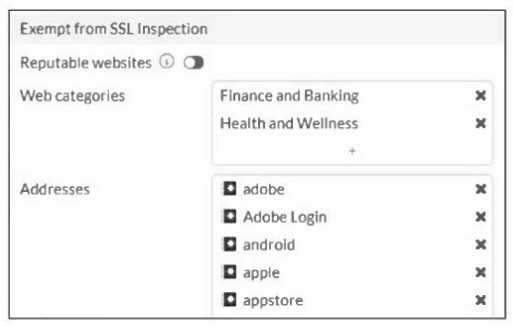
The predefined deep-inspection and custom-deep-inspection profiles exclude some web categories
from SSL inspection, as shown in the exhibit.
For which two reasons are these web categories exempted? (Choose two.)
- A. The FortiGate temporary certificate denies the browser’s access to websites that use HTTP Strict Transport Security.
- B. These websites are in an allowlist of reputable domain names maintained by FortiGuard.
- C. The resources utilization is optimized because these websites are in the trusted domain list on FortiGate.
- D. The legal regulation aims to prioritize user privacy and protect sensitive information for these websites.
Answer:
A, D
Explanation:
FortiGate's temporary SSL certificate may cause access denial to sites using HTTP Strict Transport
Security (HSTS), so such sites are exempted from deep SSL inspection.
Legal regulations require exemption of certain categories to protect user privacy and sensitive
information, so these web categories are excluded from SSL inspection.
Question 6
Refer to the exhibit.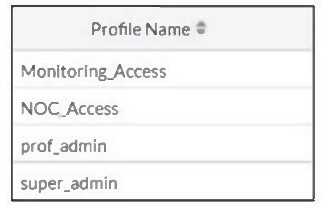
The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that
their GUI sessions do not disconnect too early during inactivity.
What must the administrator configure to answer this specific request from the NOC team?
- A. Move NOC_Access to the top of the list to ensure all profile settings take effect.
- B. Increase the offline value of the Override Idle Timeout parameter in the NOC_Access admin profile.
- C. Ensure that all NOC_Access users are assigned the super_admin role to guarantee access
- D. Increase the admintimeout value under config system accprofile NOC_Access.
Answer:
D
Explanation:
The admintimeout setting in the admin access profile controls the inactivity timeout for GUI sessions.
Increasing this value will extend the session duration before automatic disconnection.
Question 7
Refer to the exhibit.
Based on this partial configuration, what are the two possible outcomes when FortiGate enters
conserve mode? (Choose two.)
- A. Administrators cannot change the configuration.
- B. FortiGate skips quarantine actions.
- C. Administrators must restart FortiGate to allow new session.
- D. FortiGate drops new sessions requiring inspection.
Answer:
B, D
Explanation:
In fail-open mode, FortiGate skips quarantine actions to maintain traffic flow despite IPS or antivirus
failures.
FortiGate drops new sessions that require inspection when in conserve mode and fail-open is
enabled, to protect the network from potentially harmful traffic.
Question 8
What is the primary FortiGate election process when the HA override setting is enabled?
- A. Connected monitored ports > Priority > HA uptime > FortiGate serial number
- B. Connected monitored ports > Priority > System uptime > FortiGate serial number
- C. Connected monitored ports > HA uptime > Priority > FortiGate serial number
- D. Connected monitored ports > System uptime > Priority > FortiGate serial number
Answer:
A
Explanation:
When HA override is enabled, FortiGate uses the following election order: number of connected
monitored ports, then device priority, followed by HA uptime, and finally FortiGate serial number as
a tiebreaker.
Question 9
An administrator wanted to configure an IPS sensor to block traffic that triggers a signature set
number of times during a specific time period.
How can the administrator achieve the objective?
- A. Use IPS group signatures, set rate-mode 60.
- B. Use IPS packet logging option with periodical filter option.
- D. Use IPS filter, rate-mode periodical option.
Answer:
C
Explanation:
The IPS filter with the rate-mode set to "periodical" allows the administrator to block traffic that
triggers a signature a specified number of times within a defined time period, meeting the
requirement.
Question 10
A FortiGate firewall policy is configured with active authentication, however, the user cannot
authenticate when accessing a website.
Which protocol must FortiGate allow even though the user cannot authenticate?
- A. LDAP
- B. TACASC+
- C. Kerberos
- D. DNS
Answer:
D
Explanation:
DNS traffic must be allowed so the user can resolve domain names and reach the authentication
server or web resources, even if authentication initially fails.
Question 11
Refer to the exhibit, which shows a partial configuration from the remote authentication server.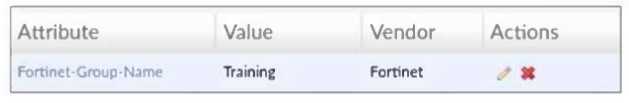
Why does the FortiGate administrator need this configuration?
- A. To set up a RADIUS server Secret.
- B. To authenticate Any FortiGate user groups.
- C. To authenticate and match the Training OU on the RADIUS server.
- D. To authenticate only the Training user group.
Answer:
D
Explanation:
The Fortinet-Group-Name attribute is used to restrict authentication to users who belong specifically
to the "Training" user group on the RADIUS server.
Question 12
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.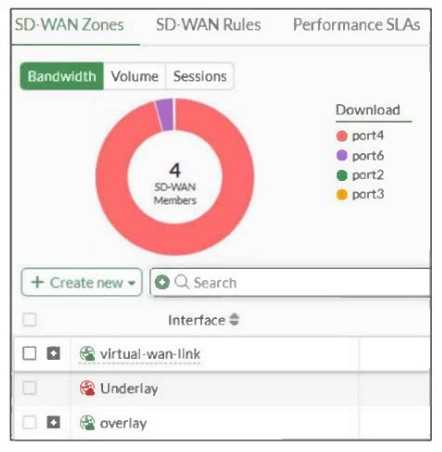
Based on the exhibit, which statement is true?
- A. The Underlay zone is the zone by default.
- B. The Underlay zone contains no member.
- C. port2 and port3 are not assigned to a zone.
- D. The virtual-wan-link and overlay zones can be deleted.
Answer:
A
Explanation:
The Underlay zone is the default SD-WAN zone, typically representing the physical interfaces in the
SD-WAN configuration before overlay or virtual links are added.
Question 13
Which three statements explain a flow-based antivirus profile? (Choose three.)
- A. FortiGate buffers the whole file but transmits to the client at the same time.
- B. Flow-based inspection uses a hybrid of the scanning modes available in proxy-based inspection.
- C. If a virus is detected, the last packet is delivered to the client.
- D. Flow-based inspection optimizes performance compared to proxy-based inspection.
- E. The IPS engine handles the process as a standalone.
Answer:
A, B, D
Explanation:
Flow-based antivirus buffers the entire file while simultaneously transmitting data to the client to
minimize latency.
Flow-based inspection combines multiple scanning techniques from proxy-based modes for efficient
detection.
Flow-based inspection provides better performance by processing traffic on the fly without full proxy
overhead.
Question 14
Refer to the exhibit.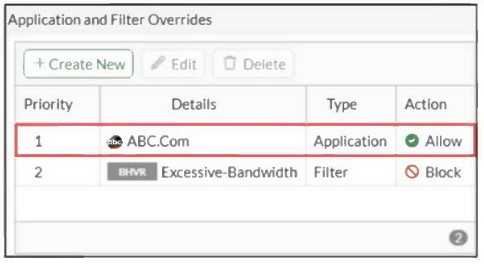
An administrator has configured an Application Overrides for the ABC.Com application signature and
set the Action to Allow. This application control profile is then applied to a firewall policy that is
scanning all outbound traffic. Logging is enabled in the firewall policy. To test the configuration, the
administrator accessed the ABC.Com web site several times.
Why are there no logs generated under security logs for ABC.Com?
- A. The ABC.Com Type is set as Application instead of Filter.
- B. The ABC.Com is configured under application profile, which must be configured as a web filter profile.
- C. The ABC.Com Action is set to Allow.
- D. The ABC.Com is hitting the category Excessive-Bandwidth.
Answer:
C
Explanation:
When the action is set to Allow in an application override, traffic matching this override is allowed
without generating security logs because it bypasses deeper inspection and blocking.
Question 15
Which two statements describe characteristics of automation stitches? (Choose two.)
- A. Actions involve only devices included in the Security Fabric.
- B. An automation stitch can have multiple triggers.
- C. Multiple actions can run in parallel.
- D. Triggers can involve external connectors.
Answer:
C, D
Explanation:
Automation stitches can execute multiple actions concurrently (in parallel).
Triggers for automation stitches can come from external connectors beyond just Fortinet devices.