f5 101 practice test
Application Delivery Fundamentals
Question 1
A BIO IP Administrator is troubleshooting a slow web application. A packet capture shows that some
of the packets coming from a window size of zero A packet capture shows that som a window size of
zero
What does this mean?
- A. The client is trying to close the TCP connection
- B. The server is trying to close the TCP connection
- C. The server is temporary unable to receive any more data
- D. The client is temporarily unable to receive any more data
Answer:
C
Question 2
Which device type in the topology will forward network packets without an OSI layer 3 address
assigned to a data plane interface?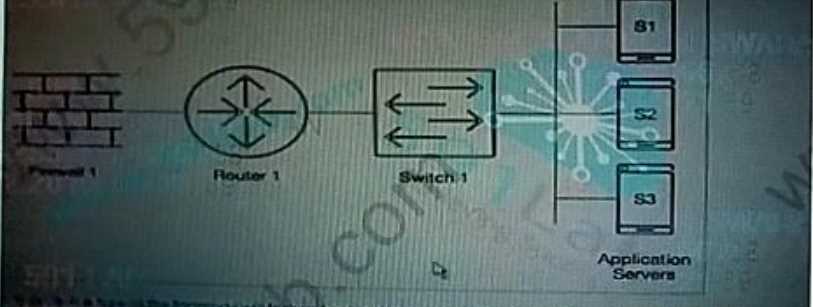
- A. Router
- B. Firewall
- C. Application Server
- D. Switch
Answer:
D
Question 3
An organization needs to cryptographically sign its domains. Which F5 product provides this
functionality?
A. GTM
B. LTM
C. ASM
D. APM
Answer:
A
https //devcentral f5 com/articles/the-tNg-ip gtm-configuring-dnssec
Question 4
A BIG-IP administrator is interested in using some of the vCMP
What should impact the administrator's decision?
- A. vCMP is available on all F5 hardware platforms.
- B. vCMP is only available on the virtual edition
- C. vCMP is hardware independent
- D. vCMP is only available on certain F5 platforms
Answer:
D
Question 5
Which three security controls are used in an SSL transaction? (Choose three.)
- A. symmetric encryption
- B. network admission controls
- C. asymmetric encryption
- D. digital certificates
- E. database encryption
Answer:
A, D
Question 6
An administrator needs to rapidly deter e newly discovered security threat to a remote desktop
application.
Which F5 feature provides this functionality?
- A. iRules
- B. SSL profiles
- C. Proxy SSL
- D. SPDY
Answer:
A
Question 7
In a fully proxy architecture, what is considered the client in the server-side communications
- A. the ADC
- B. the switch
- C. the server
- D. the client workstation
Answer:
A
Question 8
A BIG IP administrator is testing a web server behind ADC. The connection to a Virtual Server is
successful but the page is still not loading Where should the administrator test to determine if the
server is available?
- A. from server-side interface in ADC.
- B. from client side interface in ADC
- C. from Workstation client
- D. from switch connected to ADC and Server
Answer:
A
Question 9
in which scenario is a full proxy TCP connection required?
- A. when SIP UP P load balancing is defined
- B. when DNS load balancing is configured
- C. when compression is enabled
- D. when layer 3 load balancing is configured
Answer:
C
Question 10
Which method should an administrator of the BIG-IP use to sync the configuration to only certain
other BIG-IPs?
- A. synchronize only certain folders
- B. exclude devices from certain Traffic Groups
- C. exclude devices from certain Sync Groups
- D. exclude devices from certain Device Groups
Answer:
C
Question 11
What is an advantage of a packet forwarding architecture?
- A. allows for manipulation of HTTP headers
- B. allows for SSL offload
- C. reduces latency
- D. handles larger packet sizes
Answer:
C
Question 12
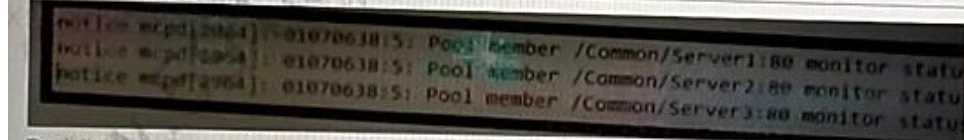
Pool A has three members.
Why is the pool up?
- A. Heaton monitoring is enabled on only one member
- B. One member has a successful health monitor
- C. Member status is determined by volume of traffic
- D. There is no health monitoring
Answer:
B
Question 13
Which type of certificate is pre-installed in a web browser’s trusted store?
- A. Root Certificate
- B. Server Certificate
- C. Client Certificate
- D. intermediate Certificate
Answer:
A
Question 14
A BIG IP Administrator need to perform a packet capture and identify the source IP that is connecting
to the Virtual Server.
Which utility should the administrator use on the BIG IP device?
- A. leinel
- B. traceroute
- C. ping
- D. tcpdump
Answer:
D
Question 15
The administrator wants client request to be directed to the same pool member through the session
based on the client IP address.
Which persistence method should the administrator choose?
- A. SSL persistence
- B. destination address affinity persistence
- C. cookie persistence
- D. Source address affinity persistence
Answer:
D