ericsson ecp-206 practice test
IP Networking
Question 1
What is an important difference between OSPF and IS-IS?
- A. OSPF runs directly on IP, while IS-IS runs directly on Ethernet.
- B. OSPF is a link state protocol, while IS-IS is a distance vector protocol.
- C. OSPF runs directly on Ethernet, while IS-IS runs directly on IP.
- D. OSPF is a distance vector protocol, while IS-IS is a link state protocol.
Answer:
A
Explanation:
OSPF runs directly on IP, while IS-IS runs directly on Ethernet. This means that OSPF uses IP addresses
to identify routers and links, while IS-IS uses MAC addresses or other link-layer identifiers. OSPF also
requires an IP header for each packet, while IS-IS does not. Both OSPF and IS-IS are link state
protocols, which means that they flood information about the network topology to all routers in the
same area or domain. Reference:
Ericsson IP Networking - Routing Protocols
,
Ericsson Router 6000
Series - Ericsson
Question 2
What is the subnet address for 10.57.126.156/29?
- A. 10.57.126.152
- B. 10.57.126.144
- C. 10.57.126.0
- D. 10.57.126.156
Answer:
A
Explanation:
The subnet address for 10.57.126.156/29 is 10.57.126.152. To find the subnet address, we need to
perform a bitwise AND operation between the IP address and the subnet mask. The subnet mask for
/29 is 255.255.255.248, which in binary is 11111111.11111111.11111111.11111000. The IP address
in binary is 00001010.00111001.01111110.10011100. The result of the AND operation is
00001010.00111001.01111110.10011000, which in decimal is 10.57.126.152. Reference:
Ericsson IP
Networking - IP Addressing
,
Software Installation and Upgrade Overview (Junos OS)
Question 3
What is the CLI command to obtain the software version in Ericsson Router 6000 products?
- A. show sysstat
- B. show version
- C. show log
- D. show release
Answer:
B
Explanation:
The CLI command to obtain the software version in Ericsson Router 6000 products is show version.
This command displays information about the software release, the hardware model, the serial
number, the uptime, and the boot image of the router. Reference: [ERICSSON SMARTEDGE 600
HARDWARE MANUAL Pdf Download | ManualsLib],
Ericsson Router 6000 Series - Ericsson
Question 4
For IP destinations not found in the IS-IS Level 1 database, the Level 1 router must forward packets to
the nearest Level 1-Level 2 router with which set?
- A. options bit
- B. status bit
- C. attach bit
- D. overload bit
Answer:
C
Explanation:
For IP destinations not found in the IS-IS Level 1 database, the Level 1 router must forward packets to
the nearest Level 1-Level 2 router with the attach bit set. The attach bit is a flag in the IS-IS Level 1
LSP that indicates that the router is also a Level 2 router and can reach destinations outside the Level
1 area. The Level 1 router will install a default route pointing to the nearest Level 1-Level 2 router
with the attach bit set. This way, the Level 1 router can forward packets to other areas without having
to maintain a full Level 2 database. Reference:
Ericsson IP Networking - Routing Protocols
,
Configure
Attach Bit Set - Cisco
Question 5
Within an IGP area, which two statements are correct? (Choose two.)
- A. Routers summarize information they learn from neighbors.
- B. Routers discard valid but inaccurate information from neighbors.
- C. Routers advertise information about themselves.
- D. Routers relay information delivered by neighbors.
Answer:
C, D
Explanation:
Within an IGP area, routers advertise information about themselves and relay information delivered
by neighbors. This is how link-state routing protocols such as OSPF and IS-IS work. They flood
information about the network topology to all routers in the same area or domain. That information
is then used to build a complete network connectivity map and to calculate the shortest path to
destinations. Routers do not summarize or discard information within an area, unless they are
configured to do so by some filtering mechanism. Reference:
Ericsson IP Networking - Routing
Protocols
,
IP Routing: ISIS Configuration Guide - IS-IS Overview and Basic Configuration
Question 6
Which network is reserved as a private network according to RFC1918?
- A. 172.16.1.0/9
- B. 10.254.1.0/24
- C. 193.168.1.0/24
- D. 172.15.1.0/24
Answer:
B
Explanation:
According to RFC1918, there are three network blocks reserved as private networks that are not
allocated to any specific organization and are not routable on the public Internet. These are:
10.0.0.0/8 (10.0.0.0 - 10.255.255.255)
172.16.0.0/12 (172.16.0.0 - 172.31.255.255)
192.168.0.0/16 (192.168.0.0 - 192.168.255.255)
Out of these, only option B (10.254.1.0/24) falls within one of the private network blocks
(10.0.0.0/8). Option A (172.16.1.0/9) is not valid because it exceeds the /12 prefix length of the
private network block (172.16.0.0/12). Option C (193.168.1.0/24) is not valid because it does not
belong to any of the private network blocks, and is actually assigned to RIPE NCC as a public network
block . Option D (172.15.1.0/24) is also not valid because it does not belong to any of the private
network blocks, and is actually assigned to ARIN as a public network block . Reference:
RFC 1918:
Address Allocation for Private Internets
,
Private network - Wikipedia
, [RIPE NCC IPv4 Address Space
Chart], [ARIN WHOIS Database Search]
Question 7
Which action will influence BGP route selection within your AS?
- A. reducing number of hops in the network
- B. changing the default value of the local preference
- C. changing the default link metric
- D. changing the administrative distance for eBGP
Answer:
B
Explanation:
The action that will influence BGP route selection within your AS is changing the default value of the
local preference attribute. The local preference attribute is used to indicate the preference of a path
among multiple paths learned from different external BGP neighbors or autonomous systems (ASes).
The higher the local preference value, the more preferred the path is within your AS, and vice versa.
The default value of local preference is 100, but you can change it using route maps or other
configuration methods on your BGP routers. Reference:
Ericsson IP Networking - Routing
Protocols
,
BGP Attributes and Path Selection
,
BGP Local Preference Attribute: Controlling Traffic Like
a Pro
Question 8
Which statement is true about LDP?
- A. LDP and IGP both exchange their databases every 60 seconds.
- B. LDP and IGP both exchange their databases every 30 seconds.
- C. LDP relies on IGP for all routing-related decisions.
- D. LDP performs routing functions along with IGP.
Answer:
C
Explanation:
LDP relies on IGP for all routing-related decisions. LDP is a protocol that distributes labels in an MPLS
environment, but it does not perform any routing functions. LDP uses the underlying routing
information provided by an IGP, such as OSPF or IS-IS, to forward label packets. LDP and IGP do not
exchange their databases at regular intervals, but rather use hello messages to maintain adjacencies
and sessions. Reference:
Ericsson IP Networking - Routing Protocols
,
Label Distribution Protocol -
Wikipedia
Question 9
Which two statements are true about priority queuing (PQ)? (Choose two.)
- A. Traffic in the highest priority queue will experience the least amount of jitter and delay compared to traffic in the other queues.
- B. Traffic in the highest priority queue is only reserved for voice traffic.
- C. Traffic in lower priority queues can be starved of bandwidth.
- D. Traffic in all queues are always guaranteed a minimum bandwidth.
Answer:
A, C
Explanation:
Priority queuing (PQ) is a queuing method that establishes four interface output queues that serve
different priority levels: high, medium, normal, and low. Traffic in the highest priority queue will
experience the least amount of jitter and delay compared to traffic in the other queues, because PQ
always services the higher-priority queues first. However, this can also cause traffic in lower priority
queues to be starved of bandwidth, especially if the highest priority queue is oversubscribed. Traffic
in the highest priority queue is not only reserved for voice traffic, but can also include network
control and routing traffic. Traffic in all queues are not always guaranteed a minimum bandwidth,
because PQ does not provide any bandwidth reservation mechanism. Reference:
Quality of Service
(QoS) Queues and Queuing Explained
,
Chapter: Configuring Priority Queueing - Cisco
Question 10
Review the exhibit.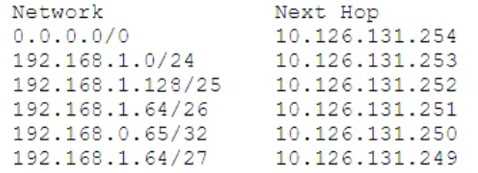
Given the routing table shown in the exhibit, what is the next-hop to reach the host 192.168.1.129?
- A. 10.126.131.251
- B. 10.126.131.252
- C. 10.126.131.250
- D. 10.126.131.248
Answer:
C
Explanation:
The next-hop to reach the host 192.168.1.129 is 10.126.131.250. This can be determined by looking
at the routing table in the exhibit. The host 192.168.1.129 falls within the range of the network
192.168.1.64/26, which has a next-hop of 10.126.131.250. Reference:
Ericsson IP Networking - IP
Addressing
,
Software Installation and Upgrade Overview (Junos OS)
Question 11
Which two statements are true about link-state routing protocols? (Choose two.)
- A. The advertisement exchange is mainly triggered by a change in the network.
- B. Each router uses a reliable update mechanism to exchange topology information with its neighbors. C Link-state routing protocols mainly use hop-counts to determine the link cost
- D. A distance vector algorithm is very processor intensive compared to Dijkstra's algorithm.
Answer:
A, B
Explanation:
Link-state routing protocols are one of the two main classes of routing protocols used in packet
switching networks for computer communications, the other being distance-vector routing
protocols. Examples of link-state routing protocols include Open Shortest Path First (OSPF) and
Intermediate System to Intermediate System (IS-IS). The basic concept of link-state routing is that
every node constructs a map of the connectivity to the network, in the form of a graph, showing
which nodes are connected to which other nodes. Each node then independently calculates the next
best logical path from it to every possible destination in the network. Each collection of best paths
will then form each node’s routing table.
Two statements that are true about link-state routing protocols are:
The advertisement exchange is mainly triggered by a change in the network. Link-state routing
protocols use a flooding mechanism to distribute information about the network topology to all
routers in the same area or domain. This information is encapsulated in link-state packets (LSPs) or
link-state advertisements (LSAs), which contain information about the router, its directly connected
links, and the state of those links. LSPs or LSAs are sent only when there is a change in the topology,
such as a link failure or recovery, or when a periodic refresh timer expires. This way, link-state routing
protocols can quickly adapt to network changes and maintain an accurate and consistent view of the
network.
Each router uses a reliable update mechanism to exchange topology information with its neighbors.
Link-state routing protocols use a reliable update mechanism to ensure that all routers receive and
acknowledge the LSPs or LSAs sent by their neighbors. This mechanism involves sending hello
messages to establish and maintain adjacencies with neighbors, sending acknowledgment messages
to confirm the receipt of LSPs or LSAs, and requesting missing or outdated LSPs or LSAs from
neighbors. This mechanism ensures that all routers have a synchronized database of LSPs or LSAs,
which is used to build a complete network connectivity map and to calculate the shortest path to
destinations.
Reference:
Link-state routing protocol - Wikipedia
,
Ericsson IP Networking - Routing Protocols
Question 12
Which operating system is used in Ericsson Router 6000 products?
- A. SE-OS
- C. ERS
- D. IPOS
- E. Junos
Answer:
C
Explanation:
The operating system used in Ericsson Router 6000 products is ERS (Ericsson Router Software). ERS is
based on IPOS (IP Operating System), which is a common operating system for Ericsson’s IP portfolio.
ERS provides advanced features and functionality for IP transport, such as MPLS, Segment Routing,
QoS, IPSec, synchronization, SDN, and more. ERS also supports seamless integration with Ericsson
Radio System and Ericsson Network Manager.
Reference:
Router 6000 Series - Ericsson
,
Router 6675 Datasheet - Winncom
Question 13
What network information is, without additional configuration, shared between two iBGP neighbors
by default?
- A. BGP routes learned from an OSPF neighbor
- B. IP address information of loopback interfaces
- C. BGP routes learned from eBGP neighbors
- D. IP address information from all directly connected interfaces
Answer:
C
Explanation:
iBGP works by exchanging routing information between two or more routers within an AS. Each
router sends its own routing table to its neighbors, which contains information about the networks it
knows and how they can be reached from that router. By default, iBGP neighbors only share BGP
routes learned from eBGP neighbors, which are routers in different ASes. This is because iBGP
assumes that all routers within an AS have consistent internal routing information provided by an
IGP, such as OSPF or IS-IS. Therefore, iBGP neighbors do not need to share IP address information of
loopback interfaces or directly connected interfaces, unless explicitly configured to do so by using
commands such as neighbor update-source or network.
Reference:
iBGP Ultimate Guide | How iBGP Is Different From eBGP
,
Ericsson IP Networking - Routing
Protocols
Question 14
An IS-IS router has been assigned the NSAP address: 49.00F0.0100.5012.3010.00.
What is the Area ID to which the router belongs?
- A. 49.00F0
- B. 49.00F0.0100
- C. 5012.3010.00
- D. 00F0 0100
Answer:
B
Explanation:
The Area ID to which the router belongs is 49.00F0.0100. The Area ID is a variable-length field in the
NSAP address that identifies the area to which the router belongs. The Area ID can be between 1 and
13 bytes long, but it must start and end with an octet (8 bits). The NSAP address is composed of three
parts: the authority and format identifier (AFI), the area ID, and the system ID. The AFI is a one-octet
field that indicates the format and authority of the rest of the address. The system ID is a fixed-length
field of six octets that uniquely identifies the router within an area. The NSAP address also has a
network selector (NSEL) field, which is a one-octet field that identifies the network layer service to
which a packet should be sent. For IS-IS routers, the NSEL must always be 00.
In this question, the NSAP address is 49.00F0.0100.5012.3010.00. This means that:
The AFI is 49, which indicates a private address.
The Area ID is 00F0.0100, which is four octets long and starts and ends with an octet.
The system ID is 5012.3010, which is six octets long and identifies the router within the area.
The NSEL is 00, which indicates IS-IS.
Therefore, the answer is B.
Reference:
Ericsson IP Networking - Routing Protocols
,
IS-IS NSAP address - Cisco
Community
,
Understanding IS-IS NSAP Addresses - Todd Lammle, LLC
,
IS-IS - Nokia
,
Network service
access point address - Wikipedia
Question 15
P routers forward packets based on the ______.
- A. flow label
- B. B. VPN label
- C. C. LSP label
- D. D. inner label
Answer:
C
Explanation:
P routers forward packets based on the LSP label. The LSP label is the label that corresponds to the
label-switched path (LSP) that is established between two PE routers in an MPLS network. The LSP
label is also called the outer label or the transport label, because it is used to transport packets
across the MPLS core network. P routers are also called LSRs (label switch routers) or transit routers,
because they switch packets based on their labels or remove the labels. P routers do not need to
look at the IP header or any other information in the packet, except for the top label in the label
stack. P routers perform one of three possible operations on labels: swap, pop, or PHP (penultimate
hop popping). In a swap operation, the label is swapped with a new label, and the packet is
forwarded along the path associated with the new label. In a pop operation, the label is removed
from the packet, and the packet is forwarded based on its IP header or another label in the stack. In a
PHP operation, the label is removed from the packet at the last P router before reaching the egress
PE router, and the packet is forwarded without any label to the egress PE router.
The LSP label is different from other types of labels that may be used in MPLS networks, such as VPN
labels or service labels. These labels are used to identify different VPNs or services that run over
MPLS networks, such as Layer 2 VPNs, Layer 3 VPNs, traffic engineering, or QoS. These labels are also
called inner labels or payload labels, because they are related to the payload of the packet. These
labels are not used by P routers for forwarding decisions, but only by PE routers for delivering
packets to their destinations.
Therefore, the answer is C.
Reference:
Ericsson IP Networking - Routing Protocols
,
MPLS Fundamentals: Forwarding Labeled
Packets - Cisco Press
,
MPLS Labels and Devices - NetworkLessons.com
,
Multiprotocol Label Switching
- Wikipedia
,
VPN Packet Forwarding > MPLS/VPN Architecture Overview | Cisco Press
,
Basic concepts
- Hewlett Packard Enterprise