Eccouncil ecsav10 practice test
Certified Security Analyst (ECSA) v10 Exam
Question 1
Mason is footprinting an organization to gather competitive intelligence. He visits the company's
website for contact information and telephone numbers but does not find any. He knows the entire
staff directory was listed on their website 12 months. How can he find the directory?
- A. Visit Google’s search engine and view the cached copy
- B. Crawl and download the entire website using the Surfoffline tool and save them to his computer
- C. Visit the company's partners’ and customers' website for this information
- D. Use Way Back Machine in Archive.org web site to retrieve the Internet archive
Answer:
D
Question 2
You work as a penetration tester for Hammond Security Consultants. You are currently working on a
contractfor the state government of Californi
a. Your next step is to initiate a DoS attack on their network. Why wouldyou want to initiate a DoS
attack on a system you are testing?
- A. Use attack as a launching point to penetrate deeper into the network
- B. Demonstrate that no system can be protected against DoS attacks
- C. List weak points on their network
- D. Show outdated equipment so it can be replaced
Answer:
C
Question 3
What is the target host IP in the following command?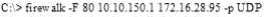
- A. Firewalk does not scan target hosts
- B. 172.16.28.95
- C. This command is using FIN packets, which cannot scan target hosts
- D. 10.10.150.1
Answer:
A
Question 4
An attacker injects malicious query strings in user input fields to bypass web service authentication
mechanisms and to access back-end databases. Which of the following attacks is this?
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer:
D
Question 5
Transmission Control Protocol (TCP) is a connection-oriented four layer protocol. It is responsible for
breaking messages into segments, re-assembling them at the destination station, and re-sending.
Which one of the following protocols does not use the TCP?
- A. Reverse Address Resolution Protocol (RARP)
- B. HTTP (Hypertext Transfer Protocol)
- C. SMTP (Simple Mail Transfer Protocol)
- D. Telnet
Answer:
A
Question 6
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security
audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and
most of the ports scanned do not give a response. In what state are these ports?
- A. Filtered
- B. Stealth
- C. Closed
- D. Open
Answer:
D
Question 7
Information gathering is performed to:
i) Collect basic information about the target company and its network
ii) Determine the operating system used, platforms running, web server versions, etc.
iii) Find vulnerabilities and exploits
Which of the following pen testing tests yields information about a companys technology
infrastructure?
- A. Searching for web page posting patterns
- B. Analyzing the link popularity of the company’s website
- C. Searching for trade association directories
- D. Searching for a company’s job postings
Answer:
D
Question 8
Timing is an element of port-scanning that can catch one unaware. If scans are taking too long to
complete or obvious ports are missing from the scan, various time parameters may need to be
adjusted.
Which one of the following scanned timing options in NMAPs scan is useful across slow WAN links
or to hide the scan?
- A. Paranoid
- B. Sneaky
- C. Polite
- D. Normal
Answer:
C
Question 9
SQL injection attacks are becoming significantly more popular amongst hackers and there has been
an estimated 69 percent increase of this attack type.
This exploit is used to great effect by the hacking community since it is the primary way to steal
sensitive data from web applications. It takes advantage of non-validated input vulnerabilities to pass
SQL commands through a web application for execution by a back-end database.
The below diagram shows how attackers launched SQL injection attacks on web applications.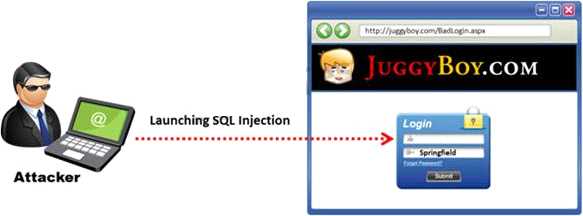
Which of the following can the attacker use to launch an SQL injection attack?
- A. Blah' “2=2 –“
- B. Blah' and 2=2 --
- C. Blah' and 1=1 --
- D. Blah' or 1=1 --
Answer:
D
Question 10
Jim performed a vulnerability analysis on his network and found no potential problems. He runs
another utilitythat executes exploits against his system to verify the results of the vulnerability test.
The second utilityexecutes five known exploits against his network in which the vulnerability analysis
said were not exploitable.
What kind of results did Jim receive from his vulnerability analysis?
- A. True negatives
- B. False negatives
- C. False positives
- D. True positives
Answer:
B
Question 11
Windows stores user passwords in the Security Accounts Manager database (SAM), or in the Active
Directory database in domains. Passwords are never stored in clear text; passwords are hashed and
the results are stored in the SAM.
NTLM and LM authentication protocols are used to securely store a user's password in the SAM
database using different hashing methods.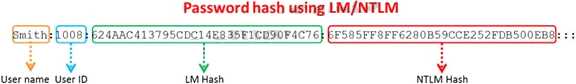
The SAM file in Windows Server 2008 is located in which of the following locations?
- A. c:\windows\system32\config\SAM
- B. c:\windows\system32\drivers\SAM
- C. c:\windows\system32\Setup\SAM
- D. c:\windows\system32\Boot\SAM
Answer:
D
Question 12
Output modules allow Snort to be much more flexible in the formatting and presentation of output
to its users. Snort has 9 output plug-ins that push out data in different formats. Which one of the
following output plug-ins allows alert data to be written in a format easily importable to a database?
- A. unified
- B. csv
- C. alert_unixsock
- D. alert_fast
Answer:
B
Question 13
DMZ is a network designed to give the public access to the specific internal resources and you might
want to do the same thing for guests visiting organizations without compromising the integrity of the
internal resources. In general, attacks on the wireless networks fall into four basic categories.
Identify the attacks that fall under Passive attacks category.
- A. Wardriving
- B. Spoofing
- C. Sniffing
- D. Network Hijacking
Answer:
A
Question 14
Identify the attack represented in the diagram below: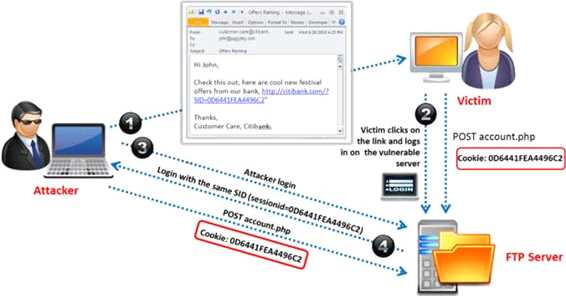
- A. Input Validation
- B. Session Hijacking
- C. SQL Injection
- D. Denial-of-Service
Answer:
B
Question 15
Which among the following information is not furnished by the Rules of Engagement (ROE)
document?
- A. Techniques for data collection from systems upon termination of the test
- B. Techniques for data exclusion from systems upon termination of the test
- C. Details on how data should be transmitted during and after the test
- D. Details on how organizational data is treated throughout and after the test
Answer:
A