Eccouncil 312-96 practice test
JAVA
Question 1
Sam, an application security engineer working in INFRA INC., was conducting a secure code review
on an application developed in Jav
a. He found that the developer has used a piece of code as shown in the following screenshot.
Identify the security mistakes that the developer has coded?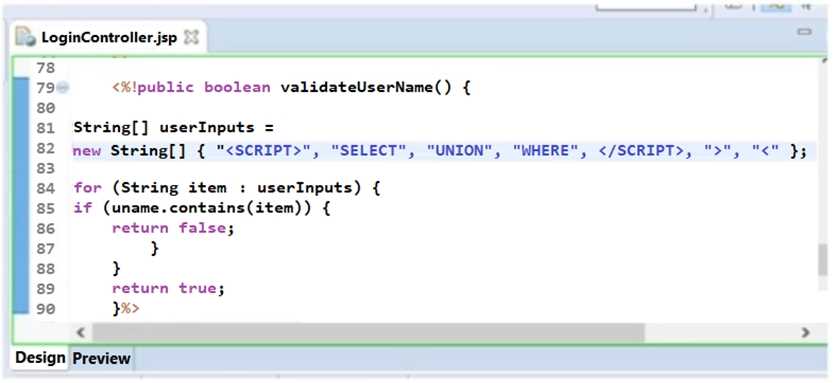
- A. He is attempting to use client-side validation
- B. He is attempting to use whitelist input validation approach
- C. He is attempting to use regular expression for validation
- D. He is attempting to use blacklist input validation approach
Answer:
D
Question 2
Identify the type of attack depicted in the following figure.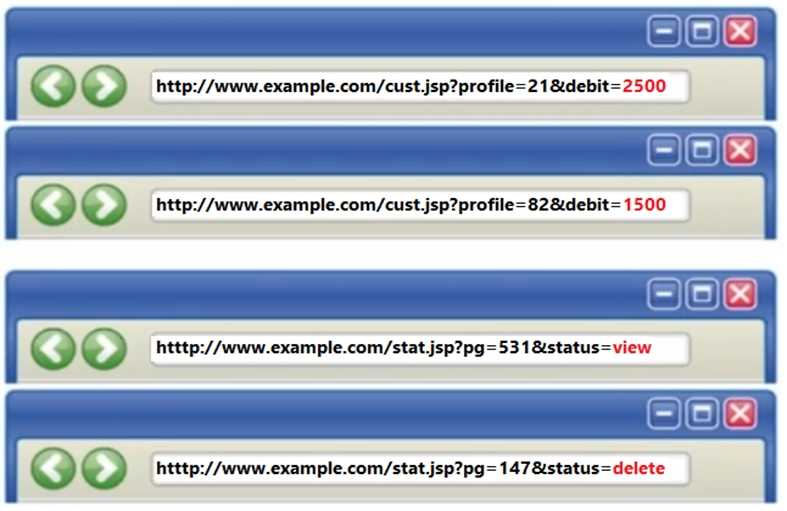
- A. SQL Injection Attacks
- B. Session Fixation Attack
- C. Parameter Tampering Attack
- D. Denial-of-Service Attack
Answer:
C
Question 3
According to secure logging practices, programmers should ensure that logging processes are not
disrupted by:
- A. Catching incorrect exceptions
- B. Multiple catching of incorrect exceptions
- C. Re-throwing incorrect exceptions
- D. Throwing incorrect exceptions
Answer:
D
Question 4
Which of the threat classification model is used to classify threats during threat modeling process?
- A. RED
- B. STRIDE
- C. DREAD
- D. SMART
Answer:
B
Question 5
Which line of the following example of Java Code can make application vulnerable to a session
attack?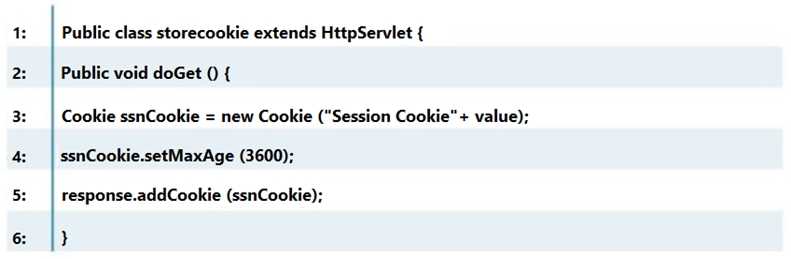
- A. Line No. 1
- B. Line No. 3
- C. Line No. 4
- D. Line No. 5
Answer:
B
Question 6
Alice, a Server Administrator (Tomcat), wants to ensure that Tomcat can be shut down only by the
user who owns the Tomcat process. Select the appropriate setting of the CATALINA_HOME/conf in
server.xml that will enable him to do so.
- A. < server port="" shutdown-"' >
- B. < server port="-1" shutdown-*" >
- C. < server port="-1" shutdown="SHUTDOWN" >
- D. < server port="8080" shutdown="SHUTDOWN" >
Answer:
B
Question 7
Which of the following method will help you check if DEBUG level is enabled?
- A. isDebugEnabled()
- B. EnableDebug ()
- C. IsEnableDebug ()
- D. DebugEnabled()
Answer:
A
Question 8
Which of the following elements in web.xml file ensures that cookies will be transmitted over an
encrypted channel?
- A. < connector lsSSLEnabled="Yes" / >
- B. < connector EnableSSL="true" / >
- C. < connector SSLEnabled="false" / >
- D. < connector SSLEnabled="true" / >
Answer:
D
Question 9
In which phase of secure development lifecycle the threat modeling is performed?
- A. Coding phase
- B. Testing phase
- C. Deployment phase
- D. Design phase
Answer:
D
Question 10
Identify the type of attack depicted in the figure below: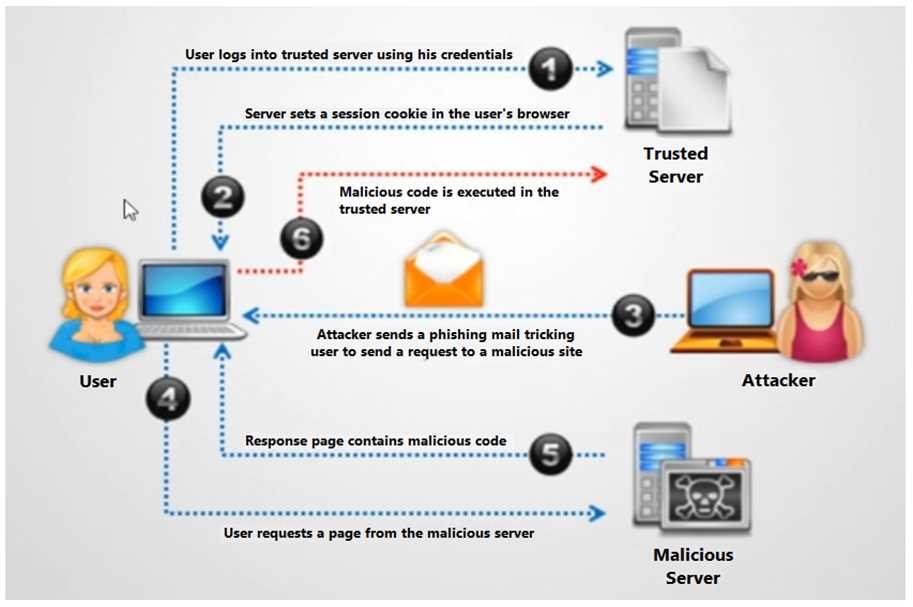
- A. XSS
- B. Cross-Site Request Forgery (CSRF) attack
- C. SQL injection attack
- D. Denial-of-Service attack
Answer:
B
Question 11
Stephen is a web developer in the InterCall Systems. He was working on a Real Estate website for
one of his clients. He was given a task to design a web page with properties search feature. He
designed the following searchpage.jsp
< form Id="form1" method="post" action="SearchProperty.jsp" >
< input type="text" id=''txt_Search" name="txt_Search" placeholder="Search Property..." / >
< input type="Submit" Id="Btn_Search" value="Search" / >
< /form >
However, when the application went to security testing phase, the security tester found an XSS
vulnerability on this page. How can he mitigate the XSS vulnerability on this page?
- A. He should write code like out-Write ("You Searched for:" +ESAPI.encoder().encodeForHTML(search));
- B. He should write code like out.write ("You Searched for:" + request.qetParameter("search"l.toStrinq(ll;
- C. He should write code like out.write ("You Searched for:" + request.qetParameterf'txt Search"));
- D. He should write code like out.write (("You Searched for:" +(search));
Answer:
A
Question 12
Jacob, a Security Engineer of the testing team, was inspecting the source code to find security
vulnerabilities.
Which type of security assessment activity Jacob is currently performing?
- A. ISCST
- C. CAST
- D. SAST
Answer:
D
Question 13
Oliver, a Server Administrator (Tomcat), has set configuration in web.xml file as shown in the
following screenshot. What is he trying to achieve?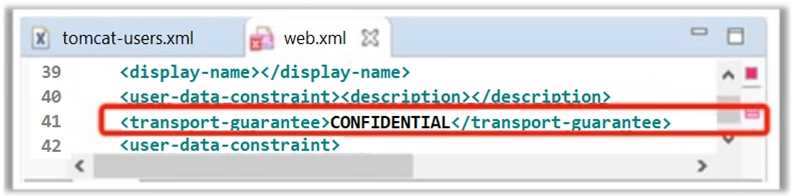
- A. He wants to transfer the entire data over encrypted channel
- B. He wants to transfer only response parameter data over encrypted channel
- C. He wants to transfer only request parameter data over encrypted channel
- D. He wants to transfer only Session cookies over encrypted channel
Answer:
A
Question 14
Alice works as a Java developer in Fygo software Services Ltd. He is given the responsibility to design
a bookstore website for one of their clients. This website is supposed to store articles in .pdf format.
Alice is advised by his superior to design ArticlesList.jsp page in such a way that it should display a list
of all the articles in one page and should send a selected filename as a query string to redirect users
to articledetails.jsp page.
Alice wrote the following code on page load to read the file name.
String myfilename = request.getParameter("filename");
String txtFileNameVariable = myfilename;
String locationVariable = request.getServletContext().getRealPath("/");
String PathVariable = "";
PathVariable = locationVariable + txtFileNameVariable;
BufferedInputStream bufferedInputStream = null;
Path filepath = Paths.get(PathVariable);
After reviewing this code, his superior pointed out the security mistake in the code and instructed
him not repeat the same in future. Can you point the type of vulnerability that may exist in the above
code?
- A. URL Tampering vulnerability
- B. Form Tampering vulnerability
- C. XSS vulnerability
- D. Directory Traversal vulnerability
Answer:
D
Question 15
In a certain website, a secure login feature is designed to prevent brute-force attack by implementing
account lockout mechanism. The account will automatically be locked after five failed attempts. This
feature will not allow the users to login to the website until their account is unlocked. However,
there is a possibility that this security feature can be abused to perform __________ attack.
- A. Failure to Restrict URL
- B. Broken Authentication
- C. Unvalidated Redirects and Forwards
- D. Denial-of-Service [Do
Answer:
D