Bios parameter block and the oem id
Which tool allows dumping the contents of process memory without stopping the process?
A. psdump.exe
B. pmdump.exe
C. processdump.exe
D. pdump.exe
B
Which of the following files store the MySQL database data permanently, including the data that had
been deleted, helping the forensic investigator in examining the case and finding the culprit?
D
MAC filtering is a security access control methodology, where a ___________ is assigned to each
network card to determine access to the network.
A
Which Event Correlation approach assumes and predicts what an attacker can do next after the
attack by studying statistics and probability?
B
Which of the following stand true for BIOS Parameter Block?
A
James is dealing with a case regarding a cybercrime that has taken place in Arizona, US
D
You are asked to build a forensic lab and your manager has specifically informed you to use copper
for lining the walls, ceilings, and floor. What is the main purpose of lining the walls, ceilings, and floor
with copper?
D
What document does the screenshot represent?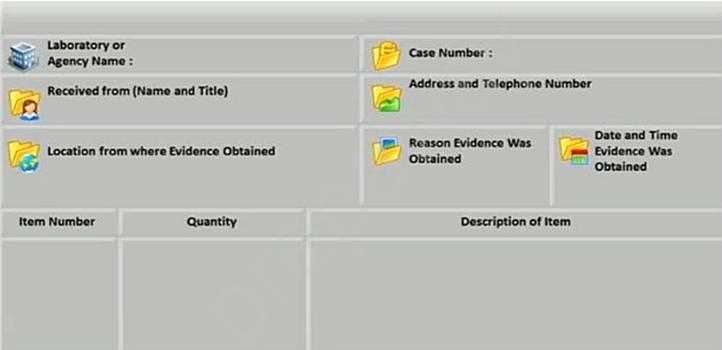
D
What does the Rule 101 of Federal Rules of Evidence states?
A
What does the bytes 0x0B-0x53 represent in the boot sector of NTFS volume on Windows 2000?
A. Jump instruction and the OEM ID
B. BIOS Parameter Block (BPB) and the OEM ID
C. BIOS Parameter Block (BPB) and the extended BPB
D. Bootstrap code and the end of the sector marker
C
Bios parameter block and the oem id
Which program uses different techniques to conceal a malware's code, thereby making it difficult for
security mechanisms to detect or remove it?
D
Which of these rootkit detection techniques function by comparing a snapshot of the file system,
boot records, or memory with a known and trusted baseline?
B
Which forensic investigation methodology believes that criminals commit crimes solely to benefit
their criminal enterprises?
C
Which of the following Linux command searches through the current processes and lists the process
IDs those match the selection criteria to stdout?
B
Which of these ISO standards define the file system for optical storage media, such as CD-ROM and
DVD-ROM?
A
Psdump.exe