Dell EMC des-5121 practice test
Specialist ? Implementation Engineer, Campus Networking Version 1.0 Exam
Question 1
How many untagged VLANs are allowed on a switchport mode trunk interface?
- A. 0
- B. 1
- C. 128
- D. 4096
Answer:
B
Question 2
Based on the exhibit,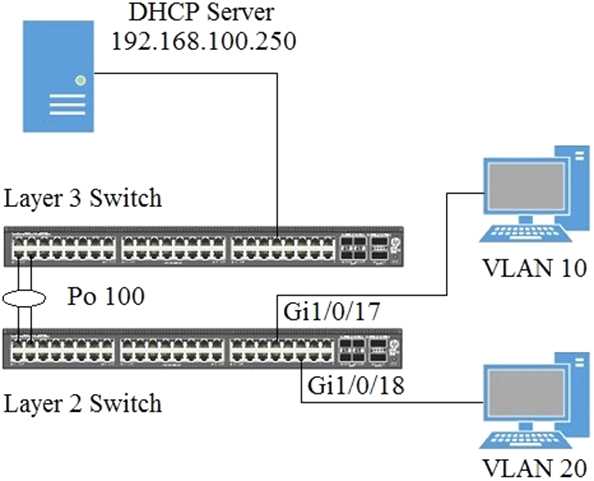
which configuration on interface Gi1/0/18 will allow the DHCP request to reach the DHCP server for
the specified VLAN?
- A. Configuration A: console(config-if-Gi1/0/18)# switchport mode general console(config-if-Gi1/0/18)# switchport general pvid 20 console(config-if-Gi1/0/18)# switchport general allowed vlan add 20 console(config-if-Gi1/0/18)# switchport general allowed vlan remove 1
- B. Configuration B: console(config-if-Gi1/0/18)# switchport access vlan 10 console(config-if-Gi1/0/18)# service-policy in dhcp_250 console(config-if-Gi1/0/18)# switchport general allowed vlan add 20 console(config-if-Gi1/0/18)# switchport general allowed vlan remove 1
- C. Configuration C: console(config-if-Gi1/0/18)# switchport access vlan 10 console(config-if-Gi1/0/18)# ip dhcp snooping trust console(config-if-Gi1/0/18)# switchport general allowed vlan add 20 console(config-if-Gi1/0/18)# switchport general allowed vlan remove 1
- D. Configuration D: console(config-if-Gi1/0/18)# channel-group 100 mode active console(config-if-Gi1/0/18)# switchport access vlan 250 console(config-if-Gi1/0/18)# switchport general allowed vlan add 20 console(config- if-Gi1/0/18)# switchport general allowed vlan remove 1
Answer:
A
Question 3
Refer to the Exhibit.
Switch-1(config)# radius server host 10.1.1.111
Switch-1(config-radius)# key "secretkey"
Switch-1(config-radius)# exit
Switch-1(config)# aaa authentication login "LOCAL-AUTH" local
Switch-1(config)# aaa authentication login "REMOTE-AUTH" radius local
Switch-1(config)# aaa authentication enable "REMOTE-AUTH" radius enable
Switch-1(config)# aaa authentication login default tacacs local
Switch-1(config)# aaa authentication enable default tacacs enable
Switch-1(config)# line telnet
Switch-1(config-telnet)# login authentication "REMOTE-AUTH"
Switch-1(config-telnet)# exit
Switch-1(config)# line ssh
Switch-1(config-ssh)# login authentication default
Switch-1(config)# exit
Switch-1(config)# line console
Switch-1(config-line)# login authentication "LOCAL-AUTH"
Switch-1(config-line)# exit
Which authentication method will be used if a user tries to log into the switch when accessing
through SSH?
- A. RADIUS, then fails over to a local user account
- B. Local user account
- C. TACACS, then fails over to a local user account
- D. None
Answer:
C
Question 4
Which spanning tree feature will prevent unnecessary timeouts from DHCP servers?
- A. PortFast
- B. Loop Guard
- C. BPDU Flooding
- D. Root Guard
Answer:
A
Reference:
https://www.dell.com/community/Networking-General/Advice-on-basic-STP-and-network-
design/td- p/4434346
Question 5
Which packet characteristics can policy-based routing be configured to match against?
- A. TTL, TCP Port, and L3 Packet Length
- B. L3 Packet Length, TTL, and 802.1p Priority
- C. TCP Port, L3 Packet Length, and 802.1p Priority
- D. TCP Port, TTL, and 802.1p Priority
Answer:
C
Question 6
How does the weighted Queue Scheduler prioritize packets?
- A. Scheduler prioritizes weighted queues over any strict queues
- B. Weights are calculated based on the number of packets
- C. Weights are used to calculate the number of bytes
- D. Weight is assigned to each port
Answer:
C
Reference:
https://infohub.delltechnologies.com/static/media/6582046d-70f0-4ab6-ba72-2c0b9cf26649.pdf
page 6
Question 7
A network administrator wants to configure an ACL to deny traffic for a specific source IP and source
UDP port.
Which type of ACL should be used?
- A. Layer 2 Standard ACL
- B. Layer 2 Extended ACL
- C. Layer 3 Standard ACL
- D. Layer 3 Extended ACL
Answer:
D
Question 8
In order to alter a packet’s routing direction, which packet layers can policy-based routing use?
- A. Transport, Network, Link Layer, and Physical
- B. Link Layer, Physical, Presentation, and Session
- C. Network, Link Layer, Physical, and Session
- D. Application, Transport, Network, and Link Layer
Answer:
A
Question 9
If VoIP traffic uses multiple QoS prioritization schemes, what refers to VoIP traffic?
- A. COS 2, DSCP 22, AF
- B. COS 2, DSCP 46, EF
- C. COS 5, DSCP 42, AF
- D. COS 5, DSCP 46, EF
Answer:
D
Question 10
N4032F#show interfaces status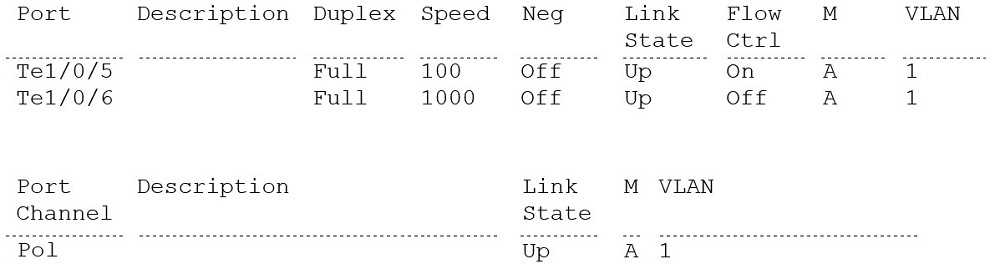
N4032F#show interfaces port-channel 1
Hash Algorithm Type
1 - Source MAC, VLAN, EtherType, source module and port Id
2 - Destination MAC, VLAN, EtherType, source module and port Id
3 - Source IP and source TCP/UDP port
4 - Destination IP and destination TCP/UDP port
5 - Source/Destination MAC, VLAN, EtherType, source MODID/port
6 - Source/Destination IP and source/destination TCP/UDP port
7 - Enhanced hashing mode
N4032F#
A Dell EMC N-Series switch has been configured with a 2-member port-channel; however, only one
link is currently active.
Based on the exhibit, why is only one link active?
- A. Minimum links value for Po1 is set to "1"
- B. Hash algorithm is configured for active-passive
- C. Te1/0/6 interface is administratively disabled
- D. Speed setting is different between ports
Answer:
D
Question 11
Which type of an attack is considered MAC poisoning?
- A. Duplicating the MAC address of a legitimate device so frames are forwarded to the incorrect port
- B. Host imitating a trunk port by using tagging and trunking protocols
- C. Flooding MAC addresses to the switch to fill its CAM table, causing the switch to act as a hub
- D. Host on a VLAN gaining unauthorized access to other VLANs on the network
Answer:
A
Question 12
What is a recommended configuration for an MLAG peer-link on a Dell EMC N-Series switch?
- A. Spanning tree must be disabled
- B. Spanning tree must be enabled
- C. Link must be a trunk port
- D. Link must contain multiple interfaces
Answer:
B
Question 13
N4032F#show interfaces status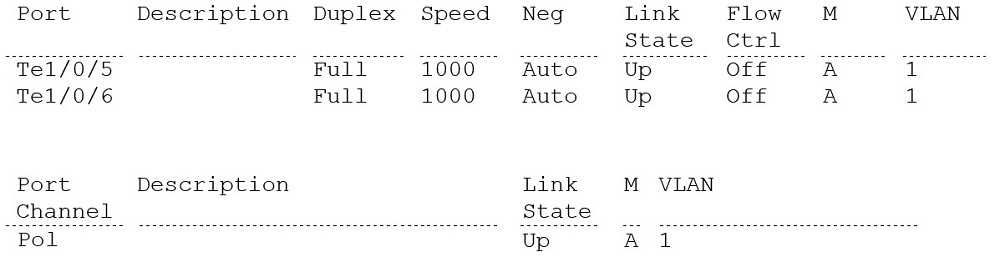
N4032F#show interfaces port-channel 1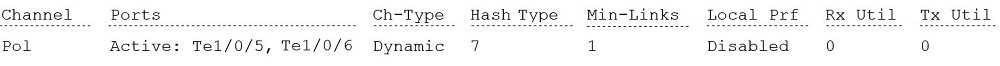
Hash Algorithm Type
1 - Source MAC, VLAN, EtherType, source module and port Id
2 - Destination MAC, VLAN, EtherType, source module and port Id
3 - Source IP and source TCP/UDP port
4 - Destination IP and destination TCP/UDP port
5 - Source/Destination MAC, VLAN, EtherType, source MODID/port
6 - Source/Destination IP and source/destination TCP/UDP port
7 - Enhanced hashing mode
A network administrator has reported poor network performance to an application server. After
reviewing the logs, you determine that the server is using 100 percent of the available bandwidth on
its network port. As shown in the exhibit, you configure a second link and a 2-member port-channel
to an application server in an effort to increase performance. However, during testing, the network
performance has not improved.
What is a possible reason why there has been no increase in the performance?
- A. Application is using a single I/O flow
- B. File server needs to be configured with LACP
- C. Minimum links needs to be increased to "2"
- D. Port-channel needs load balancing enabled
Answer:
A
Question 14
A Dell EMC N-Series switch is configured to uplink to a customer switch using two separate 4-port
port- channels configured as trunks. Both switches are configured with 16 VLANs and RSTP.
How will VLAN traffic be distributed across the port-channels?
- A. All VLANs are allowed across a single port-channel
- B. A single VLAN is allowed across each port-channel
- C. All VLANs are allowed across both port-channels
- D. Eight VLANs are allowed across each port-channel
Answer:
A
Question 15
A network administrator is planning a PoE budget for their network.
What is the PoE source maximum power budget for a Class 4 end device?
- A. 12.95 watts
- B. 15.4 watts
- C. 34.2 watts
- D. 60 watts
Answer:
C
Reference:
http://ftp.dell.com/manuals/all-products/esuprt_ser_stor_net/esuprt_networking/
esuprt_net_fxd_prt_swtchs/networking-n3000-series_User's-Guide10_en-us.pdf page 82