Dell EMC des-1423 practice test
Specialist Implementation Engineer Isilon Solutions Exam
Question 1
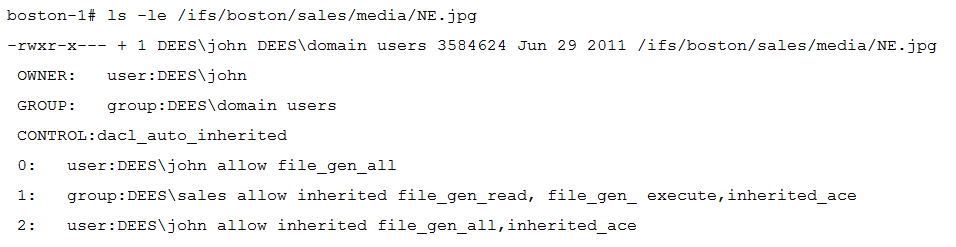
Which access information is represented in the exhibit?
- A. Real ACL is applied and group “DEES\domain users” has read access to the file
- B. Real ACL is applied and group “DEES\sales” has read access to the file
- C. Synthetic ACL is applied and group “DEES\sales” has read access to the file
- D. Synthetic ACL is applied and user “DEES\john” has read access to the file
Answer:
A
Question 2
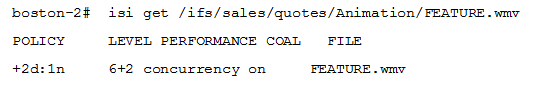
Based on the exhibit, what is the actual protection level of the FEATURE.wmv file?
- A. N+1
- B. N+2
- C. N+2n
- D. N+2d: 1n
Answer:
C
Explanation:
341
Isilon Administration and Management participant guide
Question 3
You have been tasked with designing SyncIQ policies for a systems administrator that requires
failover and failback testing. What information should be provided to the administrator?
- A. SyncIQ supports failback replication policies that specify directory includes or excludes.
- B. Failback replication policies that specify includes or excludes cannot use data encryption.
- C. Failback replication policies that specify includes or excludes are not supported with SyncIQ.
- D. Failback replication policies that specify includes or excludes cannot use historical snapshots.
Answer:
C
Question 4
You are configuring the network on a Isilon source cluster. The administrator wants to dedicate a new
subnet for replication. Which consideration must be addressed for SyncIQ to work properly?
- A. SyncIQ must run on a static IP pool.
- B. SnapshotIQ must be licensed first.
- C. 10GbE ports must be used for replication
- D. SyncIQ must run on a dynamic IP pool
Answer:
A
Explanation:
Isilon Administration and Management participant guide
Question 5
When reconciling permissions for clients using UNIX as well as Microsoft Windows systems, what
describes the scope of the permissions?
- A. Windows ACLs and POSIX bits have overlapping semantics, but neither completely reflects the other.
- B. Windows ACLs have semantics that are a subset of POSIX bits.
- C. POSIX bits have semantics that are a subset of Windows ACLs, but Windows ACLs are more extensive.
- D. POSIX bits and Windows ACLs are semantically equivalent.
Answer:
B
Question 6
What is the maximum number of nodes that can be added into a node pool in Isilon Gen 6 hardware
and OneFS 8.2.0?
- A. 144
- B. 252
- C. 288
- D. 352
Answer:
B
Question 7
What are the two ways a FlexProtect job can start?
- A. An at or batch command and Non-event driven
- B. Administrative and Even-driven
- C. An at or batch command and Alert-driven
- D. Administrative and Alert-driven
Answer:
D
Question 8
DRAG DROP
What is the correct hierarchy of the Job elements structure?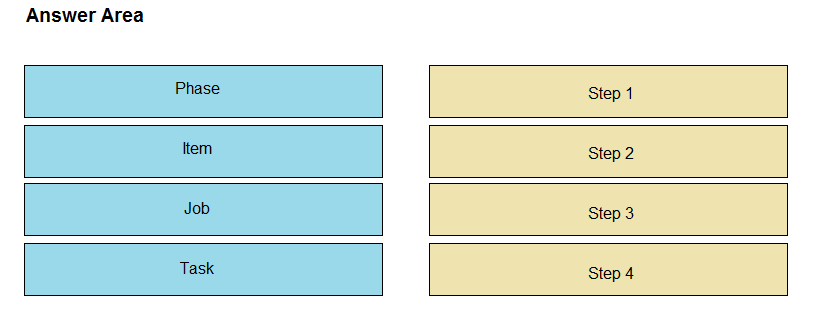
Answer:
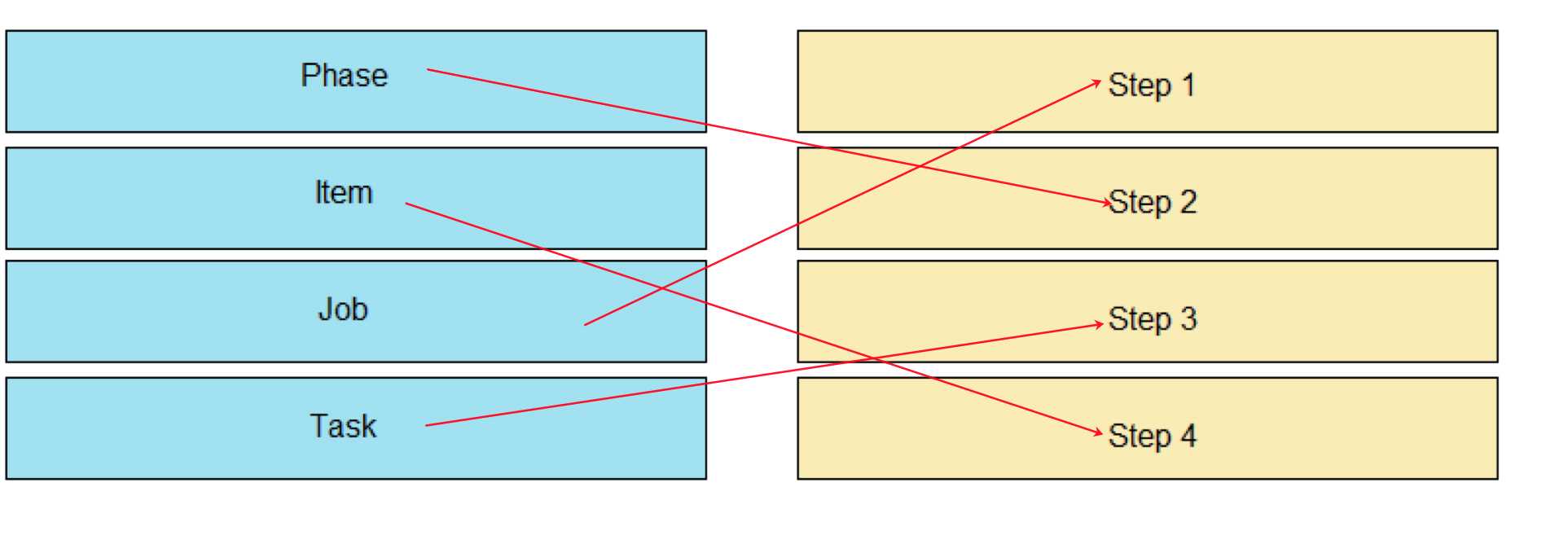
Question 9
What information is required to enable the LDAP service on an Isilon cluster?
- A. Administrator account and password, and LDAP server name and IP address
- B. Port number, cluster name, and an LDAP server IP address
- C. Base distinguished name, cluster name, and port number
- D. Base distinguished name, port number, and at least one LDAP server
Answer:
D
Question 10
A systems administrator must ensure that an IP address never becomes unavailable, even if a node
goes offline. What needs to be configured on SmartConnect?
- A. Dynamic Allocation
- B. Static Allocation
- C. Connection Count
- D. Round Robin
Answer:
A
Question 11
You have just completed an upgrade from OneFS 8.0.0.7 to 8.2.0 but have not committed the
upgrade. How many days will pass before you are prompted to commit the upgrade in the WebUI?
- A. 5
- B. 7
- C. 10
- D. 14
Answer:
C
Question 12
An Isilon administrator wants to create a new SMB share to an existing directory structure. The
directory contains migrated production data and has an active NFS export. What will happen if the
administrator selects the Apply Windows default ACLs option during creation?
- A. Windows default ACLs are overwritten by the existing mode bit rights.
- B. Existing mode bit rights are overwritten by the Windows default ACLs.
- C. Windows default ACLs are merged with the existing mode bit rights.
- D. Creation of the SMB share fails due to the existing mode bit rights.
Answer:
B
Explanation:
246
Isilon Administration and Management participant guide
Question 13
A new Isilon administrator has created their first quota of 100 TB on a directory called /ifs/Boston-
zone/RnD. Both the Engineering and QA teams have access to this directory. The directory sits on a
4-node H400 node pool.
Two weeks later, the administrator notices that the teams available disk space is decreasing faster
than anticipated for the /ifs/Boston-zone/RnD directory.
What is the most likely cause for the decrease in disk space?
- A. Quota was configured to include overhead.
- B. SmartPools tiering is not enabled.
- C. Quota was configured as an Advisory quota.
- D. SmartPools global spillover is not enabled.
Answer:
A
Question 14
A Job Engine is running in low space mode and no jobs are in the running state. What is the OneFS8.2
behavior if the AutoBalance job is initiated?
A. Job is started.
B. Job is failed.
C. Job is put into the queue.
D. Job is not started.
Answer:
A
494 / 495 Autobalance is a space saving job
Isilon Administration and Management participant guide
Question 15
What is the difference between a rolling upgrade and simultaneous upgrade in an Isilon cluster?
- A. Rolling updates take less time to complete.Simultaneous upgrades take longer to complete.
- B. Rolling updates are more disruptive.Simultaneous upgrades are less disruptive.
- C. Rolling updates are less disruptive.Simultaneous upgrades are more disruptive.
- D. Rolling updates are available between all OneFS versions.Simultaneous upgrades are restricted between certain OneFS versions.
Answer:
C