Dell EMC dee-1421 practice test
Isilon Expert Solutions Exam
Question 1
You have been asked to design a Dell EMC Isilon cluster running OneFS 8.x for a service provider. One
of the most critical areas to the provider is data segregation with multi-tenants. Use the Launch
Simulator button to identify the current condition of the cluster: Note: It is necessary to close (x)
the simulator window to answer the question.
Based on your findings, what is the clusters current condition?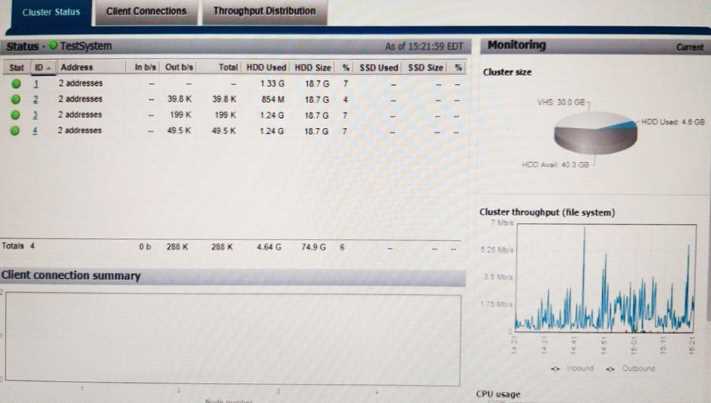
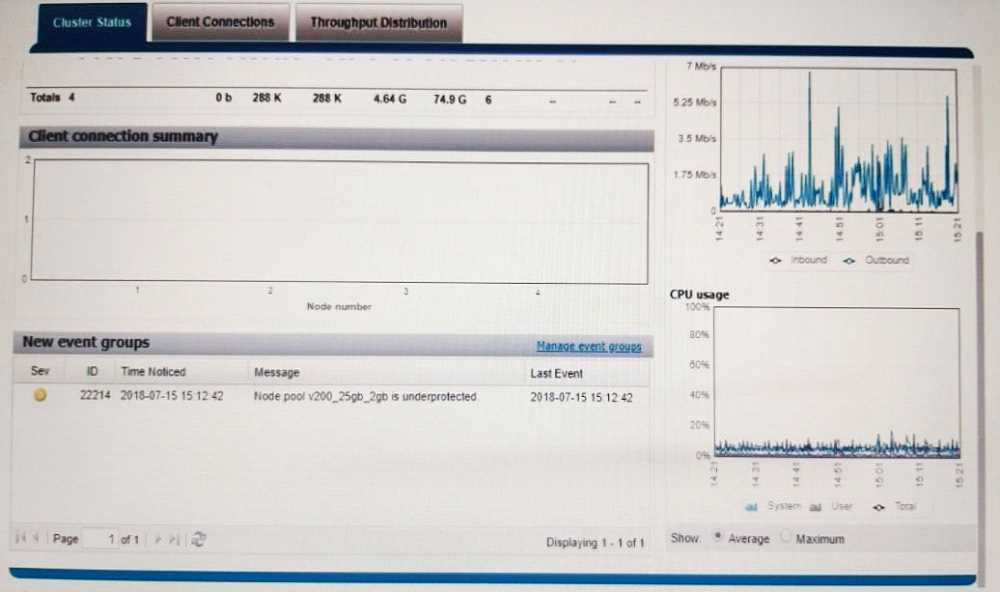
- A. All non-System Access zones are connected to the same groupnet. each with its own DNS server
- B. Each non-System Access zone is connected to an individual groupnet. each with its own DNS server
- C. All non-System Access zones are connected to the same groupnet with the same DNS server
- D. Each non-System Access zone is connected to an individual groupnet with the same DNS server.
Answer:
A
Question 2
A Dell EMC Isilon administrator has reported that in Access zone ProdZone on the OneFS file
system nfs1, Microsoft Windows DEES\user1 has root level permission on nfs1. Use the Launch
Situation button to examine the environment and validate the reason for this condition. Note: It is
necessary to close (x) the simulation windows to answer the question.
Based on your findings, what is the reason for the condition?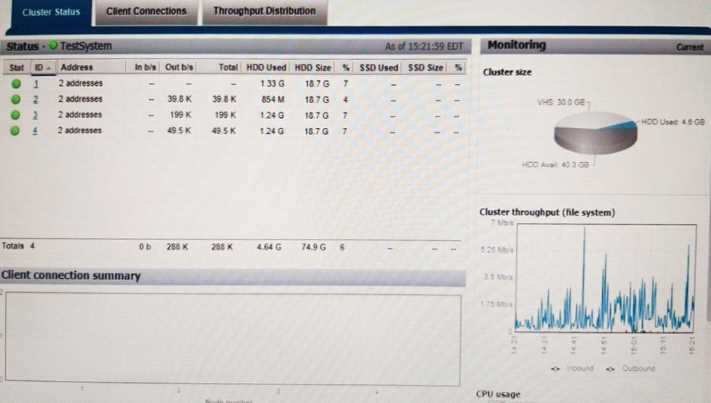
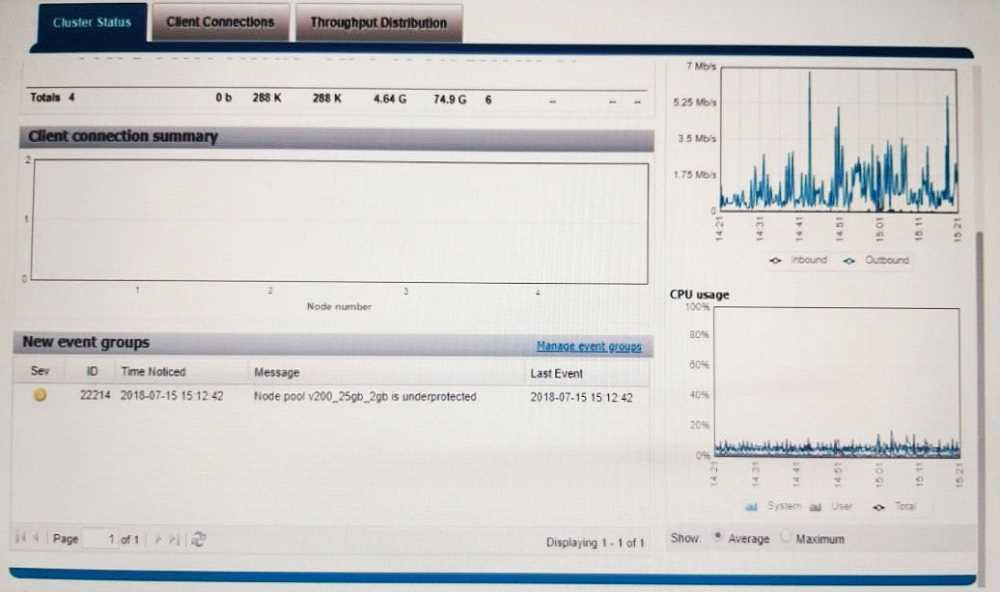
- A. RFC-2307 has been enabled
- B. NFS Export settings has been set
- C. Active Directory has not been added to the Access Zone
- D. User mapping rule has been created
Answer:
C
Question 3
The :nfs2 file system has been experiencing delays that have been impacting the entire Dell EMC
Isilon cluster. Neither Snapshots nor SyncIQ is configured for these directories. Use the Launch
Simulator button to verify the SSD strategy. Note: It is necessary to close (x) the simulator window
to answer the question.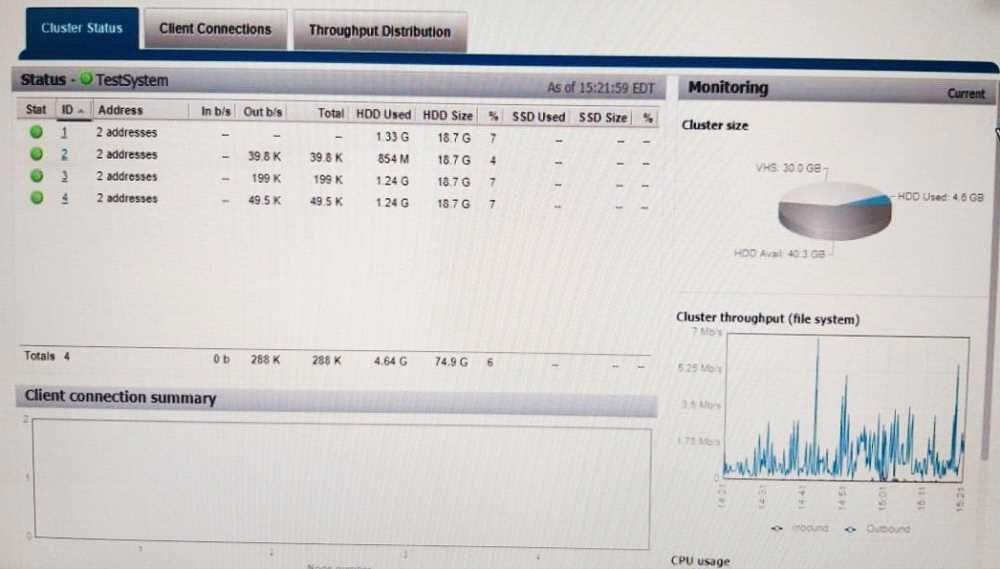
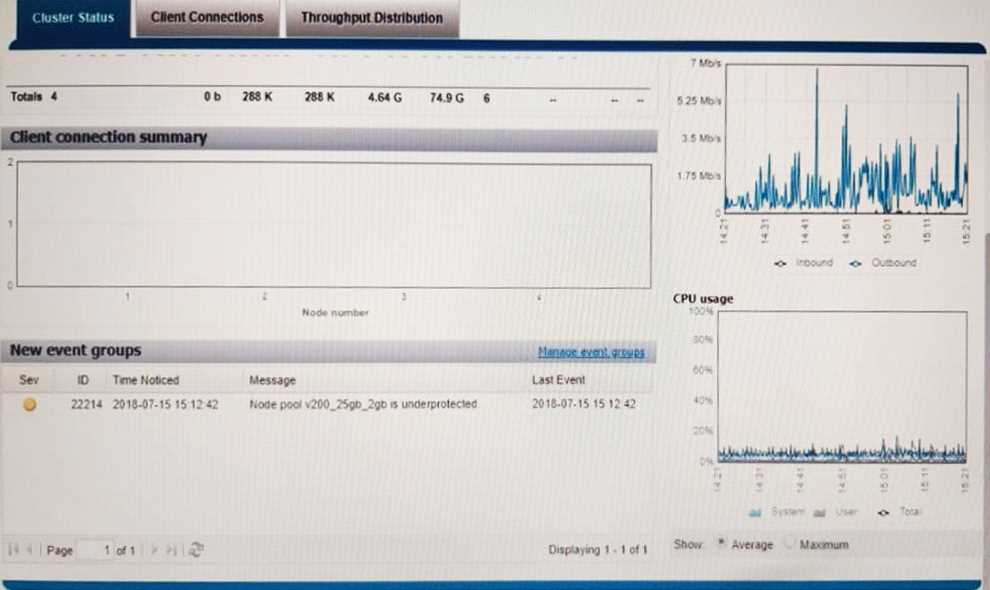
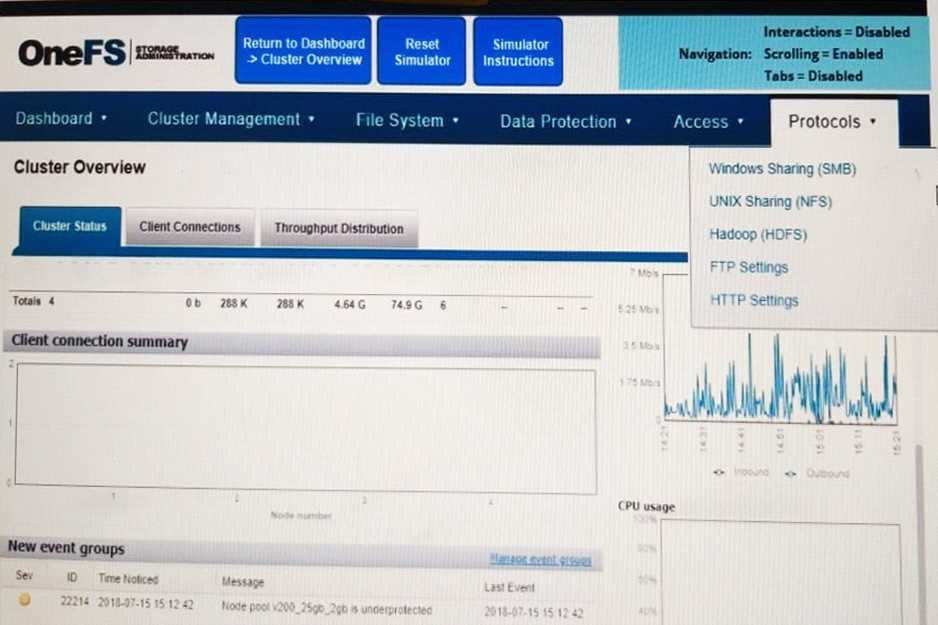
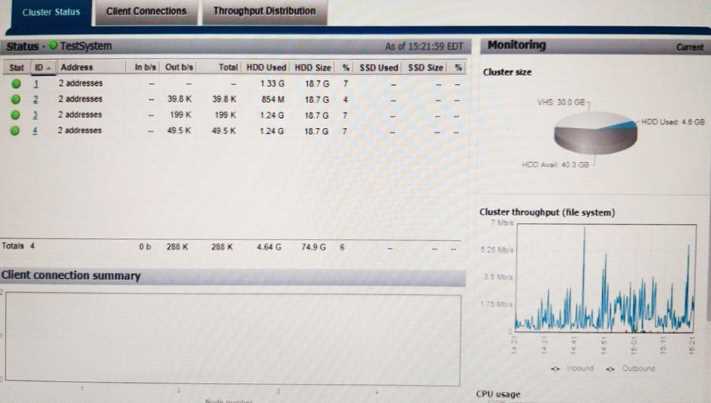
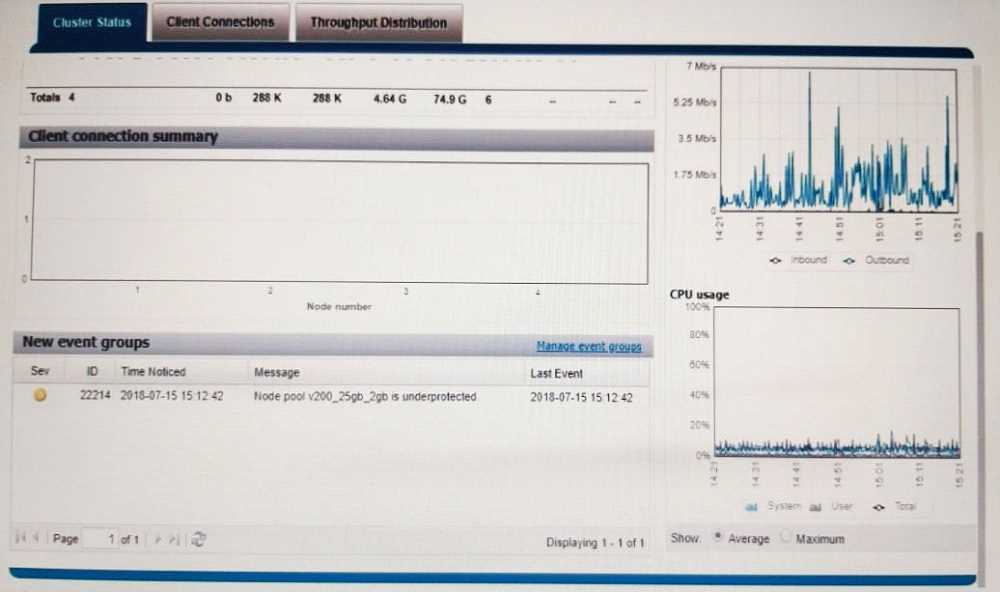
Based on your findings, which operation should be performed to address the delays?
- A. None; the 'Use SSDs for metadata read/write acceleration' strategy is set correctly
- B. None; the 'Use SSDs for metadata read acceleration' strategy is set correctly
- C. Set the strategy to 'Use SSDs for metadata read acceleration"
- D. Set the strategy to "Use SSDs for metadata read/write acceleration'
Answer:
D
Question 4
Case Study 3
A financial services company has file sharing workflows and 2000 home directories which include
70% Microsoft Windows and 30% Linux. The Security team is also interested in credit card usage data
analytics such as point of sale, geolocation, and authorization and transaction dat
a. Home directories and file shares do not require D@RE or SEC compliance.
However, due to the sensitivity of the credit card data, the company requires D@RE for credit card
information and must adhere to the U.S. SEC 17a-4(f) compliance standards. Additionally, they are
interested in auditing user access and anti-virus features.
The compute and storage environment consists of the following:
200 TB of Fibre Channel drives on NetApp ONTAP 7
Environment is expected to grow 200 TB over the next three years
Which type of encryption is used in a D@RE-enabled Dell EMC Isilon cluster?
- A. 128-M AES encryption key
- B. 256-bit AES encryption Key
- C. 1024-bit SKA encryption key
- D. 2048-bit SHA encryption hey
Answer:
B
Question 5
Case Study 3
A financial services company has file sharing workflows and 2000 home directories which include
70% Microsoft Windows and 30% Linux. The Security team is also interested in credit card usage data
analytics such as point of sale, geolocation, and authorization and transaction dat
a. Home directories and file shares do not require D@RE or SEC compliance.
However, due to the sensitivity of the credit card data, the company requires D@RE for credit card
information and must adhere to the U.S. SEC 17a-4(f) compliance standards. Additionally, they are
interested in auditing user access and anti-virus features.
The compute and storage environment consists of the following:
200 TB of Fibre Channel drives on NetApp ONTAP 7
Environment is expected to grow 200 TB over the next three years
In order to remove the encryption key on the SED drives, which steps are required?
- A. SmartFail the cluster and then remove the drive
- B. Suspend the cluster and then SmarlFail the drive
- C. Suspend the node and then remove the drive
- D. SmartFail and then remove the drive
Answer:
C
Question 6
Which combined solution addresses the company requirement for D@RE and U>S SEC 17a-4(1)?
- A. SED and Smartlock Enterprise mode
- B. All Flash and SmacILock Compliance mode
- C. SED and SmarlLock Compliance mode
- D. SmatlLock Enterprise mode and $TIG
Answer:
B
Question 7
The company's IT team is now looking (or a new data protection strategy. The company wants to:
Minimize the backup window
Increase the speed of data recovery
Reduce the network traffic
Reduce the overall growth of the backup datasets
The IT team indicates that their current backup hardware will be used in any solution. Which solution
meets their requirement?
- A. Change the backup strategy to token-based backups
- B. Increase the backup tape block size to 512 KB
- C. Implement an incremental forever backup strategy
- D. Configure the DMA to use IPv6 for better performance
Answer:
C
Question 8
SPECIAL INSTRUCTIONS
The remaining Part1 questions are associated with four case studies that describe various
environments or settings. Each case study appears on its own display screen. Questions for each case
study will appear on separate display screens.
When displaying a question, you can easily review the related case study by clicking on the Review
Case Study icon shown below:
Case Study 5 Refer to the Exhibit.
Backing up data from a Dell EMC Isilon cluster exceeds the companys backup window. Because the
company has a large amount of data with a continuous high growth rate, they want to change their
backup strategy. The Gen 6 Isilon cluster consists of 24 nodes. Their current backup strategy is an
NDMP three-way backup performing weekly full backups to tape and incremental backups each
night. The strategy uses Dell EMC NetWorker. The DMA uses Include paths to specify what data to
backup. All data on the cluster must remain accessible.
The companys IT team is now looking for a method to increase the performance of their backups.
After some investigations, you notice that the backup job quiesces the file system. This is creating
lock contention issues on open files and not allowing users full access to data when the backup job
runs.
What advice should be provided to the team to eliminate lock contention and allow full access to
users?
- A. Enhance the backup strategy using snapshots tor backups
- B. Add A100 Backup Accelerators and configure for three-way NDMP
- C. Stop using an NDMP-based backup strategy
- D. Create a cron job to remove all locks before each backup
Answer:
B
Question 9
SPECIAL INSTRUCTIONS
The remaining Part1 questions are associated with four case studies that describe various
environments or settings. Each case study appears on its own display screen. Questions for each case
study will appear on separate display screens.
When displaying a question, you can easily review the related case study by clicking on the Review
Case Study icon shown below:
Case Study 5 Refer to the Exhibit.
Backing up data from a Dell EMC Isilon cluster exceeds the companys backup window. Because the
company has a large amount of data with a continuous high growth rate, they want to change their
backup strategy. The Gen 6 Isilon cluster consists of 24 nodes. Their current backup strategy is an
NDMP three-way backup performing weekly full backups to tape and incremental backups each
night. The strategy uses Dell EMC NetWorker. The DMA uses Include paths to specify what data to
backup. All data on the cluster must remain accessible.
The companys IT team is now looking for a method to increase the performance of their backups.
After some investigations, you notice that the backup job quiesces the file system. This is creating
lock contention issues on open files and not allowing users full access to data when the backup job
runs.
What advice should be provided to the team to eliminate lock contention and allow full access to
users?
- A. Add A100 Backup Accelerators and configure for two-way NDMP
- B. Change the backup strategy to token-based backups
- C. Exclude the targets datasets from the backup job
- D. Create more parallel streams to utilize multi-stream NDMP backups
Answer:
A
Question 10
Case Study 1
A company has several independent business units that operate globally. The company has
consolidated its IT infrastructure services and operations. Common infrastructural services which
include IPAM, DNS, NTP, DHCP, and SMTP have been consolidated. The company has complimented
its infrastructure development by investing in Dell EMC Isilon clusters to host its users home and
group directories and for compliance archival purposes required by individual business units.
The IT operations are located in India and the United States with its primary data center facilities co-
located between New York and Texas. The company has a total of 60 AD forests:
1 main domain
55 domains have one-way trust relationships with the main domain
An additional 4 domains do not have any trust relationship with no future plans of establishing trust
relationships with the other domains.
Users of different AD domains use different FQDN to access their corresponding file services.
Additionally, the company does not plan to consolidate the AD domains and each domain uses a
different IP subnet. The users of the domains with no trust relationships have a compliance archival
requirement. The company wants to all data to be replicated between New York and Texas.
What is the minimum number of replication policies that are required to facilitate granular failover
and failback capabilities for each AD domain?
- A. Only one replication policy per Access zone
- B. Two replication polities for each Access zone, one for regular data and one for the Smartlock directory
- C. One replication policy per Access zone with an additional replication policy for each SmartLock directory
- D. One replication policy for all data on the cluster
Answer:
B
Question 11
Case Study 1
A company has several independent business units that operate globally. The company has
consolidated its IT infrastructure services and operations. Common infrastructural services which
include IPAM, DNS, NTP, DHCP, and SMTP have been consolidated. The company has complimented
its infrastructure development by investing in Dell EMC Isilon clusters to host its users home and
group directories and for compliance archival purposes required by individual business units.
The IT operations are located in India and the United States with its primary data center facilities co-
located between New York and Texas. The company has a total of 60 AD forests:
1 main domain
55 domains have one-way trust relationships with the main domain
An additional 4 domains do not have any trust relationship with no future plans of establishing trust
relationships with the other domains.
Users of different AD domains use different FQDN to access their corresponding file services.
Additionally, the company does not plan to consolidate the AD domains and each domain uses a
different IP subnet. The users of the domains with no trust relationships have a compliance archival
requirement. The company wants to all data to be replicated between New York and Texas.
What is the minimum number of groupnets required?
- A. 1
- B. 2
- C. 5
- D. 9
Answer:
D
Question 12
Case Study 1
A company has several independent business units that operate globally. The company has
consolidated its IT infrastructure services and operations. Common infrastructural services which
include IPAM, DNS, NTP, DHCP, and SMTP have been consolidated. The company has complimented
its infrastructure development by investing in Dell EMC Isilon clusters to host its users home and
group directories and for compliance archival purposes required by individual business units.
The IT operations are located in India and the United States with its primary data center facilities co-
located between New York and Texas. The company has a total of 60 AD forests:
1 main domain
55 domains have one-way trust relationships with the main domain
An additional 4 domains do not have any trust relationship with no future plans of establishing trust
relationships with the other domains.
Users of different AD domains use different FQDN to access their corresponding file services.
Additionally, the company does not plan to consolidate the AD domains and each domain uses a
different IP subnet. The users of the domains with no trust relationships have a compliance archival
requirement. The company wants to all data to be replicated between New York and Texas.
How many tenant Access zones will be required?
- A. 1
- B. 55
- C. 59
- D. 60
Answer:
C
Question 13
Case Study 4
A company is experiencing a noticeable decrease in performance when accessing data on their Dell
EMC Isilon cluster. The cluster hosts Microsoft Windows home directories and general purpose file
shares. In addition, a file pool policy moves data that has not been modified in six months to an
achieve tier. The administrator wants your assistance in understanding the reason for the slow data
access. The number of users accessing the cluster has not changed.
The administrator has shared the following baseline metrics. The outputs were captured from a
performance- acceptable time frame.
Trace route shows:
-3 hops between clients and the cluster
-Average latency is 3 ms
Iperf shows:
-940 Mb/s average bandwidth
-005 ms average jitter
Netstat on the local network shows:
-05% average re-transmission rate
Hostcache list:
-20 ms average roundtrip time across all clients
The administrator shows you the following output from the netstat command:
32366653 data packets (35556615947 bytes)
8010 data packets (9525723 bytes) re-transmitted
Based on the output, what information should be provided to the administrator?
- A. Re-transmission rates have no impact on performance
- B. Re transmission rate exceeds recommendations
- C. Re-transmission rate is in the acceptable range
- D. Change in the re-transmission rata indicates an issue
Answer:
C
Question 14
Case Study 4
A company is experiencing a noticeable decrease in performance when accessing data on their Dell
EMC Isilon cluster. The cluster hosts Microsoft Windows home directories and general purpose file
shares. In addition, a file pool policy moves data that has not been modified in six months to an
achieve tier. The administrator wants your assistance in understanding the reason for the slow data
access. The number of users accessing the cluster has not changed. The administrator has shared the
following baseline metrics. The outputs were captured from a performance- acceptable time frame.
Trace route shows:
-3 hops between clients and the cluster
-Average latency is 3 ms
Iperf shows:
-940 Mb/s average bandwidth
-005 ms average jitter
Netstat on the local network shows:
-05% average re-transmission rate
Hostcache list:
-20 ms average roundtrip time across all clients
The administrator shows you the details of the hostcahce.list output. The output indicates that the
top clients on the list have an average of 242 ms round trip time. Based on the output, what
information should be provided to the administrator?
- A. Only the aggregate of all average round trip bines will indicate an issue
- B. Recalculate and re-populate round trip uses by using the isi_cbind clear commend
- C. An increase in the average round trip time indicates a network problem
- D. An average round trip time less than 300 ms is the acceptable range
Answer:
A
Question 15
Case Study 4
A company is experiencing a noticeable decrease in performance when accessing data on their Dell
EMC Isilon cluster. The cluster hosts Microsoft Windows home directories and general purpose file
shares. In addition, a file pool policy moves data that has not been modified in six months to an
achieve tier. The administrator wants your assistance in understanding the reason for the slow data
access. The number of users accessing the cluster has not changed. The administrator has shared the
following baseline metrics. The outputs were captured from a performance- acceptable time frame.
Trace route shows:
-3 hops between clients and the cluster
-Average latency is 3 ms
Iperf shows:
-940 Mb/s average bandwidth
-005 ms average jitter
Netstat on the local network shows:
-05% average re-transmission rate
Hostcache list:
-20 ms average roundtrip time across all clients
The administrator shows you the following iperf output
890 Mb/s avenge bandwidth
96 8 ms average jitter
Based on the output, what information should be provided to the administrator?
- A. Amount of jitter a an indication of network congestion
- B. Numbers remain within the recommended range
- C. Amount of jitter is in an acceptable range
- D. Lower than average bandwidth needs to be investigated
Answer:
D